Following its dominance as a provider of silicon for smartphones, Qualcomm is eager to replicate that ubiquity with not only processors for augmented reality headsets but also reference designs to give device makers a head start.

The Photos app on iPhone has long offered basic editing features for quick edits to pictures, but iOS 13 greatly expanded them and gave the same love to videos. One of the best additions offers the ability to turn off photo and video edits without undoing them, so you can preview how your shots look with or without an effect.

As far as HBO is concerned, it's not augmented reality — it's Snapchat. The premium cable network is leaning hard on Snapchat's AR magic tricks to promote yet another series, this time for the adaptation of Philip Pullman's His Dark Materials series of novels.
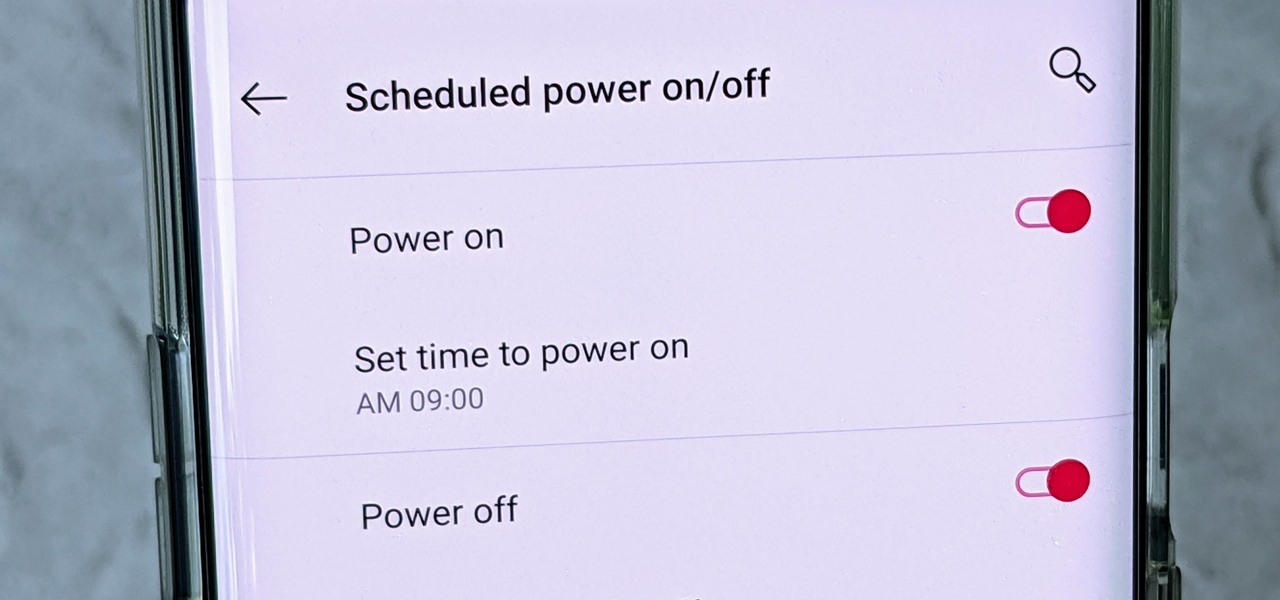
One of the more interesting power-related features for OnePlus phones is the ability to schedule a time to turn it, off then back on again. While OnePlus phones typically run blazingly fast, you can still benefit from the RAM clearing and process killing that a reboot provides. And since you can schedule this to happen overnight, you can wake up to a refreshed, restarted phone every morning.

One of the more low-key functions to arrive with the Note 10 was the ability to easily record your screen system-wide. Thankfully, this long-awaited feature will finally make its way to popular Galaxy devices like the S10 and Note 9 thanks to One UI 2.

The spatial computing world of Magic Leap is no longer limited to the rarefied tones of Sigur Rós and Sennheiser's Ambeo Augmented Audio app. Now, the entire music universe will be at your augmented reality fingertips.

All Kohl's wants for Christmas is Snapchat augmented reality. In conjunction with a holiday pop-up hosted in New York City from Nov. 7 through Nov. 10, Snapchat ran a sponsored portal lens available to targeted Snapchat users in the AR carousel. The experience gave users the ability to virtually transport themselves to the pop-up.

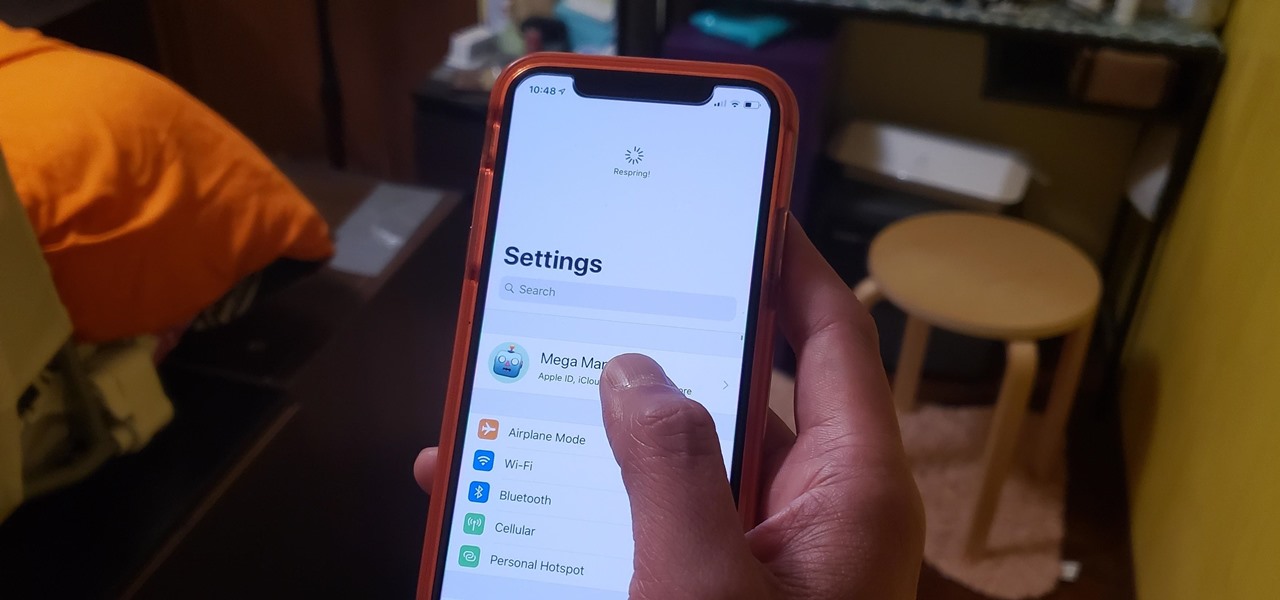
Restarting your iPhone can cure software glitches, but it should only be done as a last resort if your device has a semi-tethered jailbreak, because it will disable any tweaks you've applied. Luckily, your jailbroken iPhone has a faster alternative to rebooting to help you troubleshoot and make changes on the fly.

The iPhone 11, 11 Pro, and 11 Pro Max are the most advanced flagships Apple has to offer, but that doesn't mean they're immune to occasional bugs. Anything from an app plagued with issues to a faulty software update still can cause your device to freeze up, so having the ability to force a restart can come in very handy.

When attending networking events, a LinkedIn exchange is a common occurrence. Equally common is the awkward fumbling dance with how to add each other. Fortunately, we have the solution: the ultimate way to add LinkedIn contacts.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

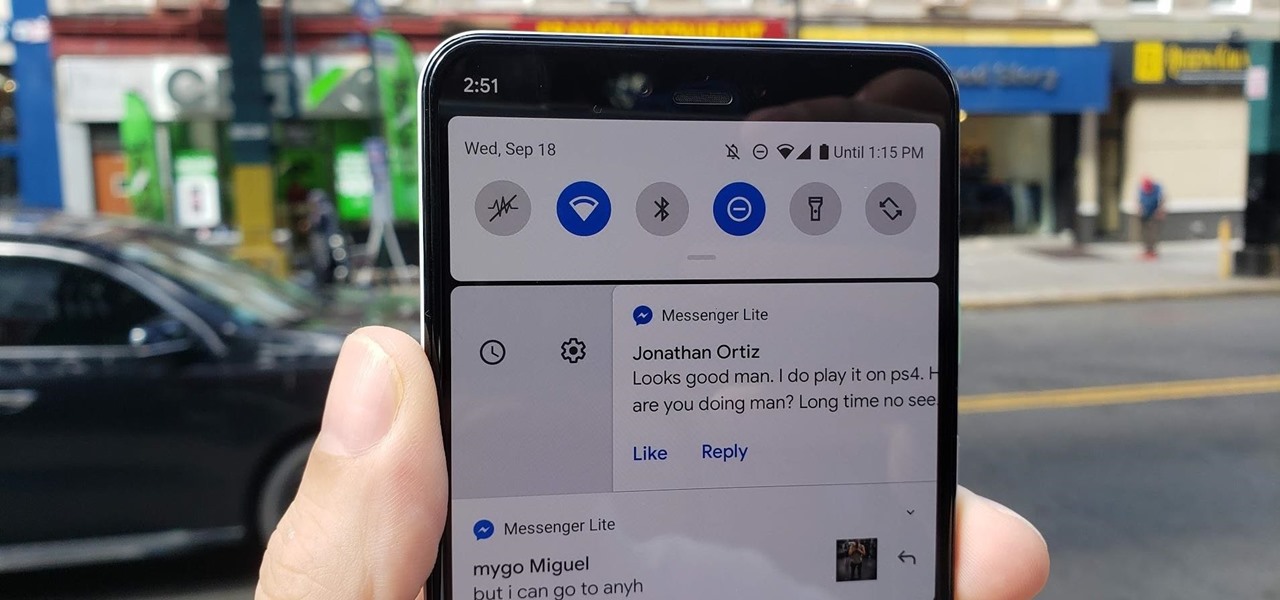
I'm a notification minimalist. When I get alerts, I want to deal with them ASAP. If the time is not right and I want to reference the notification later, snoozing was always the best course of action. But in Android 10, Google tucked away snoozing, so here's how to get it back.

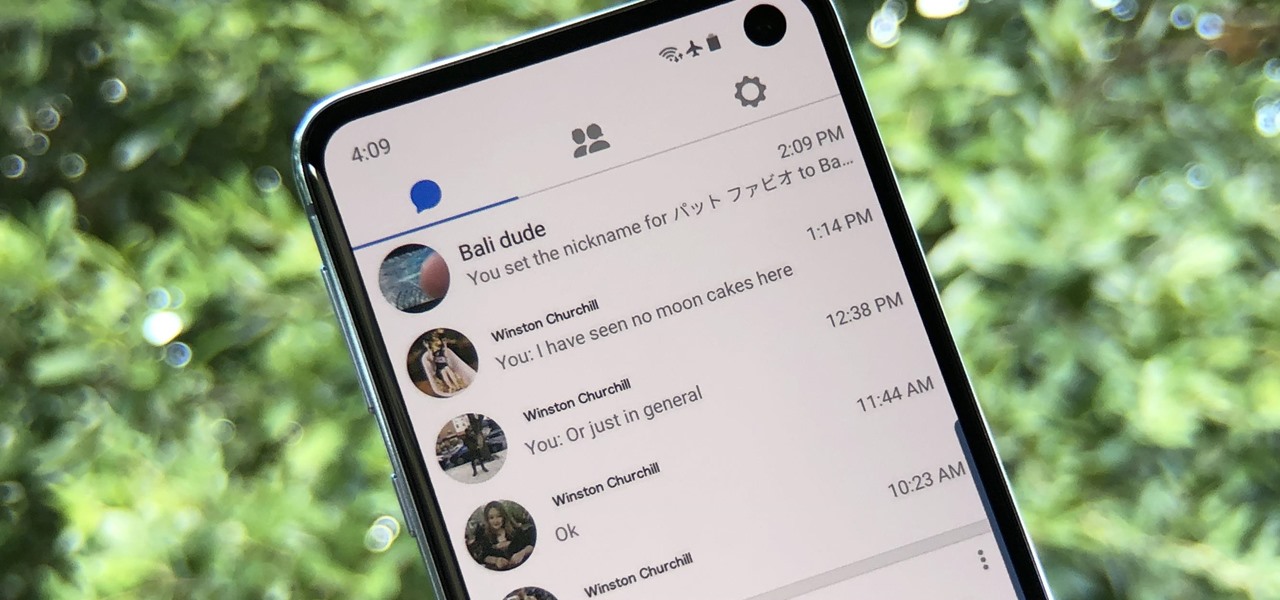
Facebook Messenger Lite is more than just a battery-friendly version of the full-fledged Messenger app for Android. It's still packing some pretty neat features and it's so much snappier than its bloated counterpart. All of the essentials are present, down to the ability to give your contacts nicknames.

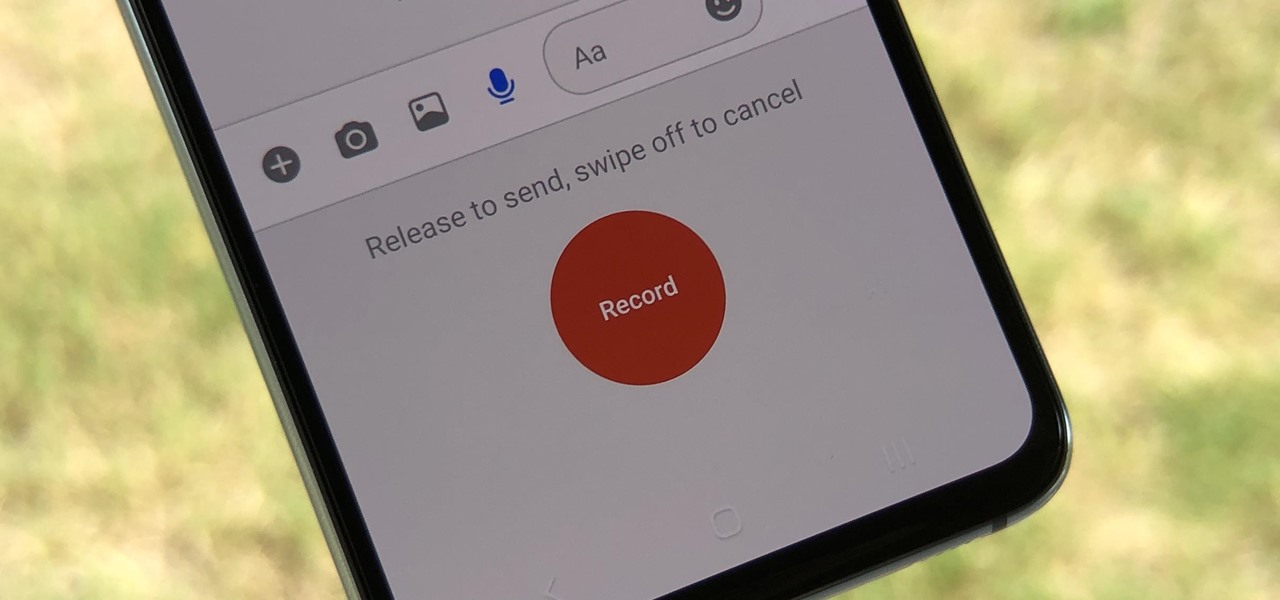
Facebook Messenger Lite is an official, de-bloated version of Facebook Messenger for Android. It's snappier and it's a lot more battery-friendly, but this is because there are fewer features complicating everything. One feature they didn't leave out, however, is the ability to send audio messages.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

If the name Leroy Jenkins elicits a reaction from you, then you are old enough to remember the iconic title World of Warcraft from its heydey (whether or not you actually played the massively multiplayer online role-playing game).

Video may have killed the radio star, but will volumetric capture and augmented reality kill the video star?

Imagine sitting on your patio, scrolling through your phone's photos, reminiscing about the past. Now imagine being able to see those photos floating in the air, at the exact vantage point from where they were taken a year ago.

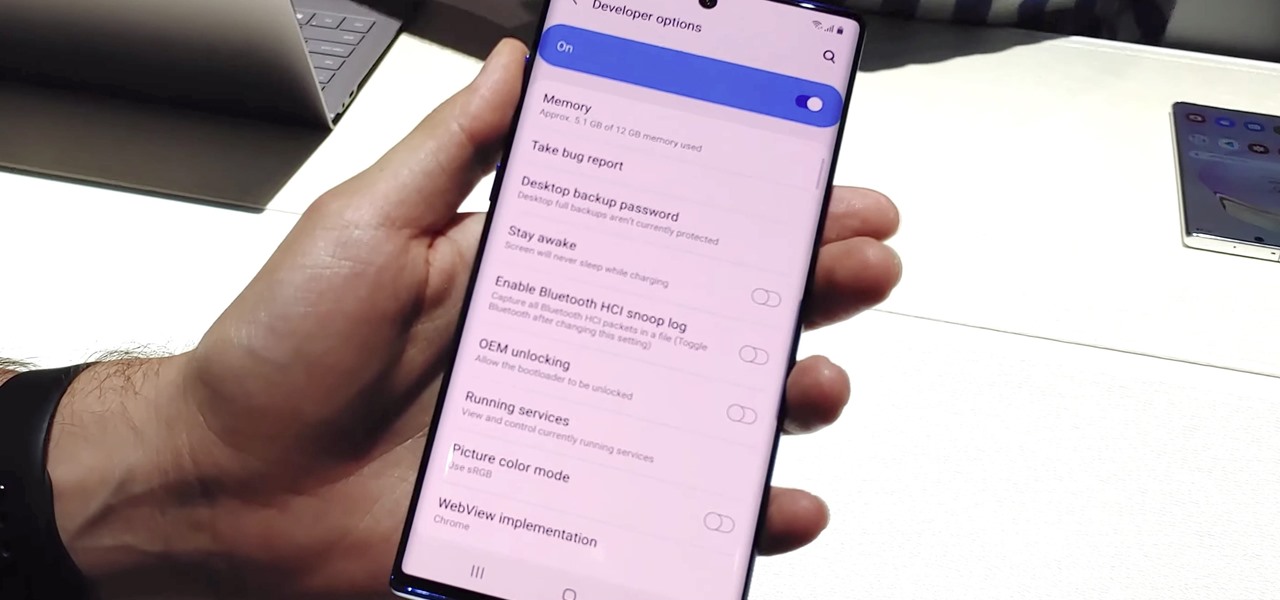
You may note be able to root your Snapdragon-powered Note 10, but thanks to the hidden Developer Options, you can still tweak low-level settings like custom codecs for better audio quality on Bluetooth headphones and faster animations to enhance your experience. Best of all, you don't need to be an expert at modding to take advantage of this menu.

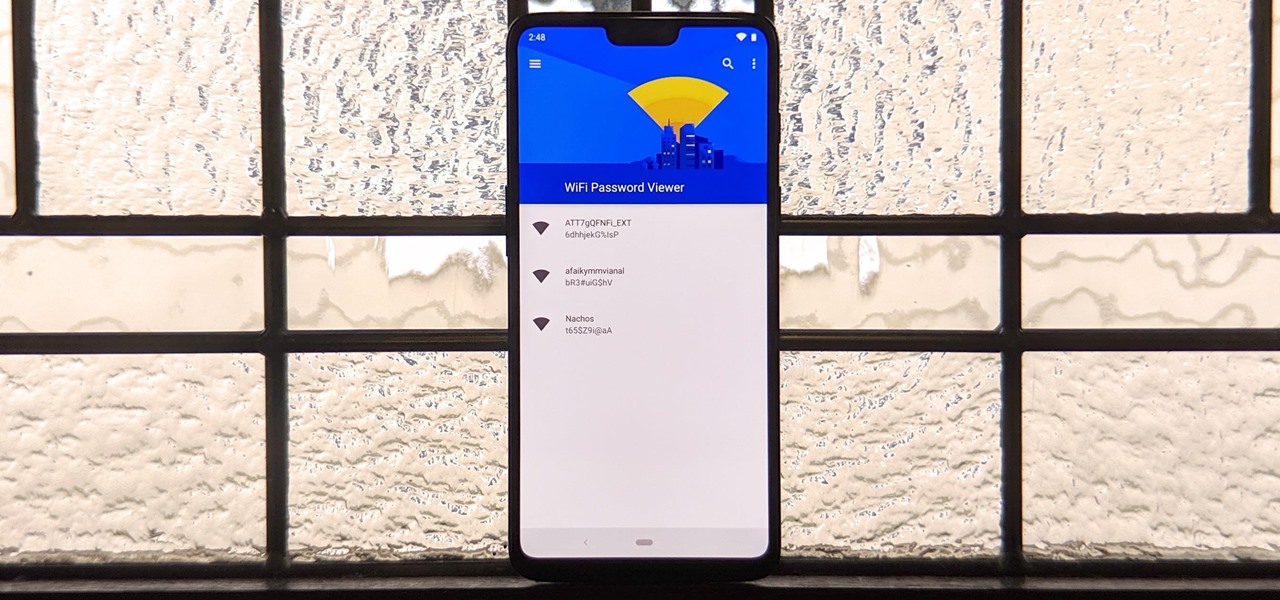
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

It's always great to see a company pull off a bit of augmented reality magic, but what we see is not always what it's cracked up to be.

With all the talk about returning to the moon via SpaceX, NASA, and international agencies, some have forgotten some of the magic surrounding the original Apollo 11 mission.

While the 49th Annual Gay Pride Parade and Festival will take place on Santa Monica Boulevard and West Hollywood Park, revelers will also be able venture Northeast to the TCL Chinese Theater on Hollywood Boulevard to continue celebrating via Snapchat.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

Though primarily a Pixel exclusive, Google Camera has become the go-to camera app for many Android users. Not only does come with a standout features like Night Sight and capture better photos than most stock camera apps, but it's also packed with functionality that makes it a one-stop-shop for all your photo and video needs.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

Don't look now, but stock photo mega-site Shutterstock may have the most extensive library of augmented reality content available.

The marketing team for Marvel Studios is doing "whatever it takes" to make sure you see Avengers: Endgame when it hits theaters in a couple of weeks, including offering an updated set of augmented reality Playmoji for the Playground app on Google Pixel.

The partnership between Magic Leap and leading South Korean wireless carrier SK Telecom took on an added importance earlier this week as the company unveiled the world's first nationwide 5G network.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

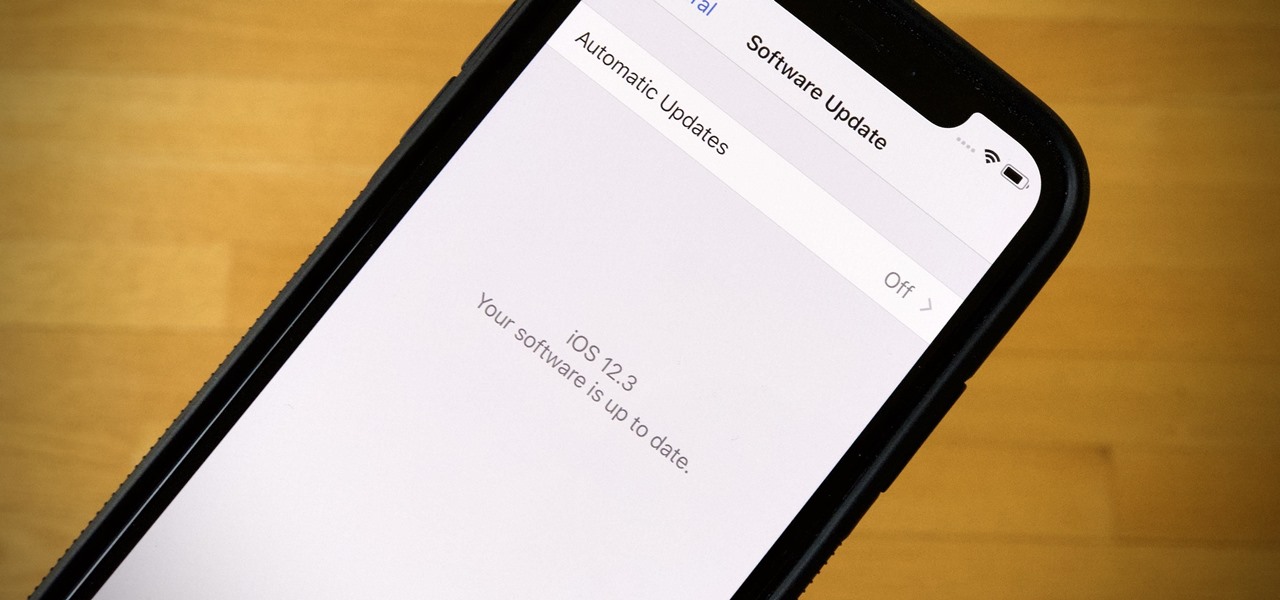
If you're a public beta tester, your Thursday just got awesome. Apple just released the first public beta for iOS 12.3 today, March 28. This update comes right on the heels of the first developer beta for 12.3, which itself released just one day ago. Thanks to that release, we know that this update contains a new TV app with updated layouts, Apple TV Channels subscriptions, a new logo, and more.

It's an exciting time to be an Apple fan. Monday saw not only a major announcement of new Apple services and subscriptions but also the official release of iOS 12.2. If you're a beta tester, you probably watched 12.2's evolution over the last two months. Well, get ready to do it all over again — Apple just released the first developer beta for iOS 12.3 today, Wednesday, March 27.

Hollywood loves sequels so much that studios and their marketing teams are not too proud to release a sequel of an augmented reality promotion.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

The navigation and status bars aren't very noticeable on the S10's home screen since they're transparent. The status bar will even change colors to match many apps. Unfortunately, the same can't be said for the navigation bar.