This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Connecting your Nokia N900 smartphone to a wireless hotspot or your home wifi network is just a few quick taps away! Take a look at this tech support video from Nokia that will tell you exactly where to find the available internet connections on the phone and select the one you wish to connect to.

Fring is a free app available from the Apple store which will allow you to use video chat, Skype or AIM on your iPhone 4 over a 3G network. This tutorial demonstrates how to use the app with your iPhone to make video calls.
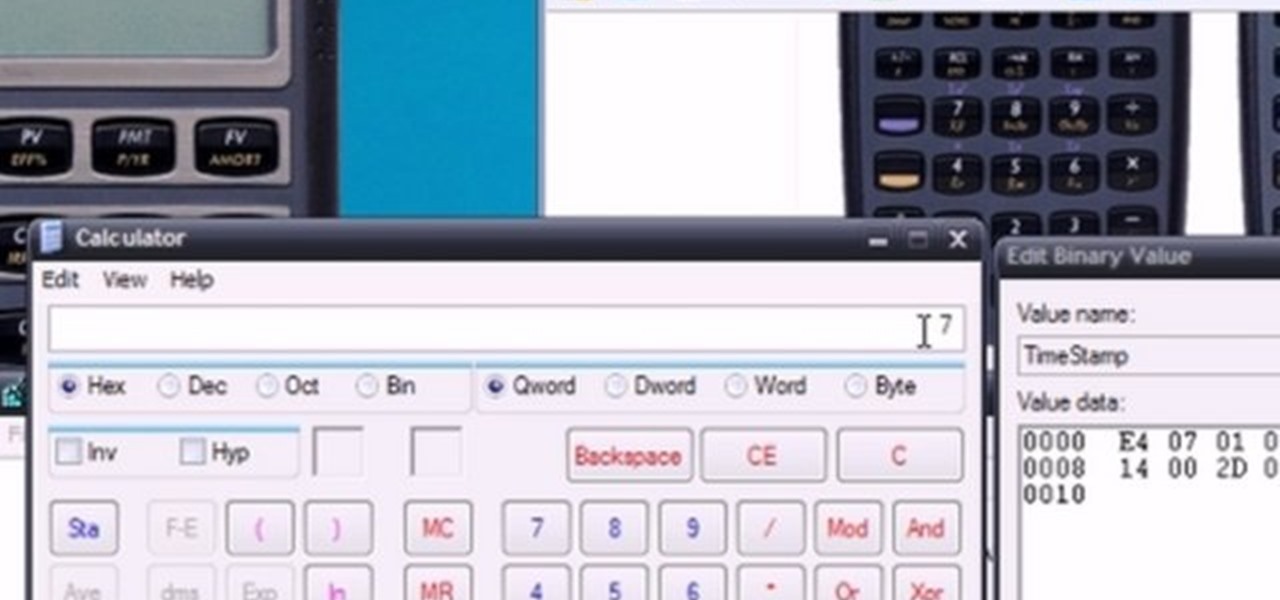
In this tutorial, learn about the nuances and abilities of the HP10BII Financial Calculator and how to get it running properly and indefinitely.

For efficiency’s sake, if you’re going to cheat on your girlfriend, you might as well date her roommate. Watch this video for some tips on how to hook up with your girlfriend's roommate. You will need a girlfriend with a jealous roommate and the ability to lie convincingly.

SyncVue announced at NAB that they would be offering a new version of their remote collaboration software for editors and producers. Well the long awaited update is finally here and all existing SyncVue users will definitely want to grab it. The functionality is improved and the new features are killer. So check out this quick little video tutorial on setting up and using the new version of the software, This walks you through the newest features and how to basically get around.

If you've ever wanted to syndicate your Ustream videos on YouTube but weren't sure how to go about it, then you'll be well served by this video tutorial. Ustream has the ability to convert recorded shows into a compatible YouTube format such as WMV and MOV. Learn how with this clip.

Ever wonder how you get debug mode in the classic Sonic and Knuckles game? It's not directly possible, but, by exploiting a class 7 bug (very severe as it'll crash the game) with Sonic 3 & Knuckles, you can. There's only one requirement: you've obtained all the emeralds and have the ability to transform. Take a look at this instructional video and learn how to get this mode in the game.

A magician's heart is easy to open, with a soda can tab. This simple prop trick just takes a soda can pull tab and a simple sleight of hand, the ability to palm small objects behind fingers. Watch this video magic tutorial and learn how to perform this soda can tab palming trick.

Watch this harmonica tutorial video to learn how to play octaves on your harmonica. The split interval or octave technique is useful in all different kinds of harmonica playing. Harmonica players of all ability levels will find this instructional video helpful in learning how to play octaves on a harmonica.

Learn how to utilize this ankle bounce exercise as a part of your ladder training workout, geared at improving your athletic ability.

The pataflafla is a unique drum rudiment that is sure to challenge your ability to play flam strokes. It requires that you play back-to-back flams with the same hand. This rudiment is great for drum fills and solo patterns.

Perfect for attaching the guy line of a tent to a peg or a post, this sliding loop is prized for its ability to adjust up or down, tighter or looser. If only pitching the rest of the tent were so easy.

Learn about the structure of the tee ball game in order to play and coach to the best of your ability.

This video is a demonstration of how to develop the ability to play in thumb position on cello. Many practical tips are given for practicing and performing.

This video starts off demonstrating the basic technique of how to count bars. Also, how to use this fundamental ability as a springboard for more advanced techniques such as mixing together beats or inserting a vocal into a break is explained.

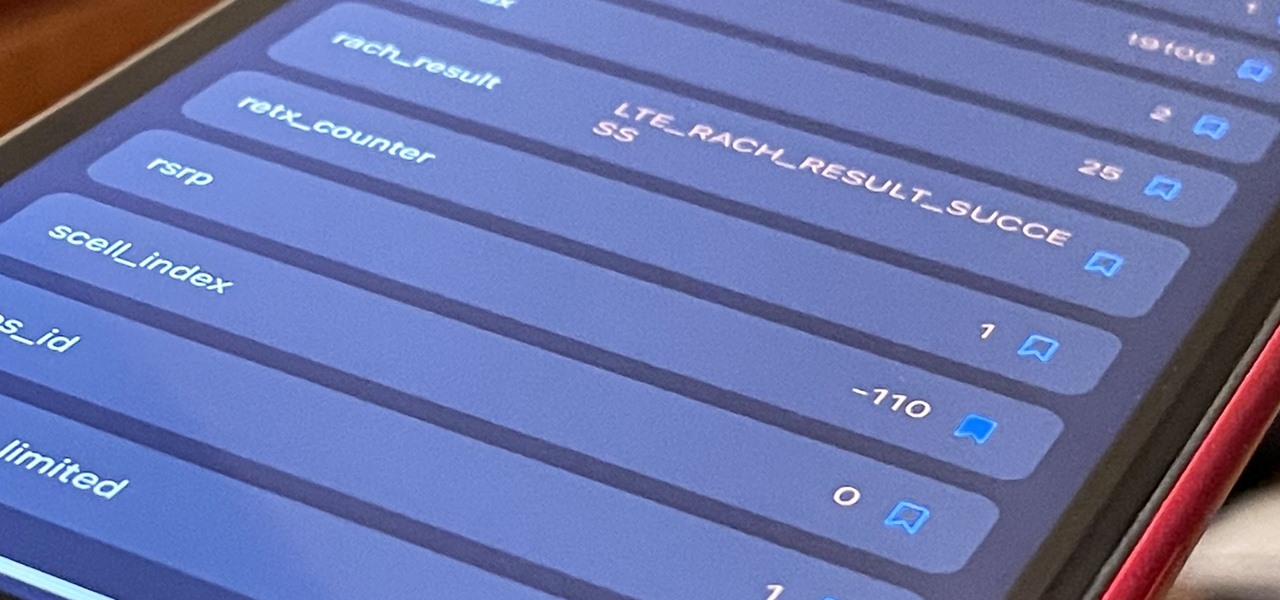
If you've ever used your iPhone's hidden Field Test mode to view your signal strength in decibel-milliwatts, locate the tower you're connected to, or find out the radio frequency in use, you no longer have to dig through all of the confusing-looking data every time you need to check. Apple updated Field Test's interface in iOS 15, and one improvement gives you more control of the Dashboard.

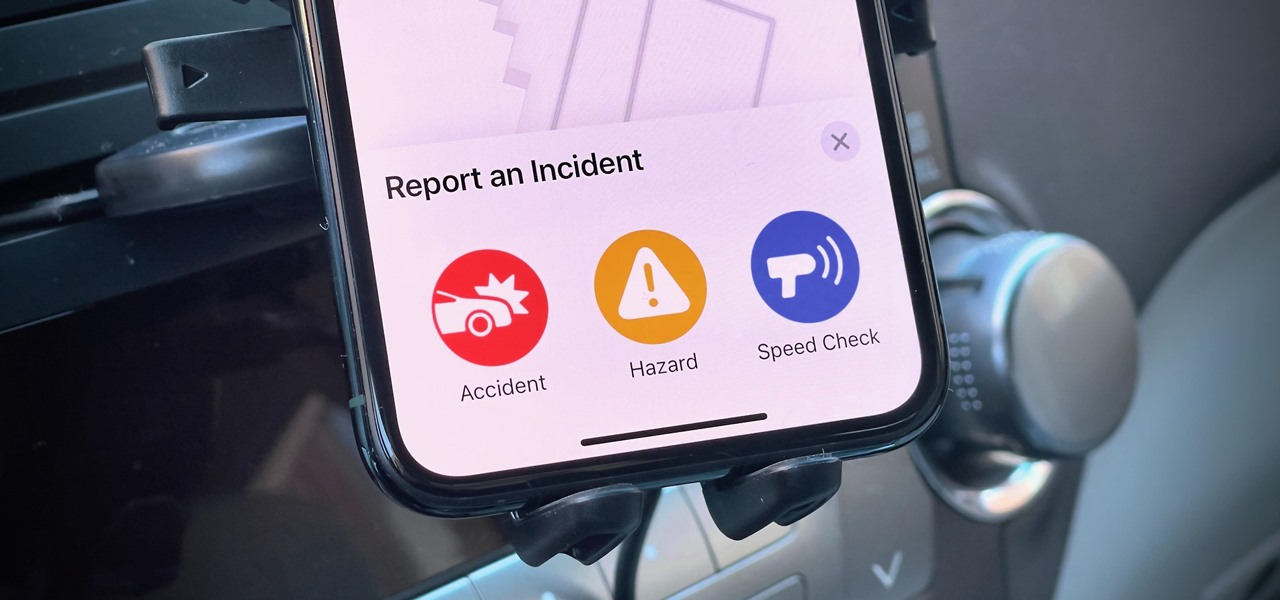
Driving is anything but problem-free. Speed traps, accidents, and other hazards can appear at any time, requiring motorists to be attentive, quick, and prepared for anything. If you see something dangerous on your route that you want to warn others about, there's an easy way to do so in Apple Maps.

ESP8266-based microcontrollers can be used to create exciting and legal Wi-Fi hacking games to test your or your friends' Wi-Fi hacking skills.

It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.

If you had a phone in 2004, there's a pretty good chance it was a Motorola RAZR. The iconic phone is the tenth highest-selling of all time, and it marked the height of the flip phone era. Now that the technology has caught up, Lenovo (Motorola's parent company) is bringing it back in a big way.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

When the Steam Link app was first introduced in 2018, I was impressed. As long as you were on the same network as your PC, you could play your Steam games on your phone. But now, it's even more impressive. By enabling a few extra settings, you can play your Steam library on mobile data anywhere in the world.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.