In this video tutorial, viewers learn how to set and encrypt the wireless password using WEP Apple Airport. Begin by opening the Apple Airport utility program. Then find the network's name and double-click on it. The Configure "Apple Airport Express" opens, click on the Airport tab. Then click on the Wireless Security button. Now click on the Wireless Security drop-down menu and select 128-bit. Click on the Set WEP Password button, type in the password and verify it. Finish by clicking on Upd...

Watch this video to learn how to encrypt Wi-Fi using WEP password on Linksys in 4 simple steps. Connect to your wireless network. Open your Web browser and type in the web address http://192.168.1.1. Press enter key. Type in the User Name for your network. Type in the Password, press OK button. Select the Wireless text tab, select the Wireless Security text item. Pull down and select the WEP menu item. Type in a good password. Click the Generate button. Click the Save Settings button. Encrypt...

Jeremy at GamerTell shows us how to connect our X-Box 360 to the internet VIA Windows Vista and a Laptop Computer that is already connected to a wireless network. First we have to connect your laptop to your X-Box 360 using an Ethernet cable. Now we will turn on the Xbox 360. Make sure you are on the correct TV Input or channel. Now go to your laptop and Click on the start button on your laptop and find control panel. Once your in control panel select Network and Internet. Now we will select ...

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

This how-to is aimed at the uncynical, bright-eyed outsider who wants to become a television producer…the talented person who believes he or she has the ‘it’ to crack Hollywood. The ‘Sammy’ who just arrived in 90210.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to set up a WiFi network on a mac, For Dummies.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

If you're a believer in the power of logic, may as well skip the game tomorrow. Two math professors at the University of London have supposedly determined who will win the World Cup, and have displayed their findings as a sophisticated infographic:

Just acquired a new Sony PlayStation 3? Well, in order to start using the many extra online features of the PS3, you will need to set up your internet connection. This interactive video walkthrough takes you step-by-step through the process of connecting your version of the PlayStation 3 to the web.

Here is a magic trick for the kids. Ever want to learn how to make a coin go through something? Be the first kid on your block to learn how to make a coin go through a jar and make all your friends believers in your magical abilities. Make a coin go through rubber.
Do you'll know a program software to detect unmask caller's for cellphones for abroad network's carriers, as i often travel abroad to Hong Kong ,Japan and Malaysia and i went switch to those networks via changing the States sim card to the local domestic sim card i often received unmasked/private number's callers calling myself but i have not way of finding out who is it?
Do you know a program software to detect unmask caller's for cellphones for abroad network's carriers, as i often travel abroad to Hong Kong ,Japan and Malaysia and i went switch to those networks via changing the States sim card to the local domestic sim card i often received unmasked/private number's callers calling myself but i have not way of finding out who is it?

Parody of the social network using Pres Obama.

Amazing trailer. A sequel that's not a sequel, but takes the series to the open skies! From the official website:BioShock Infinite is a first-person shooter currently in development at Irrational Games, the studio behind the original BioShock (which sold over 4 million units worldwide). Set in 1912, BioShock Infinite introduces an entirely new narrative and gameplay experience that lifts players out of the familiar confines of Rapture and rockets them to Columbia, an immense city in the sky.F...

As discussed in a previous tidbit, people are over-confident in their abilities for many reasons. Here's an example...

Remember Dan White's "Twinkie defense" in 1979? Well it turns out that the the ability to convert food into glucose is correlated with the ability to control oneself.

In this video, you'll find instructions on how to use the Ettercap plug-in dns_spoof to set up DNS spoofing on a local area network. This Ettercap plug-in is ony one potential way to pull of DNS spoofing, and only works if the attacker is on the same subnet. To get started DNS spoofing with Ettercap, press play! Use DNS spoofing in Ettercap.

+Eric Cattell, the Social Graph Technical Lead of Google+, announced a lot of improvements and added features this morning, most of them having to do with circle management and blocking people.

We've covered Chrome browser extensions that make your Google+ experience richer and more useful, but there are still many users who prefer to use Firefox. To that end, I've gathered 13 Firefox add-ons to aid in the enhancement of your Google+ experience.

This infographic from SingleGrain aptly and succinctly describes the primary differences between Facebook and Google+. Which social network will reign supreme?

There's a lot of talk going around about Google's new social network and how it's heavily influenced by Facebook, but truth be told, how could they build Google+ without taking a note
From Gaming Age: An Xbox LIVE Gold Family Pack includes:

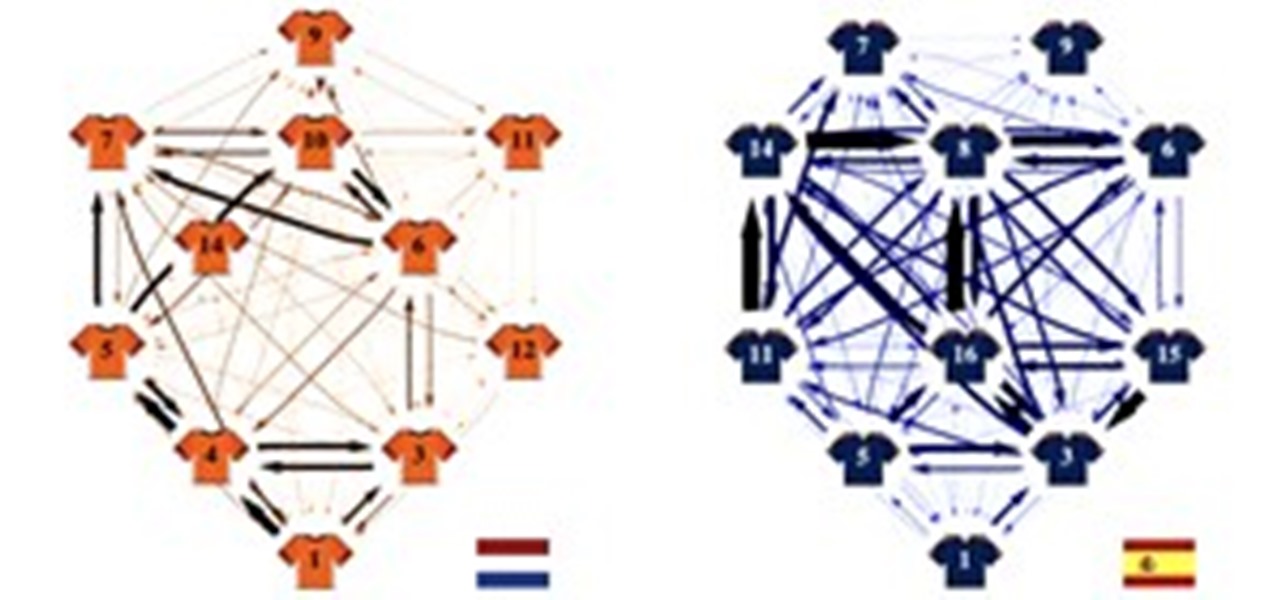
Sami Hyypia, who plays defense for Finland, claims that it doesn't matter how fast or slow you are in soccer. Rather, it's your ability to read the game that'll determine whether you win or not.

You will need to have the correct grip on the baseball to have accurate and consistent pitching abilities. Arrange your fingers in proper positioning and throw at a consistent speed when warming up and practicing pitching.

This modo 302 video shows briefly how to use the enhanced Symmetry Fix tool which now has a topology traversal method. This new method dramatically improved the ability to heal meshes that have become asymmetrical. modo 302 is a free service update for all modo 301 users. Use the enhanced symmetry fix tool in modo 302.

In modo 301 3D painting has really "come of age". One powerful enhancement is the ability to paint across multiple images of varying resolution with a single stroke. It's very nice. Why are you reading this? Watch the modo 301 clip! Paint across multiple UVs in modo 301.

This how-to video shows how to enable the ability to stream audio and video through Second Life. This is very self explanatory, but for those that don't know, this how-to video should help. Stream audio and video in Second Life.

This video brings you a great guide on surfing with the expertise of Andy Bottomley. Learn how to read the waves and improve your surfing ability dramatically. Read waves while surfing.

What is a master page, and how is it used? This video shows you new features of master pages in InDesign, including the ability to override master page items, and text wrap on a master page. Check out this how-to video created by Colin Fleming now! Work with master pages in InDesign CS3.

Expert knitter Rachel Ong shows you how to knit the knit stitch, which is the most basic stitch and requires the ability to cast on. A large pair of knitting needles and a smooth, large weight pure wool yarn. Knit the knit stitch.

People who work in PMC all the time should really have a kiln, but for folks who want to give it a try, the ability of PMC3 to be torch fired is a huge advantage. This video is only a minute or two long, and it's practically a real-time demonstration on how to torch fire Precious Metal Clay. Torch fire precious metal clay.

Snapchat users have clamored for the ability to share their Stories since the app's inception, and we're finally going to be able to with "Stories Everywhere." Similar to how Twitter gave people the ability to embed tweets in 2011, Snap, Inc. aims to make Stories even more accessible for those outside of the platform.

How to Make the Internet Faster in Windows 7 Go to Control Panel.

You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Social network fatigue sets in when it starts to feel impossible to keep up with all that new content from your friends, followers, and acquaintances on a daily basis. You lose track of stuff you wanted to read more about, and you miss important news from your friends, but are bombarded with inconsequential details from people you don't actually care about. What's the solution? Filter your streams so that you only see the content you do care about, and get rid of the rest.
I've struggled for a long time trying to set up a virtual network between my KVM virtual machines. I tried several forums and tutorials on the web, but still on my system it just wouldn't work. I eventually got it owrking, so I've decided to make some notes of my own. Hopefully it will be helpful to you as a reader as well.

It seems like the EU is currently in the works of making "the production or sale of devices such as computer programs designed for cyber-attacks" illegal. So, if you're a network admin that uses WireShark or Metasploit, you better watch out!