Adobe Premiere Pro CS4 software is the start-to-finish video production solution ideal for editors, filmmakers, cable and network broadcasters, event and corporate videographers, rich media creative professionals, and hobbyists. In this Adobe Premiere Pro CS4 video tutorial, you'll learn how to apply color correction. Color correct in Premiere Pro CS4.
Adobe Premiere Pro CS4 software is the start-to-finish video production solution ideal for editors, filmmakers, cable and network broadcasters, event and corporate videographers, rich media creative professionals, and hobbyists. In this Adobe Premiere Pro CS4 video tutorial, you'll learn how to apply special effects. Take a look. Apply effects in Premiere Pro CS4.
Adobe Premiere Pro CS4 software is the start-to-finish video production solution ideal for editors, filmmakers, cable and network broadcasters, event and corporate videographers, rich media creative professionals, and hobbyists. In this Adobe Premiere Pro CS4 video tutorial, you'll learn how to instert graphics into your Premiere projects. For more information on inserting graphics, watch this video lesson. Insert graphics in Premiere Pro CS4.

Adobe Premiere Pro CS4 software is the start-to-finish video production solution ideal for editors, filmmakers, cable and network broadcasters, event and corporate videographers, rich media creative professionals, and hobbyists. In this Adobe Premiere Pro CS4 video tutorial, you'll learn how to export audio to multimedia formats such as Blu-ray and YouTube as well as how to launch the Adobe Media Encoder and render vide. Export a project from Premiere Pro CS4.

Check out this instructional swimming video that demonstrates the proper techniques to practiceing the single arm drill. The single arm drill ensures that you are getting the rotation you need throughout your stroke. Push off the wall with both arms extended in front of you with your hands touching, one on top of the other. Rotate to your side so that you are lying on your left side with your left arm in front on you. Now, swim down the pool, using only your right arm - once you get to the ot...
Many people think that learning to use Regular Expressions is difficult, but if you stick to the basics it is actually quite easy. This screencast and cheatsheet will give you a gentle introduction and allow you to gradually expand your knowledge into advanced usage.

This vehicle video tutorial contains a basic testing procedure using an automotive fuel pressure gauge as a detection tool. Correct fuel pressure and fuel pressure regulator operation is essential for your truck or car's engine to operate properly. Many engine run-ability problems can be related to a weak or failing fuel pump or faulty fuel pressure regulator. Problems can range from hard cold engine starting, low power and stalling while driving. This video contains visual information design...

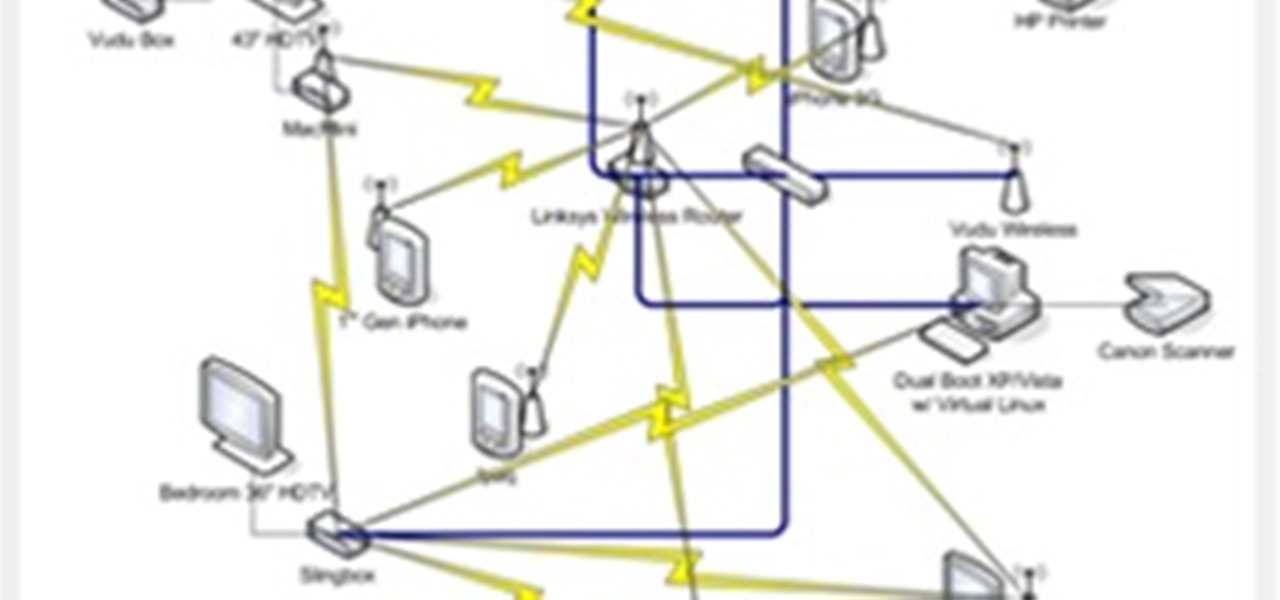
Having Internet connection problems? Is your PC's net connection dead? Learn some steps you can take to troubleshoot and fix the problem including dealing with cables, routers, ISPs, and Windows network settings. Reset your Internet connection.

A quick-stop-rescue is harder for a beginner to perform. But allows the sailboat to stay closer to the COB. It is also easier to keep site of the COB during the maneuver. Shown in the picture is the a final approach to the COB on a close reach. (Whether one approaches an COB on a close reach or in-irons will depend on your boat's maneuverability, position after your jibe, wind and sea conditions and helmsman's ability.) Quick stop when a victim is in the water while sailing.

In this video tutorial you will learn to export Photoshop layers into Flash. See how to export each Photoshop layer as a PNG file so you can import each file into Macromedia Flash 8. Portable Network Graphics (PNG) format is especially useful when you have transparencies in your files. Export Photoshop layers into Flash.

In this Computers & Programming video tutorial you will learn how to encrypt a D-Link router with WEP password protection. First you connect to your wireless network. Open your browser and type in http://192.168.0.1. Type in your base station username and password and press OK. Under the SETUP tab, select WIRELESS SETTINGS, scroll down to 'Wireless Security Mode' and select 'Enable WEP Wireless Security'. Scroll down to WEP. Under WEP Encryption pull down menu select 128Bit. Now create a pass...

In this video tutorial, viewers learn how to change the default password on a NET-GEAR router. Begin by opening your web browser and go to this site: Router Login. When the Prompt window opens, type in your router's user name and password, and click OK. In the sidebar, under Maintenance, click on Set Password. Now type in the old password, new password and re-type the new password once again to confirm. Finish by clicking Apply. This video will benefit those viewers who use a NET-Gear router,...

In this video tutorial, viewers learn how to disable SSID broadcast on a NETGEAR router. Begin by opening your browser and go to the site: Router Login. Then type in your user name and password. Click OK. In the sidebar under Setup, click on Wireless Settings. In Name (SSID), type in a new network name and click on Apply. In the sidebar under the Advanced, click on Wireless Settings. Type in your user name and password once again, and click OK. Under Wireless Router Settings, uncheck Enable S...

In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on the tab on the left hand side of the screen that says "wireless settings". Type in your user name and password once more, then find where it says "security settings", and click on the "WPA-PSK" radio button. Now, make a p...

Oh Data, You so Awesome! We are going to use Node.JS to gather us some data. Given nodes plethora of well abstracted network abilities and it's deep evened nature, it will make quick work of plugging into various data sources and gathering / making good use of said data.

In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff.

This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you should set one up.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we've covered over time.

You've been on Google+ for a few weeks now. You're loving it. You're exchanging thoughtful posts, pictures with your friends, meeting new people and following lots of interesting, intelligent people. There's just one problem.

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

I've always wanted a gigantic saltwater aquarium, but maintaining a big, beautiful fish tank is not only time consuming—it's expensive. Also, it's a potential hazard if you have children, pets or any other uncontrollable elements around the house.

Despite the fact that you may not find this as a necessity, if you do follow this quick guide, you will wonder how you ever managed before. This tutorial is based on the assumption that you're using Google Chrome, so if you aren't, I advise you to download and install it. Furthermore, this tutorial is aimed towards beginners, however advanced users may also learn a thing or two.

Reading crochet instructions for beginners isn't exactly the easiest thing to do. But fear not, I'm here to help! :)

Hi there, nullbytes! I've been recently using NullByte as my only source of learning (almost) and it has proven to be really good to me.

Mass Effect 2 may have been around for a whole year... but not on the PlayStation 3. And last Tuesday, January 18th, PS3 gamers finally got their hands on a copy of the critically acclaimed RPG. Actually, this is the first time any Mass Effect game has been available on the PS3, making this a historical event for BioWare.

Despite the recent problems with the 1.04 update for PlayStation 3 gamers, Call of Duty: Black Ops remains a juggernaut for Activision in the gaming community, and its sales alone prove it.

www.jailbreakme.com has recently created a new way to Jailbreak any iPod Touch, iPhone, or iPad, regardless of the firmware it is running. It is EXTREMELY easy! If you were thinking about Jailbreaking, but were afraid you did not have the technical abilities to do so, now you can! What is "Jailbreaking?"When someone says that their iPod, iPhone, or iPad is "jailbroken," they mean that they have installed Cydia, a third-party app store.Why Jailbreak? Why not just stick with the original App St...

This tutorial offers a look at using point clouds in shading, and the pcopen, pciterate, and pcimport nodes in VOPs. It also gives a further example of a POP network. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.
(CNN) -- Abu Yahya al-Libi, the No. 2 man in al Qaeda and a longtime public face of the terror network, has been killed by a U.S. drone strike in Pakistan, a U.S. official said Tuesday.
The Department of Homeland Security has been forced to release a list of keywords and phrases it uses to monitor social networking sites and online media for signs of terrorist or other threats against the U.S.

How to play Spy, my personal favorite class What do Spies do?

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.
Backtrack 5 R2 was recently released and added over 40 new tools and updates to their old tools. Along with a new Linux 3.2.6 Kernel and better networking support.

http://www.seonorthamerica.com Learn how to sign up for and use Onlywire's automatic social network and social bookmarking submission service.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

A hacker from Anonymous broke off communication with an FBI agent posing as a Symanec employee after being offered $50,000 to not publish the Symantec pcAnywhere code online. And in a not surprising turn of events... the code was released today on peer-to-peer networks.

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

The Standing Stones in The Elder Scrolls V: Skyrim are wonderful little additions to the game. Basically, they give your character modified attributes, or special abilities to give you the upper hand in the game. For example, if you activate The Mage Stone, you'll learn all of your magicka skills 20% faster. Long story short, they're awesome and you should find as many as possible.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.