5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

A free Wi-Fi hotspot can be a lifesaver. Whether it's because you have shitty reception, need faster connectivity, or just don't want to go over your monthly data plan, free Wi-Fi in public areas is greatly appreciated. While connecting to these free hotspots is fairly easy, finding them can become a whole nother issue. I've been in plenty of situations where I wasted my data plan instead of taking a few steps to the right, where free Wi-Fi would have been waiting for me and my Samsung Galaxy...
In the business world, it is always best to have the people you work with. For you to become the best you could give, here are at least 5 tips in using team building tools.

When the specs for Google's Nexus 4 came out, most critics were more than thrilled. A very fast processor, lots of RAM, a big display with very high resolution, and an 8MP camera made it the media darling of the smartphone world. It climbed the ranks of the best smartphones available, but couldn't quite reach to the top due to one reason—no 4G LTE. Samsung's Galaxy S III and Apple's iPhone 5 both come with 4G LTE, so why couldn't the LG Nexus 4? While there are many reasons, Google was stated...

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...

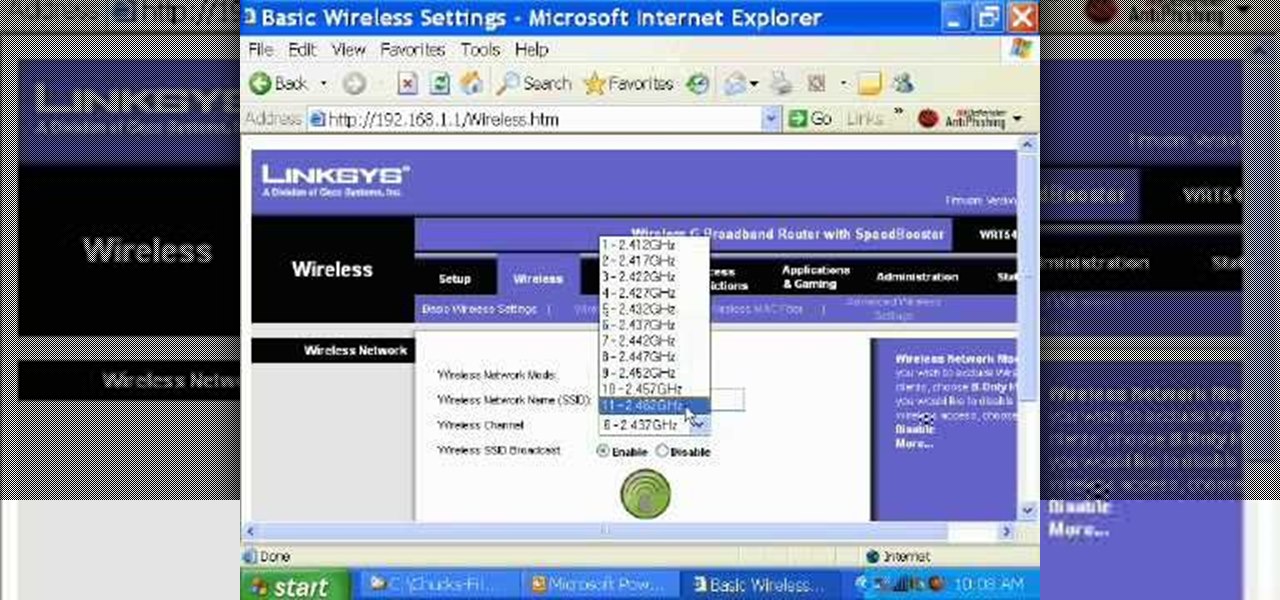
This video tutorial is in the Computers & Programming category which will show you how to set up a Linksys WR54g or WRT54g2 wireless router. First you connect to your Linksys router. Then go to http://192.168.1.1 and type in "admin' as your password in to log in window and click "log in'. then go to the "wireless' tab and enter your wireless network name. In the wireless channel select '11 2.462GHz' and click save. Next go to "wireless security' and type in the wireless network key. This is t...

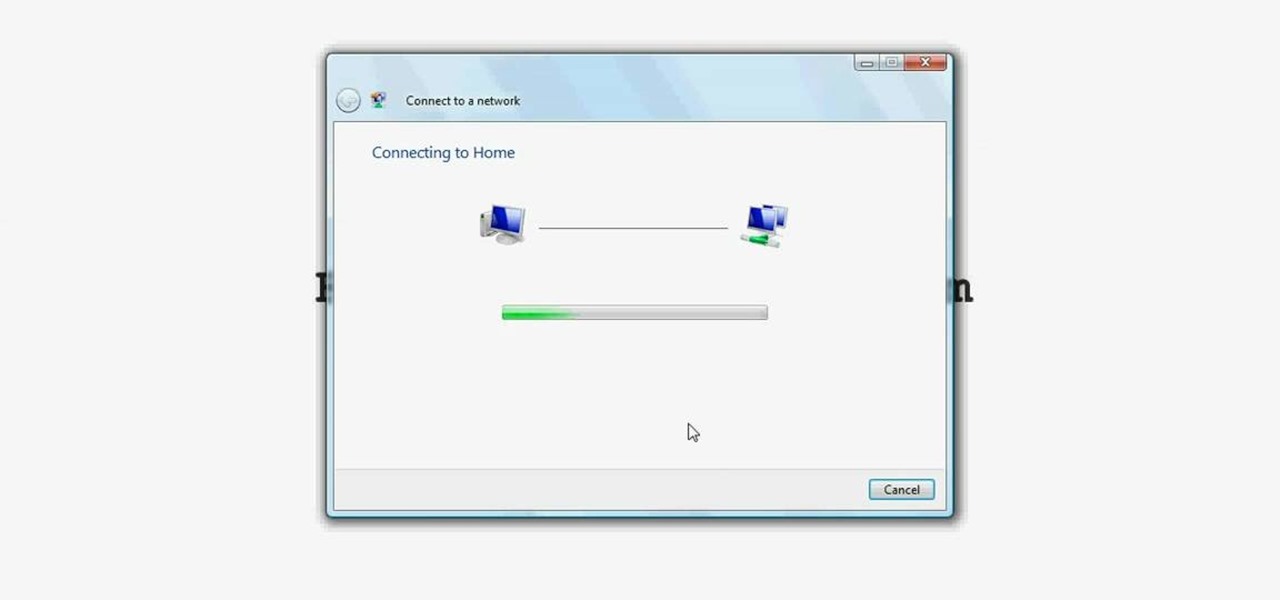
Wireless networks are really the only way to go these days. With WiFi you can access the world wide web from almost anywhere, at anytime, and not have to worry about annoying wires or cords. In this tutorial, learn how to set up a wireless connection in a Windows Vista based machine.

Ever had router trouble? Got router trouble? Well don,t worry the people over from quickcert.com have made this video to help! More specifically a linksys 802.11g router. All new routers come with a standard Ethernet cable, which must be plugged into one of the four ports on the router and connected to your computer as well. This is necessary to change settings, using Microsoft IE (internet explorer) when the routers IP is typed into the address bar. It is strong recommended to change the def...

In this five part video series, we are going to be creating a gorgeous storage chest that is sure to be a favorite at your house. Over the course of these videos, I will give you easy to follow instructions, along with some helpful hints.

What does your backyard need? A garden. You already have one? Then how about a garden bench? Join Lowe's as they walk you through, step by step, the building of a wooden garden bench. One of the most marvelous things about woodworking is that with just a little planning and effort, you can turn a few boards of lumber into an beautiful and elegant project like this bench.

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

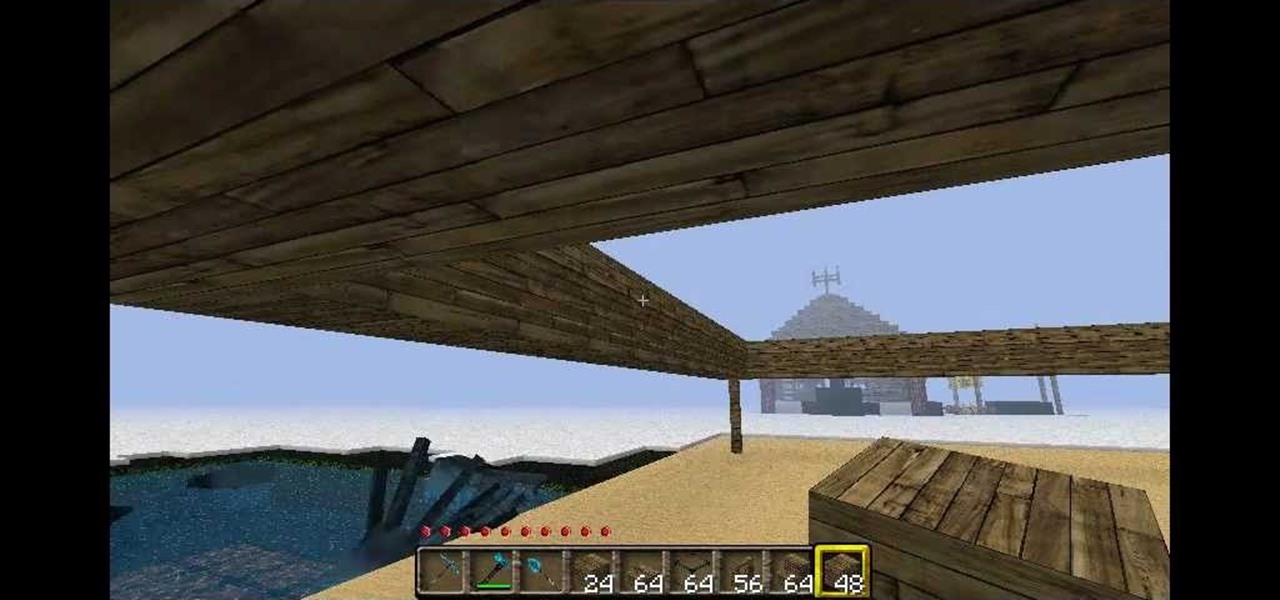
In this two part tutorial, you will learn how to build a beach house from scratch in Minecraft. You will need wooden planks, wooden slabs, glass, fence, wooden stairs, levers, doors, pistons, and redstone torches. Once you have all of your resources, you can construct a beautiful raised house on the sand.

Minecraft presents a vast, seemingly never ending landscape for exploration. How do you cover all of that ground? This video will show you how to build a train station, including a minecart call button and automating station. Watch this video to learn how to make a minecart train station in Minecraft beta.

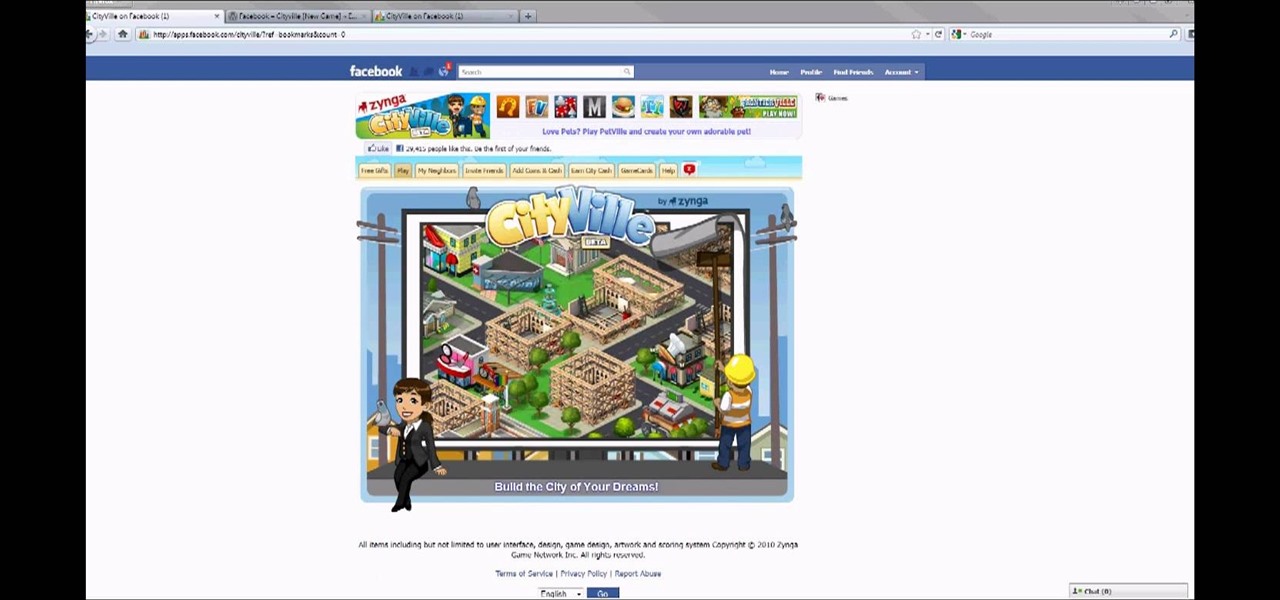
CityVille is the newest Facebook game from Zynga, the same people who make FarmVille and FrontierVille. Starting from scratch, this tutorial shows you how to start and build your own city. Make sure you have the most efficient and profitable city of all your friends!

Having an epic base in Minecraft is one thing, having an epic moat, much more awesome. But let's up the stakes, a moat that also doubles as a way of killing those nasty zombis, spiders, creepers and more and then transports all their loot right into a little holding area that you can claim them from. In this two part video series you'll learn how to construct the moat itself, although he does it for a 6x6x6 building you can do it for larger, it will just require more materials.

Looking for a new Lego project? Look no further! In this two-part series you'll learn how to build a great flat bed truck out of lego bricks! Each video starts showing you each brick that you'll need, the first video being the truck cab, and the second being the actual flat bed, and then goes into a great, step-by-step tutorial, showing you where each piece goes and before you know it you'll have a flatbed truck!

There's nothing like spending time outside with friends and family members during chill winter nights. What makes those nights so great is usually a nice, warm fire. You can easily build one by gathering some stones together to make a pile or you can build one from scratch using material you can find at home improvement stores. These can last for many years and make it much more safer to use, especially when you have little ones hanging around the area. So check out this tutorial on how to bu...

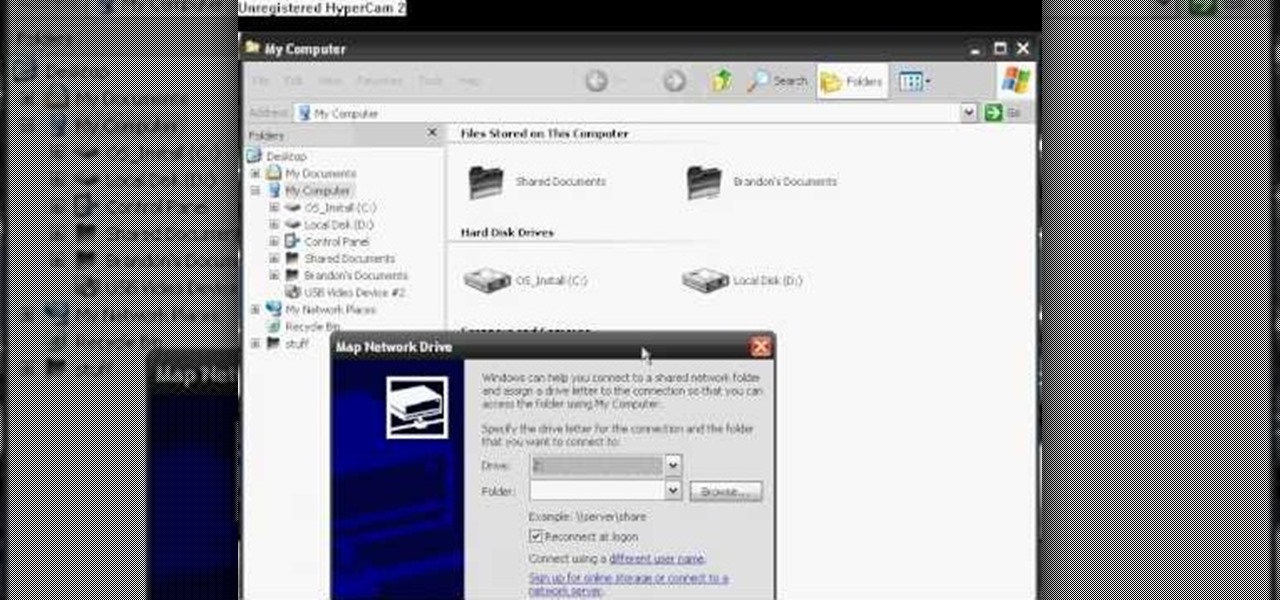
This tutorial will walk you through the steps you need to map a network drive for file access in Windows XP. By mapping your network drive you will be able to store and access files offsite and make computing easier all around.

How to build a high tunnel to protect your plants

If you ever find yourself in the woods after a long day of hunting or fishing, you're going to need a fire. So in this two part video tutorial you'll find out how to build an upside down fire and make it last longer than the traditional method of making a fire. Enjoy!

Getting into killer shape can be a lot harder than it seems. It takes a lot of hard work, dedication, and knowing the right approach. Trainer Vince Del Monte shows you seven exercises to have a killer workout.

Tony Reale shows you how to mod a pro-sumer Canon HV30 camera rig in order to give it a more professional setup. Here are the items he uses:

In this video, Andy Bell shows different ways of how to build temporary makeshift stairs for use during construction or remodeling projects. He will teach you how you can easily measure your own stringers (the sides of the stairs, that the steps rest on to cut them on your own, or, as he tells viewers, you can also build stair building kits that come with the stringers precut and ready for use. Learn about the variations of precut stringers, as well as their affordability! Then, the procedure...

In this video the instructor shows how to map a network drive in Microsoft Windows XP. Network drive is similar to the disk drive that is present on your computer like C drive, D drive but instead of pointing to a hard disk on your computer it points to a server that has enabled shares. Shares allow you to create or edit files and folders. By mapping that server share to a folder in XP you can use that share as a normal drive. To do this go to start menu, right click on My Computer and select...

Veronica from Tekzilla teaches you how to monitor network activity on Windows 7. Go to ITSamples and download the Network Activity Indicator program. Install it and run it. This will add a new icon on your system tray. It blinks to reflect incoming and outgoing packets. You can right click to see a more detailed report. You also get statistics and a menu for your network and firewall settings. So to get the popular windows XP type network indicator icon all you need to do is follow the steps ...