In this episode of Southwest Yard and Garden Curtis Smith shows you how to turn a steep slope into a usable garden. By building walls along the slope using serpentine designs he shows you how to obtain a compromise of both strength and artistic design. Starting with a good concrete footer and rebar you can construct a retaining wall strong enough to hold the weight of the slope. Materials such as wood and railroad ties can be used but may not stand the test of time as the weight of the soil c...

Curtis Smith, an extension horticulturist talks about using cages for your tomato plants. He says that some people like to stake tomatoes, some like to cage them and some even just let their tomato plants sprawl. He talks to a local gardener who has built his own tomato cages out of concrete wire. The gardener shows his cages, which he built 10 years ago and they still look sturdy today. Curtis gives a few tips like wrapping the cages with a special fabric that lets air and light through, but...
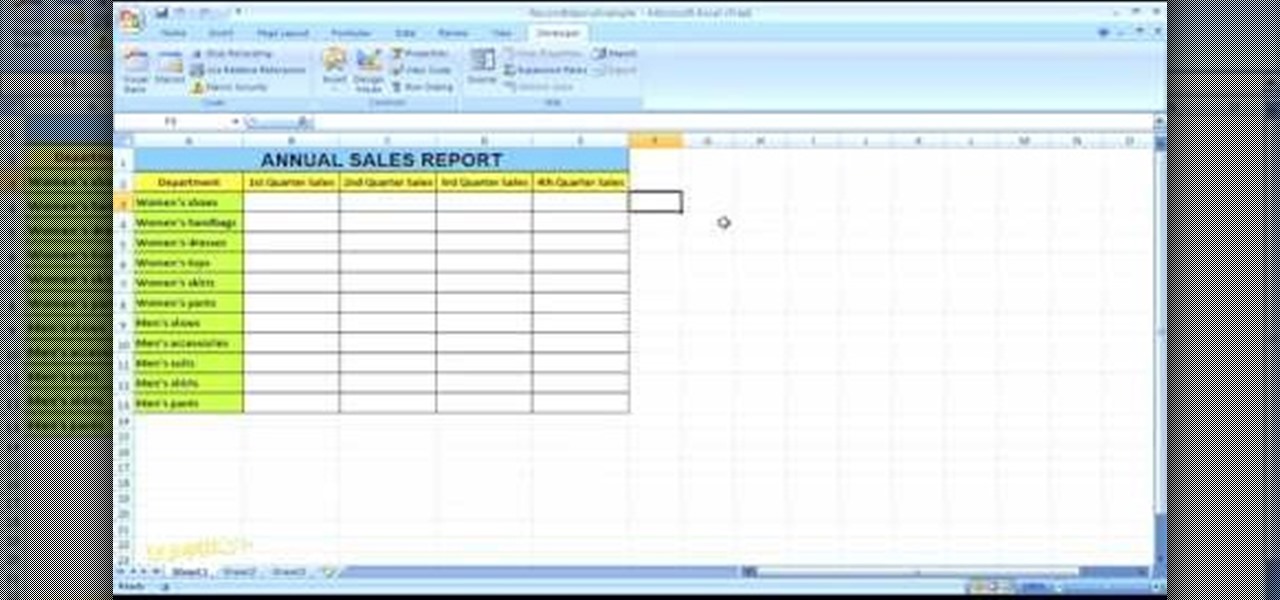
In this Microsoft Excel 2007 for Dummies video the instructor shows how to record a Macro. Macros let you create a shortcut to perform a sequence of commands all at once. For example you can create a macro to quickly build a sales report template that you frequently use. When ever you run that macro the Word will automatically build the template for you based on the recorded commands. To write macros you need to have the developer tab enabled. To enable it click on the office button and at th...

In this culinary how-to from the Food Network's Ellie Krieger, you'll learn how to bake delectable, almost-healthy carrot cupcakes using whole carrots, lemon zest, canola oil, brown sugar, two eggs, 3 quarters of a cup of whole wheat pastry flour, 1/2 cup all-purpose flour, 1 teaspoon of baking powder, 1/2 teaspoon of cinammon, 1/4 teaspoon of nutmeg and a 1/4 teaspoon of salt.

Wondering how you can finally use that Paragon? Dooom Box shows how to finally start using the Paragon using the Imbagon build in Guild Wars in what he calls the "Imbaguide".

See a tour of the new fur system in Houdini 9.5! It presents a workflow for adding fur to a character, then dives into implementation of the tools to help build that fur.

Home security is as important as having a job. You have to protect your family and your valuables. If you can't afford a high tech security system, then maybe a fake security camera will do the trick. This security camera dud is also a cheap alternative for a film prop. Watch this video tutorial to learn how to build a fake cardboard security camera.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

Check out this Make Magazine segment on building mini robots. Then you can move onto huge ones like Big Dog!

Filming can get REALLY expensive, especially if you're just out of film school and starting on your first major short. It requires not only a camera, but a crane for swooping panoramic shots, a mounted camera rig for overhead shots, lens filters, and moving ground camera mounts, among other things.

In this demonstration, you will see how to build an HVX200 up with a Zacuto Letus35 Elite DOF Baseplate and Backfocus kit in a handheld setup. These three videos will show you how to build the HVX200 setup from nothing, start to finish. The first step to setting up the package is the baseplate, just like most cameras. If you want, you can even add a monitor to the setup to see what you're doing when filming.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

Mike Lively of Northern Kentucky University shows you how to build an interactive Molecule Viewer in Papervision3D and Flex 3. This is a fun application building project for anyone learning Adobe Flex Builder 3 and a great resource for molecule viewer for students, educators, and researchers in chemistry and biochemistry.

This tutorial builds the RED ONE camera from scratch into a traditional film style camera, complete with matte box and follow focus.

Build this ultra-simple AC electric generator from magnets, wire, and cardboard. (And a big nail!) Light a small lightbulb, or flash a red LED.

Who knew some plastic, water and air would be so much fun? If you like rockets and explosions, you probably knew. And so did this guy, who shows you how to make an awesome water rocket that can shoot over 200 feet! Before you try following along with the rocket build, you should gather the materials—5' long piece of ½" PVC, small length of 1½" PVC, glue, ½" PVC "T" fitting, 2 PVC caps (½"), ¾" hose clamp, 7" zip ties (9 of them), duct tape, 2-liter plastic bottle, and a bicycle pump (or air c...

Want to boost your WiFi reception? Have an extra wok or parabolic collander? This video tutorial demonstrates a simple hack that will allow you to build an effective radio antenna that will significantly increase the gain of your WiFi signal. To replicate this hack at home, you'll need the following items: (a) a piece of parabolic cookware, (b) heavy tape, (c) a USB WiFi stick, (d) tin snips, and (5) a USB extension cable. For detailed instructions on building your own wireless signal extende...

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

A major software tool first promised during the reveal of the HoloLens 2 earlier this year is finally available.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

The Pixel 2 and Pixel 2 XL were built by different manufacturers. This is pretty common knowledge among Android fans at this point — Google's smaller Pixel 2 was built by HTC, while the larger Pixel 2 XL was built by LG. What would the Pixel 2 XL look like if HTC had followed through and delivered on the larger phone for Google? Today we have some answers.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Building virtual portals are popular practice for developers to demonstrate the "wow" factor of augmented reality.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.