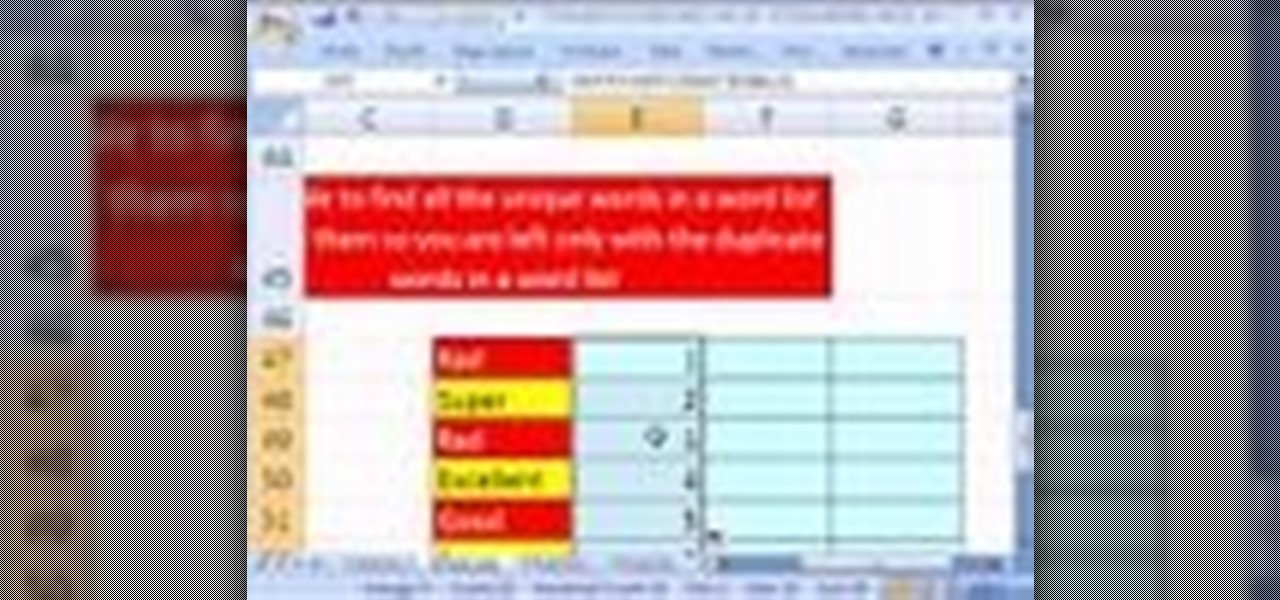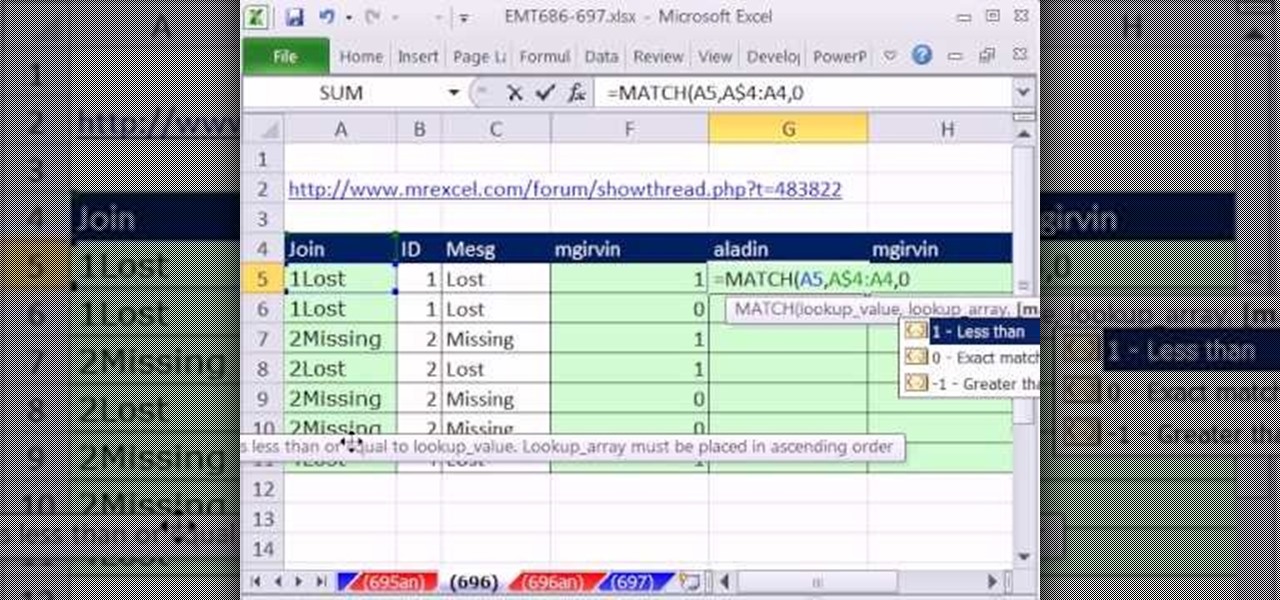
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 697th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a column of 1s and 0s (ones and zeroes) where 1 indicates the first occurrence and 0 indicates any remaining duplicates.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.
This video will show you how to use the ‘find’ and ‘replace’ text buttons in Microsoft Word 2007. Microsoft Word 7 is slightly different from the Microsoft you might be used to but with these instruction you’ll have no problem finding the buttons.
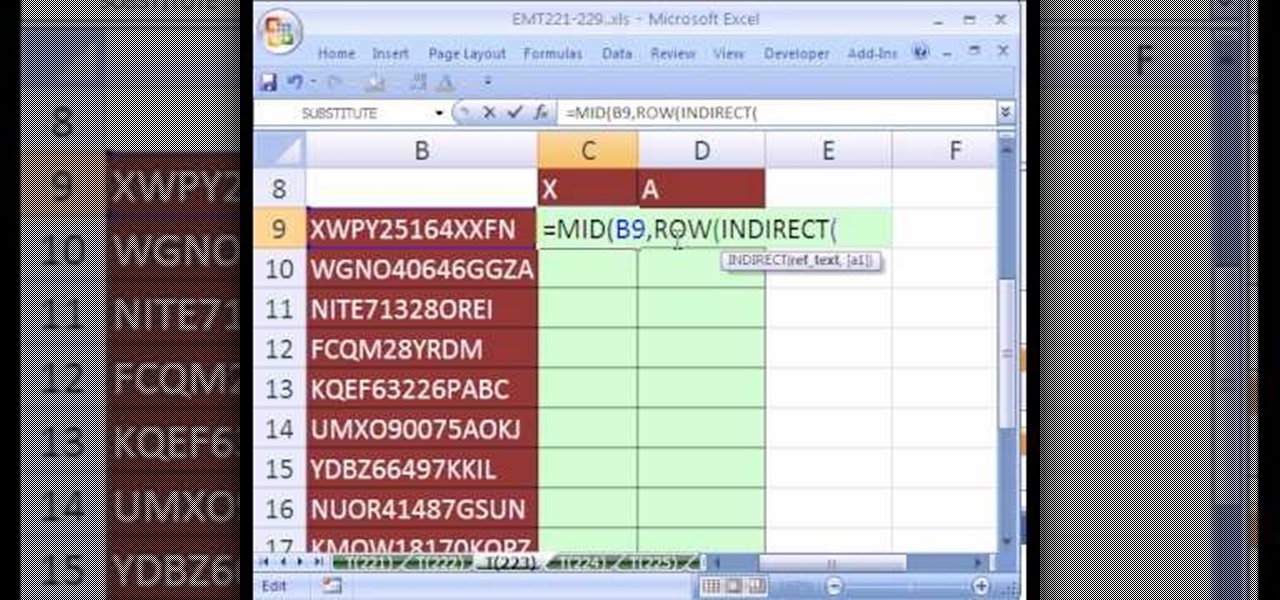
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 223rd installment in their series of digital spreadsheet magic tricks, you'll learn how to count individual letters in a word. See how to count the occurrence of a given character in a text string.
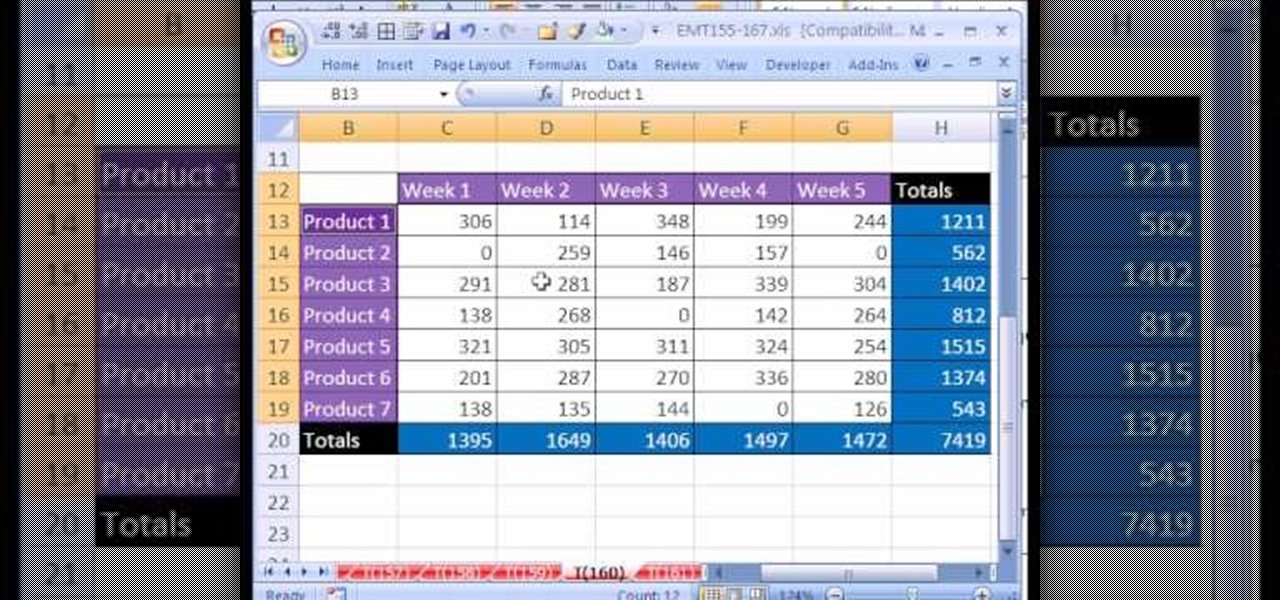
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 160th installment in their series of digital spreadsheet magic tricks, you'll learn how to find all the occurrences of a word, number, format or formula and then change or replace all of them! See how to use the Find and Replace feature in Excel with this free video tutorial.

In this tutorial the instructor shows how to convert a improper fraction to mixed number. In the example the instructor takes the denominator of the mixed fraction and writes it beside and keeps adding it self to the latest number and he keeps on doing that way generating a series until he reaches the value of the numerator. Now he counts the number of occurrences of the numbers in the series before the value of the numerator which gives the value of the whole number in the mixed fraction. No...

If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 20th installment in his "Excel Statistics" series of free video lessons, you'll learn how to take raw quantitative (numerical) data and figure out how to group it into classes so that you can have categories an...

Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 32nd installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to use the MATCH & ROW functions to create a logical test to find the first occurrence of items in a list with duplicates.. Learn to love digital spreadsheets more perfectly with the tricks outlined in this free Microsoft Office how-to.

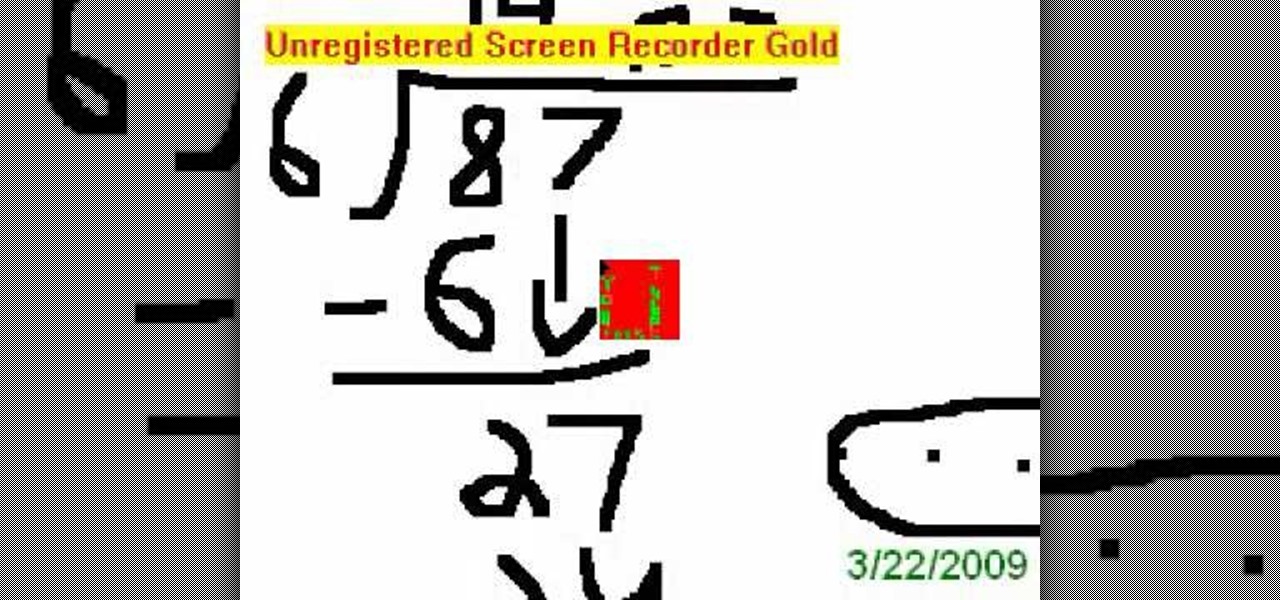
This video goes through the step by step process of doing long division with remainders. Multiple examples are used throughout the video to give the viewer a better idea of how to properly complete the difficult task. Perfect for anyone learning long division for the first time, or for anyone attempting to relearn long division after forgetting how to do the process (an all to common occurrence in a world with calculators on every cell phone).

The drum support rollers are usually in the same spot on every dryer, no matter the brand. They will be below the drum. In order to remove the rollers, you need to open the dryer's cabinet and remove the drum. Perhaps you will notice that the left roller is more worn out than the right one. This is a common occurrence, but you need to replace both at the same time. Be sure to remove the nut before you remove the roller. Don't use more than one drop of oil on the hub as too much oil will aid t...

Need to break out of the restrictions your school or workplace have on internet browsing? Maybe you want to waste some time on YouTube, check out some gaming action on Twitch, or simply just browse Facebook or Twitter.

When attending networking events, a LinkedIn exchange is a common occurrence. Equally common is the awkward fumbling dance with how to add each other. Fortunately, we have the solution: the ultimate way to add LinkedIn contacts.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

While intestinal gas is a normal occurrence within the digestive process, it can also cause bloating, burping and flatulence. Follow these tips to remedy the problem.

Watch how the F5 Networks BIG-IP Edge Client solution gets you connected automatically when you boot/start up your computer along with seeing the browser based version of the F5 BIG-IP Edge Gateway. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Learn how to use the BIG-IP Edge Client and its Smart Connect, Location Awareness, Customization, Deployment features. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

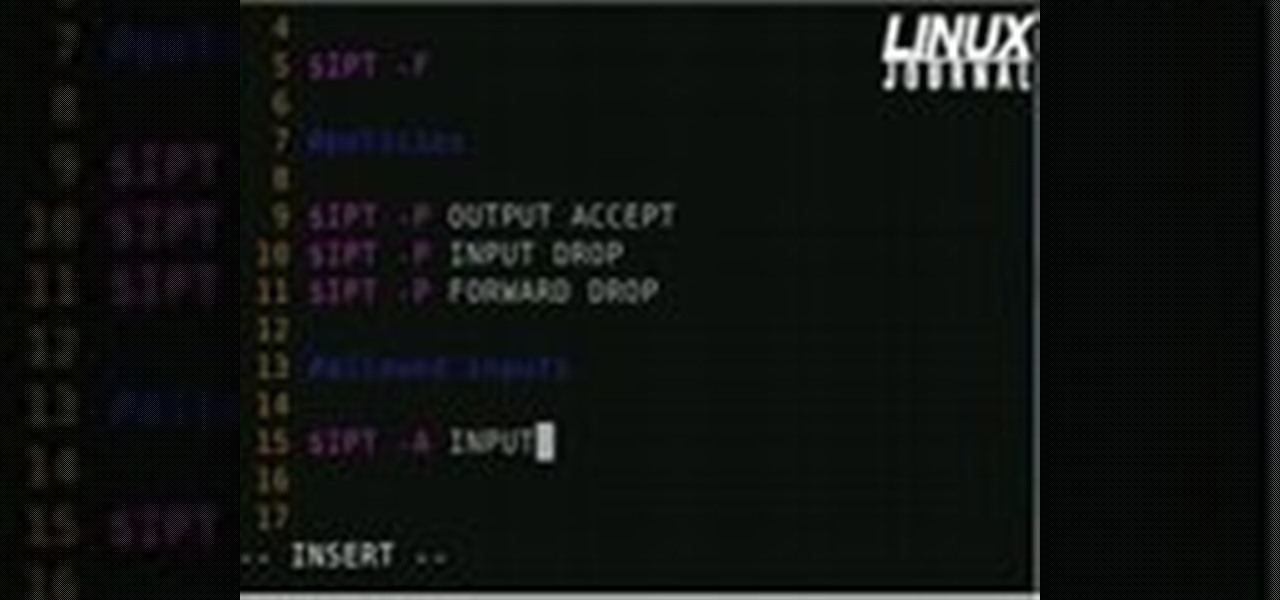
Linux comes with a powerful built-in firewall, although the interface can be a little intimidating. With this multipart GNU/Linux networking video tutorial, you'll master basic and not-so-basic IPTables functionality and create the perfect firewall for your home network. For detailed, step-by-step instructions, watch this Linux how-to.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

This clip discusses how authorization roles work and their role in the security of the latest release of the F5 Networks Management Pack suite. It also touches on the creation and use of user roles within Operations Manager console and how to apply the authorization tasks to those roles. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with F5 Networks Management Pack suite, you're sure to benefit fro...

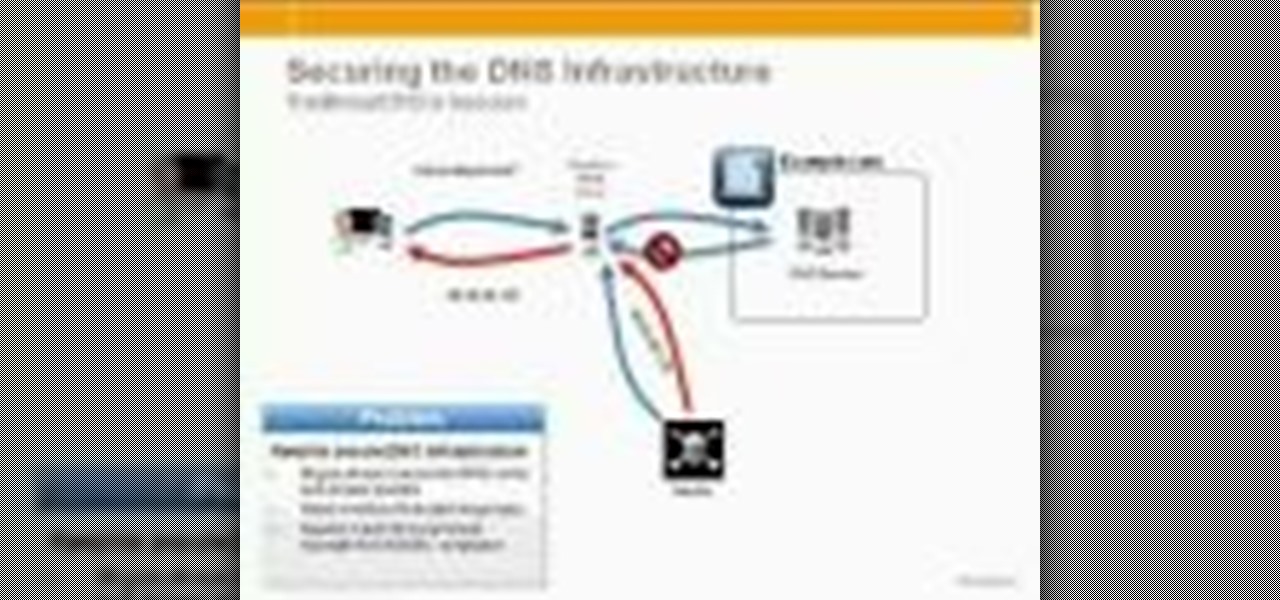
In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

See how to use the PCI compliance reporting functionality within BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

See how to enable Layer 7 DoS and brute-force protection within DoS within BIG-IP ASM. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

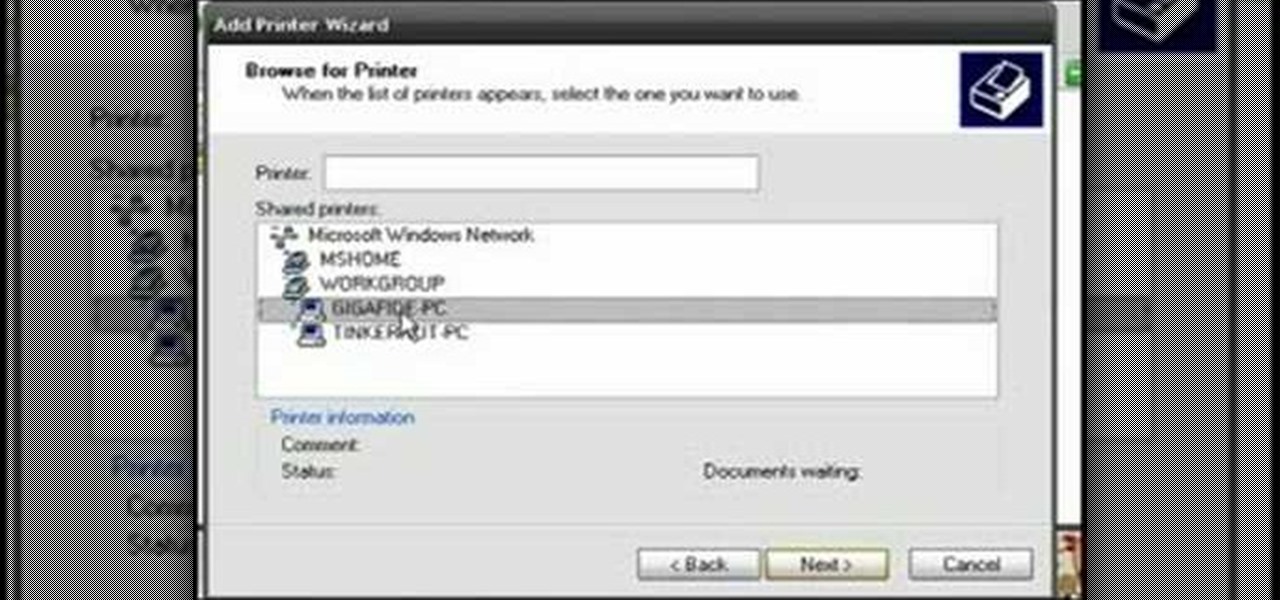
Odds are you have more computers on your network than printers. This video lays out the steps for sharing a printer over a network. This tutorial assumes that the printer is installed on another computer and not connected directly to the network. Take a look!

No wireless router? There is a way to network your computers by using your existing power-line. This CNET video will show you how to set up a power-line network - it's not as sexy as a wireless network, but it's easy and reliable!

Although it is a rare and potentially frightening occurrence, knowing how to do a system restore in Windows XP is an important thing to know how to do. To get started with a system restore, select the Start menu in the lower right of your screen. Then select All Programs. Then from the All Program menu, select Accessories and then from Accessories, select System Tools. There are several items under System Tools, but you want to select System Restore. You will follow through the next few scree...

In this tutorial the author shows how to find out a Cool XP Easter Egg hidden in the XP which comes by downloading the latest update of widows update. The author now opens Internet Explorer and visits the windows site. Now he quits the explorer and holds down both the Control key and alt key and right clicks on the desktop seven times. Now keeping the control key pressed, he releases the alt key and right clicks the desktop and chooses the option 'Create ShortCut'. Now he releases all the key...

Here are several bizarre occurrences that are believed to have happened all over the world. You gotta hear about these!

While the concepts of molecule interaction, zero force and energy states might be a little beyond an elementary school science fair's scope, the basic idea of water's capabilities and naturally prepared access to animals and insects that rely on it as a habitat is certainly worth the time. Learn how to duplicate this natural phenomenon in this free video clip series with our expert Scott Thompson as he demonstrates the occurrence of water skin or skin tension, and shows you and your children ...

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

Since its release into the arms of waiting developers, Apple's new ARKit is already making waves in the augmented reality scene. Only a week out and there are already a hefty number of videos appearing on the web showing off various demos with iPhones and iPads.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

Check out this video tutorial on how to hack into WEP encrypted wireless networks. The aim of this video is to show people how easy it is to crack a wireless network with WEP encryption. Seriously, if you know how to do it, even a little kid could if you showed them how. Now that you know this, you should upgrade to WPA! It is much harder and takes much longer to crack.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.