Do you have an old computer that may be too slow to play video games? You may think it's totally useless, but CNET Video teaches you how to turn it into a network server that functions as a centralized depository for your files!

Most oil cooler kits cost $250 or more, but the guys at Poor Man Mods show you how to make your own oil cooler for only $60! Oil coolers are great security for longer lasting and better performing engines, especially high-performance engines and in warmer climates.

In this tutorial, you'll learn about the cables required for setting up a small home or office network. Fortunately, cable selection is an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this clip, you'll learn methods for troubleshooting and resolving the most commonly encountered WiFi wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.
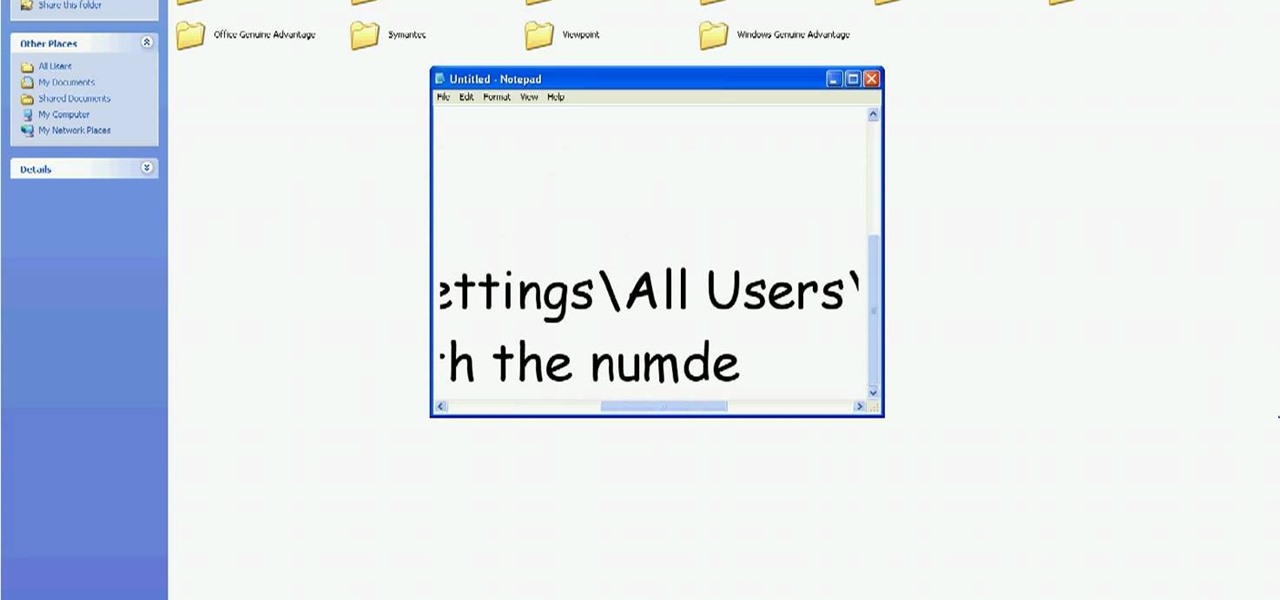
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...
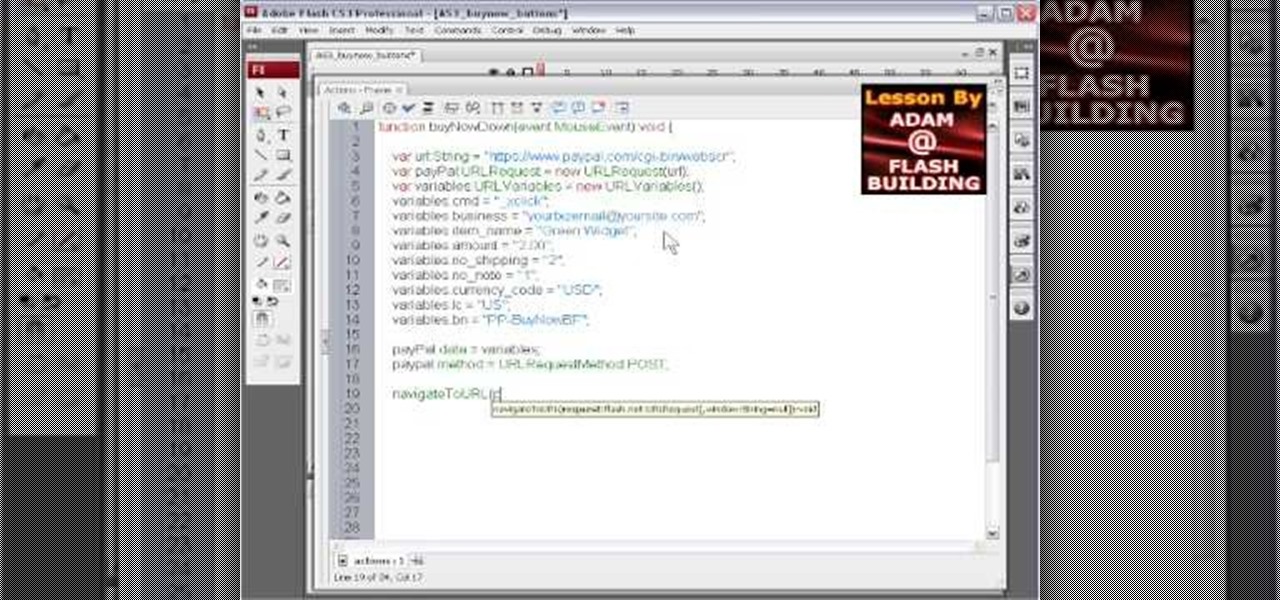
Add an extra level of security to your website by creating your own dynamic 'Buy It Now' button for PayPal-using visitors to your website. Coding this button is very easy, and you can even animate it to draw more attention to your webstore.

In this clip, you'll learn how to set up a simple wireless network in a home or office. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started making phone calls over your own Internet connection, watch this handy home-computing how-to from the folks at CNET TV.

Need a hand figuring out how to set up a wired home LAN network? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

Interested in setting up a network over your power line? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started setting up your own home network, take a look.

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.

In this tutorial, we learn how to set up an HP wireless printer. First, click "setup" on the printer, then go to "network", then "wireless setup wizard". The printer will now go through the setup process and show you available wireless networks in your area. If your network requires a password, enter it by typing it in with the keypad. Now, install the software to any computer and wait for the blue wireless light to turn on. When this is done, you will be able to print wirelessly from any com...

Learn how to use BIG-IP Live Install on F5 gear quickly and simply. Learn how to upgrade BIG-IP with Enterprise Manager 1.8 quikly and simply. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed, step-b-step instructions, and to get started using Live Install yourself, take a look.

Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

Need to install a pre-hung door? Lowe's has your back. A quality front door makes a positive first impression on guests... not to mention, a weathered and worn door can compromise your family's safety and security. In this video, learn how to install a new pre-hung exterior door with the following instructions from Lowe's.

Remote desktop is a windows feature which can be used to access a windows computer from an other windows computer over the internet. Note that to access a windows computer using remote desktop the computer must run on Windows Professional or Ultimate version. Remote desktop does not work if the remote computer runs on Windows basic home version. However you can remote from a computer that runs on home version of windows. Another requirement is that the two computers must be connected over an ...

This video shows how to do a remote desktop connection from a new Windows 7 to a older Windows XP or Vista. With Remote Desktop Connection, you can access a computer running Windows from another computer running Windows that is connected to the same network or to the Internet. This feature from Windows easily enables you to get old files from Windows XP or Vista if you need to view or print documents. This feature is free from Windows and is built in the operating system. Once connected throu...

iPod and iPhone home automation remote control using Girder is only an install away. Run the lights, heat, security system among other things in your space age home for the 21st century. Make your home a modern marvel with this app for iPhone.

In this installment from the Unorthodox Hacking series of computer security tutorials, you'll learn a number of methods for hacking Windows shares as well as means of mitigating those hacks. For detailed instructions on Windows shares, and what you can do with them, watch this helpful video guide.

How to create and map a network drive using XP home.

A basic overview of how to setup a wireless network on a Mac.

In this episode, Brandon Jackson joins D.Lee Beard to present an in-depth review of the Slingbox A/V, explore where to find free downloadable audiobooks online, and to answer viewer questions on using an iMac as a display and how to share files over a local network between a Mac and a Windows PC . Be sure to check out our next video to learn how you can win the Techies' Slingbox and begin watching your home TV from all over the world via the internet.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Google's monthly Android security updates are generally welcome—at the very least, they provide a feeling of security that our device is now somewhat safer than it was 30 days ago. Vulnerability patches, slight enhancements to performance, and overall bug fixes are generally included in the monthly OTAs, but as it turns out, they're not always for the better.

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.
Welcome back Hackers\Newbies!

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

Most hardcore Android fans loathe carrier or manufacturer additions to the Android operating system. Whether it's bloatware or changes to the user interface, many enthusiasts prefer the clean look of stock Android.