
News: The Samsung Galaxy S4 Rumor Roundup (Live Updates)
*Updates* March 6, 2013


*Updates* March 6, 2013

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.
» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.
With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...
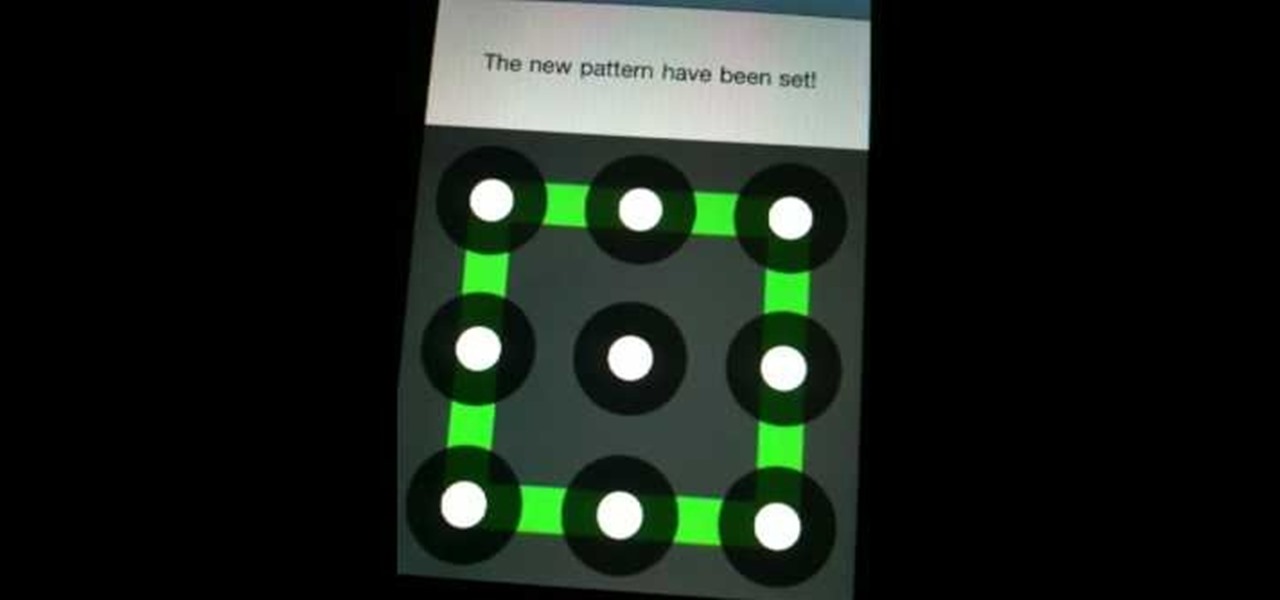
iPhone and Android both have a lot of great features. Enjoy the best of both worlds when you install Android lock on your iPhone. This is a great way to secure your iPhone. Use Android lock to get an extra layer of security.
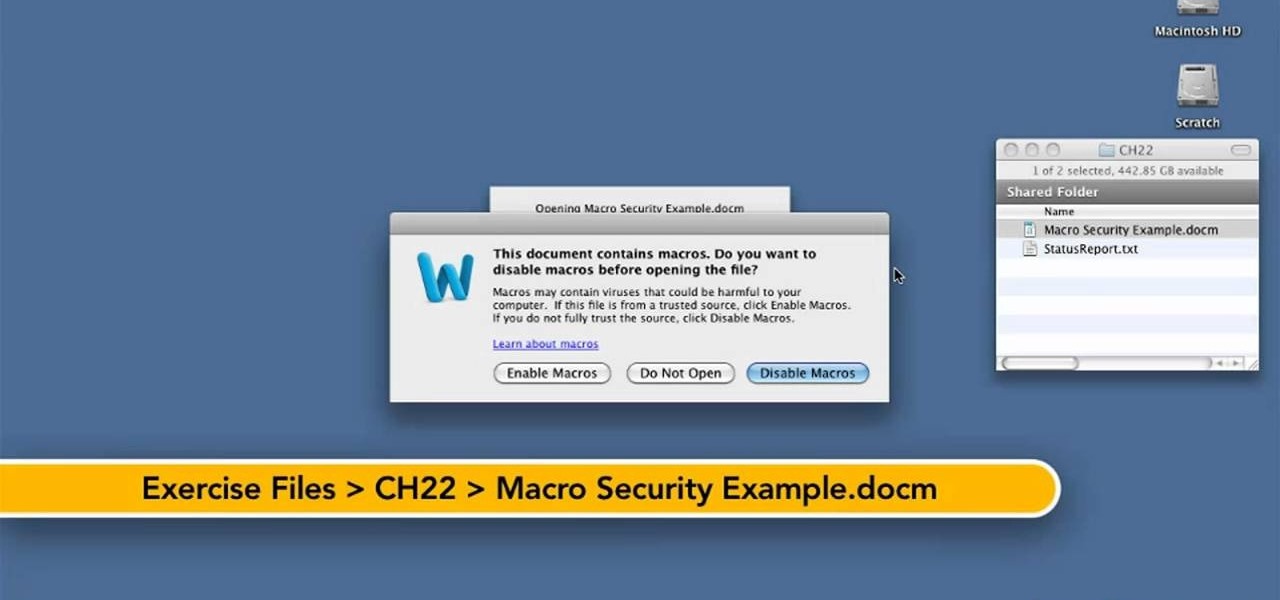
Want to know how to keep safe when using macros in Word for Mac 2011? This video will show you how it's done. Whether you're new to Microsoft's popular word processing application, new to MS Word 2011 or even an expert merely looking to brush up on the fundamentals, you're sure to be well served by this quality video tutorial from the folks at Lynda. For detailed, step-by-step instructions, watch the video.

If you have children who are still your dependents and have been living in your household for at least half of the year, and have their own social security number, you can actually get a major tax credit with a simple worksheet. In this video you will learn the requirements for the tax credit and also how to fill out the worksheet and calculate your credit.
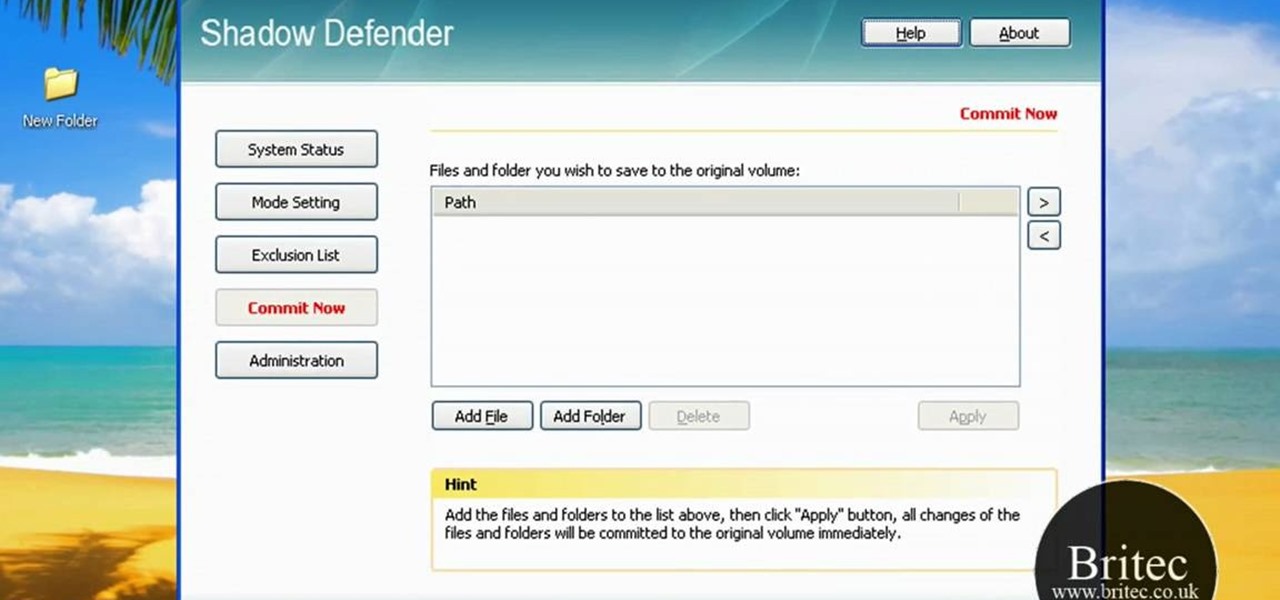
Looking for a security solution for your Microsoft Windows PC? With Shadow Defender, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions on how to get started using Shadow Defender to protect your own desktop computer or laptop, take a look.
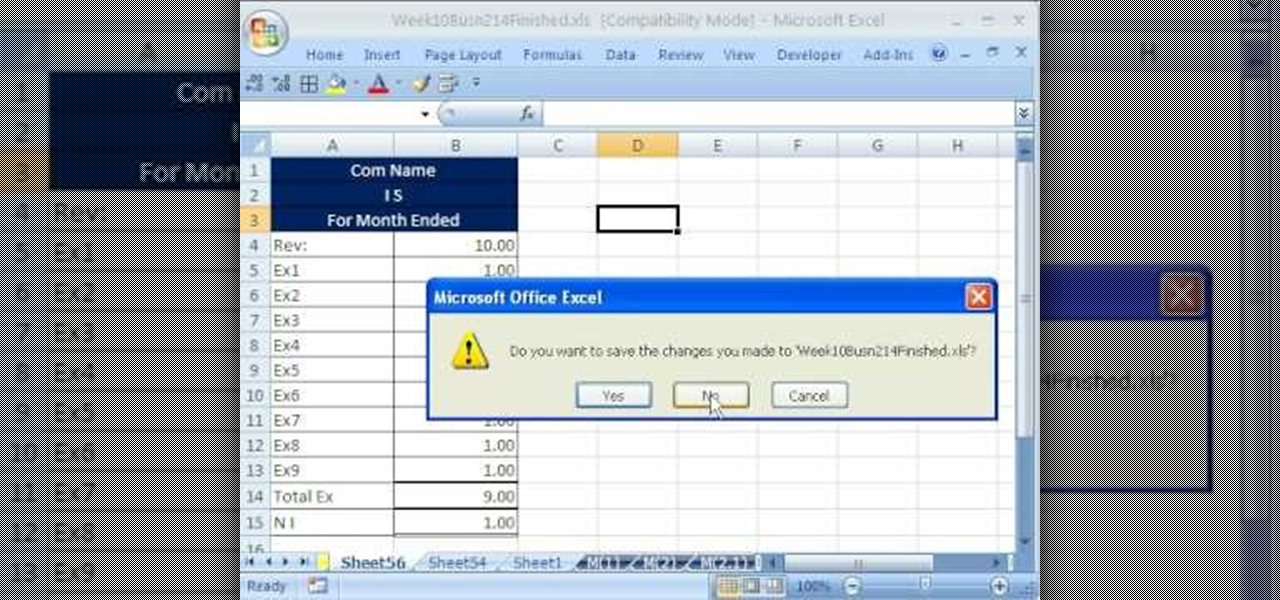
hether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 52.5th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about macro security. For more information on how to use macros safely, watch this free video guide.

Take a folder and organize documents based on the actions required. Actions:
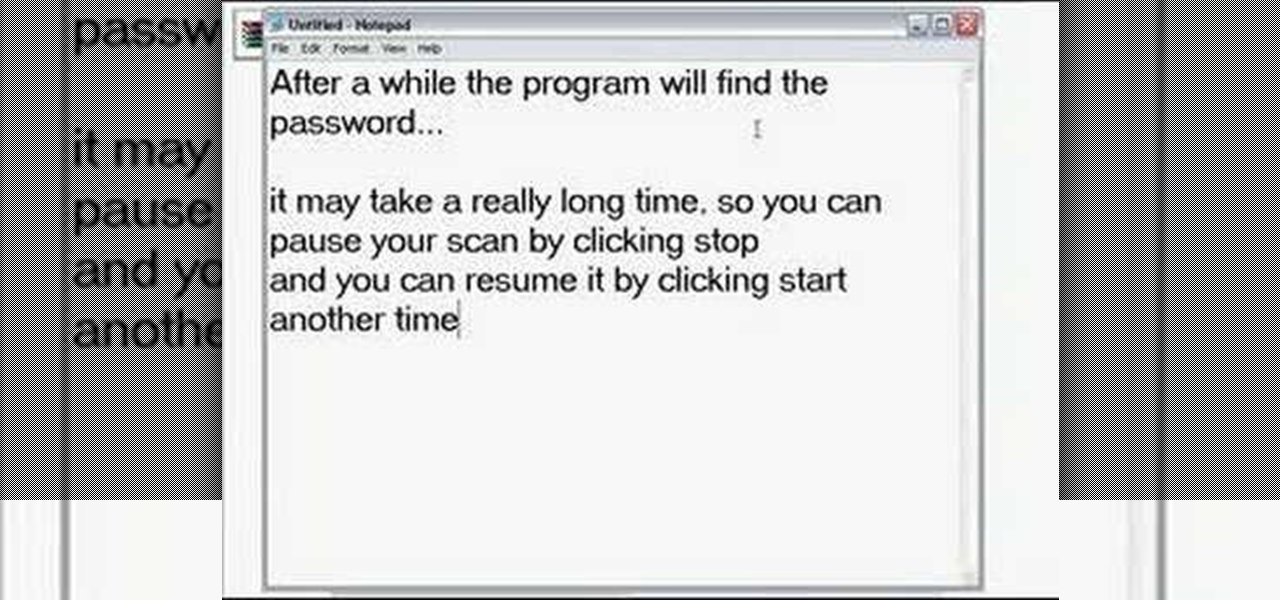
What do you do with a password protected WinRAR archive? You hack it - naturally. And how do you hack it? First, download RAR Password Recovery v1.1 RC17 then follow along with this video to crack almost any WinRAR password. So much for security.
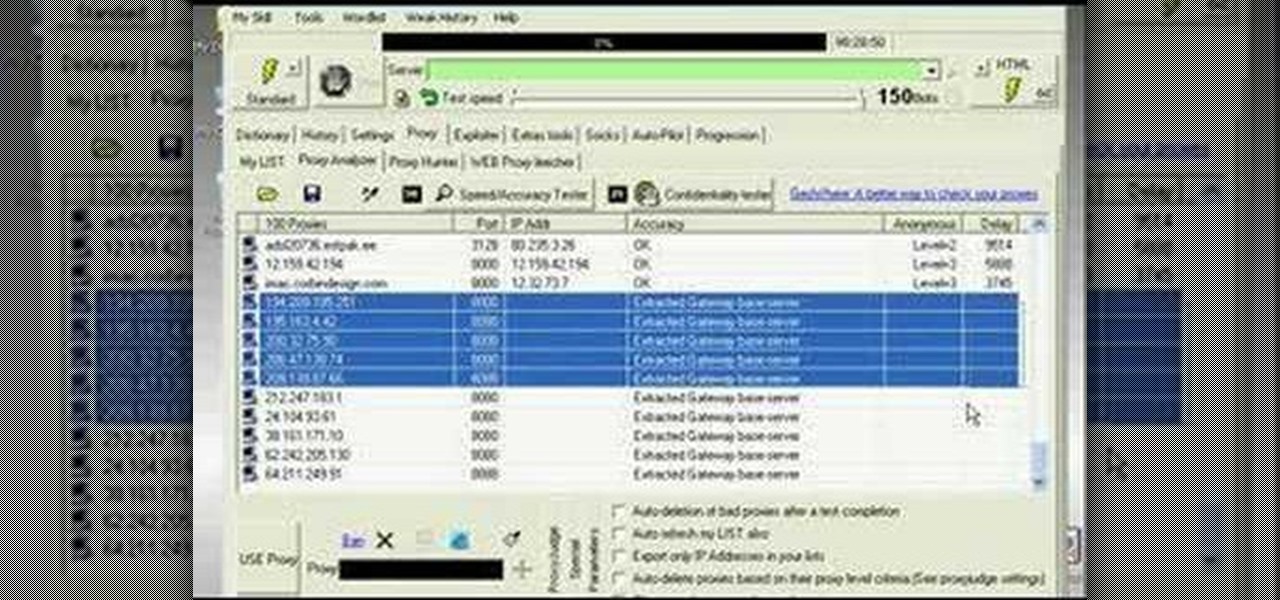
AccessDiver is a website security scanner. It incorporates a set of powerful features that will help you to find and organize vulnerabilities and weaknesses in your own site. This video tutorial presents a guide to its use. For more information, as well as to get started using AccessDiver for yourself, watch this video tutorial.

Did you know that field templates can be applied two different ways? And that the two "edit" buttons on the main interface tie directly into how these field templates are used? This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite discusses these topics and how to control such permissions through security roles.

There is a security flaw with any Apple iPhone running firmware version 2.0.2. This flaw potentially gives a person access to your email account and contacts when you have your iPhone locked. This video demonstrates a simple, but impermanent, fix for stopping others from accessing your private information. To protect your own Apple iPhone, watch this tutorial.

Dogs naturally want to have a den, so a crate gives him his own space. Puppies will get security and comfort from a crate. Because a dog will not want to go to the bathroom where they sleep, they won't make a mess in their crate, making it useful for housebreaking a dog. Watch this video pet care tutorial and learn how to crate train a dog.

In this how-to, Gary Rosenzweig of MacMost.com takes a look at best practices for making and storing passwords. You should have a different password for every account, for example, use secure passwords and store them in using a security utility. Learn how to store your passwords securely with this tutorial.

I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

Professor of RVing, Jim Twamley talks about lock security and shows you how to replace an RV entry lock.

How to get around your school or home's computer security to view restricted webpages.

This Video demonstrates how to install multi channel (4,8,16) power supply for security camera and CCTV installation.

Watch this video to learn how to make a radio controlled camera rig that can tilt and pan like an expensive security camera. This is an amazing tool for movie making! Stick to your budget.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.
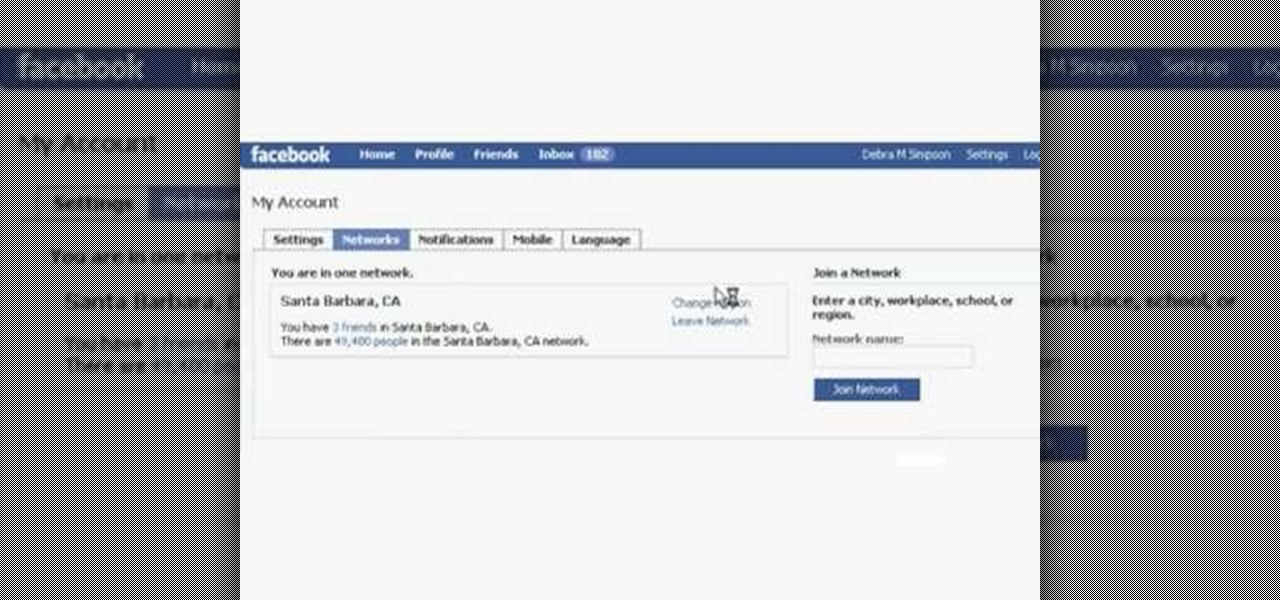
Magicinwords teaches viewers how to change their facebook network! First, you will want to log onto Facebook.com. When signed in, go to the settings tab on the right of the screen. Under this, click on 'account settings'. Under account settings choose the tab that reads 'networks'. Here, you can click 'change your region' and then you can update it. Be sure this is right though, you can only change your regional network twice every 60 days. Under this same tab, you can also join any other net...

Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you.

Ever since the iPhone X, Face ID has been the standard way to unlock your iPhone. For the most part, it works remarkably well and adds a layer of security that Touch ID can't match. That said, the tech isn't perfect. If you're finding that Face ID isn't working for you, there might be an iOS setting to blame.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.
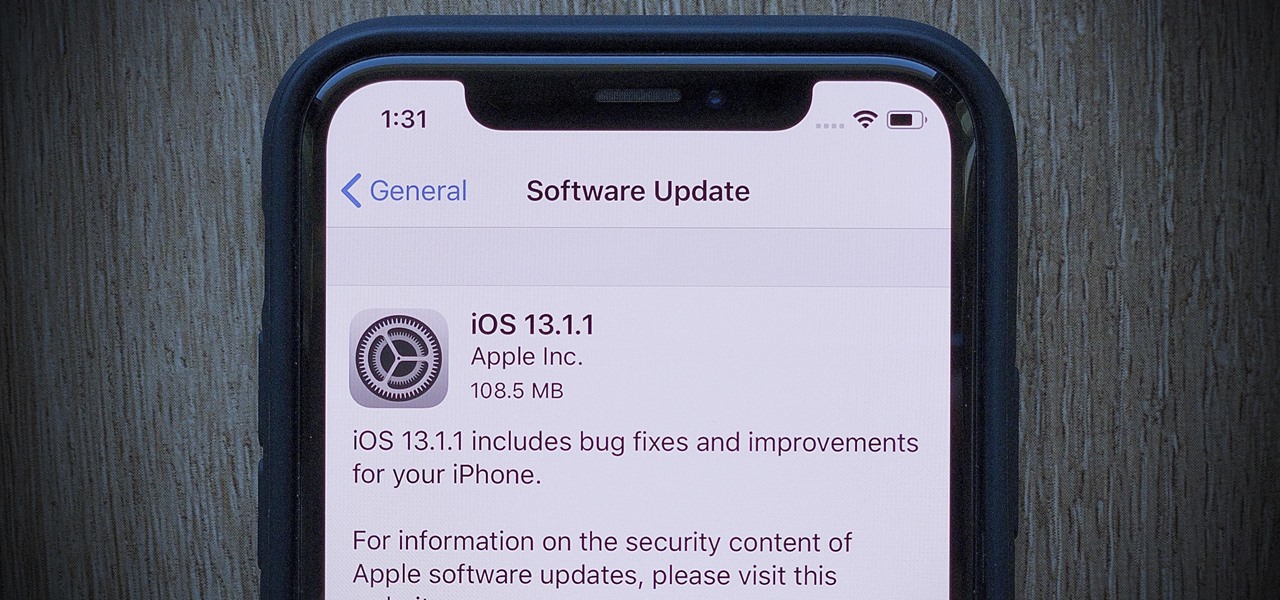
Is Apple trying to set a record for the highest number of updates within a two-week period? You wouldn't be blamed for thinking so. Just eight days ago, Apple publicly released iOS 13.0 for all compatible iPhones. Then, just five days later, Apple seeded iOS 13.1 with 22 new features to boot. Now, just three days into 13.1's tenure, Apple has released yet another update, iOS 13.1.1.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.
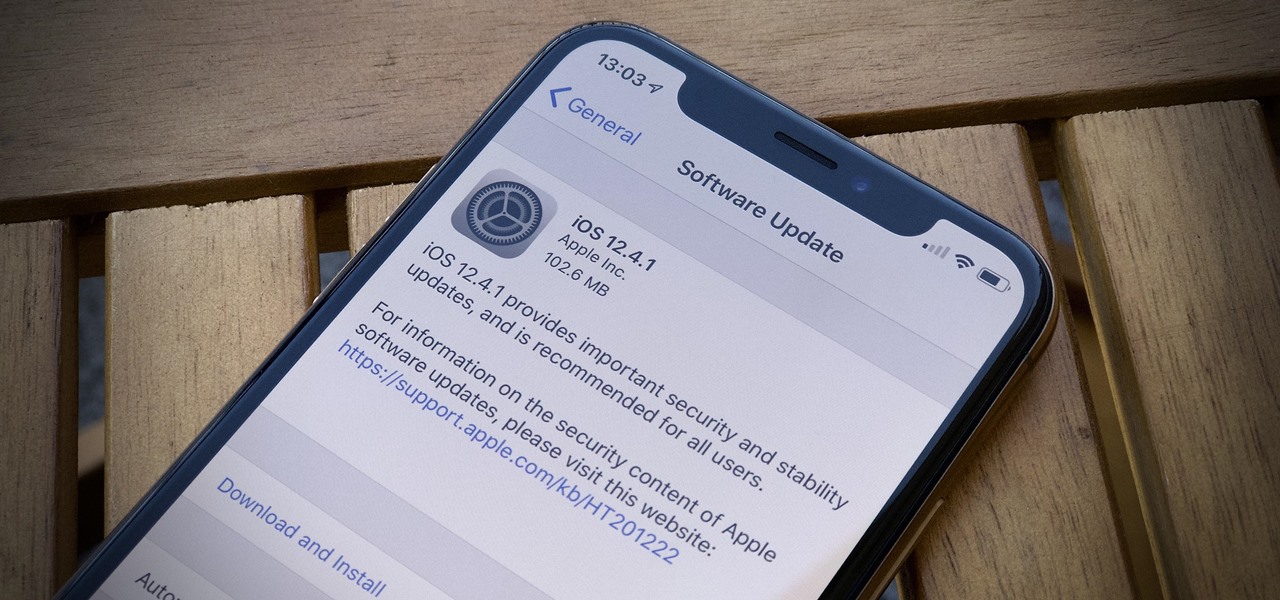
While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.
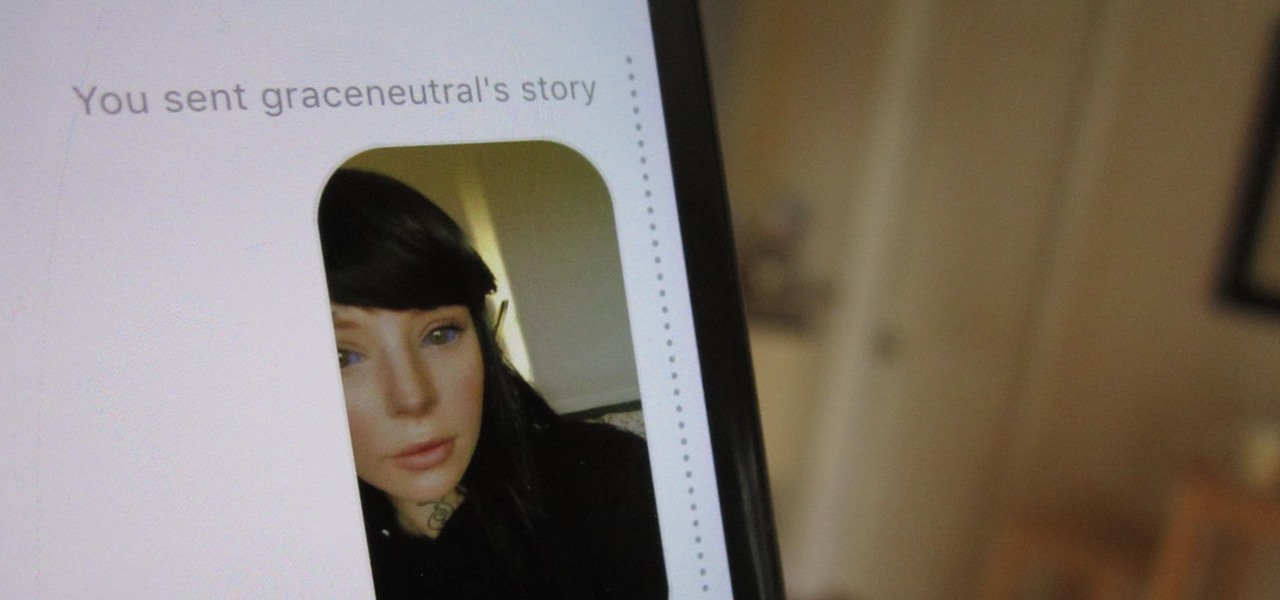
Instagram introduced a new feature in September 2018 that lets you share other users' Stories via Instagram Direct, the app's private messaging tool for solo and group messages. Problem is, it works both ways, so whenever you add to your ephemeral Story, everybody that sees it can share it directly with anyone else.

Get ready for more software testing. Just two days after the official release of iOS 12.1, Apple seeded public software testers iOS 12.1.1 — one day after developers received the update. While the rest of the iOS world is just getting to know all of the cool, new 12.1 features, testers are now sinking their teeth into what the next iteration of iOS has to offer.
While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.