It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...
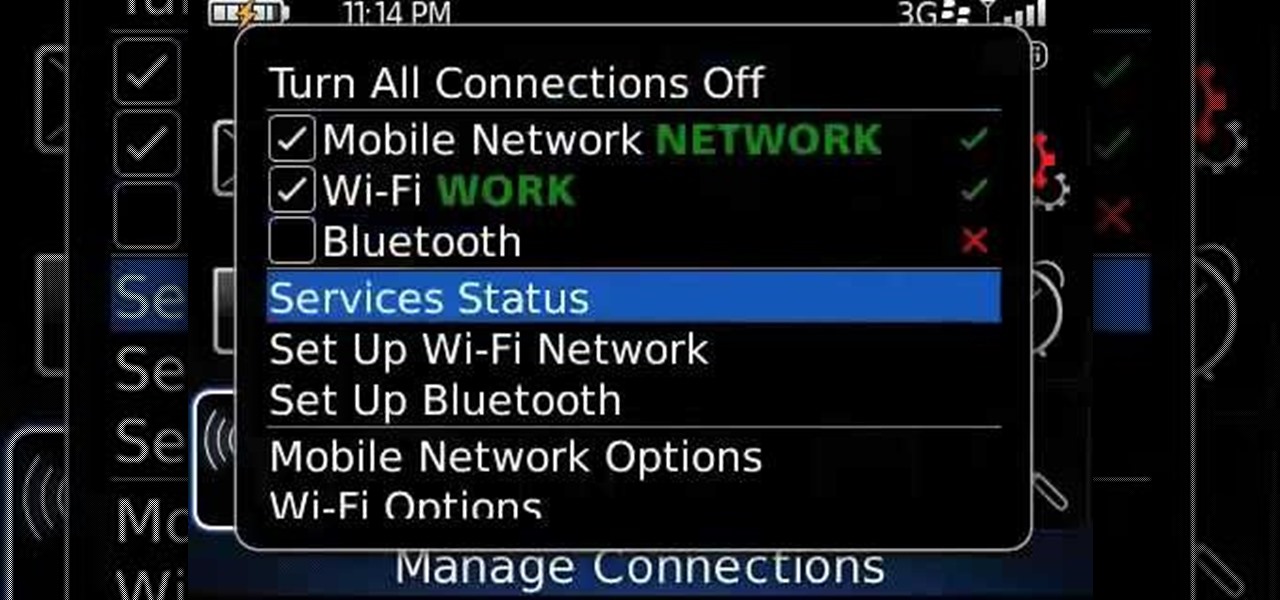
Learn how to manage your network connections through the Mobile Network Options pane on a BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.
Watch how to configure LDAPS Authentication on the BIG-IP Edge Gateway with BIG-IP LTM functionality. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

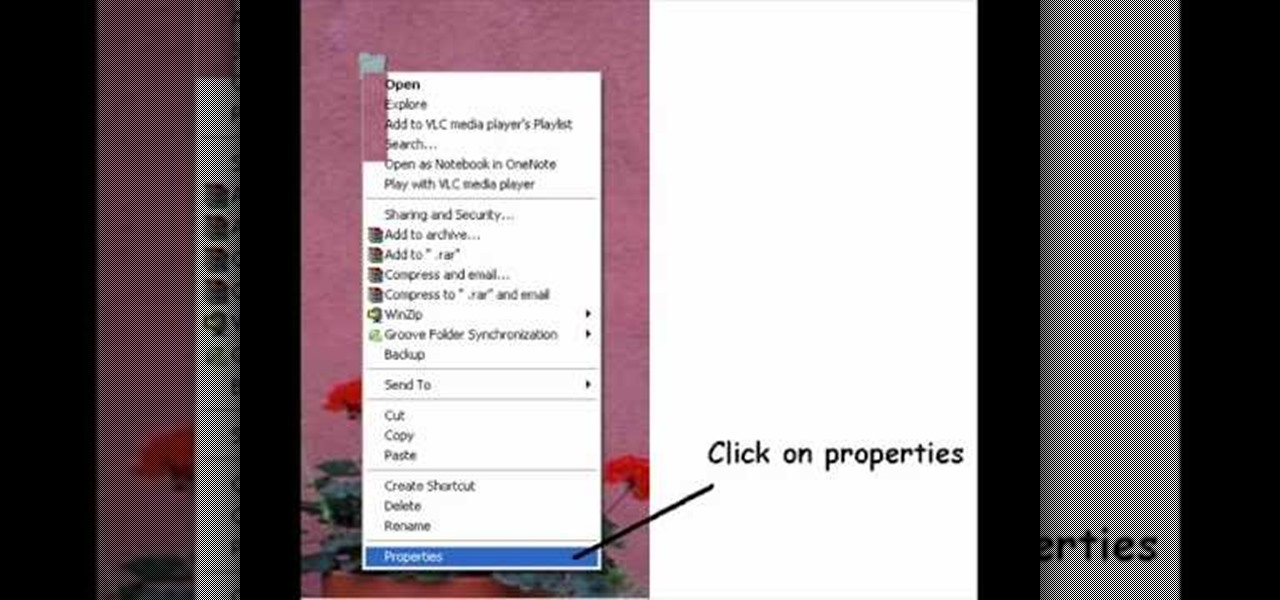
This video shows you two methods to connect to XBox Live using a laptop. For the first method, go to your start menu and open up your control panel. In the control panel window find the area marked Network and Internet and select the option View network status and tasks. In this new window, select Change adapter settings in the left hand pane. You will be presented with another window that has your network connections listed. Right click on your Wireless Network Connection and select properti...

This video shows you how to set up XBox Live using a laptop and Ethernet cable. The materials you will need are an Ethernet cable, an Xbox 360, and a laptop or desktop computer. First, you will need to connect your computer to your wireless network. Next, you must connect your computer to your Xbox 360 using your Ethernet cable. Power up your computer, go to the start menu and select network. In the window that appears, select the Network and Sharing Center located below the address bar. A ne...

In this video the instructor shows how to map a network drive in Microsoft Windows XP. Network drive is similar to the disk drive that is present on your computer like C drive, D drive but instead of pointing to a hard disk on your computer it points to a server that has enabled shares. Shares allow you to create or edit files and folders. By mapping that server share to a folder in XP you can use that share as a normal drive. To do this go to start menu, right click on My Computer and select...

In this video the tutor shows how to sign on to the Playstation network using Playstation 3. To connect to a Playstation network you will need a PS3 Controller and the PS3 itself. First signing on to the system, go to the System Settings. Then go to the network settings and you will need to configure your internet settings as shown in this video. It shows the different ways connecting to an internet like in custom mode or advanced mode, also the wired or wireless option. Finally after connect...

Veronica from Tekzilla teaches you how to monitor network activity on Windows 7. Go to ITSamples and download the Network Activity Indicator program. Install it and run it. This will add a new icon on your system tray. It blinks to reflect incoming and outgoing packets. You can right click to see a more detailed report. You also get statistics and a menu for your network and firewall settings. So to get the popular windows XP type network indicator icon all you need to do is follow the steps ...

Take your desktop security to a whole new level by making your folders invisible! This video shows how you can make a folder icon disappear, so that the folder will hide in plain sight on your desktop. Use invisible folders to trick your friends!

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

If you're paranoid about the security on your web-browsing activities, fear not. This Firefox add-on, called HTTPS Everywhere, was created by the Electronic Frontier Foundation (EFF) to help you protect you from curious sites. Installing this add-on will make most websites default to the more secure version.

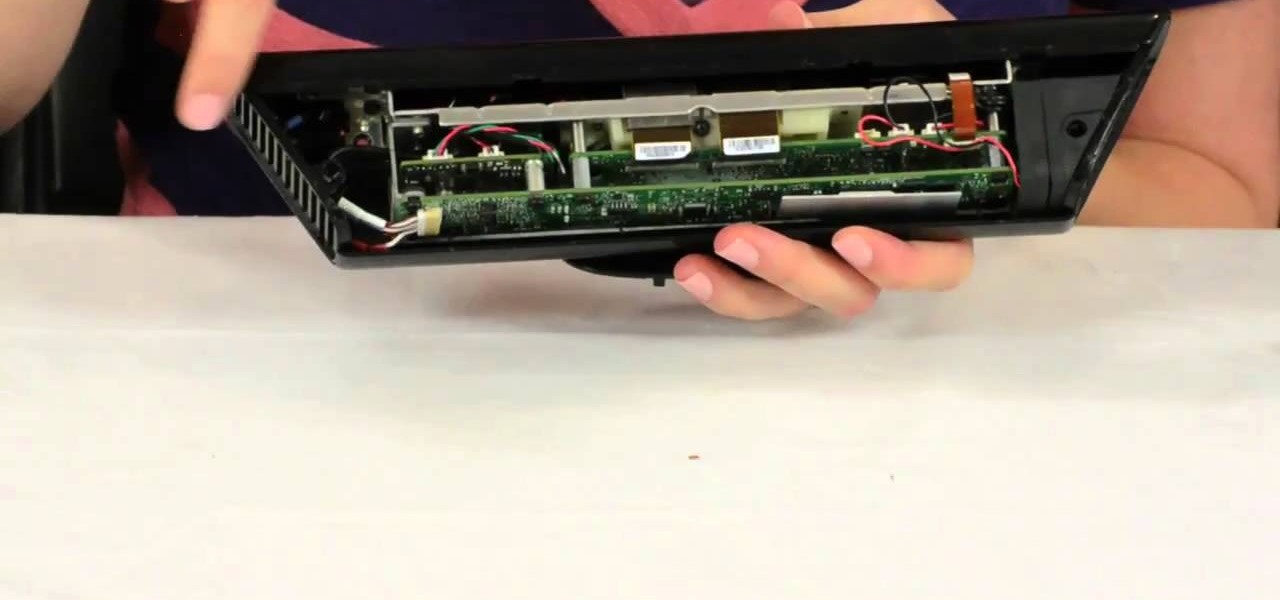
Microsoft's Kinect is gaining popularity with Xbox 360 owners, but what's really more fun? Playing games with this revolutionary hands-free gaming device or gutting the sucker to see what it's all about? We'll take the latter choice.

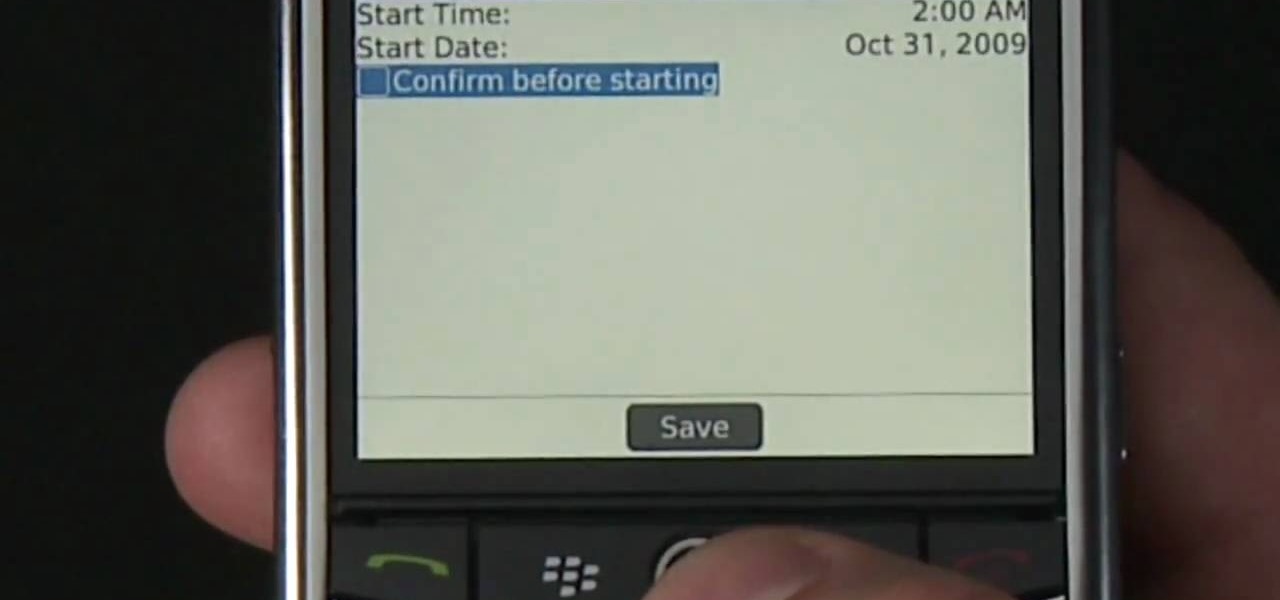
Learn how to update the software on your BlackBerry device over a WiFi or Wi-Fi network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

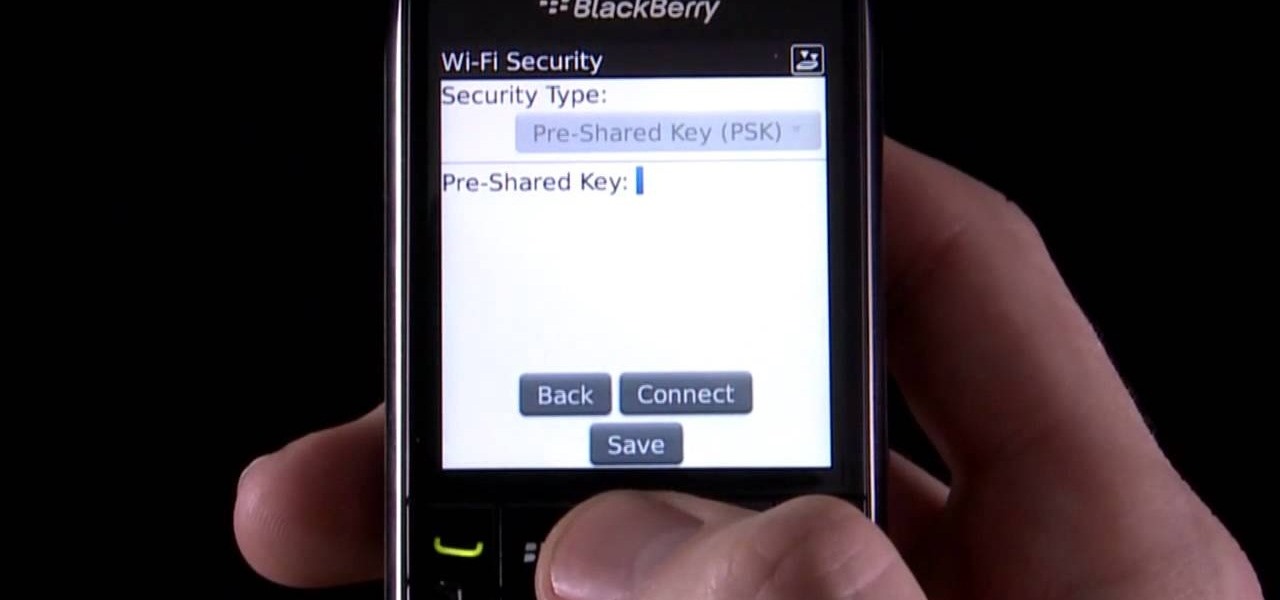
Learn how to discover and connect to close-by wireless (Wi-Fi) networks on your BlackBerry Pearl 3G. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to force your BlackBerry Pearl 3G to connect to a specific wireless (Wi-Fi) network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

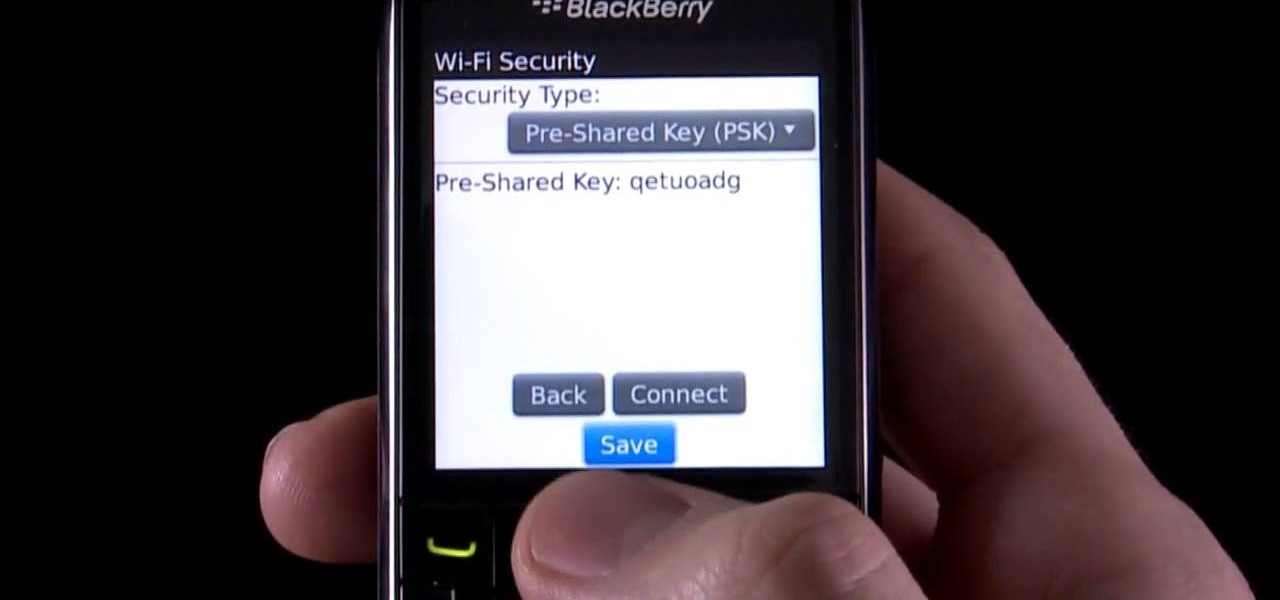
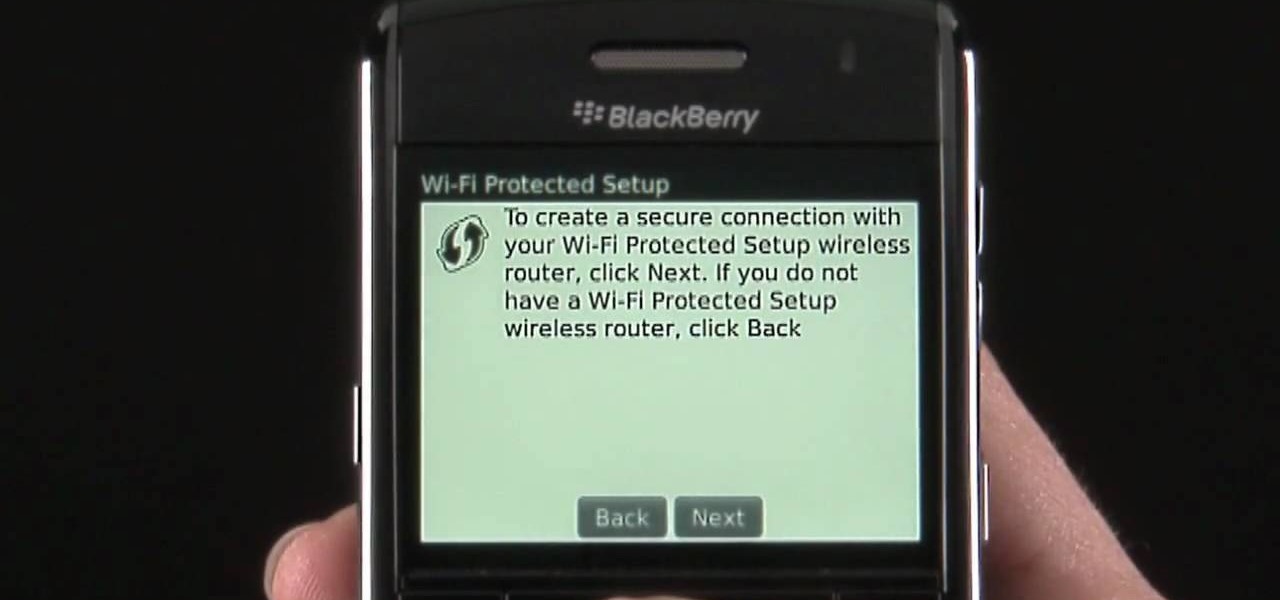
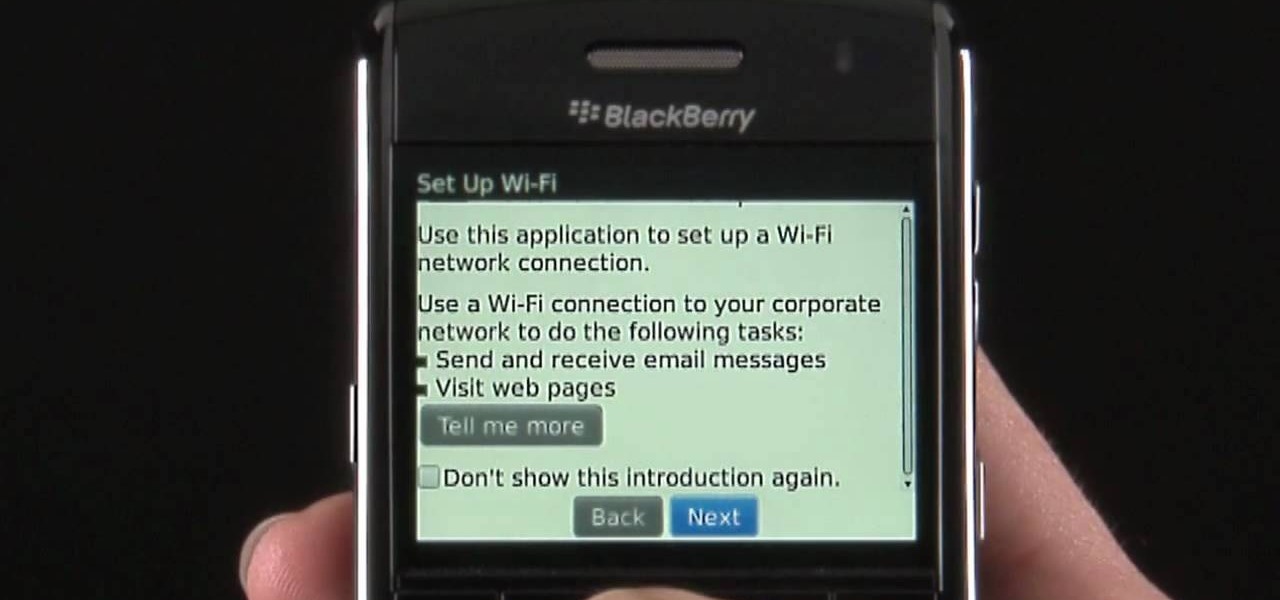
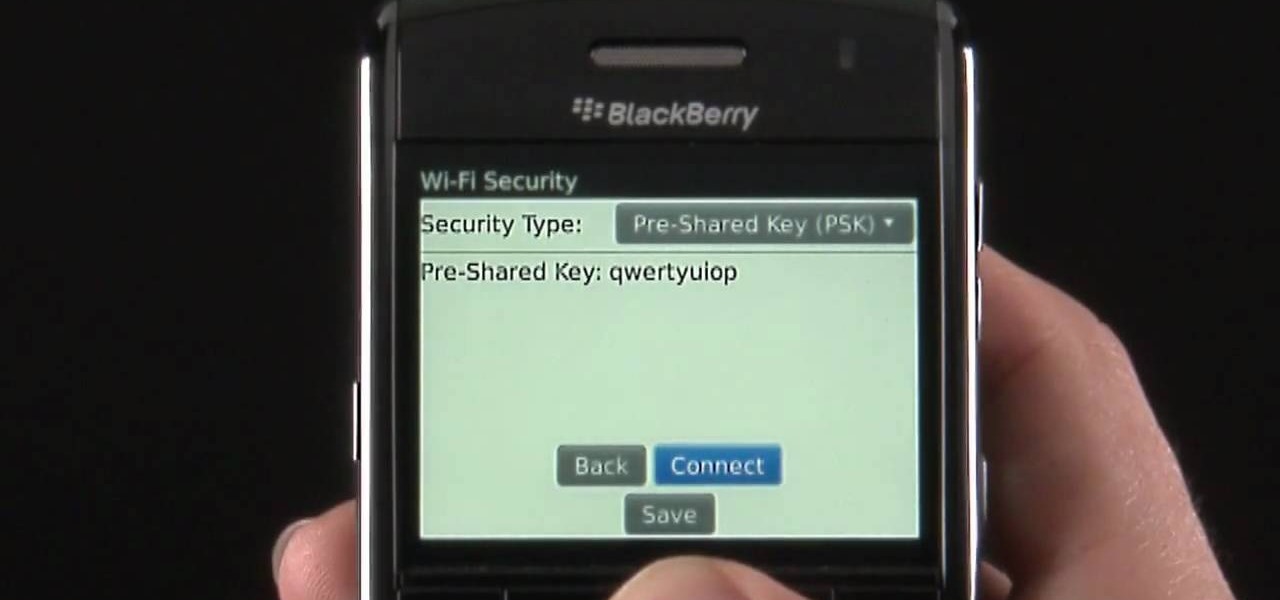
Learn how to use the Push-Button tool on your BlackBerry Bold 9650 phone to join a wireless network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to find open wireless networks with a BlackBerry Bold 9650 phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Want to know how to manually connect to a wireless network on a BlackBerry Bold 9650 phone? This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

The XBox 360 is a big, beefy console that can perform all sorts of multimedia tasks. Did you know that one of its many abilities allows it to play media files from a networked PC? This video will show you how to connect your XBox 360 to a network PC with Windows Media Player 11 or higher and stream movies and music from the latter to the former. Now you're much closer to maximizing the potential of that expensive little console you've got there.

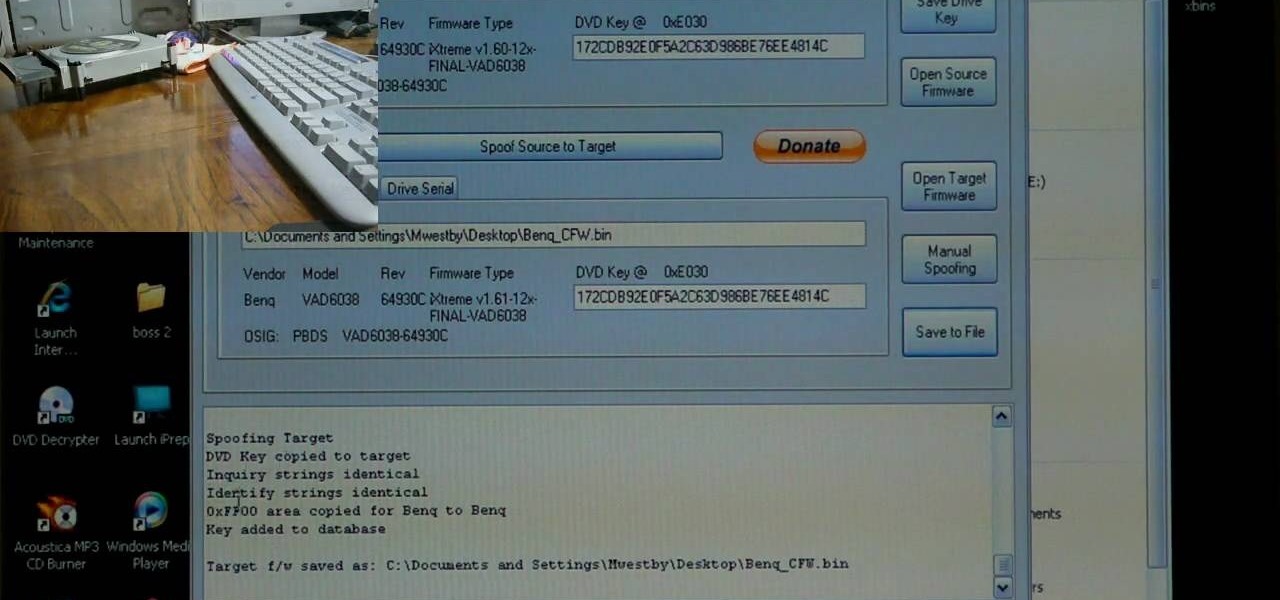
If you've already flashed your XBox 360's disc drive, then congratulations, you've accomplished the most challenging step involved in hacking you XBox. You aren't done though. As Microsoft keeps updating it's firmware to try and fend off hackers, you must keep updating your custom firmware to thwart their efforts. This video will show you how to upgrade your flashed BenQ XBox 360 disc drive's firmware to IXtreme 1.61 using Jungle Flasher 1.61. NOw you can play your burned games with a greater...

The Sony Dash is similar to an iPad and works like a PC without a keyboard. In this tutorial, learn how to connect your Dash to your home wireless Internet network so that you can go online and download updates. This clip comes straight from the pros at Sony and tells you everything you need to know about accessing WiFi on your Sony Dash.

Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

Installing a peephole in your home's front door can give you and your family a sense of security knowing who comes to your door before they enter. In this video Barbara K will show us exactly how to install a peephole on your door.

When you need a website to showcase your product or service, it can be quite confusing. Follow these easy steps to gather everything you need to have a successful website. Start your search for a domain name in the domain name registrar. (Example: www.companyname.com) Rent space from a hosting company to hold the files for your website. Set up an email account for your company. Create the content for your website (example: products, prices, services, etc). Get internet security to protect sen...

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

Not a great lock picker? Well, get some help figuring out how to break into padlocks and high security locks -- check out this video tutorial on how to open locks with comb picks. Comb picks are one of the best ways to hack into these common everyday padlocks. It's not a foolproof way to pick locks, but it's great when it works.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

The spy camera shown in this how-to video has a 60 foot cable, and is full color and has audio. This spy cam can be used as a security device, or to feed paranoid delusions or stalking urges. Watch this video tutorial and learn how to set up an X10 spy camera.

Installing a home security system can be expensive, but it doesn't have to be. This how to video shows you some easy practices that keep your home well protected. All you need is a few inexpensive items such as flood lights, signs, and light timers.

Your home security systems may not work for you if you don't turn it on. To top it off some of your bad habits can invite thieves in to your home. This how to video reviews some common sense steps to protect your home from burglars.

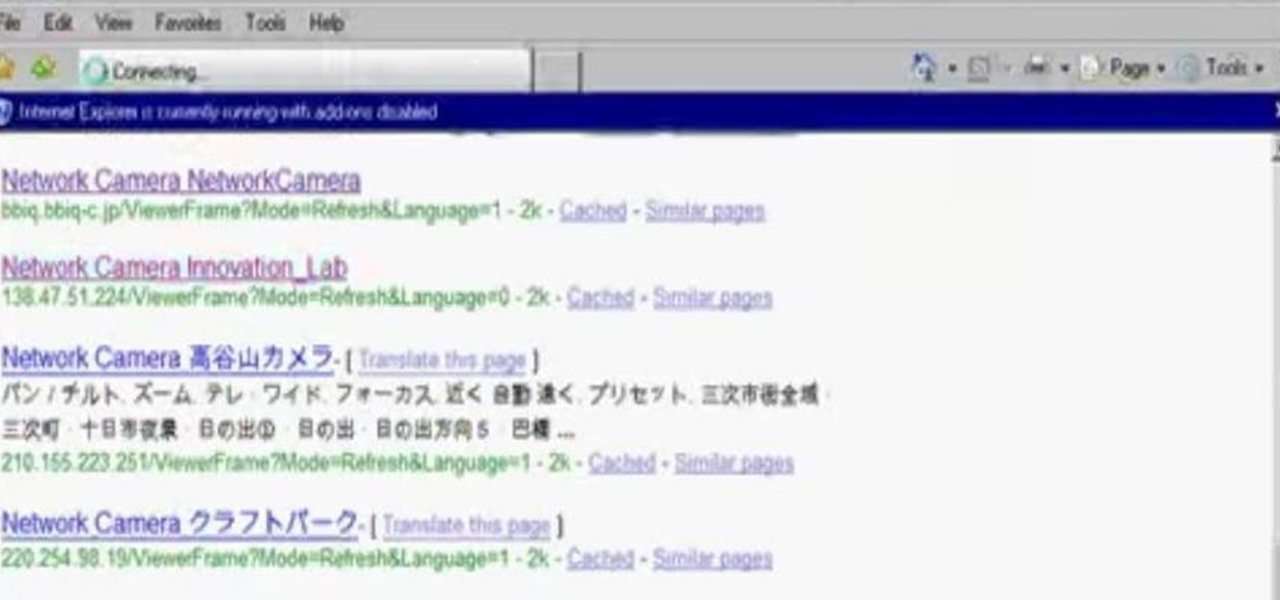
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!

Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.