In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.
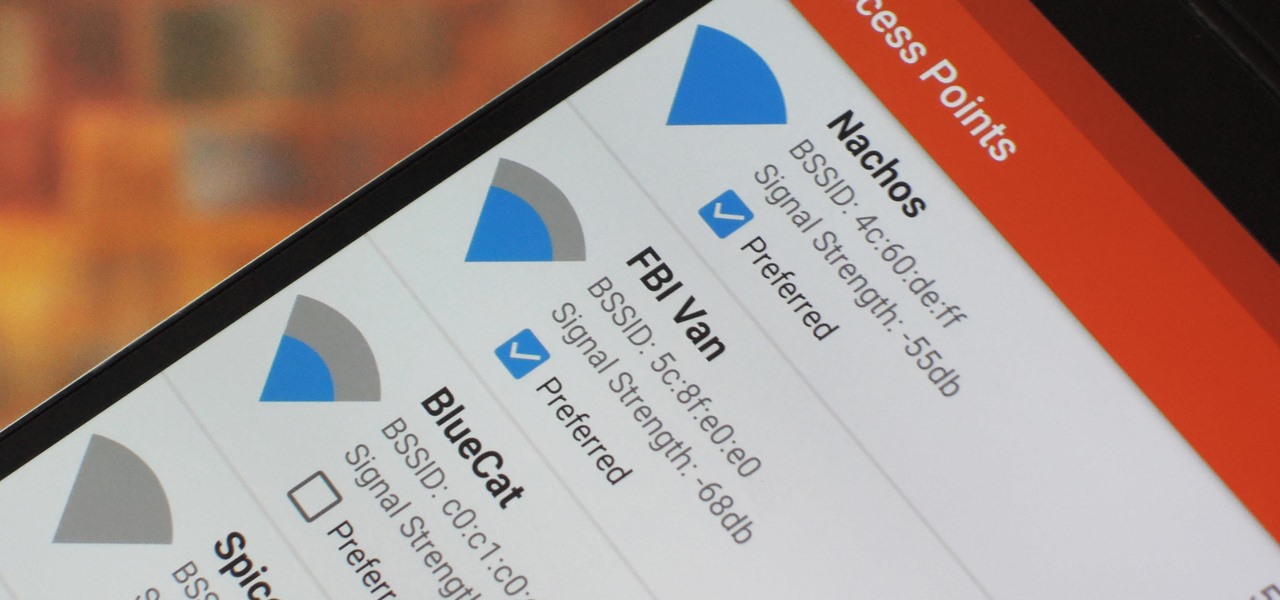
Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

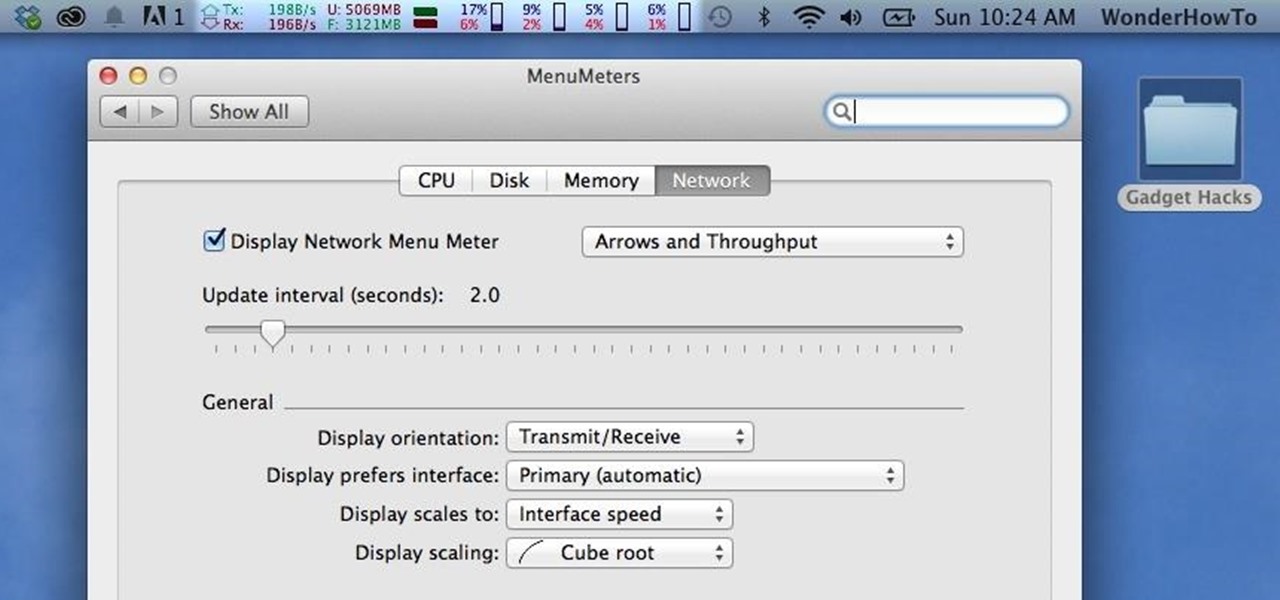
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

With all of the advancements in the smartphone world, we can virtually use them for anything. You can use your smartphone as a mobile hotspot, an Xbox controller, a car locator, and a security camera. Heck, you can even turn it into a Swiss Army knife. And now you can even use it as a wireless mouse for your computer!

In this tutorial, we learn how to map network driers from a remote server. First, go to run on your start menu, then type in the id address or server name for what you want to access and press enter. Now, right click on the folder you want to map and click on map network drives. Choose any letter you want from the drop down menu, then click next to the "reconnect on logon" text. Click on the finish button, then open your newly mapped network drive from your computer. You can do this for any s...

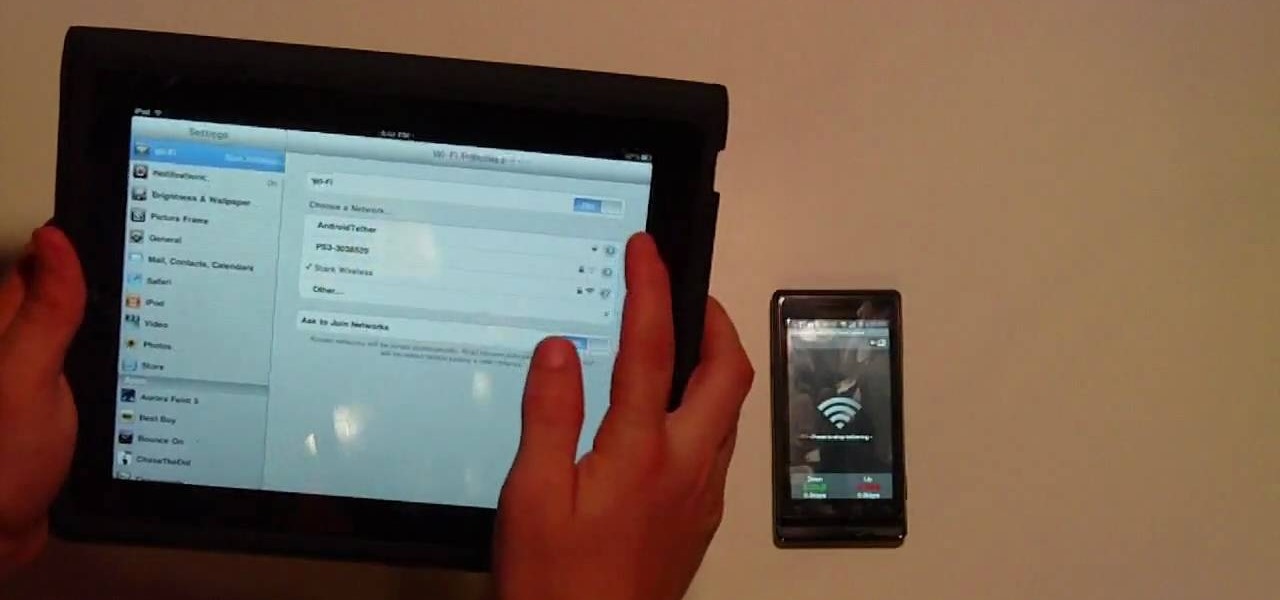
In this Electronics video tutorial you will learn how to tether a laptop to a Droid Smartphone for free Wi-Fi. For this you will need the android wifi tether application. Download the version for your device from here and install it. Then launch the app and press the icon to start tethering. In your laptop, go to settings and then to wi-fi. You will see a new network called android tether. Connect to the network and you will see that it works. As with any other network, you can change the nam...

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

Don't fret too much if your watermark is barely noticeable when you're finished with this project - the less obvious it is, the better a job you've done. Watermarkers are present in many types of paper, especially the monetary kind. If you hold up a ten dollar bill you'll see a watermark of Thomas Jefferson's face on the right, proving the bill is real.

In this, the latest family-friendly recipe from the Food Network's Neely's, you will make garlic grilled lamb chops. These chops are irresistible and you will put them together from scratch. You won't have any leftovers after serving this great Southern style recipe. Enjoy!

What could be more perfect for a summertime barbecue than an All-American flag cake? This sponge cake is easy to make and covered in berries to give it a fresh, warm-weather flavor. If you need a dessert for Memorial Day or the Fourth of July, this is the perfect one for you. Start from scratch with the Food Network's Ina Garten, aka the famous Barefoot Contessa, in this clip.

The beauty of the iPod Touch is that it is not only for music. With the iTouch, you can access the Internet as well. You can use this Internet capability to download from iTunes, get e-mail, surf the web and many more options. In this tutorial, learn exactly how to turn your iPod on to a WiFi network so that you can take advantage of all the features your new device has to offer.

Ready to do some deep south cookin'? In this video, learn how to make fried mac & cheese with owner of Lady and Sons and Food Network's resident top southern chef, Paula Deen! ...And this isn't just any mac & cheese! This is mac & cheese wrapped in bacon and fried for a delicious crunchy finger food!

Use Microsoft Windows 7? Miss the old Ctrl-Alt-Delete log-in prompt? It's easy to restore. So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete overview of the restoration process in just over a minute's time. For more information, and to get started restoring this useful security feature on your own Windows 7 PC, watch this free video tutorial.

If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial.

In this tutorial, learn how to make delicious French profiteroles for dessert with Ina Garten of the Food Network's Barefoot Contessa.

The PhotoshopUniverse team effectively teaches a method of adding a watermark to an image, as a security feature to make it harder to copy or steal. Instructions are simple and easy to follow, using as an example a photo of two girls that one might have in his or her family album. Using Photoshop, the text that will become the watermark is added, rotated and patterned across the entire image. To finalize the watermark, the opacity is edited to a desired value so that it does not interfere wit...

This video shows you how to make a security device out of a door bell. The concept is that most thefts happen when people are away from home. To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell. When the door bell rings i...

If you've already jailbroken your iPhone, but noticed that you are missing your cellular data network tab, check out this video. You will need Cydia, Winterboard, and be jailbroken on 3.0 of course.

Not 100% familiar with all the awesome features that make facebook a great storytelling medium? Check out this instructive how-to video from the cast.

Check out this RESIDENT EVIL 5 Chapter 2: Gigante walkthrough from Machinima.com The behemoth from RE4 returns with some new tricks up his sleeve.

There are two ways to properly lock your seat belt. You can use the childlock auto adhjustment. Or you can recline the seat, but then push forward to make your seat belt very tight. You don't want to be flopping around in the car. The bottom of your wrist is on top of the steering wheel and your shoulder is in the seat. It will loosen up when you get on the track.

Check out this Mahalo video walkthrough of Savannah in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

This video will show you how to fake a RAM, Flash, or entire memory clear. Lots of teachers and test administrators go around and clear your calculator so students don't cheat. This is any easy way to subvert the teacher's security measure. This is a good thing to know if you want to cheat on your GED, SAT or ACT test / exam.

Network sharing lets other iPhoto users view your photos and albums from their computers.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...