
How To: Protect your privacy on social networks
Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.


Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.

This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.

In this video you will see how to access network security cameras through google search engine easily!

Google recently unveiled the start of their new social network Google+, which is set to compete with Facebook and fix the awkward, broken aspects on online sharing they claim exist. It's currently only open to a limited number of Googlers during its "field trial," and if you weren't one of the lucky ones given an invitation, you can still sign up to be notified when Google+ is available in your area. You can also stay up to date on its Twitter page, GooglePlus.

The iPhone has always has one very big problem: that it is tied to AT&T. AT&T is a terrible network, and many iPhone users out there are probably dying to switch network but keep their awesome phone. Well now they can! This video will show you how to unlock you jailbroken iPhone 4, 3GS, or 3G using a program called Ultrasn0w, leaving it ready for use on any cell carrier in the country. Except Sprint, they don't have SIM cards.
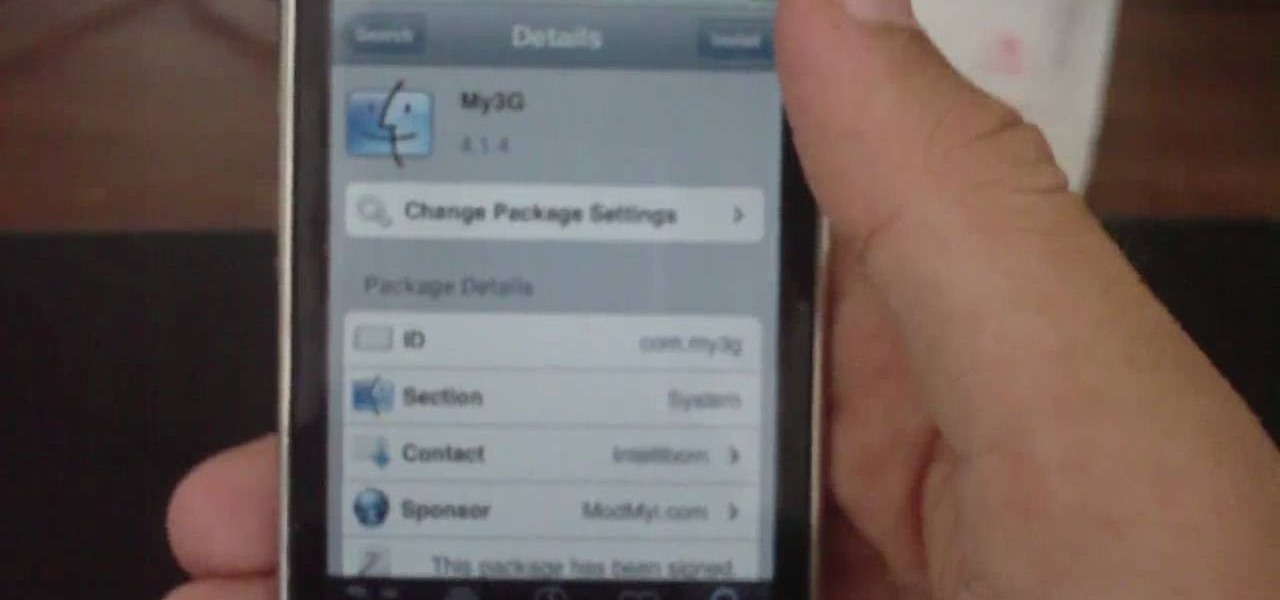
FaceTime is a very cool Apple App that makes video chat possible on the iPhone, but only if you're on a wifi network. Officially, at least! One of the many cool things that you can do after your jailbreak you iPhone 4 is use FaceTime on the 3G network! This quick video will show you how to enable Face Time 3G use using a jailbreak App called MY3G.

This 2 part video will show you to make a classic Victoria sandwich sponge cake. Follow along as this sweet afternoon tea snack is put together. Fans of raspberry jam will be delighted to get a nice sweet filling. It's a lot easier than it looks! Just follow the recipe and the video!

We all want to put our best face forwards on our social networking profiles. Facebook, MySpace, Twitter and all the rest are the best places to show great photos of yourself. You never know who might be looking. Employers, potential suitors, ex-high school classmates.. they are all snooping to see what you're doing and how you look these days.

In this video, Anne Marie teaches us how to make soap cupcakes with whipped frosting! This recipe will make 16 soap cupcakes, which is perfect for parties. For the cupcake base you will need: 40 oz white melt & pour soap, 1 1/2 oz vanilla select fragrance, 1 1/2 oz vanilla color stabilizer, 6 ml canary LabColor (diluted), SoapyLove scalloped round mold and spray bottle with rubbing alcohol. For the soap frosting you will need: 16 oz white melt & pour soap, 8 tbsp natural castile liquid soap, ...
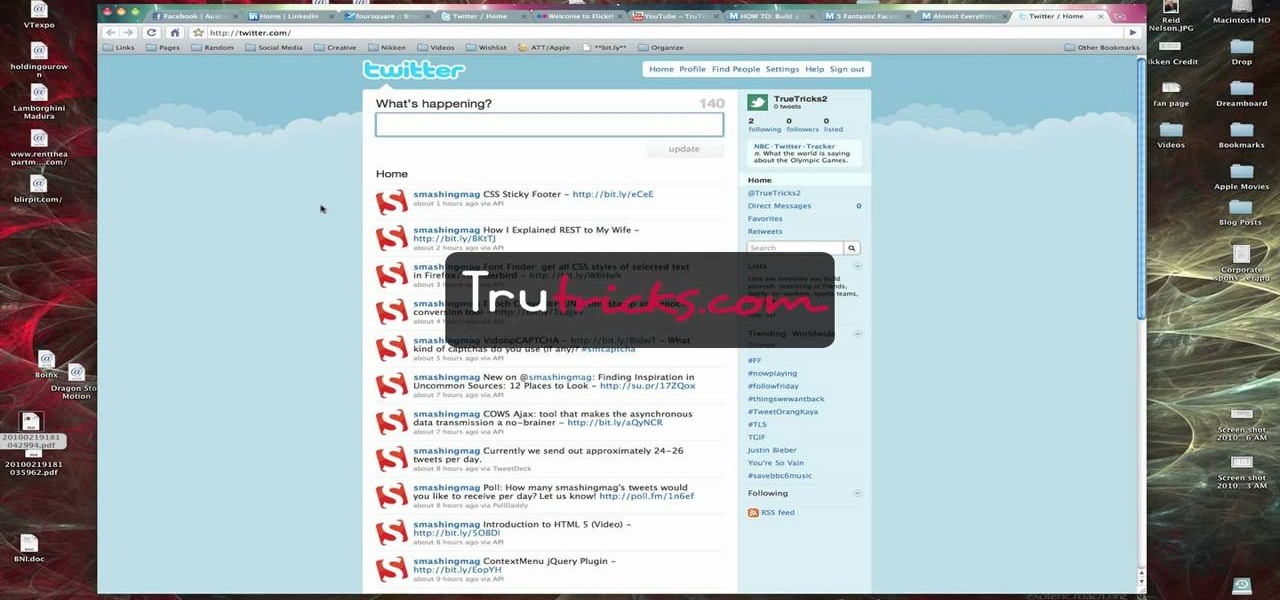
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...
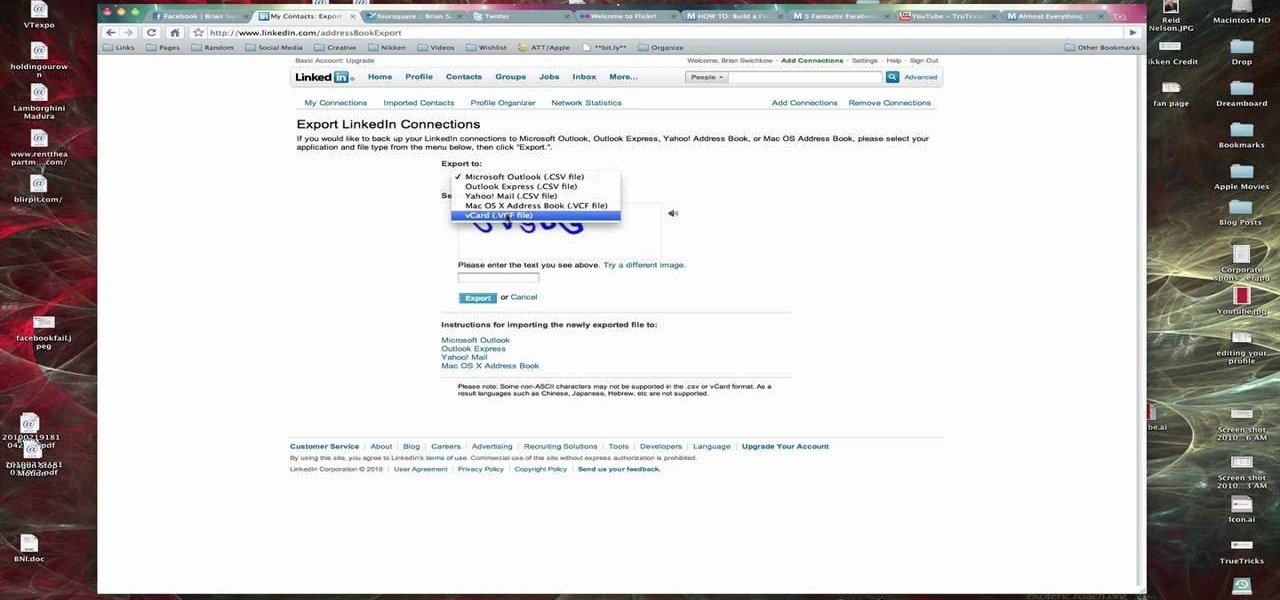
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

This video demonstrates how to make edible fruit bouquets and arrangements. you can use any fruit and chocolate. Start with a ceramic base. Also, you'll need a Styrofoam ball about 2 inches larger than the base, a hot glue gun, flower shaped cookie cutters, a pack of toothpicks, wire cutters. The video demonstration plans a layer of dates, topped by a layer of chocolate truffles, pineapple and then apricots. Begin by placing artificial leaves to the base, gluing them on. Then hot glue the Sty...

Take a look at the first place winner's tutorial on making a dress out of old tees for the Generation-t tee recon contest! Follow along with the steps in this fashion design video and make your very own quick and easy dress.
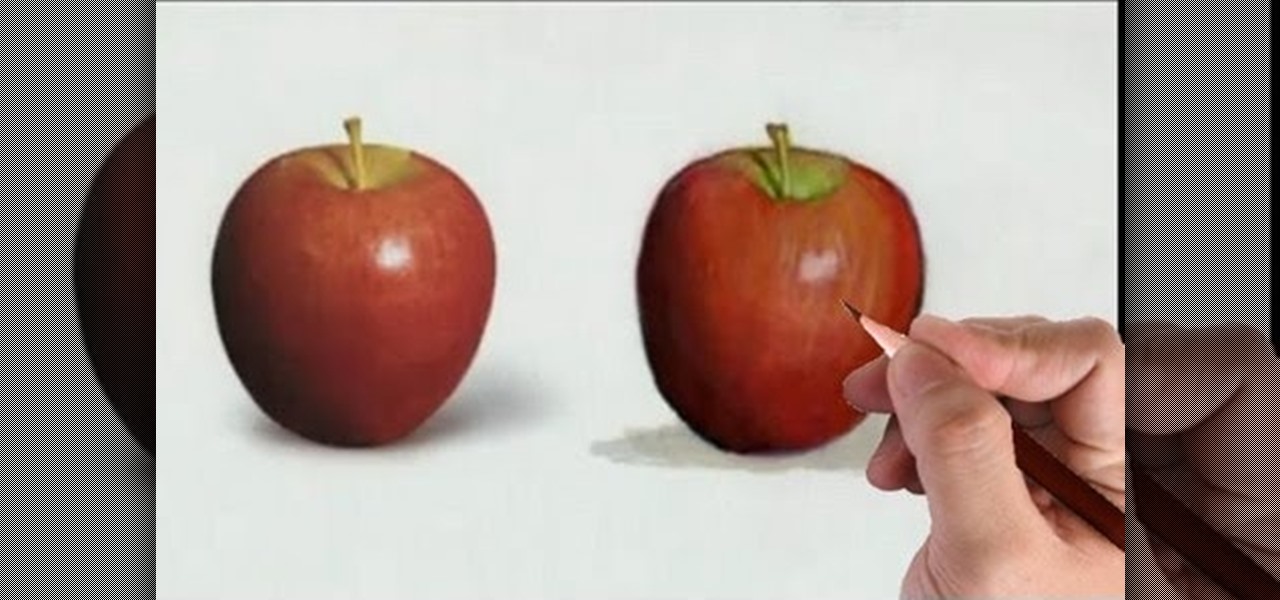
Watch this fine art video tutorial to learn how to illustrate with markers and colored pencils. "This video shows my process for making an illustration (non tradigital). I use illustration markers (usually prismacolor) and color pencils (usually prisma once again) and a wax blending stick. I make my illustrations in two steps:
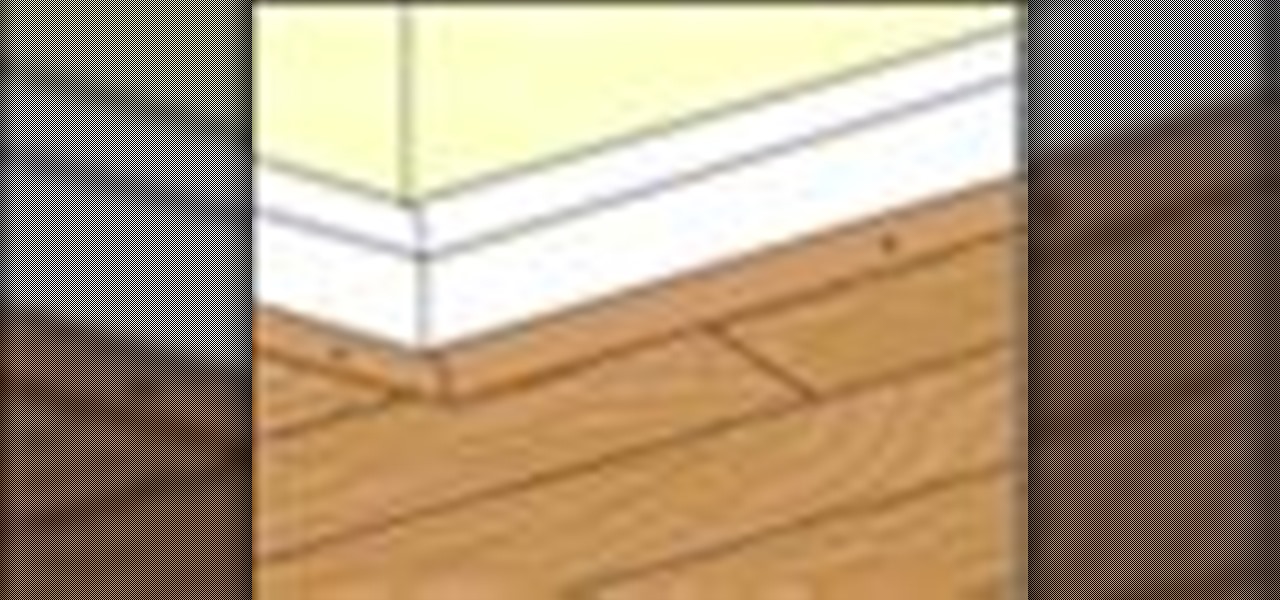
This tutorial will talk you through installing base boards. Installing base molding adds dimension to baseboard. It protects baseboards and it is easy to replace. Remove the old molding. Four techniques will be discussed about different cuts you will have to make. 1) end of run 2 )mid-run joint

On MLB channel, Rickey Henderson shares some base-stealing secrets with Barry Larkin and Harold Reynolds. Henderson has a record for stolen bases. It requires speed, agility, good judgment and decisiveness. Steal bases with Rickey Henderson.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.
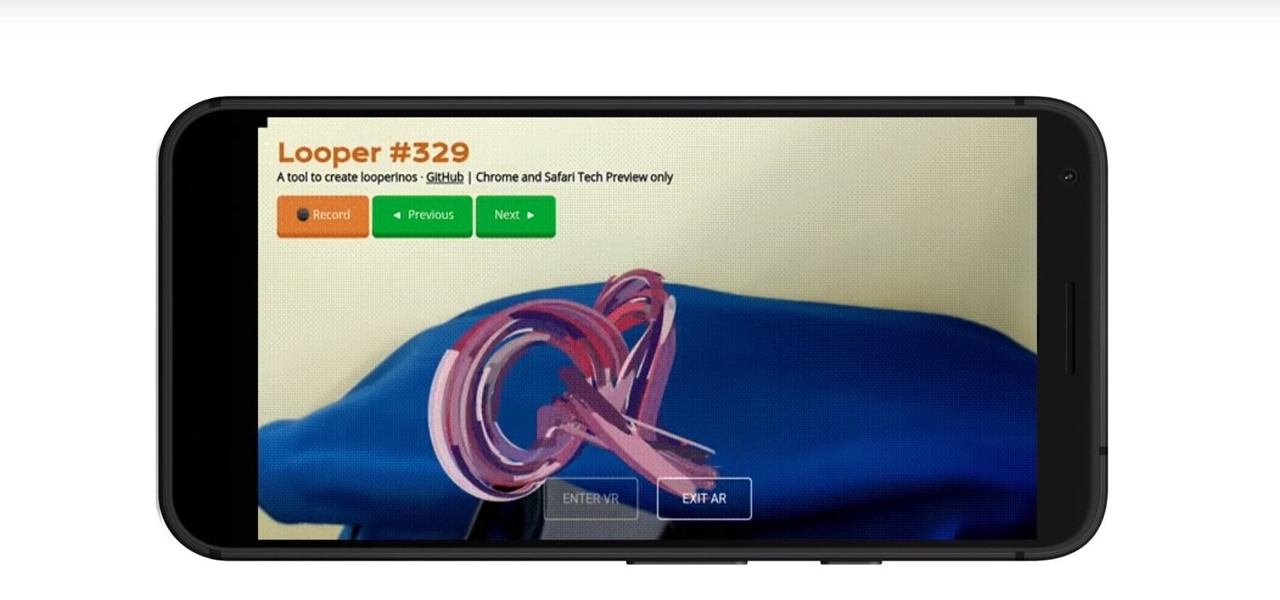
Web-based mobile augmented reality technology continues to gain momentum as Google is set to expand the standard for immersive web content to AR.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Zenko Games makes no apologies for its influences. In fact, they cite them explicitly in their own promotional materials for Diamonst AR.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. But every now and then, you'll see a ROM that isn't based on Android, though these are few and far between — at least, until now.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

Wes Craven is a very important dude in film history primarily because of his role in shaping the modern horror genre into what it is today. Plus he has a really badass sounding name.

Watch this video for instructions on making the Yukki Cross Artemis scythe from the anime / manga Vampire Knight.

First of all, you must get in to the screen and start to made a base for your ice rocket. Then you chose your pen size and start to draw the ignition rocket body and the base for the ignition metal for your rocket.

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...

This video shows you how to use couplers for cake decoration using these steps: 1. Couplers usually come in two plastic pieces, a base and a ring. This system fits inside cake decorating bags or cones and allows you to use the same icing with different tips.

For a health conscious change of pace, try a tuna burger! They are so easy to make, all you have to get is some canned tuna, which you probably already have in our pantry. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller.
To test how fast your internet speed is an intermediate level skill. Start by picking an internet speed test. You can use Google or another search engine to find one. A service that is recommended in the video is DSLreports. This site does not require you to know a lot of information about your service. To test your speed start by picking a city that is near to you. Then shut down all tabs and every application that you have running. It's important to do this on every computer on your home ne...

Power Armor that isn't faction based, mostly around the Brotherhood of Steel, is very hard to come by in Fallout New Vegas. Wearing faction based armor can have negative effects if you're traveling in the territory of a faction that doesn't like that faction, regardless of your standing with that faction. Now THAT's a mouthful! But, there is a suit of Enclave Remnant Power Armor laying at the crashed Enclave Vertibird. Check out this video for the location of the Power Armor!

There are zillions of fun and cool things you can do with guitars, including riffs, hammer down, and so on. But in order to unleash the rock star that we know is hidden deep within you, you have to start with the basics first.