A major Hollywood player since she was a preteen, Vanessa Hudgens knows what looks on the red carpet and what doesn't. And, like most girls, she's found that the smokey eye never fails to make your eyes pop and to the make the eyes of nearby cartoon wolves pop out.

This is a video that explains to a person how to write their name in Japanese. The woman shows two ways as to how to translate your name in Japanese. The first is how the name is pronounced, and the second way is to translate your name based on the meaning. Usually the name is translated based on pronunciation in the native language. The name is pronounced similarly but not exactly the same. For example Rachel is pronounced "Reicheru". She also shows a website where more information can be fo...

This video describes how to make a "no calorie" birthday cake centerpiece with carnations in soft and sweet hues of pink, yellow, white and cantaloupe. first a flower foam was taken. Then the toothpicks were used to join the flower foam together. Then trace out a circle from the foam using a kitchen knife. Add some water to the base of the cake. With equal size flowers decorate the base of the cake. Then the cake is beautifully covered with different types of flowers. decorate with as many fl...
Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large.

In this video tutorial, viewers learn how to make a Midori based "Green Iguana" cocktail. The video lists all the required ingredients to make a "Green Iguana" cocktail. The ingredients include: an ounce of Midori, half an ounce of tequila and 2 ounces of homemade sweet sour mix. To make the "Green Iguana" cocktail, follow these steps: mix all three ingredients in a cup, mix ingredients by shaking and add ice. This video will benefit those adult viewers who enjoy alcoholic beverages and are w...

This video teaches the secrets of applying flawless false lashes. An excellent summary is given below. First hold the lashes with tweezers to your eyelash to check the size of it. Cut it off a bit if the false lashes are big compared to your eyelashes. Now apply some glue carefully to the base of the false eyelash. Close your eyes and stick the false lashes to the base of your eyelash and hold it for a few seconds to let it dry. After the glue gets dried blend the false lashes to match with y...

In this video tutorial, Chris Pels will show several aspects of defining and using master pages in an ASP.NET web site. First, see how to create master pages declaratively using the ASP.NET master page model and learn what information is best suited to a master page compared to an individual content page. Next, see how to programmatically assign master pages on-the-fly in an individual content page. Also learn how to create a base page class which assigns a master page programmatically for al...

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Raise the Jolly Roger and set sail on the high seas! Seafight is a free to play, browser based game in which you assume the role of a pirate and sail about the world, killing monsters and collecting plunder. This video shows you how to start playing!

Here is a simple gradient eye look created with Cool Heat Mac products. Follow along and learn how easy it is to apply this dark and light blue eyelid color.

New to the Ruby programming language or simply looking to brush up on your skills? In this installation from his Rubyology series of Ruby tutorials, YouTube user cmatthieu demonstrates how to use SOAP-based web services with Ruby. To learn more, take a look!

From brute force hardware-based solutions like pointing a camcorder at your monitor to more elegant, software-based solutions like (the free and open source) Xvidcap, there are no shortage of ways to create a screencast while running Linux. In this how-to from Linux Journal Online, Shawn Powers offers a comparative look at many of the most popular techniques employed by Linux users.

This video crocheting tutorial, brought to you by thecrochetside.com, demonstrates how to crochet a double crochet base chain. Learn how to crochet by watching this instructional video.

It's fun to put on makeup. IT's not fun to take makeup off. This tutorial video will show you how to get rid off all those products on your face.

Learn how to open a wooden cremation urn. Most have four screws that retain the base or inset base. These screws can be removed with a Phillips Screwdriver or electric screwdriver.

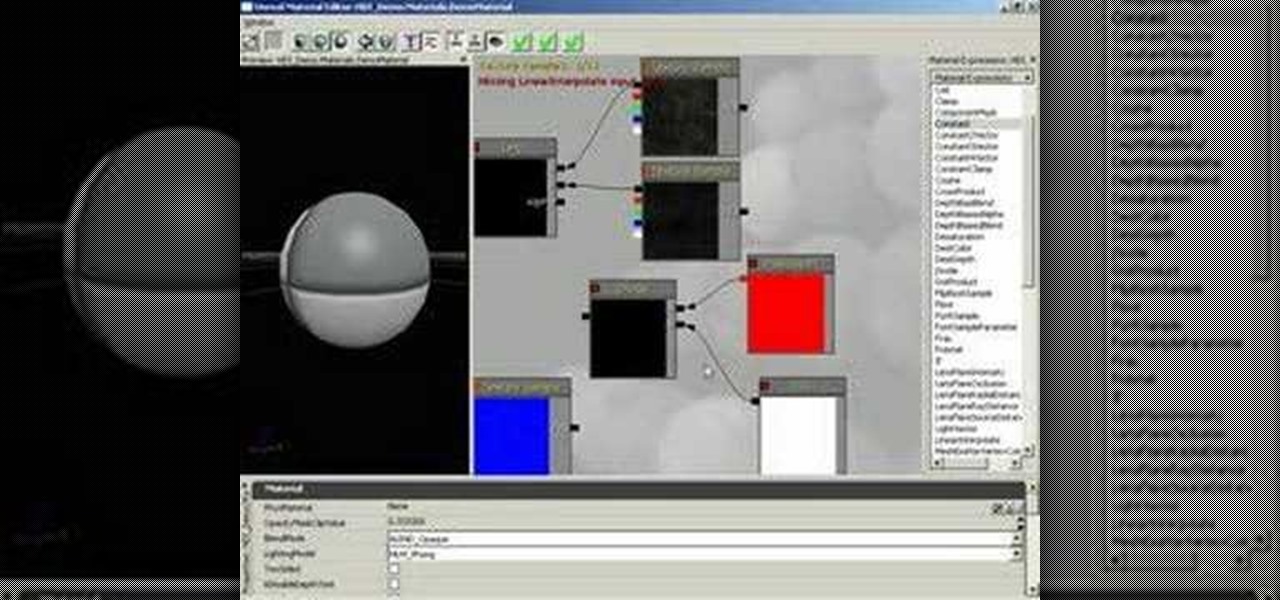
Learn how to blend between two textures based on distance from a surface in Unreal Tournament 3 Editor.

This tutorial shows you how to add flag bases to capture the flag maps in Unreal Tournament 3 Editor.

Check out how to make this Italian fruit cake. This is the base for the cake.

Italian salsa verde is a parsley-based sauce flavored with salty seasonings like anchovies and capers. You can enjoy this easy salsa verde over pasta, meat, or fish. You will need anchovy filets, capers, canned tuna, olive oil, parsley, lemon, pepper and a galic clove. This sauce is like a parsley-based pesto and can be served with meat, fish, or pasta. You can store extra salsa verde in the freezer.

Learn how to make this origami creation which can be used as either a base or can be filled with water.

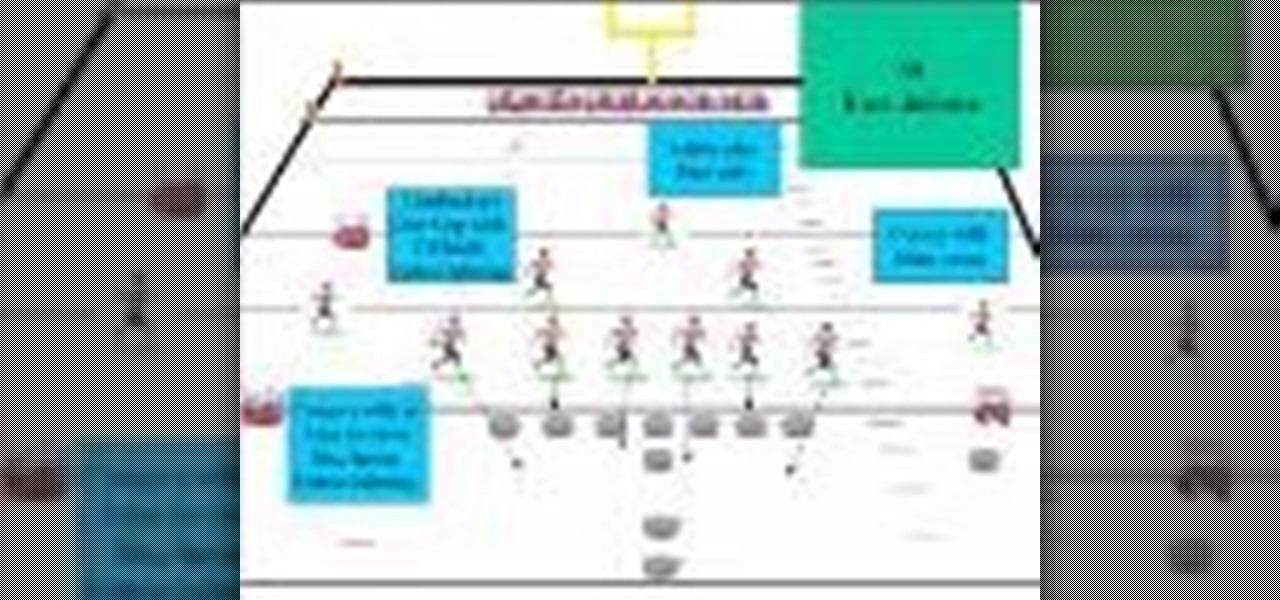
You can learn the 60 football base defense. It is a great defense for youth football, but everything changes when you blitz. Corners stay at home, linebackers take a step back, and safeties play pass only.

Summertime is a sad time for your beloved snowboard, languishing in the closet waiting for snow. Did you know that your base can become dried out from all that downtime? Watch this video to learn how to store your snowboard safely. Store your snowboard in summer & prevent base damage.

This tutorial will show you how to use FunFX, a free, open-source, and Ruby-based automated testing framework for Adobe Flex applications. Watch this video and learn how to drive a Flex application through a web browser. Use FunFx, a Ruby-based testing framework for Flex.

Handbag TV’s make-up guru, John Gustafson shows you how to create the perfect foundation base Create the perfect foundation base.

Self-storage may not be a new industry, but it is one that is rapidly reshaping its operations to suit a progressively more modernized customer base. In order to stay competitive with your self-storage facility, you'll need to keep an open mind, embrace current marketing trends, and most importantly, have a well-defined set of marketing goals. Your main focus should revolve around the following points:

Prefer a clear, hand-rubbed, "antique" finish to the shiny or satin sheen of varnishes? Then you will want to use a tung oil-based topcoat applied over an oil-based stain when you are staining or refinishing your special piece of furniture.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

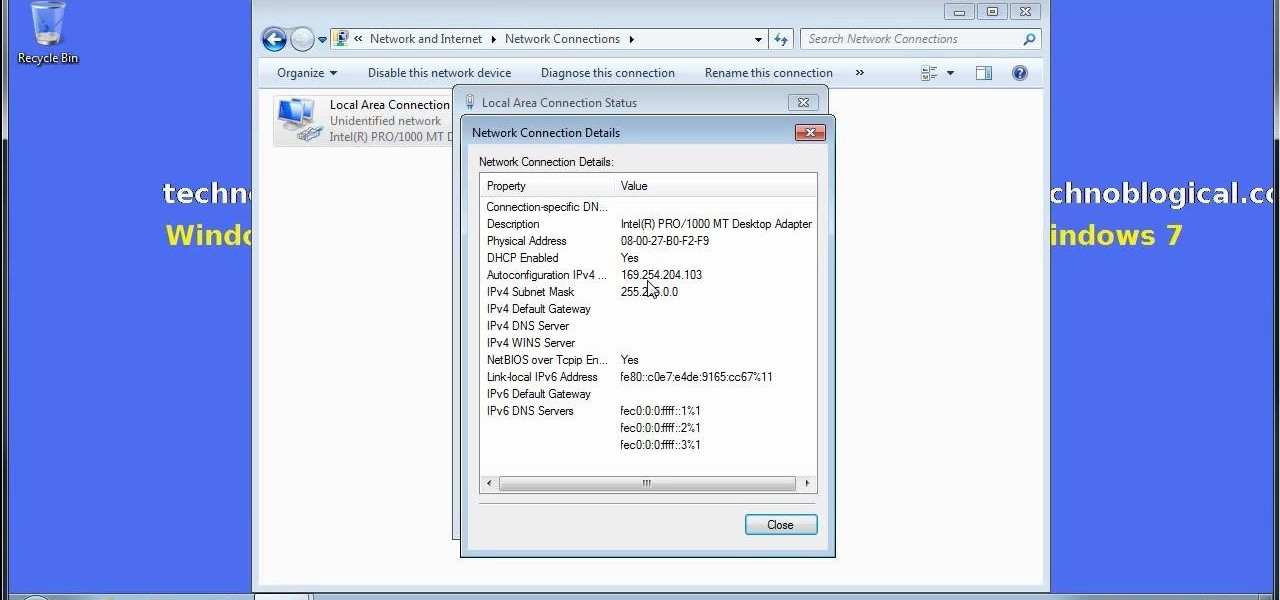
Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

GOOD, a Los Angeles-based magazine focused on doing good in the world, along with LAUSD, The USDA People’s Garden Initiative, The Environmental Media Association, The National Gardening Association, The Urban & Environmental Policy Institute, The California School Garden Network, and Mia Lehrer & Associates, is sponsoring a contest for people to help design a garden for a LAUSD school. GOOD will help build the winning garden design, and they'd like your participation, too.

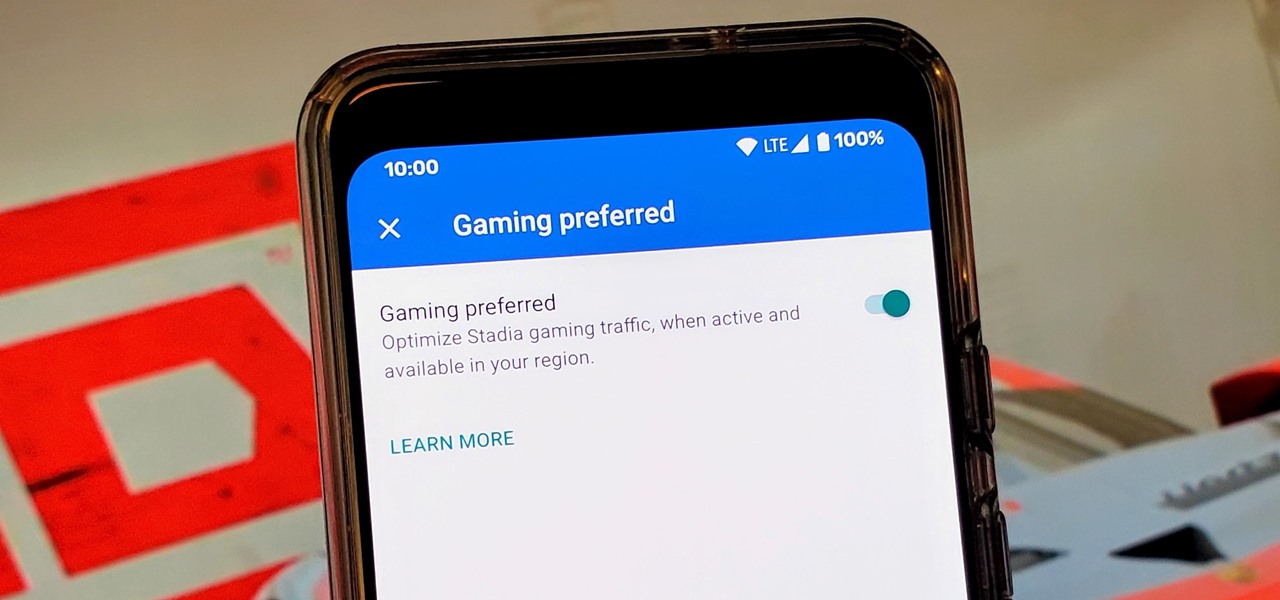
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.

In the wake of Apple and Google pitching augmented reality to schools, McGraw-Hill is stepping up its own augmented reality efforts for education.

The Apple rumor mill is getting its first real workout of 2019, and this time the whispers are more exciting than usual.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

As we predicted earlier this week, the focus has already begun to move from Magic Leap back onto Apple's rumored augmented reality smartglasses. The latest credible whispers come from none other than longtime Apple-focused analyst Ming-Chi Kuo.

Extra hardware buttons have become a trend with smartphones lately. Often, these are unmodifiable buttons designed to launch a voice assistant. That isn't the case with the BlackBerry KEY2. Making a return from the KEYone is the Convenience Key, which also received an upgrade.

Most of the animated characters and animals we've seen in augmented reality are still fairly basic in terms of visual fidelity. And because many are still impressed by simply seeing 3D figures properly scaled and tracked alongside real-world objects, this approach has worked ... so far.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.