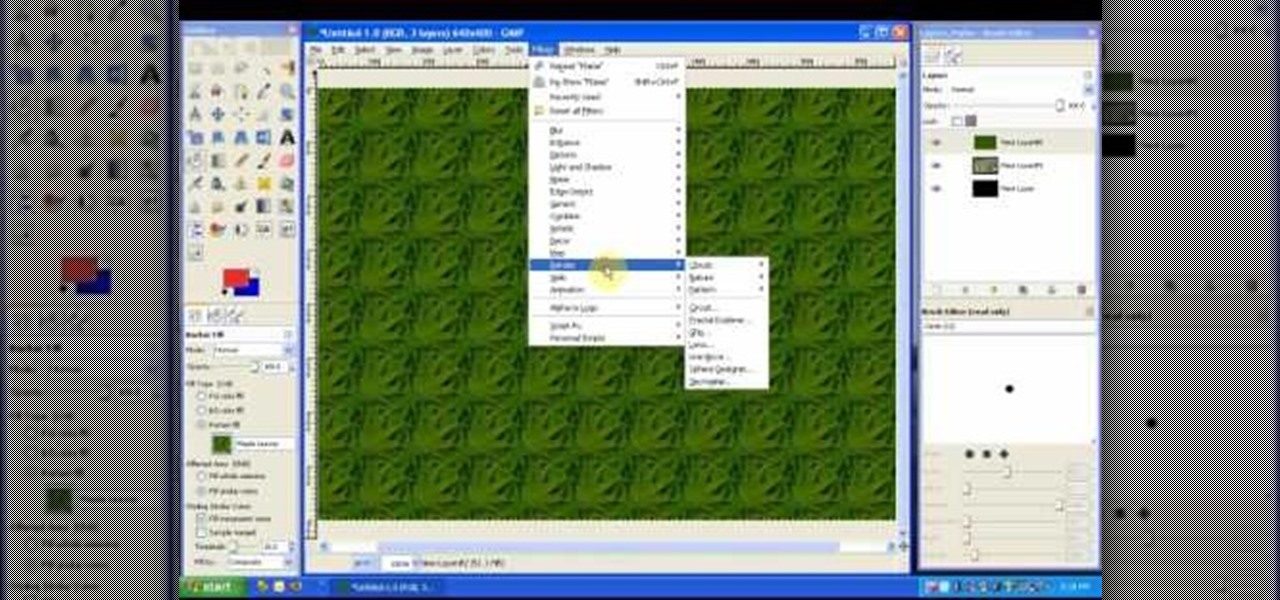
This is a tutorial in Adobe Photoshop CS2 demonstrating primarily the use of the quickmask tool to make precise selections of organic shapes. Other topics covered include adjustment layers and layer masks. So watch and learn how to enhance photos using quickmasks, layer masks and adjustment layers in Photoshop CS2.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.
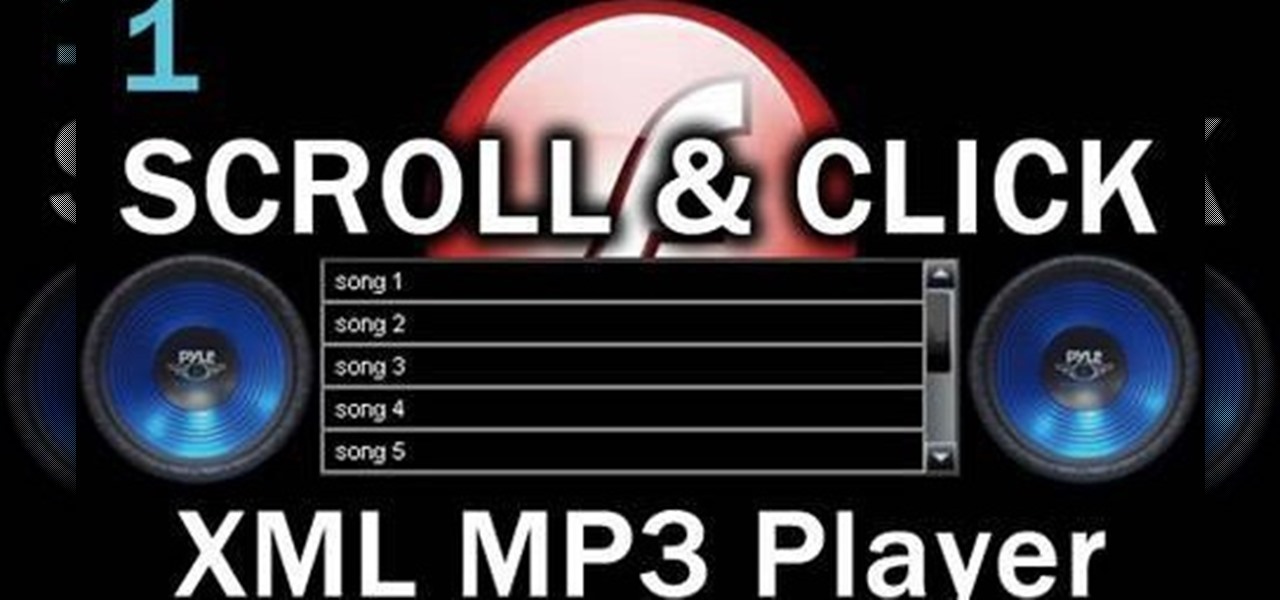
Add music content to your website! If you want to add a scrollable, clickable playist to your Flash-based website (like to show off your band's music), this tutorial shows you a step by step process to building this interactive .mp3 player using Adobe Flash CS3 and Action Script
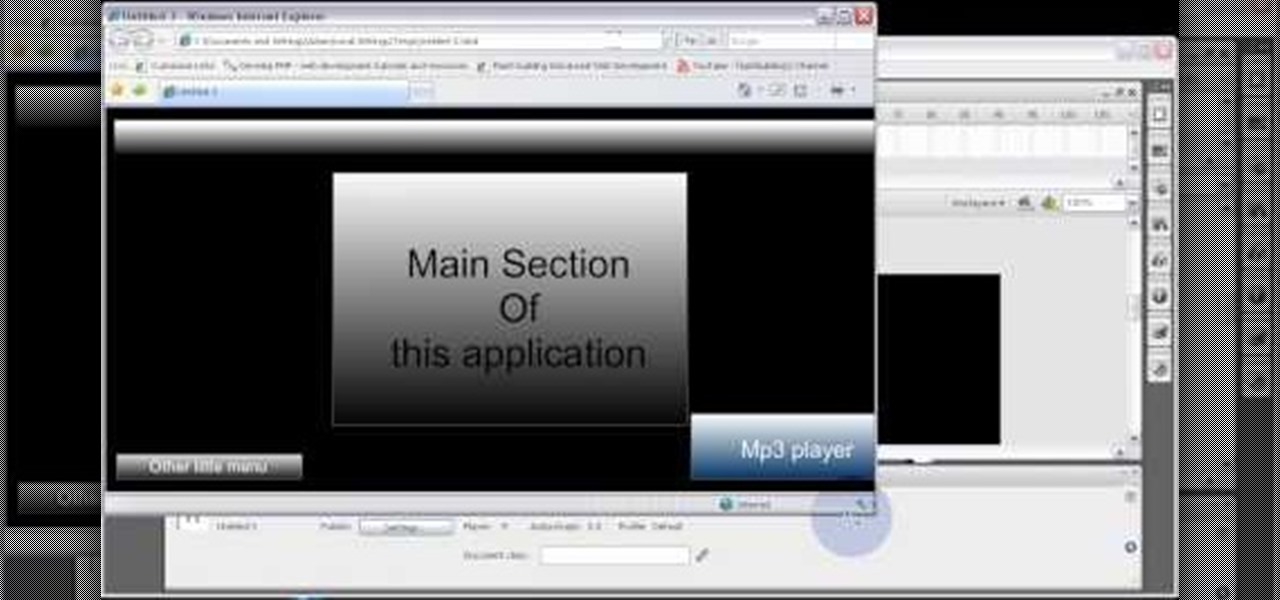
This tutorial is for anyone who wants to create their own Flash-based website, even those with little to no coding experience. You're shown how to incorporate animations, loader bars, and other interactive content into your website; as well as how to manage it all from the admin side.

How to disable Wi-Fi SSID broadcast on an Apple AirPort in seven simple steps. Open your AirPort Admin Utility application. Find your network's name and double-click it or press the Configure button on the bottom right of the screen. Enter your password and click OK. The Configure "Apple AirPort Express" Base Station should open. Click on AirPort tab. Select the "Create a closed network" check box. Click OK on the dialogue box. Click the Update button on the lower right part of your screen. D...
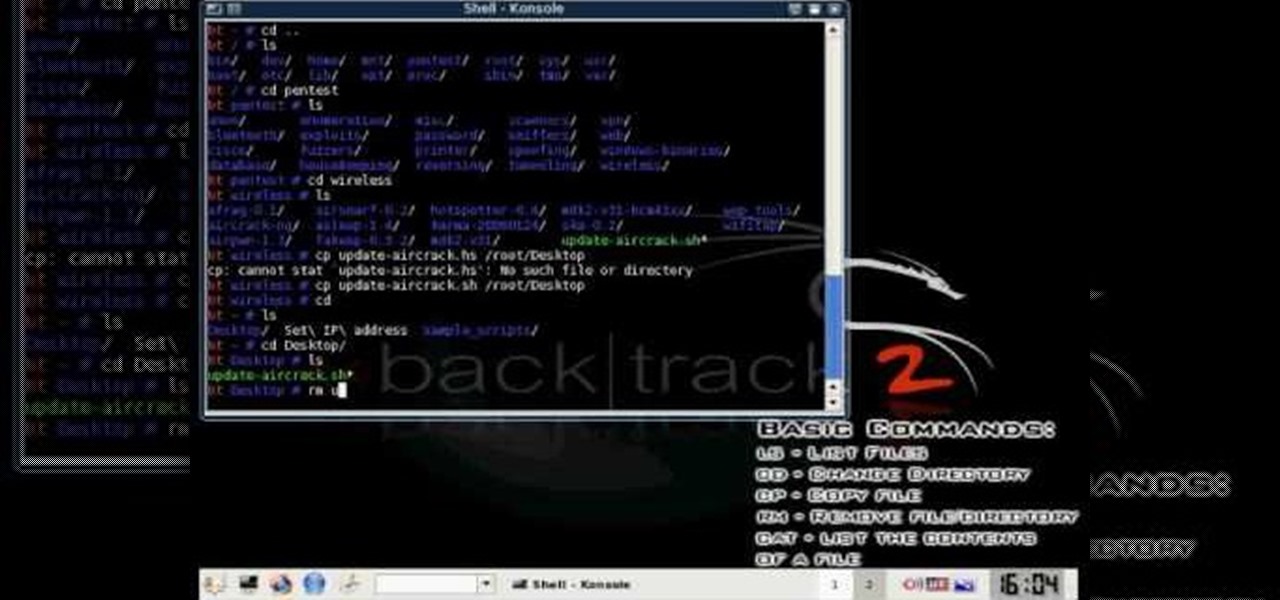
A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

Startup promises to catch 100% of network attacks - Techworld.com.

These cheats are primarily for the Playstation version of Grand Theft Auto: San Andreas, but might also work for the Xbox version as well. Use these codes to get monster trucks, stunt planes, infinite lung capacity and make your cars fly!

The Kinect is more than just a toy for your Xbox 360. While it's primarily a gaming accessory, it's also a fairly powerful high-tech camera. This tutorial shows you how you can use a Kinect to measure objects in 3D, using the Kinect's own box.

This tutorial is aimed primarily at those who crochet and are left hand dominant. Learn how to make a cute little baby hat using the puff stitch! It will even have an adorable little yarn bobble at the top. All you need is some yarn and a crochet hook!

In this tutorial on GIMP, the render-flame tool is looked over in detail. GIMP (the GNU Image Manipulation Program) is a free software raster graphics editor. It is primarily employed as an image re-touch and edit tool. It not only offers freeform drawing, but can also accomplish essential image workflow steps such as resizing, editing, & cropping photos, combining multiple images, & converting between different image formats.

Coleslaw is a popular side dish in America and Europe. Primarily consisting of shredded cabbage and carrots, many other variations have been passed down through the generations. In this quick tutorial, learn how to make coleslaw, quick and easy.

Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

Xander and Calvin go over some basic editing transitions here. They primarily feature THE CUT and THE DISSOLVE and explain why they're they best "storytelling transitions".

This video shows you how to perform the full kata using the kuwa (hoe) as a weapon, a technique primarily developed in Okinawa.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

If you want to connect your Mac notebook or desktop to a wireless network, you'll need to set up the wifi connection on your computer first. Take a look at this walkthrough to find out how to find and connect to available wireless networks in OS X. This is a great skill to know if you own an Apple laptop and need to connect to the Wi-Fi networks at different locations.

United States Womens Softball Team members discuss and illustrate how to run the bases correctly. The main techniques used are how to lead off then steal each base as the technique is different for each one, and perform the hit and run. The breakdown is great!

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Following San Francisco-based Occipital's successful Structure Sensor Kickstarter campaign, the release of its Bridge AR/VR headset, as well as a string of technology and company acquisitions, the company has built a rather strong name for itself in the AR community. And now, with the first public release of its Bridge Engine on Thursday, the company continues to expand the features its platform has to offer, with hopes of bringing in more developers to utilize it.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.

The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until now.

5G is showing up more and more in the news, as an increasing number of companies jump on the bandwagon. AT&T made a splash earlier this year with their embarrassing "5G Evolution" debacle, and the other three major wireless carriers soon followed suit, detailing their own vague plans for 5G. Today we find another company has joined the fray, just not a cellular one — Apple has officially been approved to test 5G networks.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

We like to have a variety of cupcakes on hand when we're entertaining, but we don't want to spend too much time making separate recipes. No one has the time or the money for that—especially when you're hosting and you've got a bevy of other dishes to prepare.

Watch this five part instructional video series to experiment with base coats on your Warhammer miniatures. Using thin coats of paint and small brushes, leave a wider margin for experimentation and highlight coats. The rich and impressive detailing on Warhammer figurines comes with patience and perseverance. Warhammer miniatures need several layers of primer and original fill color for a deep base coat.

If you play Elder Dragon Highlander, the awesome Magic: The Gathering variant, check out this video for a guide to building a cat-based deck that will ravage people. Cat attack! If you haven't played EDH, check out the link above and come back.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Code your Flash-based website so that your content can remain the same, no matter if visitors are viewing your site on a computer screen, smartphone display or even a high-definition TV. This tutorial shows how you can code your fluid website to achieve the true fit effect.

HTPC. It stands for Home Theater PC. Some refer to it as simply a Media Center. But no matter what you call it, you're going to learn how to build one today. Why would you want to do that? Because one of the main advantages of creating your own home theater system is that you are control, not only of the cost, but the features and functions, as well.

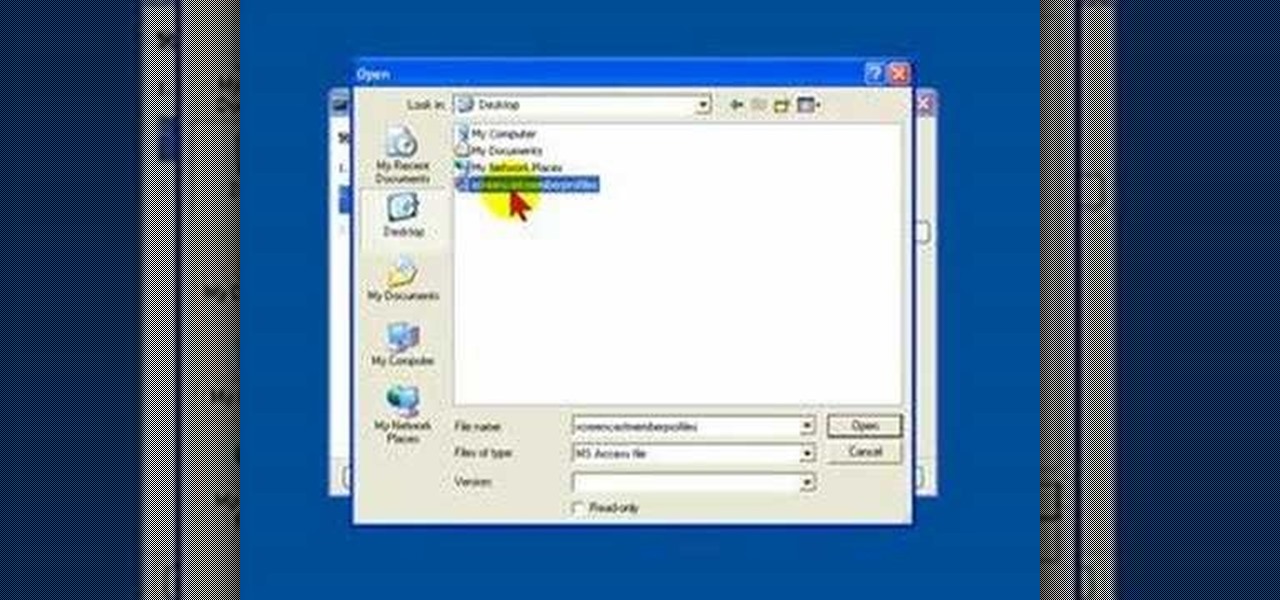
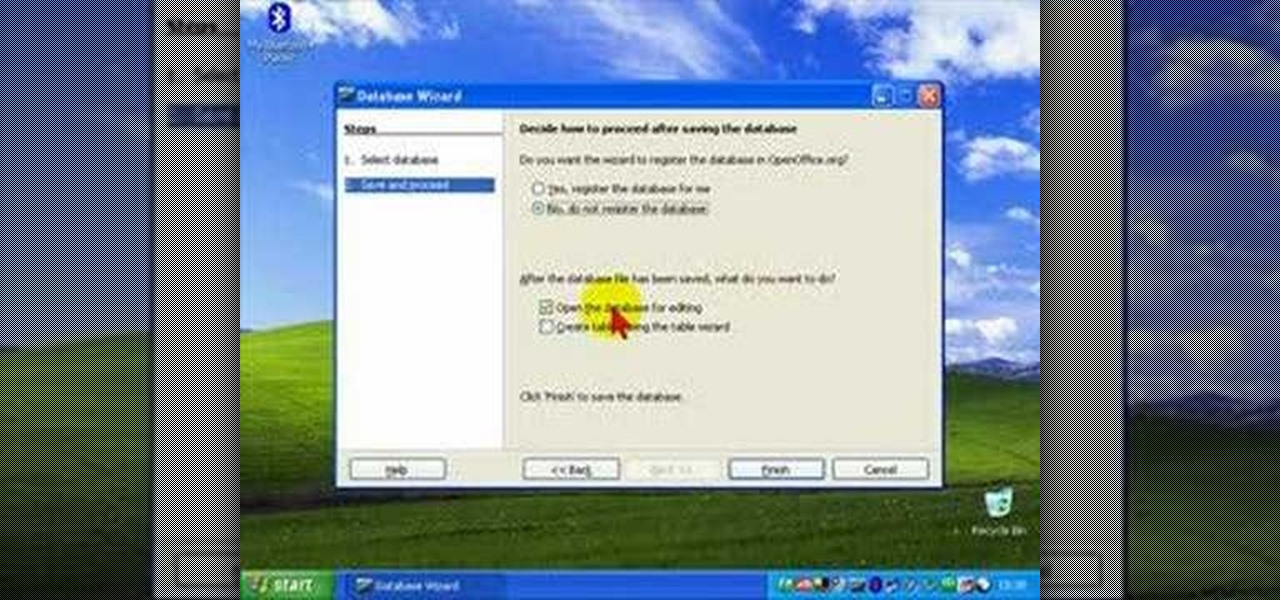
While you cannot directly open a Microsoft Access database file in OpenOffice Base, it is possible to connect Base to an Access database, and manipulate the data contained within it.

Databases allow you to store data in a systematic and organized format, making it easy for you to search, sort and edit.

This is a video tutorial in the Education category where you are going to learn how to draw an isosceles trapezoid. This video demonstrates how to draw an isosceles trapezoid with a long base (B), a short base (b) and a 35 degree angle. First you draw the long base. Now center the short base at the center point of the long base and mark the end points of the short base with dots. Next draw perpendicular dotted lines from the dots extending upwards. Draw 35 degree angles from either end of the...

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

New York-based startup CTRL-Labs has closed a $28 million Series A round of funding from Google parent Alphabet's GV and Amazon's Alexa Fund, among others, for its next-generation neural interface technology for AR/VR and robotics.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.