In this Home & Garden video tutorial you will learn how to build a landscape retaining wall in a weekend. This video is from www.allanblock.com. You can do it by using the Europa collection from Allanblock. Get the installation details and the location of the nearest dealer from the website. Tolls you need are a shovel, hand compactor, wheel barrow, measuring tape, level, hammer, rake, broom and gloves. This project will require the AB Barcelona, AB Palermo and AB Dover blocks. The first step...

In this culinary how-to from the Food Network's Ellie Krieger, you'll learn how to bake delectable, almost-healthy carrot cupcakes using whole carrots, lemon zest, canola oil, brown sugar, two eggs, 3 quarters of a cup of whole wheat pastry flour, 1/2 cup all-purpose flour, 1 teaspoon of baking powder, 1/2 teaspoon of cinammon, 1/4 teaspoon of nutmeg and a 1/4 teaspoon of salt.

Create sexy leopard print eyes. Fresh Face: Start with what I call a fresh face, which is your clean slate for all of your looks. A fresh face is after you have put concealer and foundation all over the face or only where needed, which ever you prefer. Also groom the eyebrows at this point, if needed, to avoid smudging shadow or liner while trying to groom. Apply a generous amount of loose powder to the eye to catch little stray make-up pieces. Shadow base: Apply a shadow base to give a good ...

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

Twilight, that steamy, dreamy love story between teen Bella and heartthrob vampire, Edward Cullen. This love story is based on a series of vampire novels (Twilight, New Moon, Eclipse, and Breaking Dawn) by Stephenie Meyer. True love, handsome boy, and vampire danger = perfect teen love story. Who's your favorite Twilight character? This makeup tutorial demonstrates how to create Bella Swan's makeup, based on the actress Kristin Stewart in the Twilight movie.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

After three years and change, no one seems to be able to knock Pokémon GO off its augmented reality throne. Zombies, dinosaurs, and ghosts have all met defeat at the hands of the pocket monsters. Heck, not even the world's most popular wizard and Pokémon GO's developer can replicate the original's success.

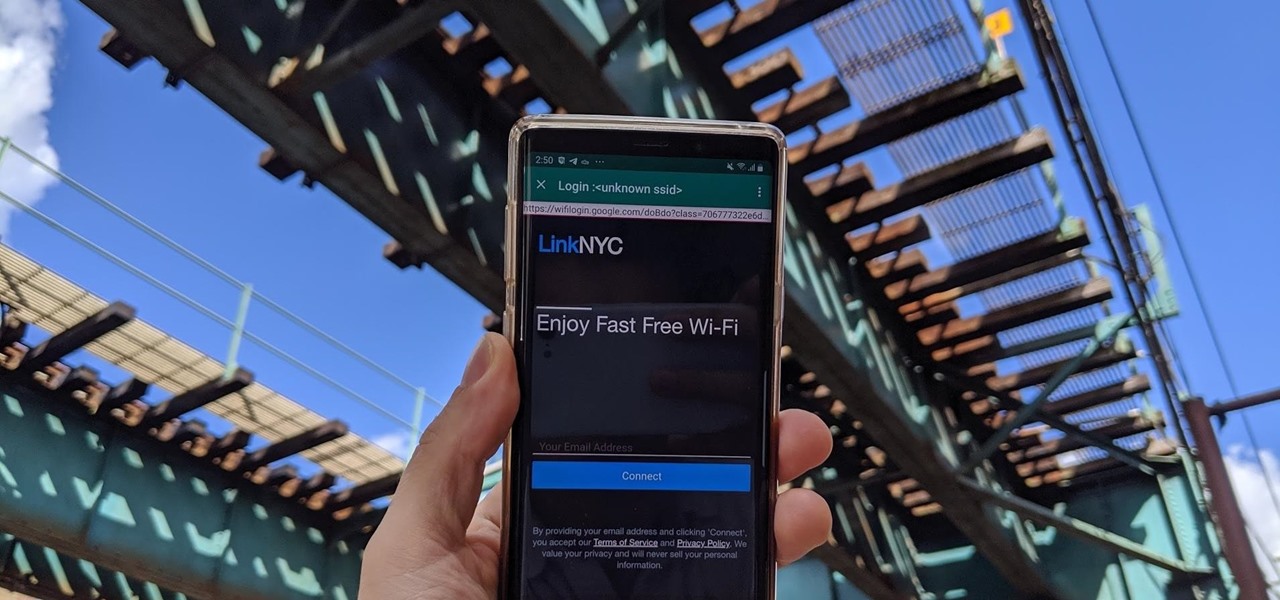
Public Wi-Fi networks that have a captive portal sign-in screen can sometimes be broken on Android. This seems to happen randomly and on some devices more than others. You'll get the "Sign into Wi-Fi network" notification, but it just doesn't work. If that's happening to you, you'll be glad to know an app can help fix the issue.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

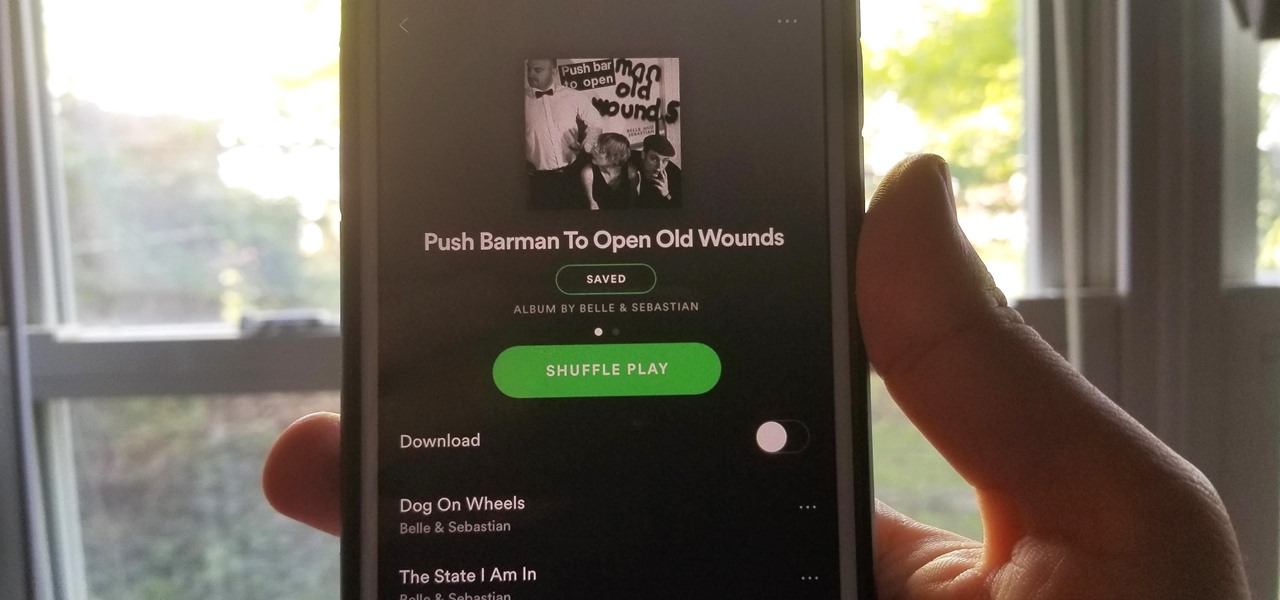
While I love Spotify, I don't like it devouring my data plan when streaming music away from a Wi-Fi network. If you have the foresight or time to download Spotify tracks for offline playback later, great. For those of you who like to listen to your music more randomly like I do, based on your current mood, streaming is the only way to go, and there are settings you can tweak to use up less data.

In hopes of strengthening its growing augmented reality team, Apple has reportedly hired Michael Abbott, an engineering and investment veteran with past ties to Twitter, Microsoft, Palm, and others.

As part of its ARCore release announcement, Google also revealed a forthcoming app that's sure to excite those who celebrate '80s pop culture.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

The Force was awakened in many a household on Christmas morning this year, as evidenced by numerous recipients of newly unwrapped Star Wars: Jedi Challenges systems sharing their first lightsaber battles in augmented reality on social media.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

As we have seen previously with the likes of SethBling's Mar I/O videos and other examples, video games seem to be a great source for training AI neural networks. Augmented reality and machine learning are part of a collection of technologies that seem to be growing toward a point of maturity, and that will likely cause them to be intertwined for the foreseeable future. As developers, machine learning will definitely change the way we create software in the coming future. Instead of going lin...

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

More video content is making its way to Facebook as the social network relentlessly tries to get its video platform up to par with YouTube. Now, they seem to be making more of an effort to improve their video tab, as new features have started to appear on some Android phones.

Delphi Automotive PLC has announced it is partnering with Transdev Group to develop on-demand driverless transportation systems, a deal that shows promise for autonomous development on a global scale.

Last week, T-Mobile CEO John Legere got salty. He announced ever so cheerily T-Mobile's intentions to release the first true 5G network in coming years, all while gaily smacking AT&T around for their bogus "5G Evolution" reveal. But could Legere be wrong to say T-Mobile will be the nation's first 5G carrier? It looks as though that title may have to be shared with Sprint ...

In February, the popular Facebook-owned WhatsApp Messenger service jumped on the "stories" bandwagon and replaced their in-app, text-based "About Me" status (you know, those lovely little messages where you can say "Sleeping" or "Not Sleeping" under the tiny nub of your profile picture). Taking its place was a clone of Snapchat's Stories feature, continuing the social media giant's recent trend of shamelessly copying Snapchat.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

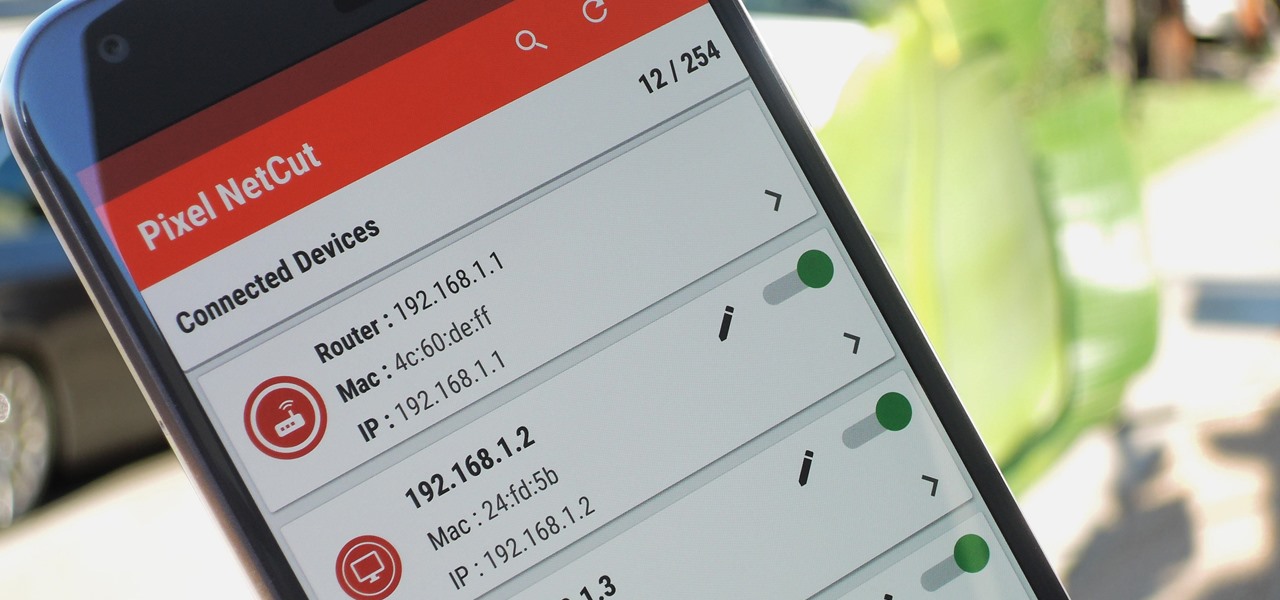
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

If you already have speakers that you love, you don't need to ditch them for an expensive wireless set for convenience's sake. With products like Chromecast Audio, you can turn any set of wired headphones or speakers into wireless versions for much less, and stream music or audio to them from pretty much any device connected to the same Wi-Fi network.

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.