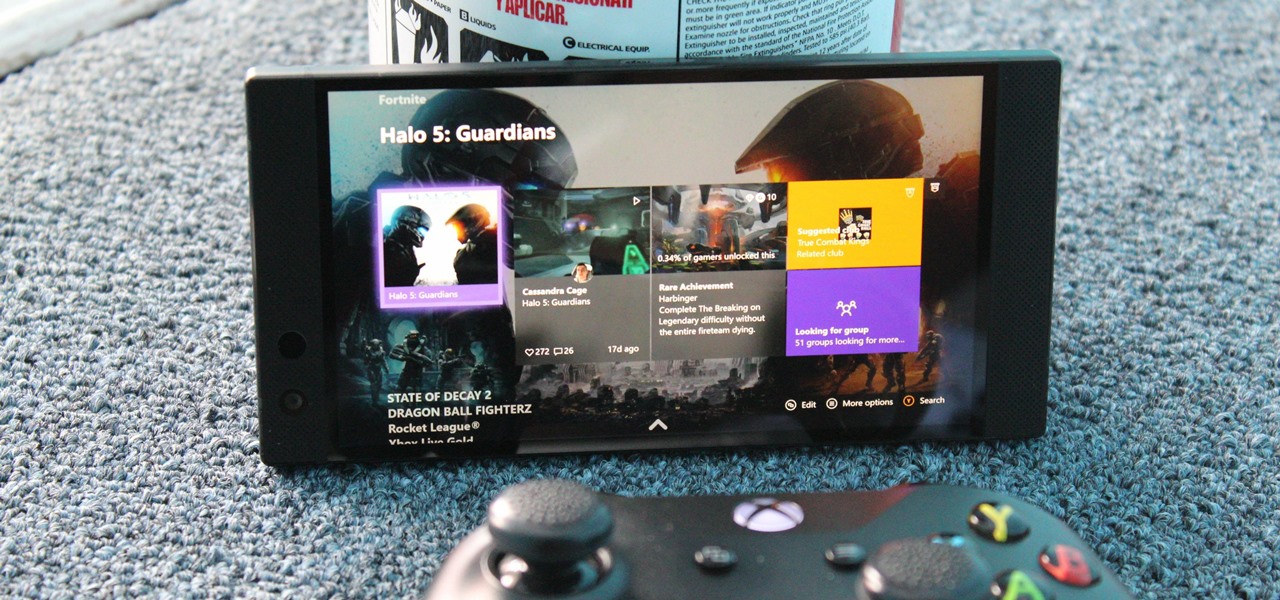
Game streaming has never been better. Not only can you watch your favorite Twitch streamer play, but with the new tools being added to YouTube, you can even play along with them. And now, with a solid internet connection, you can stream your Xbox One games to your phone to enjoy console games on the go.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.
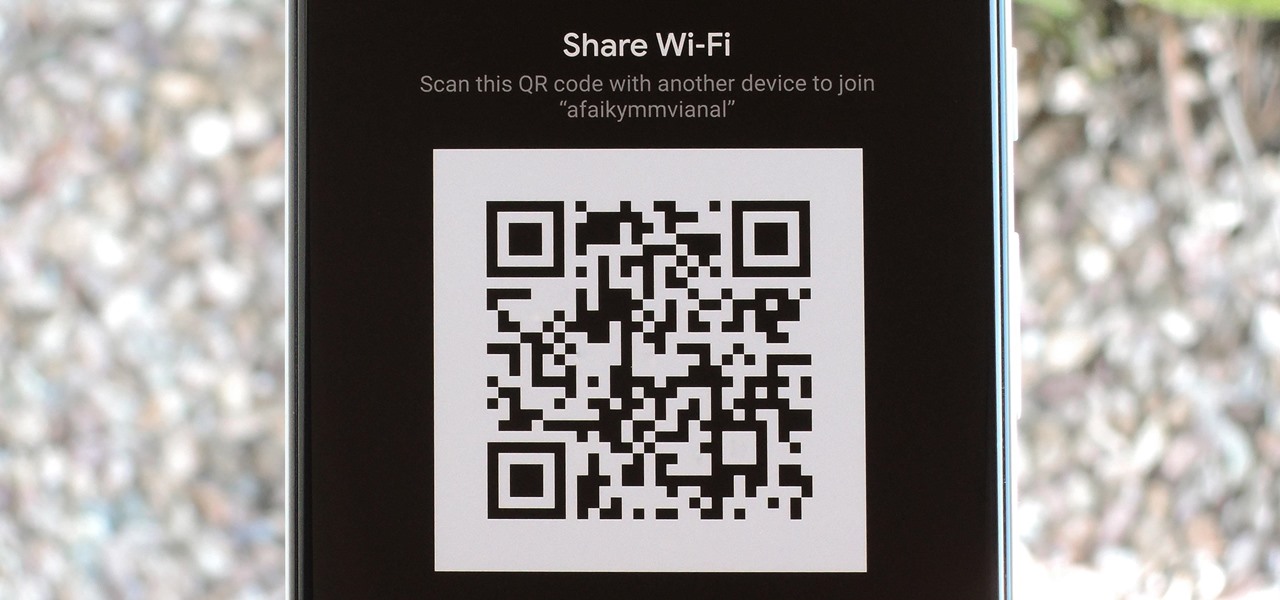
If your phone is running Android 10, you can now share your Wi-Fi network with friends using a handy QR code. The other person doesn't have to be running Android 10 — in fact, you can even share this code with iPhone users. In most situations, this is now the fastest way to share your Wi-Fi password.

If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.
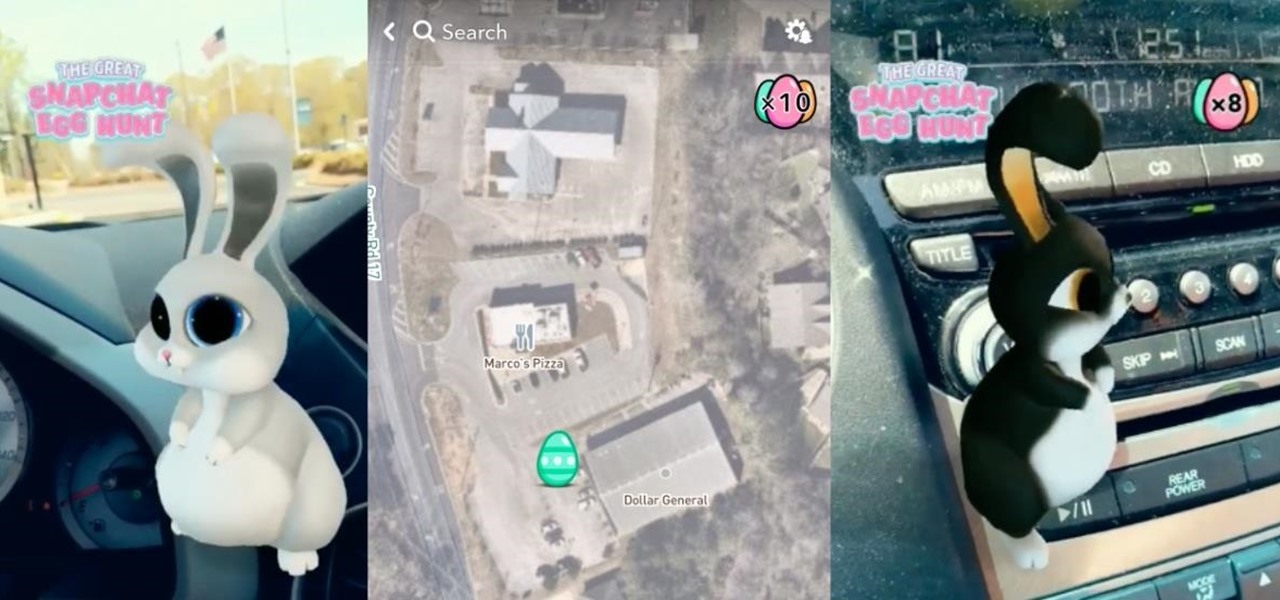
Alongside the usual collection of holiday-themed Lenses, Snapchatters received an extra-special treat from Snapchat over the weekend—a world-spanning Easter egg hunt.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Shapr is a new networking app that aims to help professionals connect more efficiently, and draws much of its format from dating-focused social networking apps. Shapr could be especially useful for those who have recently moved into their industry or location, and for those seeking employers or employees. For example, the app already has 65,000 users just in New York City alone.

Throughout the summer and fall of 2016, in the sudden whirlwind that was Pokémon GO, it was hard to go anywhere in public without seeing someone attempting to catch Pokémon. Now, thanks to an upcoming platform called Motive.io, from the Vancouver company of the same name, location-driven application development will soon be accessible to everyone.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

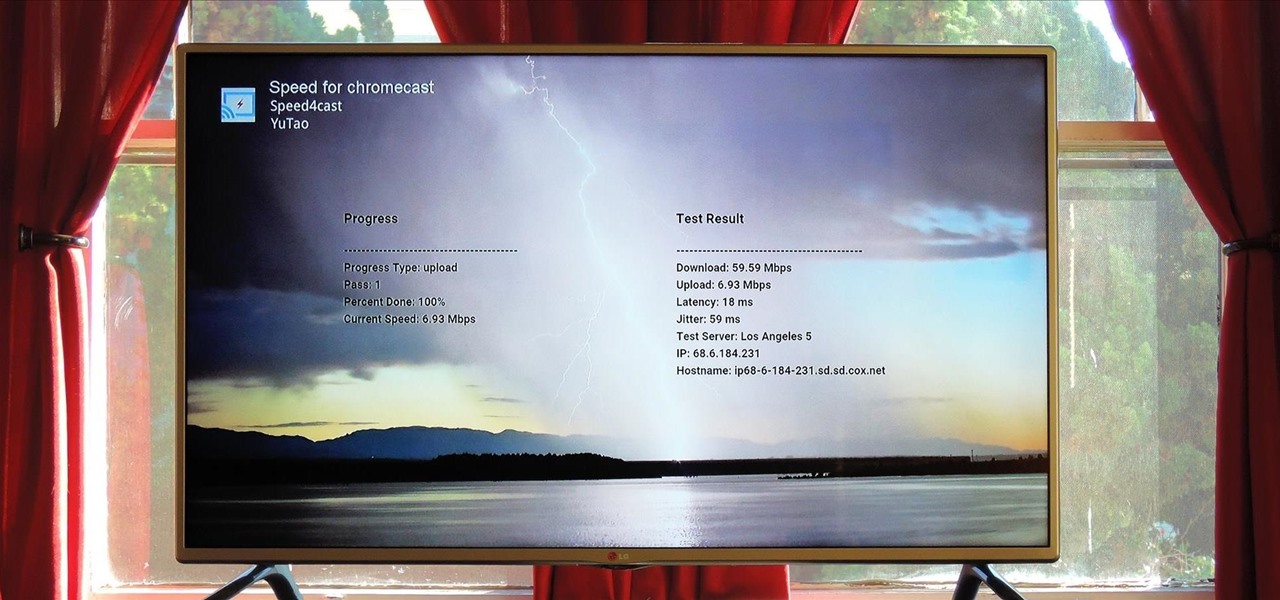
At its core, the Chromecast is essentially a web browser on a stick. When you cast content from your computer or smartphone, all you're really doing is telling the Chromecast which website to load.

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

Hydrazine sulfate has many uses, but most notably, it's been used under the trade name of Sehydrin, a treatment for anorexia, cachexia and some even think cancer. But for we DIY chemists, it's useful for something entirely different— as a substitute for the more dangerous pure liquid hydrazine in chemical reactions. NurdRage shows you how to make it via some hypochlorite and the Ketazine process.

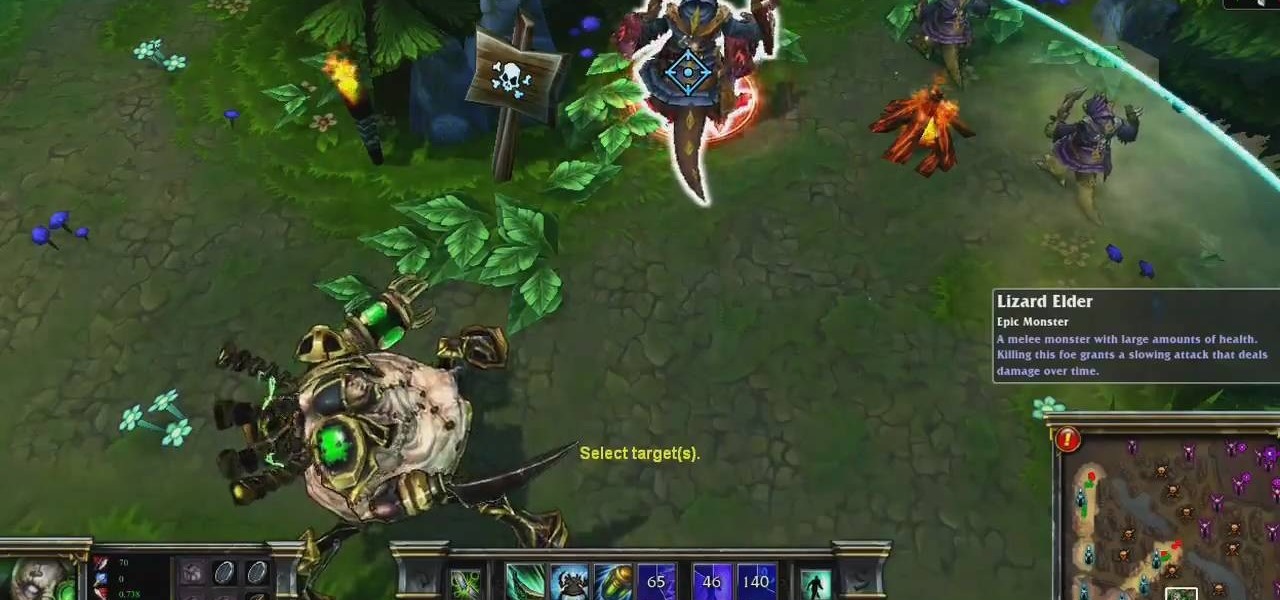
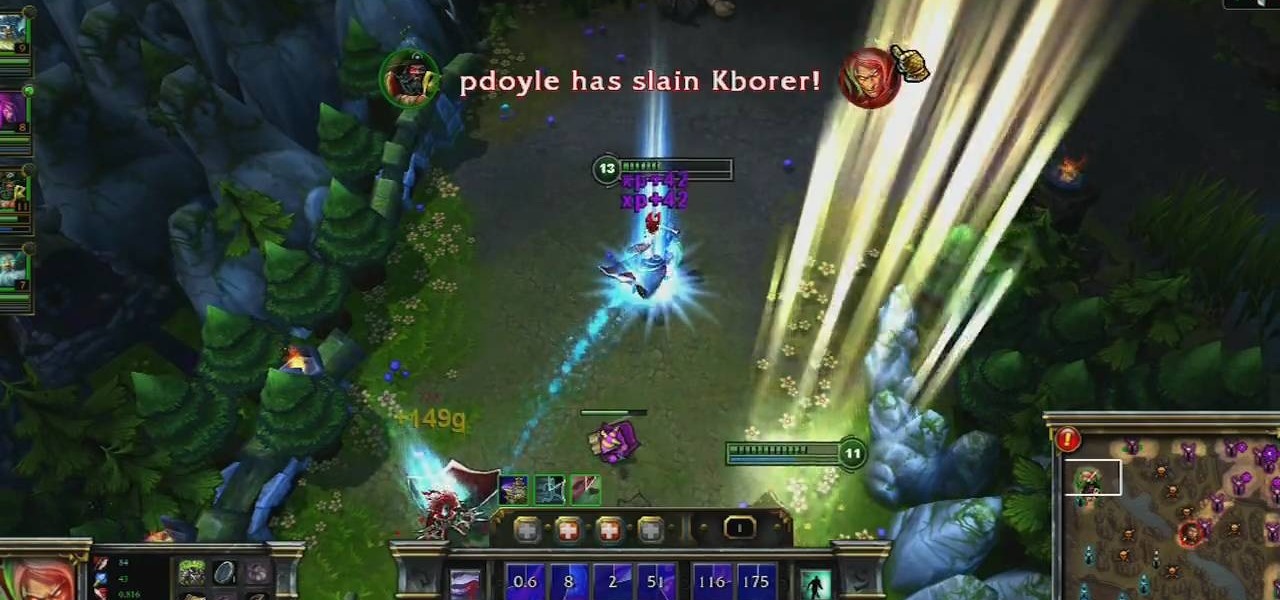
Urgot is a unique champion who can deal out high amounts of damage early in his game, and eventually evolves into a tank/assassin hybrid who can be sent after important enemy targets. Here's a guide for building and leveling Urgot to take advantage of his capabilities to help your whole team.

Galio's strength on the Fields of Justice comes from his ability to tank, though he can provide a bit of team support as well. This guide goes over his strengths, and gives good advice when it comes to making an optimum build for the Sentinel's Sorrow for your next League of Legends game.

Vladimir the Crimson Reaper makes a good champion when you want a tank/caster hybrid. When he casts, he draws on health. His health and ability points are also symbiotic, improving one as the other goes up. Here are few tips on runes, masteries and strategy to make Vladimir a terror in battle.

In this video Dave shows his unique way to grill fillet mignon. Dave begins the video with a brief history of fillet mignon. Dave says his unique way is easy as long as you follow his simple steps: 1) Allow steak to come to room temperature before putting it on the grill. This allows the cooking time to be a lot more consistent, and you won’t have a very cold middle with an overcooked outside. 2) With a great fillet mignon cut, do not over season. He adds just a little salt and coarse groun...

To make a french spiral bouquet you first start with straight stemmed flowers such as roses. It is very important that you rid the stems of foliage such as leaves as well as removing all the thorns. You can do this by using a gardening glove or washcloth and sliding it down the stem. Once that is completed it is time to begin the bouquet. The first step is to pick a base flower. It is important to use a flower that has a straight stem. From there you begin to add flowers by crossing them with...

Kevin demonstrates how to make a paper frog. Take a regular sheet of construction paper. Fold the outer ends towards the center forming a triangle. Fold a crease at the base of the triangle and cut it out. Open the folds and you can observe two creases. Create two X-shaped creases by bending the opposite corners. Hold the triangles on the side of the X and squash it down such that the other two triangles meet. Repeat the process on the other side. This forms a square with a diagonal cut conta...

Hand washing is something you learn from a young age, but how do you know you are doing it correctly? Keeping your hands clean is one of the best things you can do to keep others and yourself healthy. In this tutorial, Memorial Health will teach you the best way to wash your hands and prevent the spread of germs. There are two ways to clean germs from your hands: soap and water and alcohol-based handrubs. Watch this video to find out how to use both effectively. The video will show you how a ...

Just acquired a new Sony PlayStation 3? Well, in order to start using the many extra online features of the PS3, you will need to set up your internet connection. This interactive video walkthrough takes you step-by-step through the process of connecting your version of the PlayStation 3 to the web.

Release your inner wild thing with a costume based on the classic children's book. You Will Need

Check out this informative video tutorial from Apple on how to import photos from a digital camera in iPhoto '09.

Check out this informative video tutorial from Apple on how to organize photos with Events in iPhoto '09.

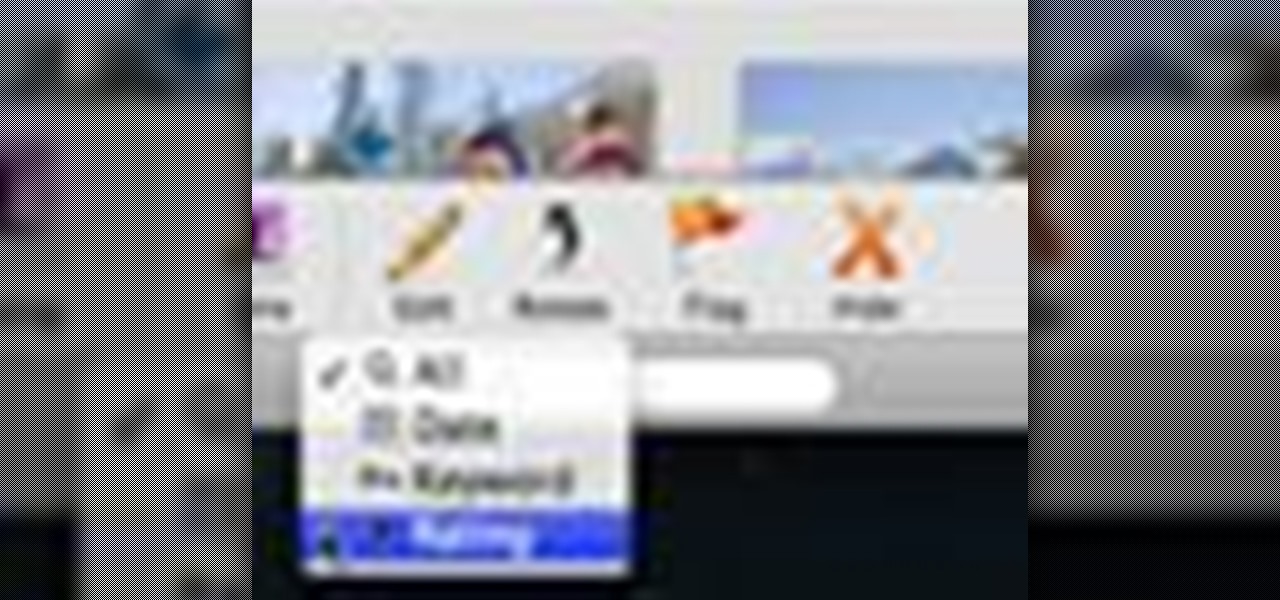
Check out this informative video tutorial from Apple on how to add keywords, ratings or flags to photos in iPhoto '09.

Check out this informative video tutorial from Apple on how to crop your photos in iPhoto '09.

Check out this informative video tutorial from Apple on how to rotate or straighten photos in iPhoto '09.

Check out this informative video tutorial from Apple on how to reduce red-eye in iPhoto '09.

Check out this informative video tutorial from Apple on how to enhance your photos with a single click in iPhoto '09.