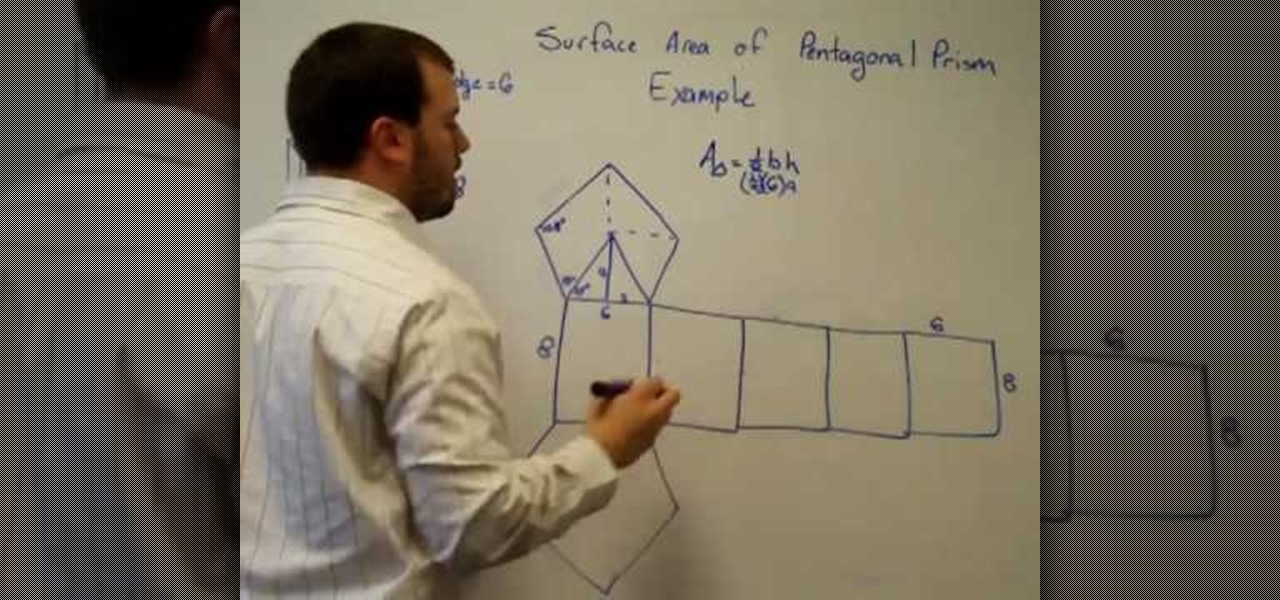
In this video, we learn how to find the surface area of a prism using a specific example. First you will need to find the base and height of your prism. If the base edge is 6 and the height is 8 you will do the equation Area= 1/2 bh. Doing this math out on your calculator, you will get the answer of 12.39. This is what the size of each triangle in the prism is going to be. The area of one pentagon (or the base) is 61.92 inches squared. If you need help with this, you can try drawing the pictu...

At the moment, the iPad is officially locked to the AT&T network in the USA. If you would like to use your iPad but do not intend on leaving your current mobile carrier, check out this video.
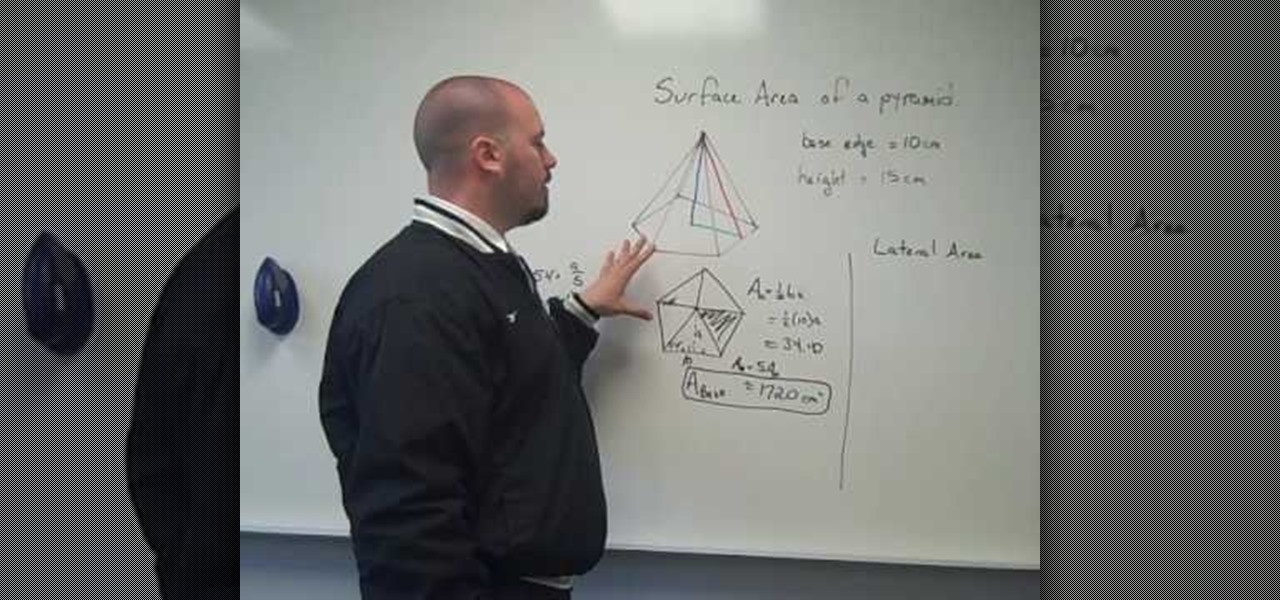
A pyramid is a three dimensional figure with the base in the form of a triangle and three slant sides to it. To find the surface area of a pyramid you have to find the area of the different pieces that make it up. The pyramid base can be triangle or even other geometric figure like pentagon. So first draw the base of the pyramid separately and compute its area first. Now compute the area of each sides separately. The area of each side can be same if the pyramid is a regular pyramid. Some time...

This video in the Education category will show you how to use a protractor to measure an angle. This video is from Brightstorm. In Geometry it is important to know how to measure an angle. This is a very simple and easy process. In order to measure an angle, you will need a protractor. Every protractor has a base and a center point marked on the base. You will put the center point on the vertex of the angle. Then align the base line of the protractor perfectly on one side of the angle. Now ch...

Gigafide explains that with so many different social networking sites, it is hard to keep information up to date on all of them. He first introduces TweetDeck, an amazing desktop application that allows a user to update information for their Twitter, Facebook, MySpace, and LinkedIn accounts. If you don't want to go through the hassle of installing TweetDeck on your computer, there is HootSuite, a web application that allows you to do this and if you're interested in keeping track of much more...

In this video tutorial you will learn about the basics of using Smart Objects in Photoshop. Smart objects can consist of pixel-based content or vector-based content. These smart objects also remember their original size and can be transformed multiple times without loss.

This origami video shows how to make a butterfly by starting with the water bomb base. Origami is fun and easy. This butterfly makes a cute gift. Follow along with this origami tutorial to learn how to make your own.

If there's any lingering uncertainty as to the mainstream viability of augmented reality, a list of the top mobile apps and games of 2019 serves to dispell those doubts.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

If you've gone anywhere near a television in the US in the last 48 hours, you've probably seen some of the reports of Hurricane Florence and its devastating wind and rain making its way toward the Carolina coast.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

In Fallout: New Vegas, you will eventually end up having to check out the other factions and tribes in the game. One of them happens to be the Boomers over at Fort Nellis Air Force Base, a clan of old vault dwellers who took over the base and have been making use of their heavy artillery to keep intruders away.

A combination of red and gold eyeshadow is great for emphasizing green eyes - this is because red and gold are complementary colors to green. For the base, apply a clear or skin-colored base to the entire eye area. Use a highlight base just beneath your eyebrows. Blend it in. Use a black liquid base on the upper eyelid. For eyeshadow, start off with a shimmery gold by putting it in the inner corners of the upper lid. Take your red and start off slightly in the middle of your eye, where you le...

If you love origami and the PlayStation, you're in luck, because this video tutorial will show you how to fold the small bird (or pajarito) from the upcoming PlayStation 3 game Heavy Rain: Origami Killer.

Add an extra level of functionality and user interactivity by adding sound to your menu buttons on your Flash-based website! This tutorial shows you how to create these sound files, and then incorporate them into your dynamic Flash-based menu by using the ActionScript code.

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

The video shows how to join a home group on a Windows 7 network by helves shows you how to join a home group on a Windows 7 network of computers. It is approximately one minute thirty seconds long. To join a home group on a Windows 7 network you first go to control panel, then you click on Network and Internet, after that you click on network and sharing center, and finally click join a home group in the top right. You now select what file types you want to share with the other Windows 7 comp...

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

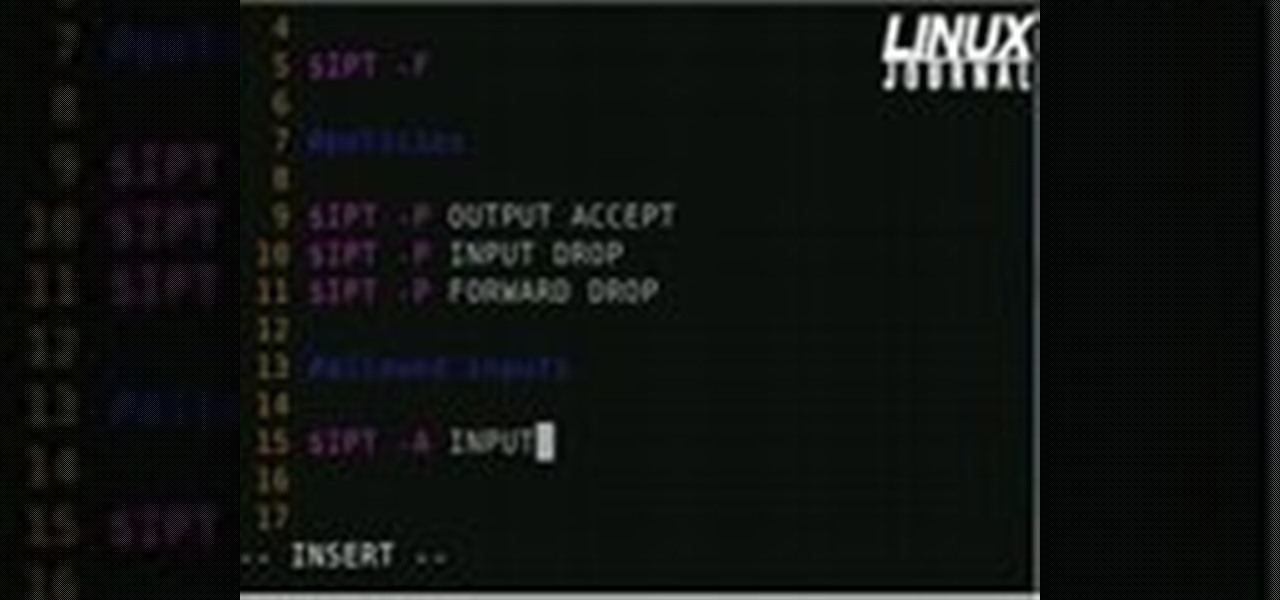
Linux comes with a powerful built-in firewall, although the interface can be a little intimidating. With this multipart GNU/Linux networking video tutorial, you'll master basic and not-so-basic IPTables functionality and create the perfect firewall for your home network. For detailed, step-by-step instructions, watch this Linux how-to.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

If you're Christian or Catholic you're probably familiar with the infamous Hail Mary prayer. It doesn't require much. Just memorize the prayer and the next time you find yourself in need you will know just what to say.

Whenever a new project comes their way, many people tend to go out to the store in order to buy all the parts they need instead of checking what they already have. This can be costly and can easily be avoided if they do find certain items lying around the house.

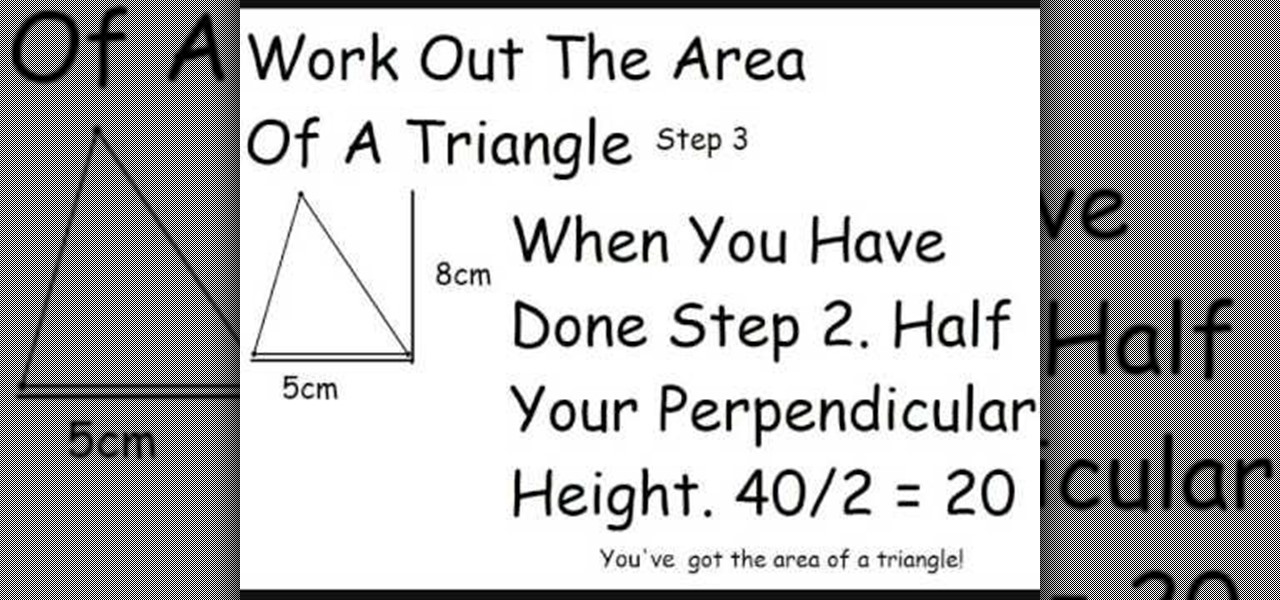
This tutorial describes the method to calculate the area of a triangle and a parallelogram To calculate the area of a triangle:

Calculating The Area Of A Parallelogram A parallelogram is a 4-sided shape formed by two pairs of parallel lines. Opposite sides are equal in length and opposite angles are equal in measure. To find the area of a parallelogram, multiply the base by the height. The formula is:

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

The end of year surprises keep on flowing from the Plantation, Florida offices of Magic Leap. This time, it's yet another game from the company's old partner Insomniac Games, and it's called Strangelets.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

Microsoft has unveiled practically every detail of the HoloLens 2 except for when eager developers and enterprise customers can expect to receive the device.

Though primarily a Pixel exclusive, Google Camera has become the go-to camera app for many Android users. Not only does come with a standout features like Night Sight and capture better photos than most stock camera apps, but it's also packed with functionality that makes it a one-stop-shop for all your photo and video needs.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

Deaf people primarily communicate through sign language, so understanding spoken languages can prove challenging. To bridge that gap in communication, the HoloHear team built a mixed reality app at a Microsoft HoloLens Hackathon in San Fransisco that translates the spoken word into sign language.

There are those who hold their phone or set it down when they're not using it, and others, like myself, who pocket it. If you're like me and are rocking the pants pocket fade, then you'll love the new Android app I found.