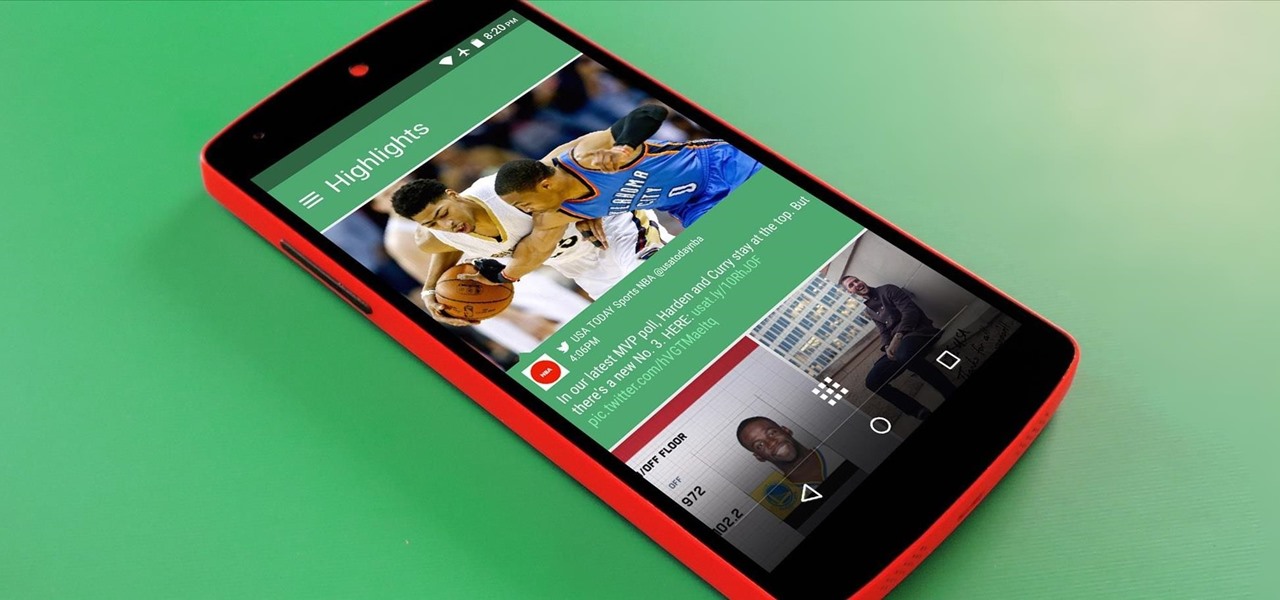
If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you could use to capture the issue you're having, then share the screenshot with your tech support.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

One of the coolest features in modern smartphones is their Bluetooth connectivity. This is how two digital devices can communicate with one another—sending data like your phone call audio or your favorite song—all while using up minimal battery life.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Apple's Touch ID, introduced on the iPhone 5S, has definitely made my life a little easier. Not only can I unlock my device, I can use the tech to log in to websites, make purchases through iTunes, and buy groceries at Walgreens using just my fingerprint. Still, as awesome as Touch ID is, it's pretty limited as to what it can do on native apps.

HTC's Sense UI is generally regarded as one of the best manufacturer-skinned versions of Android. This is mainly due to the subtle and classy styling of the interface, as well as some unique features that are added in here and there.

With only a month left until Samsung's highly-anticipated Galaxy S6 and Galaxy S6 Edge are released to the general public, it's only natural that some of the devices' features slowly trickle out, like Edge notifications, the new Smart Remote app, and, of course, wallpapers.

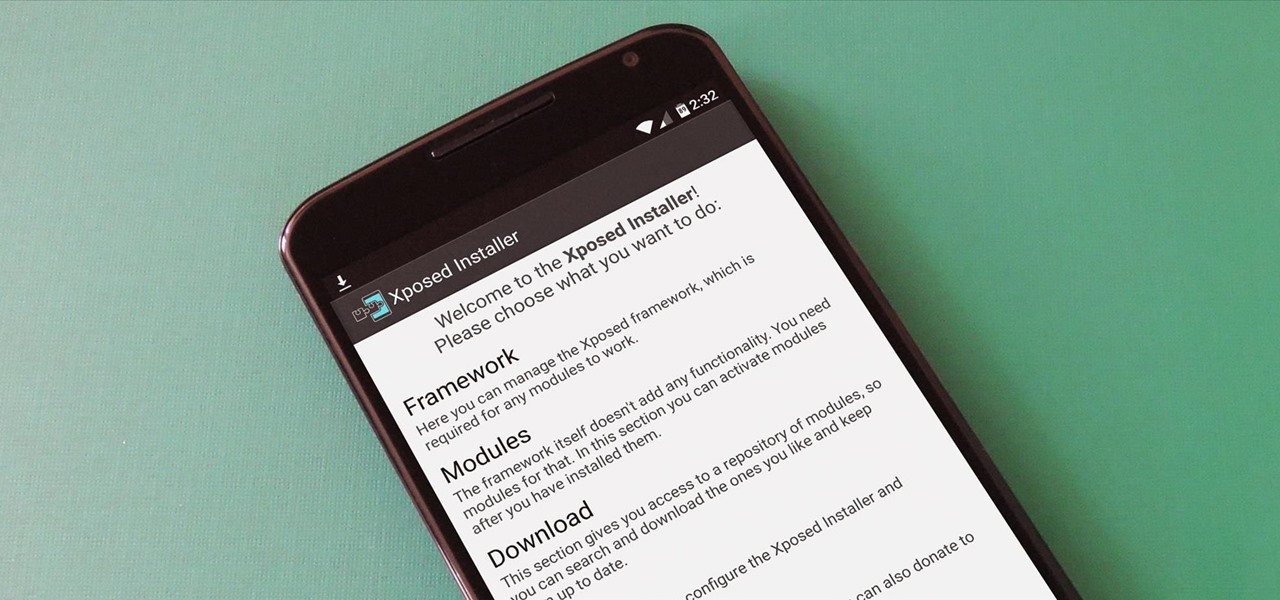
UPDATE 11/17/15 The Xposed Framework now officially supports Android 5.1 through 5.1.1 Lollipop devices as well. Everything will still work the way it has with Android 5.0 through 5.0.2, but there are a separate set of files for the newer Android version. I'll cover both below, but make sure to download the proper file for your particular version of Android.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team of developers to come up with a method for jailbreaking iOS 8.1.1 devices, and much like its predecessor, the process is a cinch.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

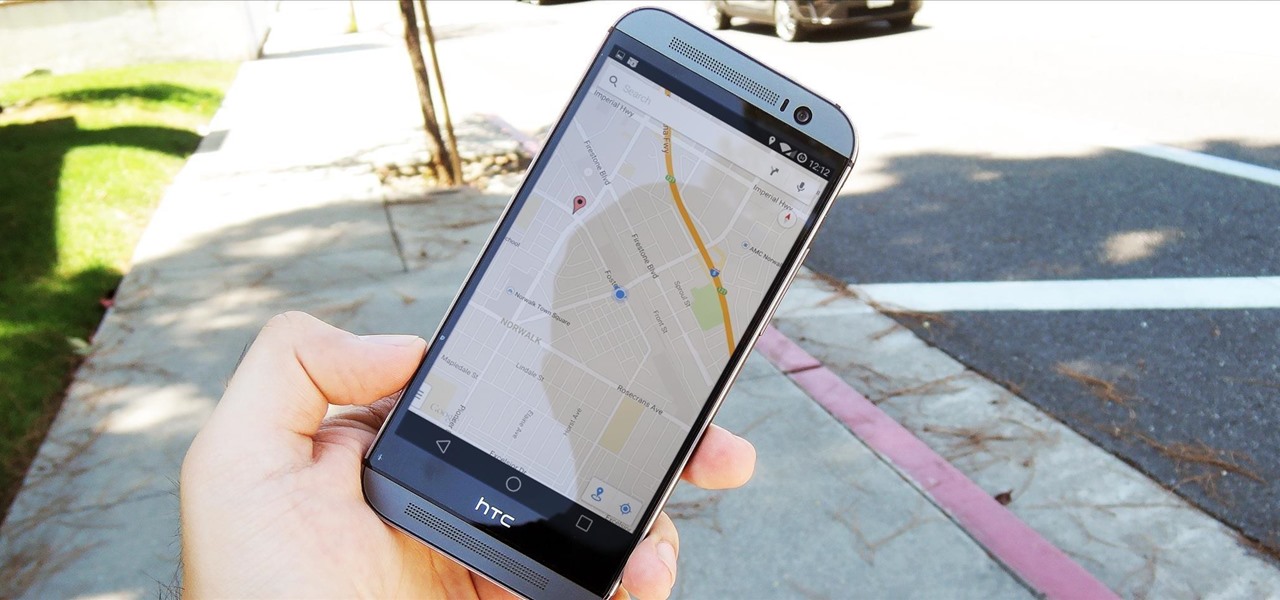
Google's Android Device Manager makes it extremely easy to track down your phone or tablet, but while it's simple to set up and use, it does require your device to have an active data connection, which can be an issue in some areas.

It happens to everyone: you set a lock screen password in a hurry and cannot remember it the next day. To unlock your device again, you need to reset the password (or PIN, pattern, etc). There are two official methods of doing this.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Audibly, from iOS developer Nick Frey, allows you create playlists and sync your music across other iOS devices. Like the Samsung-exclusive Group Play or the older Seedio app, you can connect a slew of compatible devices to create a surround-sound stereo of sorts when playing your music.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

A month ago, we showed you what I, and many around the web, dubbed the "Nexus Killer". That device is the OnePlus One, a low-priced, high-powered, CyanogenMod-run Android device.

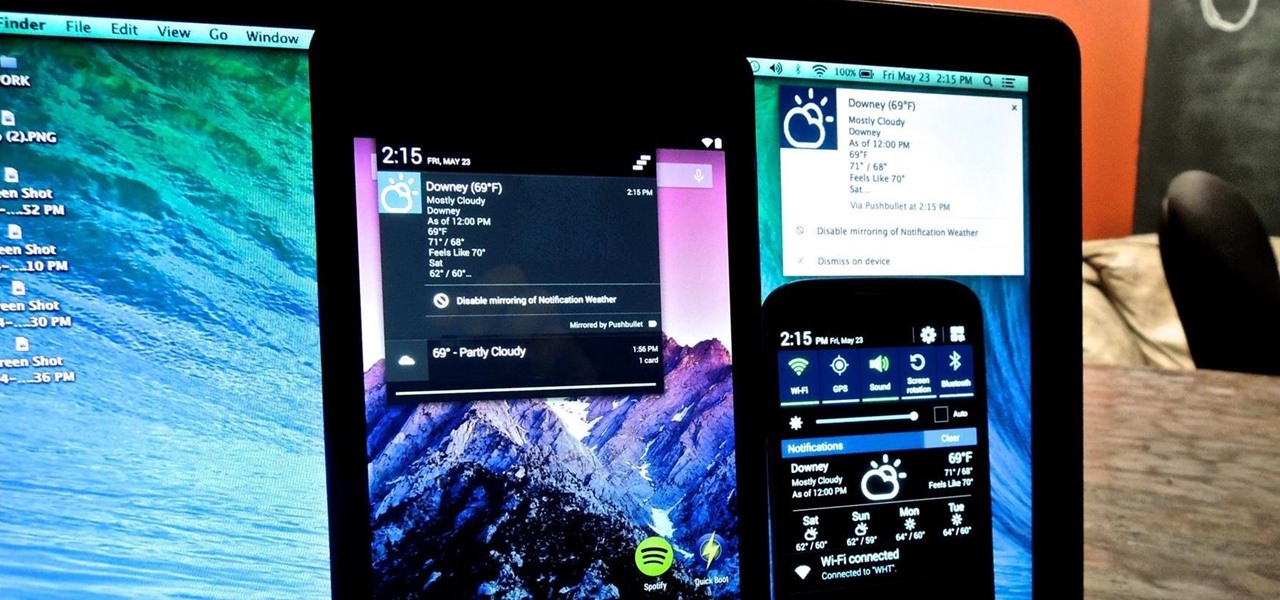
We're not always near our phone, so Pushbullet made it easy to get your phone's notifications straight to your computer, like calls and text messages. But with their latest update, you can also sync alerts with other Android devices using their new cross-device mirroring feature.

Your beloved Samsung Galaxy S3 is nearing the end of its life cycle. Sure, it can do most of what newer devices can, especially if you were lucky enough to receive the KitKat update, but your diminishing battery and scratched up screen have seen better days.

"Millions of us have smartphones with the power to speed up research that will benefit billions of people around the world." - Professor Francois Grey

Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations.

One thing we can probably all agree on is that ads suck. In particular, ad-supported mobile apps are both a gift and a curse. Most are free, but supplement that non-existent price tag with non-stop banner or video ads. Sometimes, those ads can ruin the entire app, especially if it's a game that requires your undivided attention.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

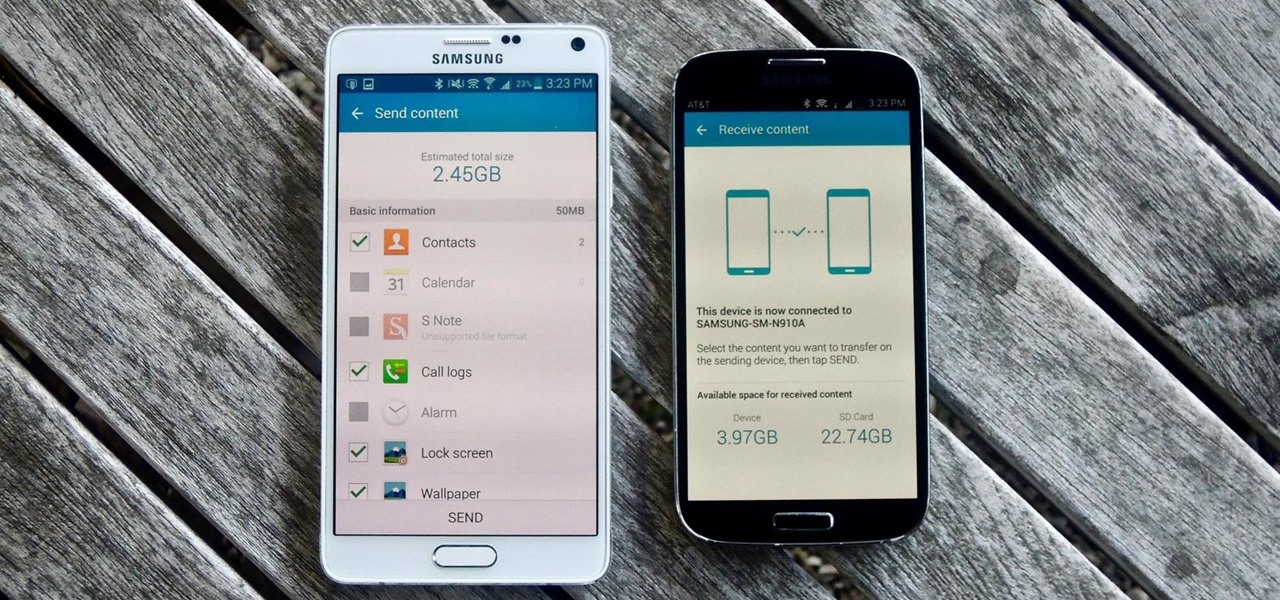
The first thing I do when I get a new phone is ditch the USB cable. At least, when it comes to data transfer. My brand new HTC One came with a USB cord that feels sturdy, but like any other cable, it will eventually fall apart from overuse. It will probably still charge just fine, but at that point it will be unreliable for transferring data. Lucky for me, there's a solution. Transfer files over the air. This will let you save that USB cord only for charging and the occasional situation when ...

I've taken a few photography classes back in the day, so I'm pretty confident in my abilities with a DSLR, but my iPhone is a completely different story. Lighting makes all the difference, so unless you're outdoors in the sun, it's hard to take a good snapshot with a mobile.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

While the majority of America was watching the Super Bowl yesterday, the crew over at the evad3rs was finishing its work on their untethered iOS 6.1 jailbreak called evasi0n. Well, the wait is finally over!

Is rooting your Android device right for you? Well, in order to answer that question, we need to get a better understanding of what rooting is and why exactly so many modders choose to root their smartphones and tablets.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

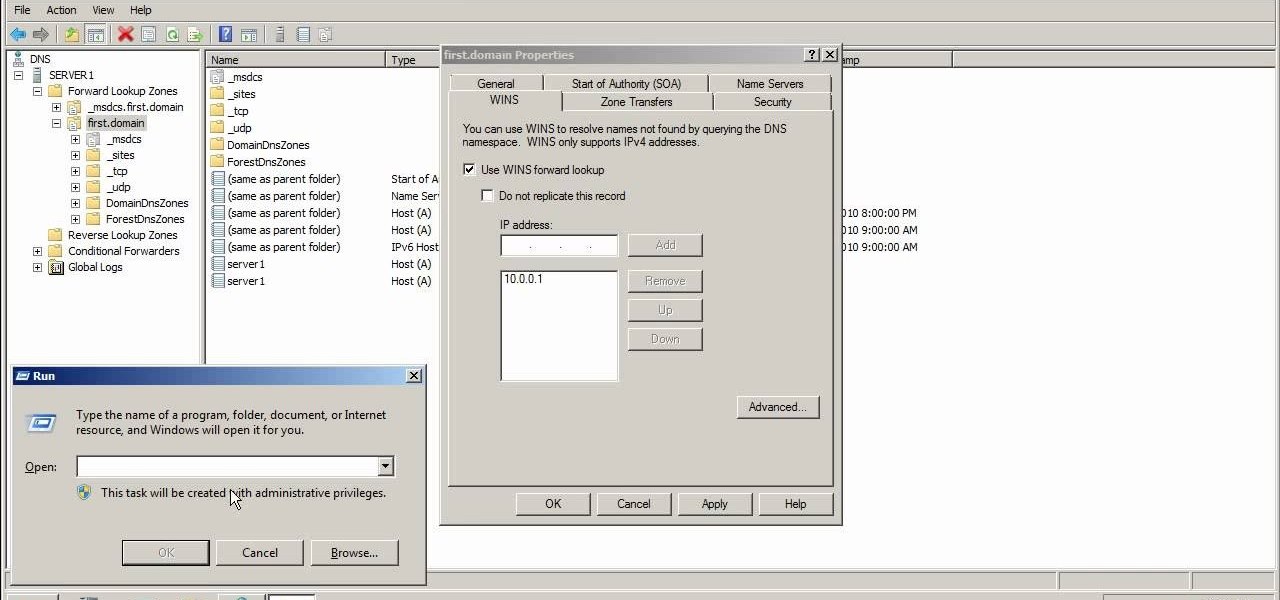
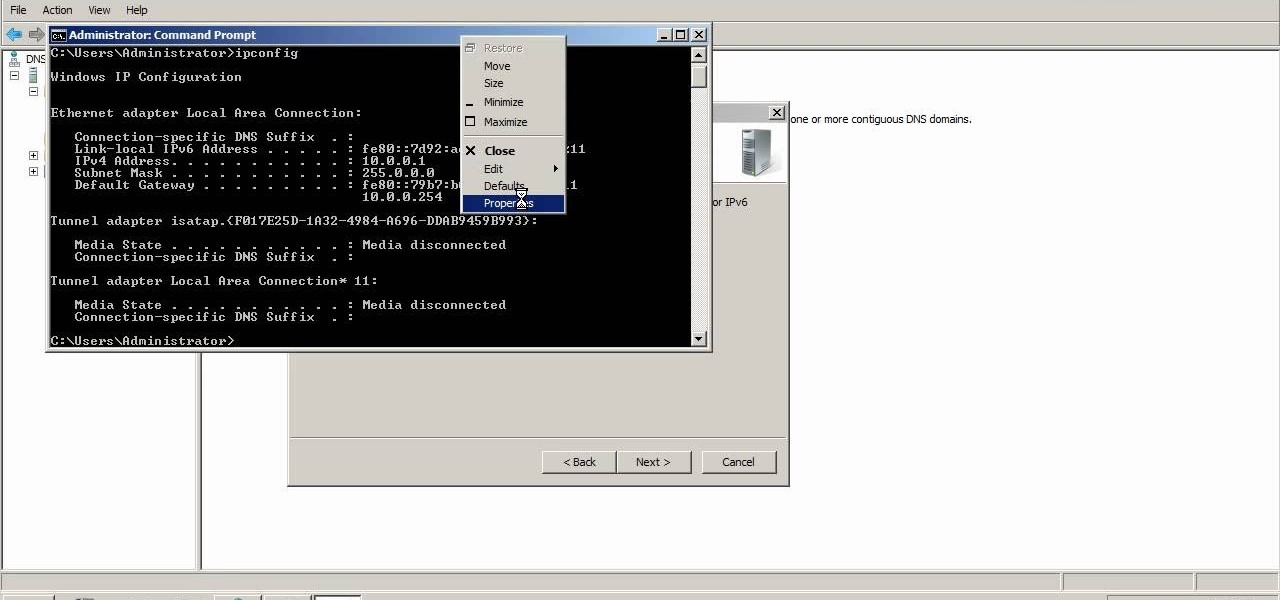
This video explains how to modify your DNS server to perform WINS lookups. Using Microsoft Windows Server 2008, you can perform WINS lookups across several networks which can resolve to a common resource. While Server 2008 cannot act as a WINS server, Server 2003 can.

A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.