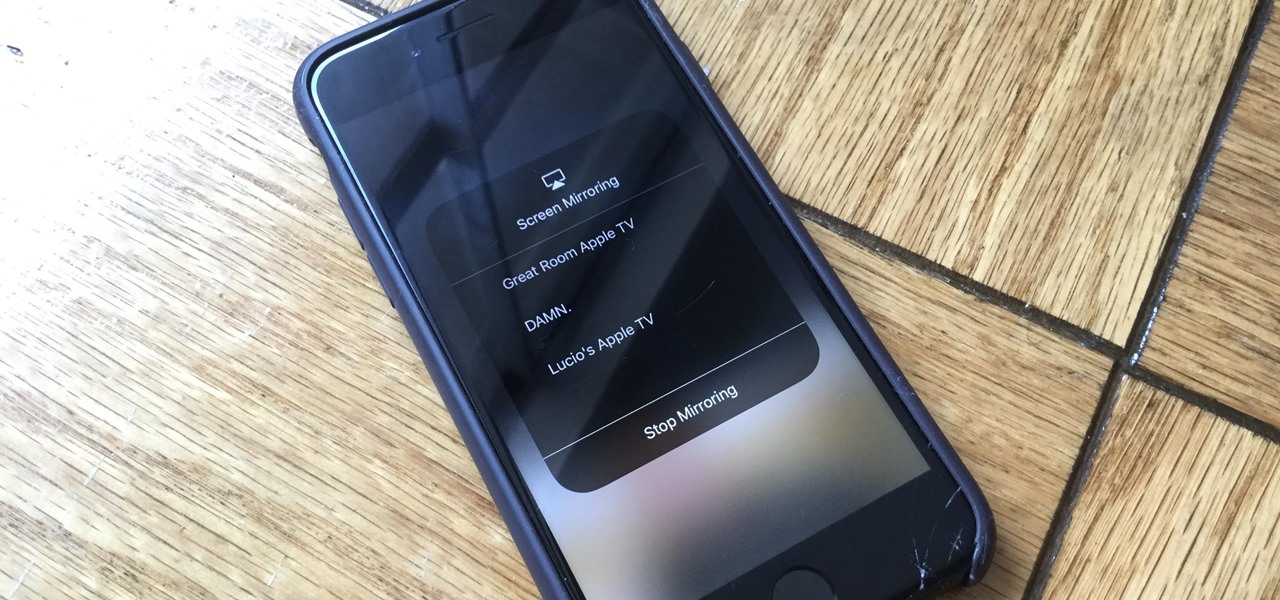
So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

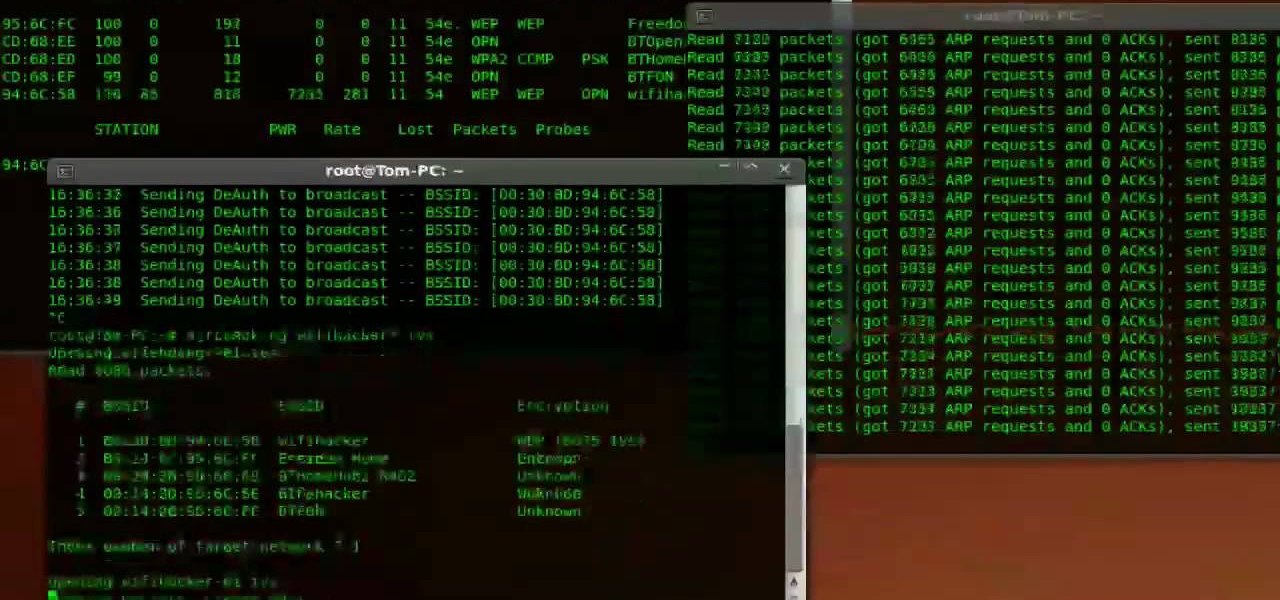
Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

While HBO Now does not support offline viewing yet, your smartphone is the perfect way to watch your favorite shows and movies on-the-go. Whether you're in a hotel running off Wi-Fi or you have an unlimited plan and are on the bus, if you want to binge some Game of Thrones, the HBO Now app is there for you.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Starting today, you'll have the opportunity to save all your live Instagram videos to your phone at the end of each broadcast session. The latest update to the Instagram app now allows you to rewatch already-played broadcasts and gives you the ability to share them later on.

Live streaming has emerged as a major part of the way people share information. With celebrities and news/media personalities utilizing mobile live streaming effectively to reach thousands, the appeal has bolstered the fortunes of Twitter's Periscope and Facebook's Live. Now, Google is ready to join the fray, and it's backed by its enormous YouTube property. According to initial reports, Google is at work on a brand new application for YouTube simply called "Connect," which will take its curr...

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

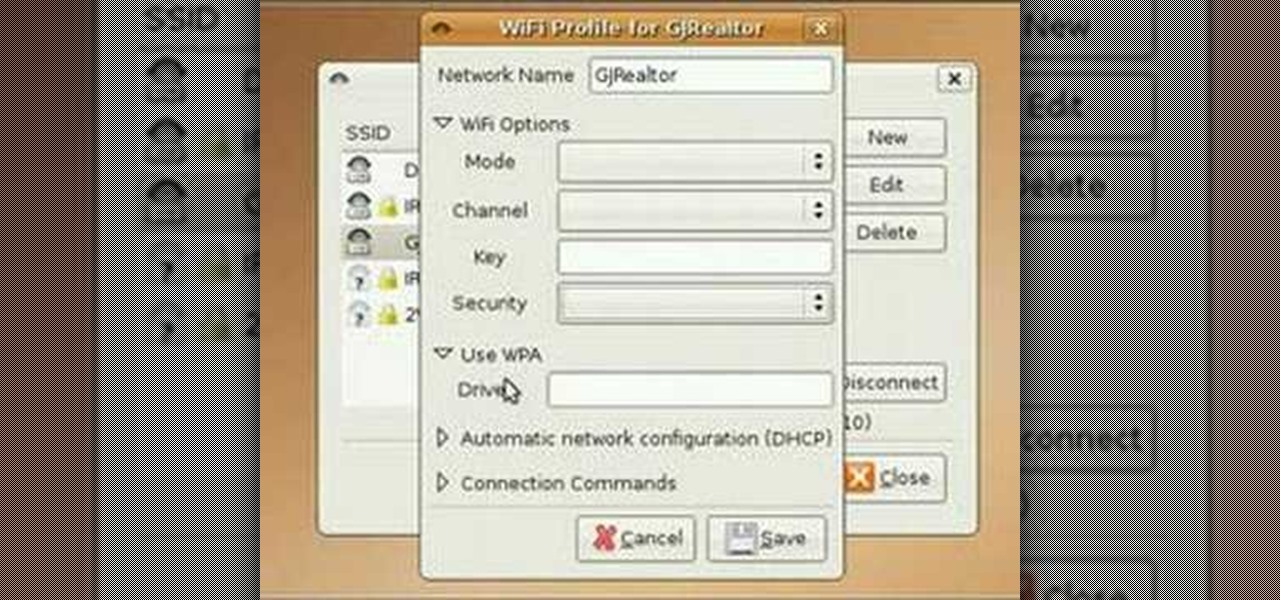
One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

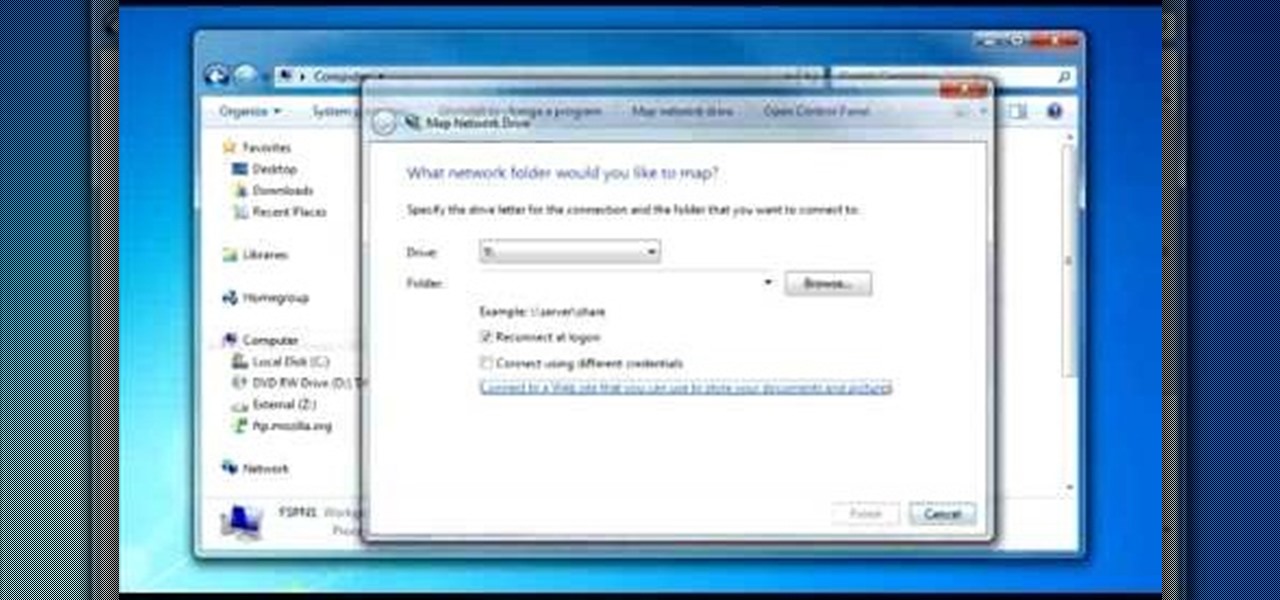
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

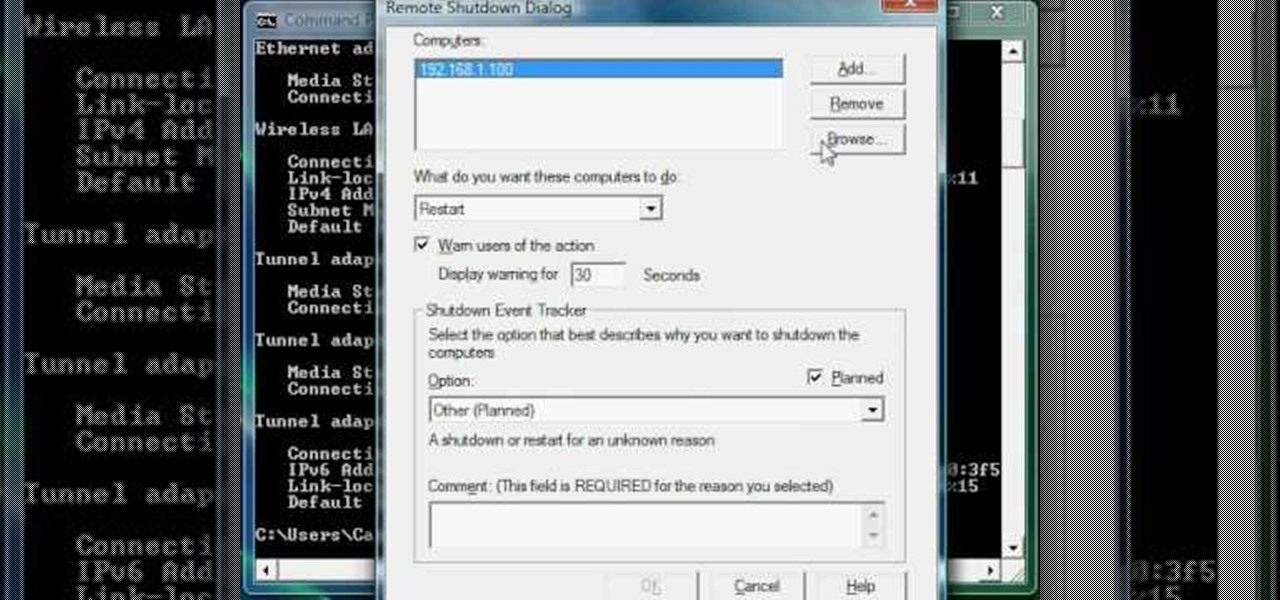
Now you can find your IP address if you need it and you don't know it, it very easy. Or if you have problem with a person on the internet, now you can discover who that person is. You can find her/his IP address and after that you can find her/his real name. But after you find the IP that you were looking for, you have to check if the person who own this computer is in your network, because if you want to find his/her name, the program works only if the owner is on your network. So if you are...

In this clip, you'll learn how to find and connect to WiFi networks on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Not only can your T-Mobile G1 phone get Internet access by itself, you can also use it as a router or modem for your home wifi network. All you need is to download a single app from the market, install it, and you're ready to set up your home wifi network!

Google G1 users, want to switch your phone network? In this video, learn how to unlock the Google G1 HTC Dream Phone. All you need to complete this tutorial is your phone and a SIM network unlock pin code.

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.

Learn how to set up an Epson printer wirelessly when you bring your new printer home you will want to start by installing the software that came with the new printer. You can set up your printer to work without wires and it will print from all over the house. There are 3 ways to set up the printer including the Epson way, with cables, and WPS. To determine is you need to use WPS, which is more complex, check your router to see if it has a sticker on it that says Wi-Fi Protected Setup. If that...

In this video tutorial, you'll learn how to use the WiFi Radar application to find wireless networks while running the Ubuntu Linux distribution. For more, and to get started finding and using wireless networks in Ubuntu for yourself, take a look!

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.

Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

With the economy as terrible as it is these days, obtaining any sort of job, from receptionist to screen writer, requires thorough networking.

Getting pectorals that ripple and bulge beneath shirts and arms that broadcast from sleeves requires a bit of work on your part (duh). That's where this video comes in.

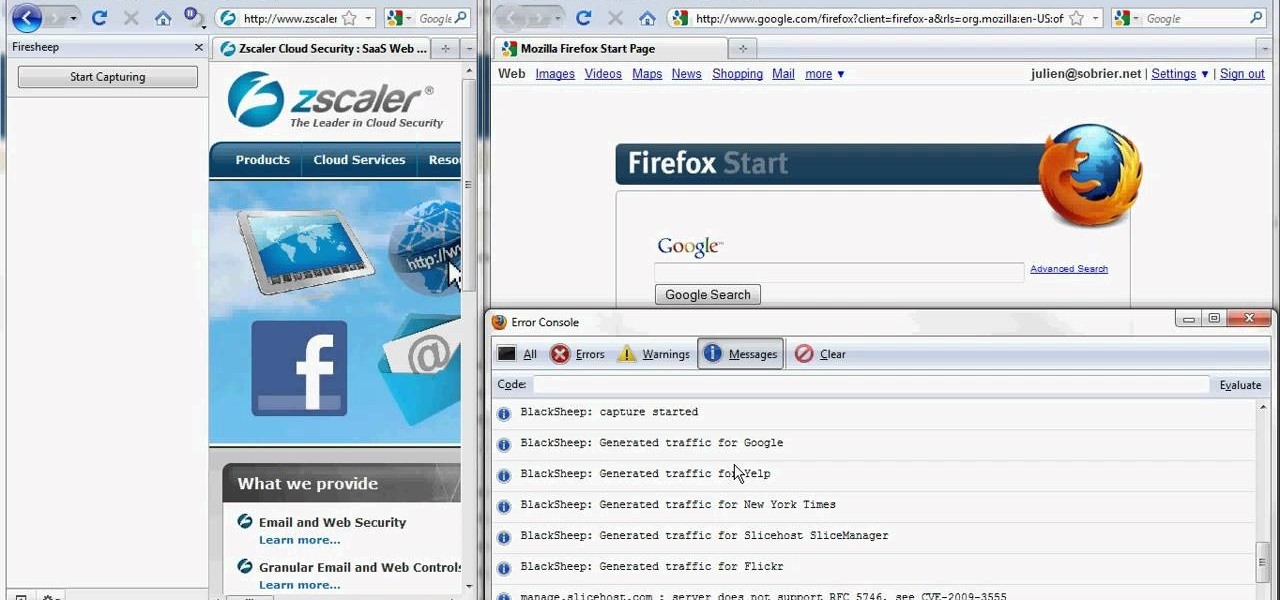
If you're scared of using public Wi-Fi networks with Firesheep out and about, then maybe you should fight back. Don't switch to another web browser— keep using Firefox safely with the help of a new Firefox Add-on that combats Firesheep's password stealing capabilities. It's called BlackSheep, and when installed and running, it will alert you whenever Firesheep is active on your network connection.

In this tutorial, learn how to save yourself the money you'd pay someone to unlock your Google G1 phone from T-Mobile and do it yourself in just a few quick minutes. This is actually a very easy process and this clip will walk you through the process step by step so you can freely use your phone on any network and not be limited to T-Mobile. This is also helpful if you wish to give away or sell your phone to someone on a new network.

In this clip, learn how to tether your rooted Droid to a WiFi network and use it as a modem for your other Wireless devices. This process is pretty easy and only requires a network and that your phone be rooted.

If you're planning to become a veteran yogini, you'd better start practicing and loving the up dog pose now, because you'll be spending the greater part of your yoga flow doing up dogs and down dogs.

In this culinary how-to from the Food Network's Ellie Krieger, you'll learn how to bake delectable, almost-healthy carrot cupcakes using whole carrots, lemon zest, canola oil, brown sugar, two eggs, 3 quarters of a cup of whole wheat pastry flour, 1/2 cup all-purpose flour, 1 teaspoon of baking powder, 1/2 teaspoon of cinammon, 1/4 teaspoon of nutmeg and a 1/4 teaspoon of salt.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

Everyone's talking about the switch to digital broadcasting, but what does it mean for you, your TV, and your old rabbit-ear antenna? You will need a digital-to-analog converter box, a pay TV service or a TV with a built-in digital tuner. Tip: Government issued coupons for digital converters are available online at dtv2009.gov.

This instructional video will show you how to remove the bumper sticker of a failed candidate, such as McCain/Palin. Now you can stop broadcasting failure without leaving a sticky residue.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.