Need to browse the web on your new Samsung Galaxy Tab? Well, first you're going to have to set up Wi-Fi on the Android device. This video shows you the complete steps to getting connected! Press MENU < SETTINGS < WIRELESS & NETWORKS < WI-FI SETTINGS and then select WI-FI to turn in on. Next, choose your network, enter the password and press CONNECT. It's that easy.

Want to make a cartoon representation of yourself? See how to create free cartoon avatars that can be customized to represent your unique personality or interests across the social networks or chat clients you frequent with this video guide. For more information, including detailed instructions, take a look.

In this tutorial, we learn how to unlock the iPhone 3G to work on other carrier networks. First, purchase an ATT Universal unlock SIM card and cut it so it is the same size as the SIM card in your phone. Don't cut any important parts off the back of the card. Now, remove the card from the iPhone and install the Universal unlock card. This is all you have to do and now you can run your iPhone on a different network. This is the most simple way to use your phone on another network. You can rese...
There are 10 major ways to protect your PC. Disable Autorun, in Windows. Make sure that your system is up to date, by setting automatic updates. Always use a log on for your computer that does not have administrative privileges. Use different passwords, and change your passwords on a regular basis. Don't use simple passwords. Be careful of using links sent to you via email. Never disclose your sensitive information in public forums: e.g. social networks. Encrypt sensitive data on your compute...
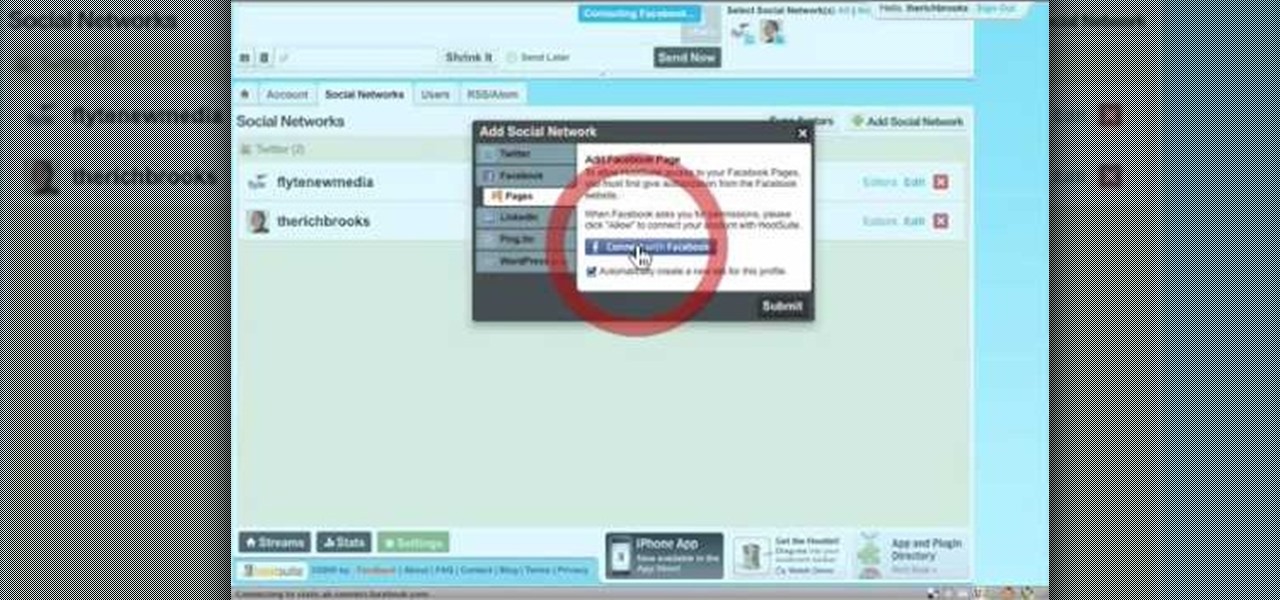
In this video tutorial, viewers learn how to sync Twitter with a Facebook fan page. Begin by going to the website: Hoot Suite and sign up for an account. Once logged into an account, click on Settings and click on the Social Networks tab. Click on Add Social Network and click on Pages under Facebook. Now click on Connect to Facebook and log into your account. Then select the page(s) that you want from your Facebook and click Add to Hoot Suite. Finish by typing in your message and select your ...

This video shows you how to easily set up Bluetooth on your Motorola Droid phone and use it with a Bluetooth headset. The first thing you have to do is go to Settings and then go to Wireless and Networks. In the pop up menu, you have to go to Bluetooth settings and check the first box. That will turn Bluetooth on. Next, you have to turn on your Bluetooth headset device and press the Scan for Devices button on your phone in the Bluetooth settings window. Insert the password and hit OK. That's ...

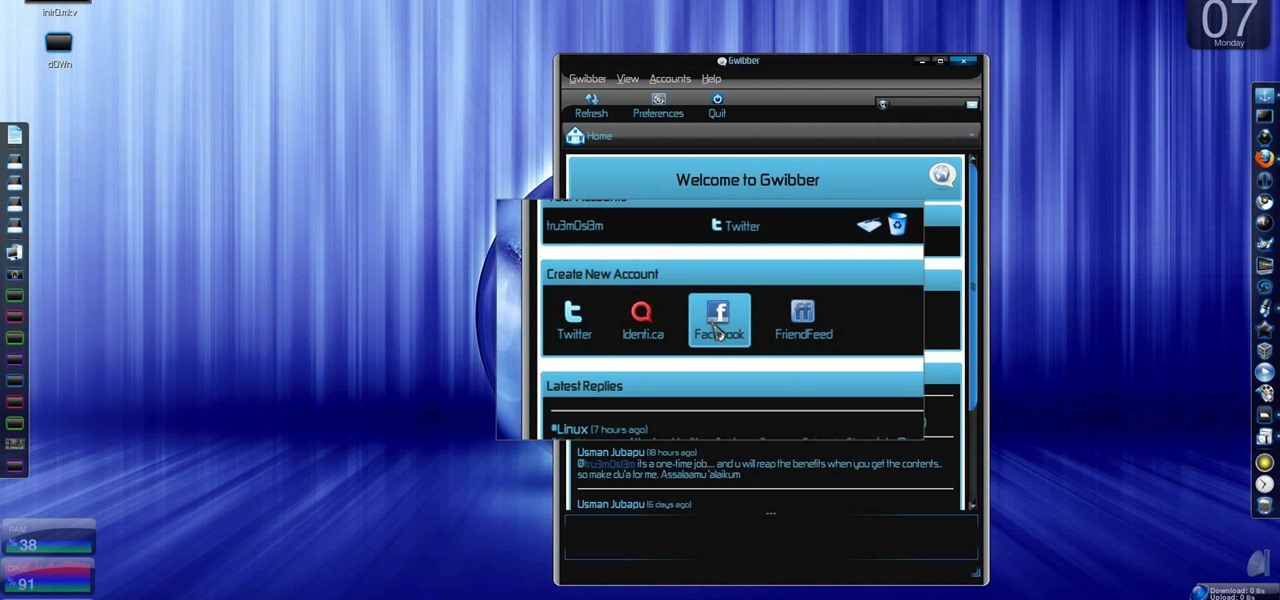
Twitter has consumed the world, so make sure you're up to date on your Tweets. One way to do that is with Gwibber 2.0 on Ubuntu Linux, the computer operating system that could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to retrieve unlimited tweets with Gwibber 2.0 on Ubuntu Linux.

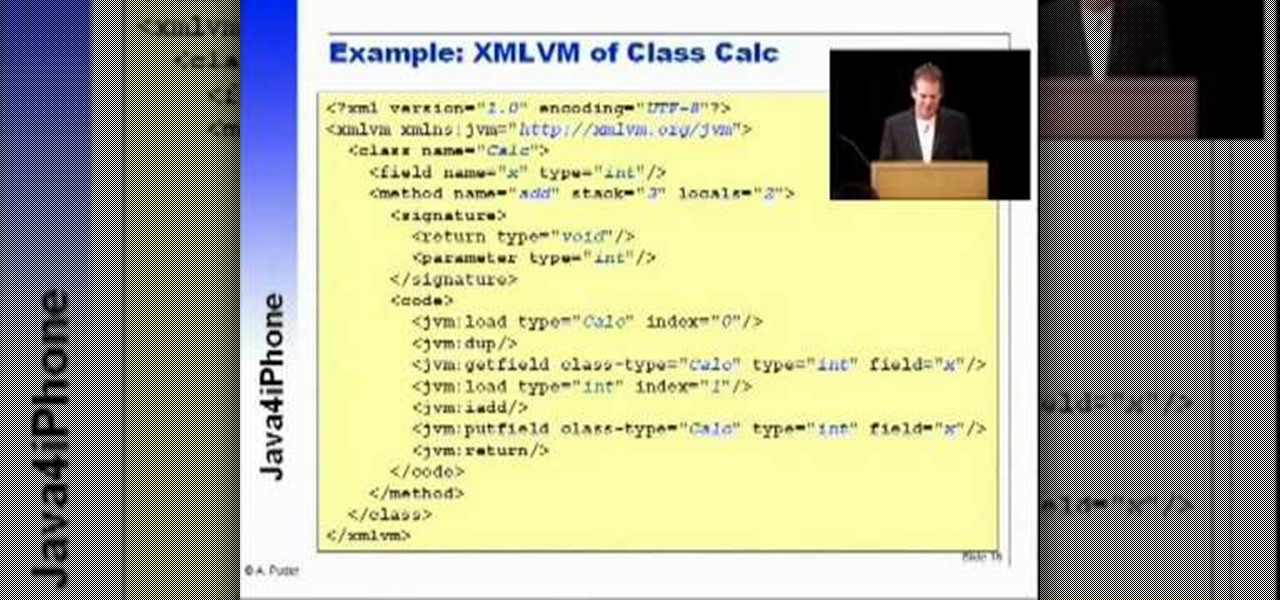
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

So, you've downloaded Boxee... Experience TV in a brand new way! This video will help you get started.

For a health conscious change of pace, try a tuna burger! They are so easy to make, all you have to get is some canned tuna, which you probably already have in our pantry. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller.

Low battery – two words you never want to hear. Banish them with these tips. You Will Need

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Sprint and T-Mobile have agreed to a $31.6 billion deal that, if it gets through federal regulators—which is far from a sure bet—would create a formidable carrier to really compete against AT&T and Verizon. The deal comes packaged with a $1 billion "breakup" fee that Sprint would have to pay T-Mobile in the event the deal does not go through. After the deal, Deutsche Telekom, which owns about 67% of T-Mobile, would maintain a 20% ownership stake.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

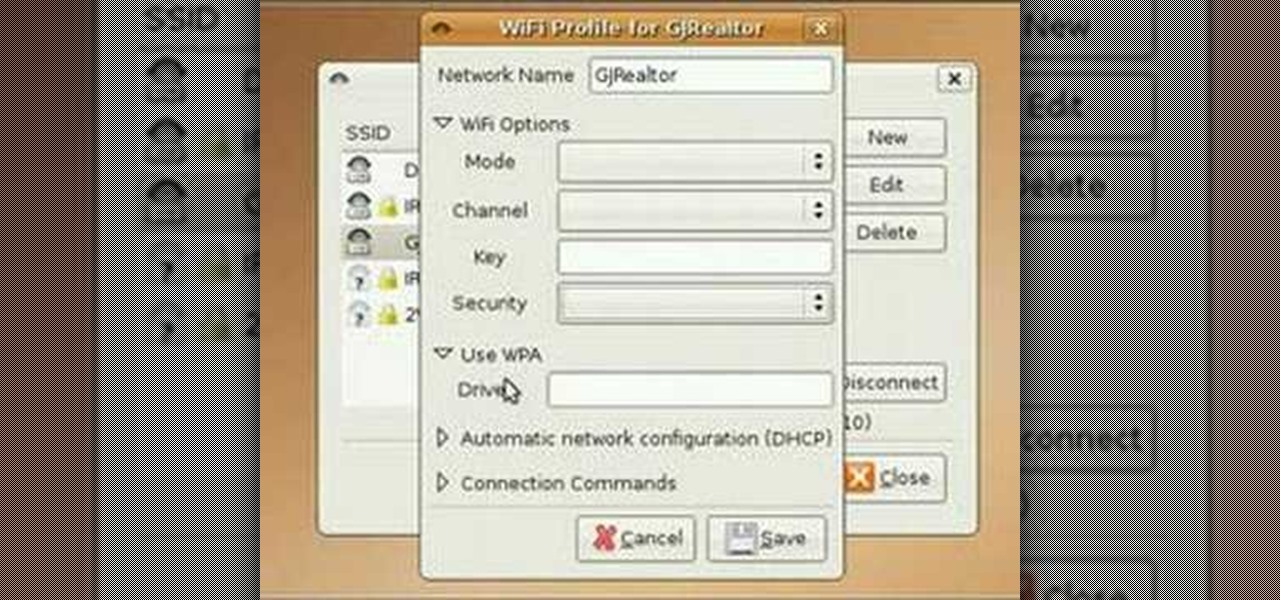
In this video tutorial, you'll learn how to use the WiFi Radar application to find wireless networks while running the Ubuntu Linux distribution. For more, and to get started finding and using wireless networks in Ubuntu for yourself, take a look!

In the latest software updates for iPhone and iPad, there's an even easier way to view all your saved Wi-Fi networks and credentials and share them with family, friends, and others who need access.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

While the third-generation iPhone SE is a decent upgrade from the second-generation model two years prior, there aren't many things about it that stand out from Apple's iPhone 13 lineup. Well, there is one thing worth singling out.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.