This year, over 2.7 billion gamers will spend nearly $160 billion dollars. That number is predicted to increase to over $200 billion in just three years. If ever an industry had growth potential, this is it.
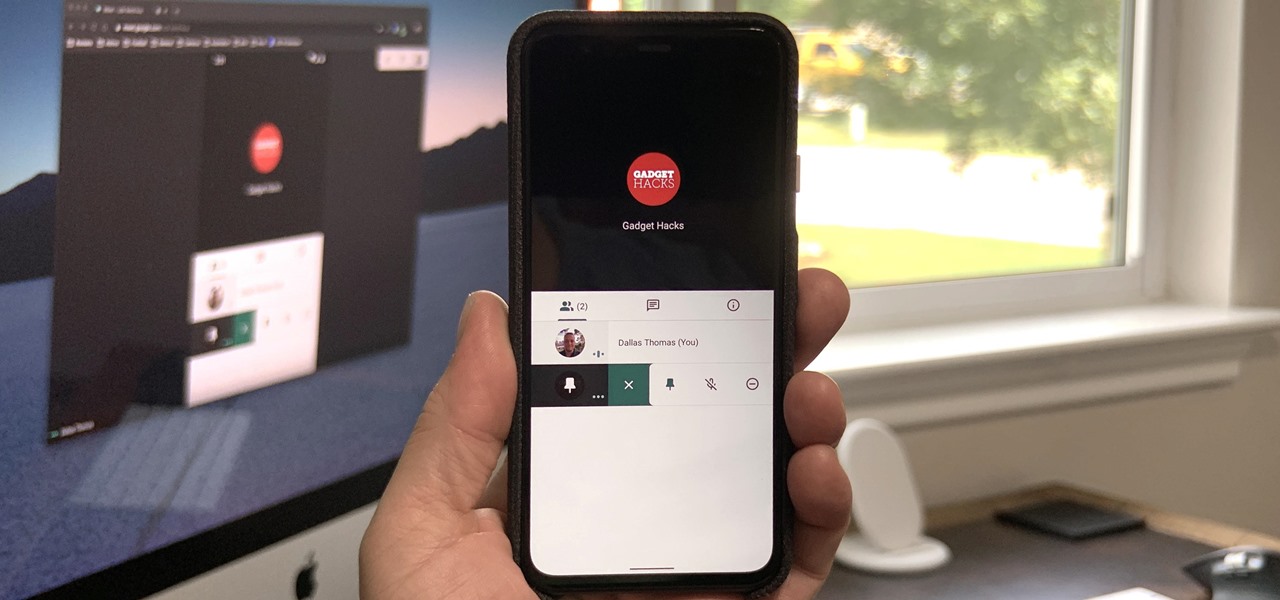
Now that Google Meet is free for anyone with a Gmail address, you can expect to see invites from Google's service alongside Zoom calls.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

When your cat goes missing, chances are it's just chilling in a cozy spot under the couch, or maybe even hiding from you. So it's okay to not freak out just yet. Cats love to hide as if they're spiders, and even their hiding spots are similar. You can find them in corners, on the refrigerator, and according to my roommate, even the dryer hose is fair game.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fighting cancer.

Facebook Reality Labs chief Andrew "Boz" Bosworth does a lot of hinting and teasing of what's coming next at Oculus, often with only a vague timeline on the horizon.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

In a similar vein to Facebook's colorful backgrounds for text posts, Instagram has a way to add vivid text-only status updates for your stories. That way, you can conjure up colorful stories that make a statement without even needing to take a photo or video in the first place. And now there are even more fonts to choose from.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.
Welcome back Hackers\Newbies!

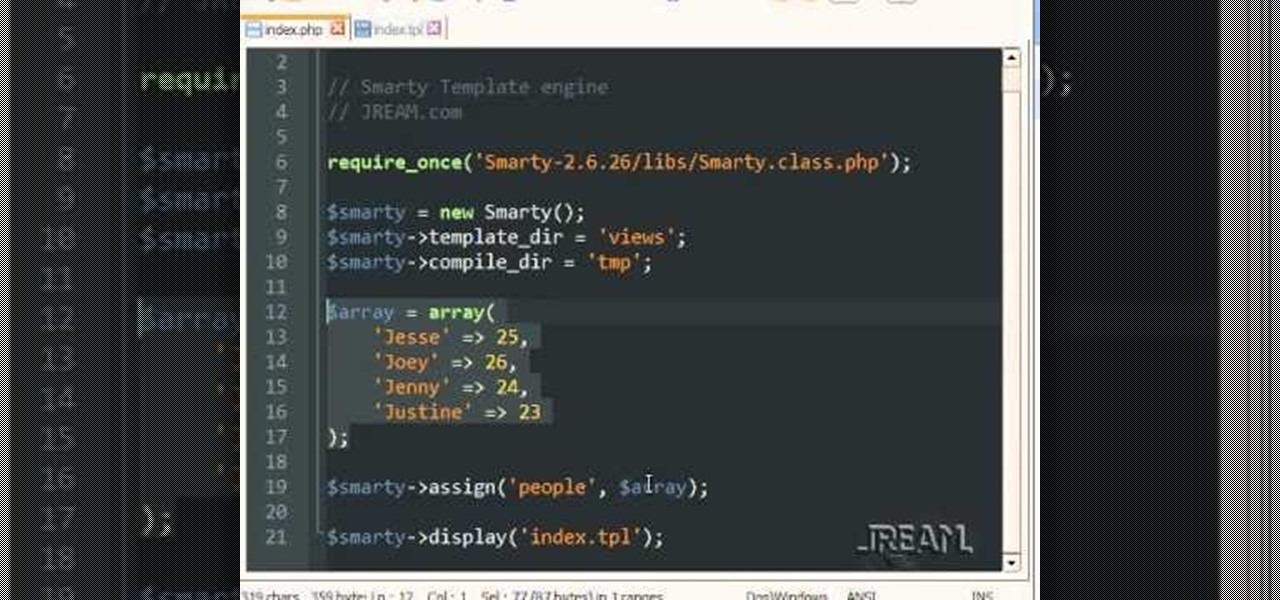
In this PHP how-to tutorial you'll learn how to get started using Smarty Template Engine for PHP. This is a basic intro for PHP coding newbies, so if you're a pro, move on. If you're not a pro, watch the vid and get a little closer.

--in under ten moves! Listen closely newbies, or actually, watch closely newbies. This algorithm gets every color on every side.

Now that the iPhone 4 made its way to Verizon, there's a whole new crowd of smartphone users that are looking for jailbreak methods. And GreenPois0n has come to the rescue (yet again).

If you hide the dock in your Mac, it might be troublesome to switch between open applications. This video shows you how to easily switch between open applications in Mac OS X by using a keyboard shortcut. It's a very cool trick especially for Mac newbies! Easily switch between open applications in Mac OS X.

To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting.

Everything works fine even the sound. If you're looking for a Linux substitute for windows. Ubuntu is great for newbies.

Jon Barrie demonstrates creating custom titles in Adobe Premiere Pro CS3. There are a few tricks for newbies that are definite time savers! Create custom titles in Premiere Pro CS3.