Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.
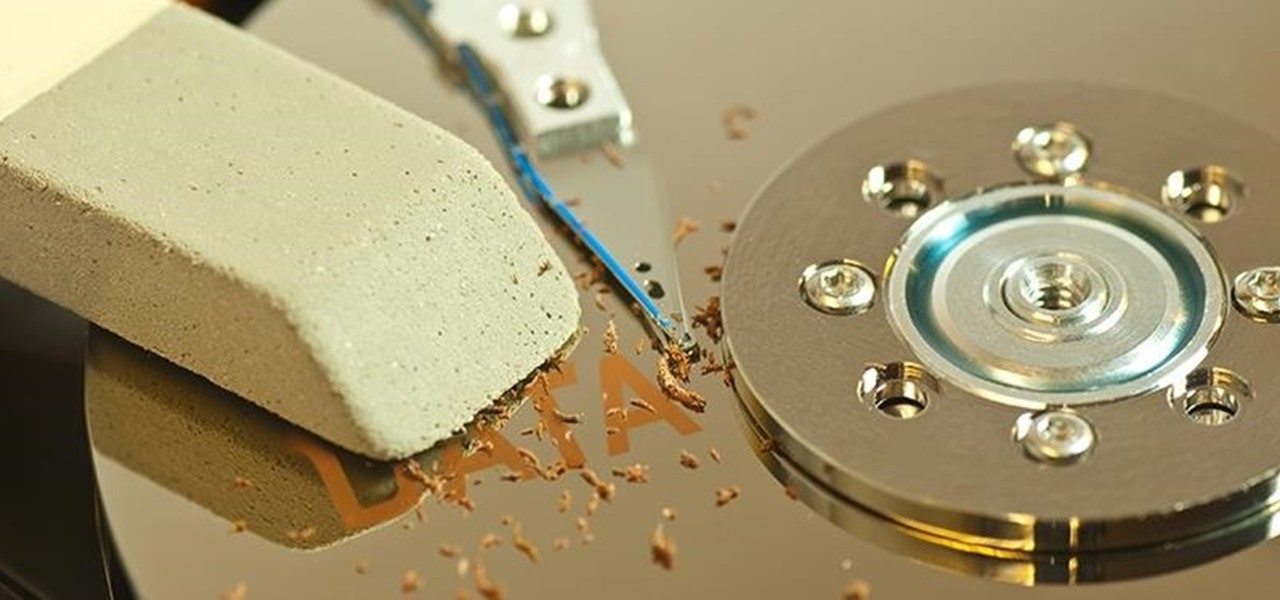
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

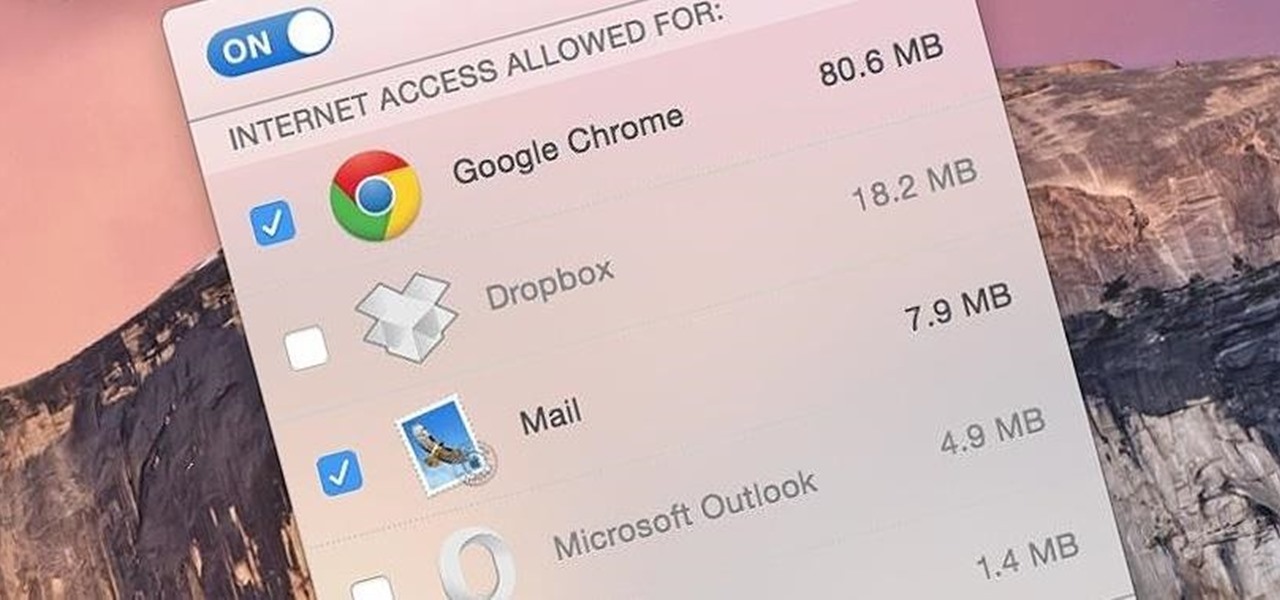
If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.
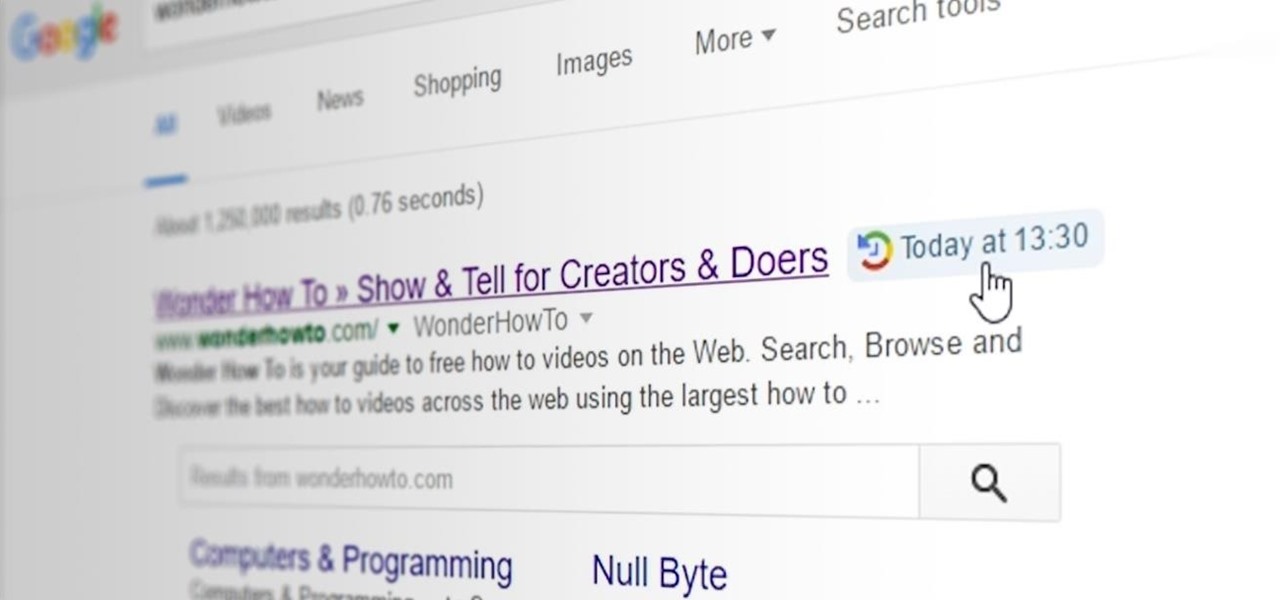
When you click a link from Google search, the link itself turns purple to let you know you've already visited this page. But let's say you're searching for something similar a few weeks from now and you see one of these purple links—you'll probably think to yourself, "What was I reading about on that site?"—and if you don't remember, you'll end up clicking the link again. And if you're a frequent Reddit user, you know this pain all too well.
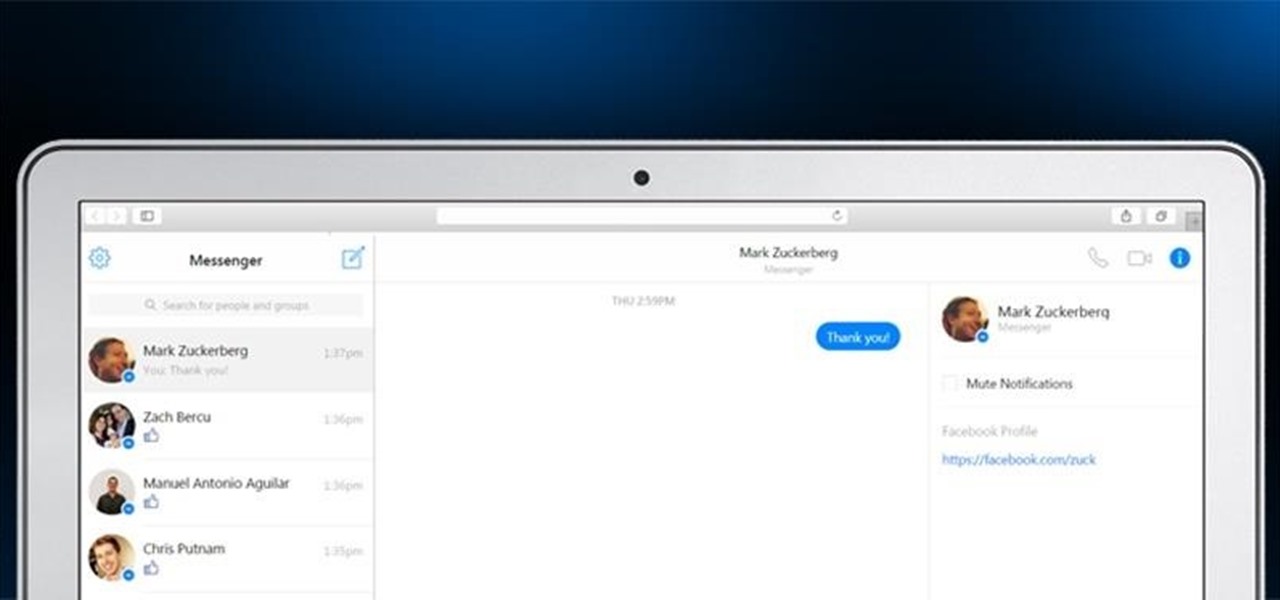
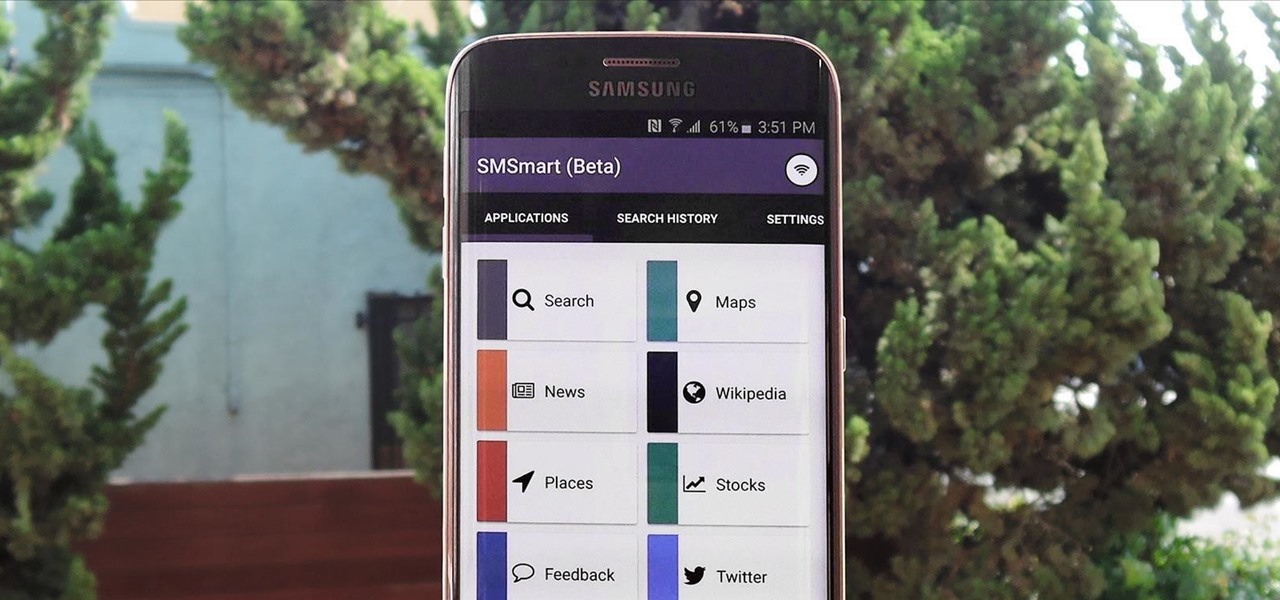
Facebook's Messenger apps for Android and iOS make it easy to navigate between conversations, helps you keep in touch with your friends or heckle your enemies, and even lets you tag yourself or others in the conversation with hilarious nicknames to keep things interesting.

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

With every version bump, Android gets a new Easter egg that can be accessed by tapping the "Android version" entry in Settings. For the most part, these have generally been little animations or live wallpapers that depict the Android code name, but starting with version 5.0 Lollipop, things got a bit more interesting.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

At this point, it'd be surprising if an iPhone release wasn't coupled with some sort of new scandal or controversy; it's gradually becoming Apple's new modus operandi. First, there was antennagate with the iPhone 4. Then it was scuffgate with the iPhone 5. Last year, it was bendgate with the iPhone 6 models. This year, it's chipgate with the iPhone 6S models, which affects something important to all on us—battery life.

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Ideas can be a fleeting thought, just like a shooting star that appears and disappears within a brief moment. So when you're inspired and have an awesome idea, it's important to jot it down as soon as possible, otherwise it may vanish from your memory for good.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around this time, you start to wonder if your trusty old remote has finally called it quits or if it's just a dead battery.

You're smashing your keyboard to increase your screen brightness, yet it won't go any higher, but you know you've been able to set it higher before. Angered by this, you get up and move your laptop, only to suddenly notice that the display does in fact get a lot brighter.

Cortana, Microsoft's personal assistant for its Windows Phones and Windows 10, will soon be released for Android. That is, officially released. It's hard to keep a good thing locked away, and to that end, Cortana for Android has been leaked, thanks to APK Mirror.

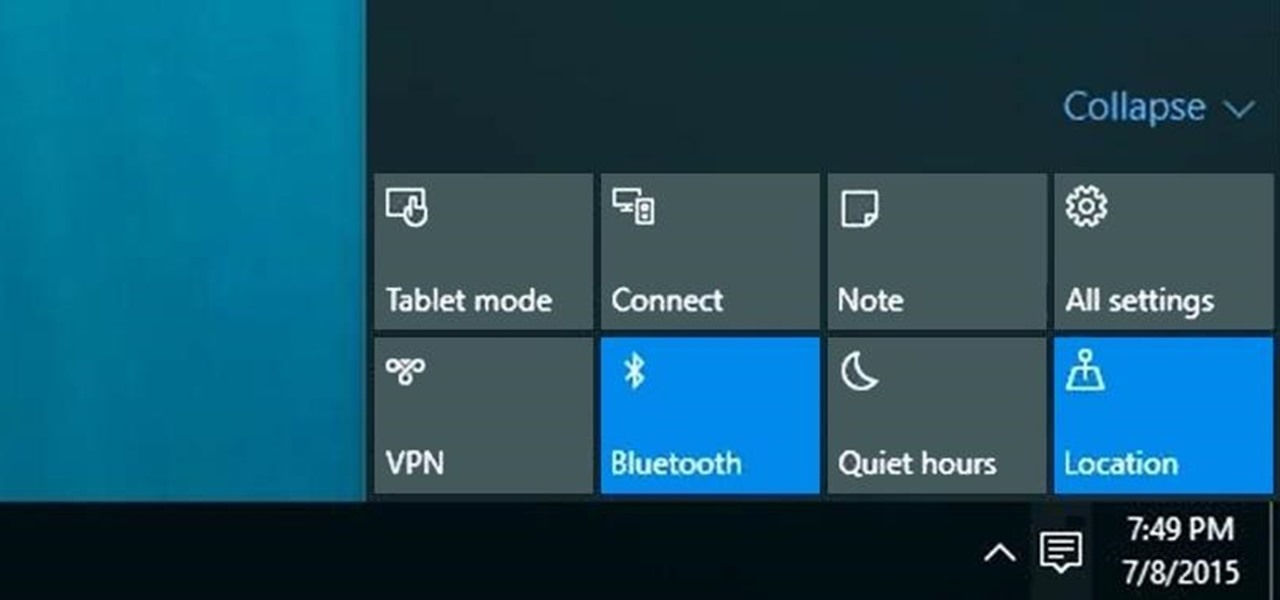
The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.

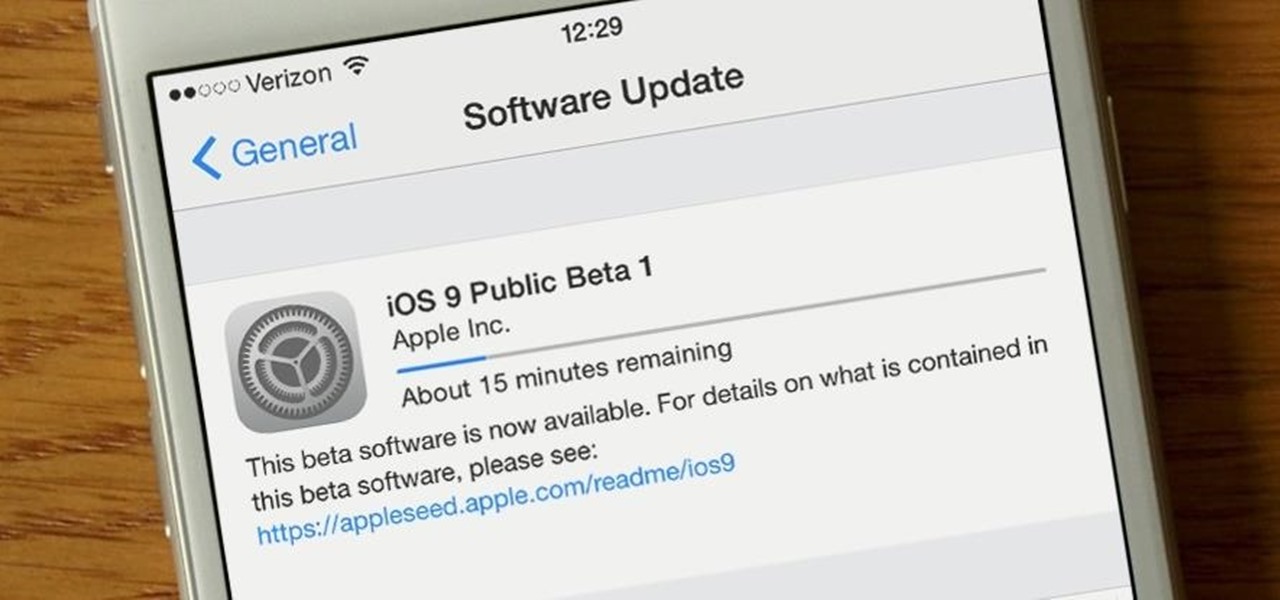
A month after its initial release to developers, iOS 9's Public Preview build is now available to everyone. If you signed up right from the start, you should receive an email or push notification letting you know of its availability. If you didn't, make sure to sign up for the Apple Beta Software Program.

Since the days of Android Jelly Bean, Samsung has implemented an energy preservation feature known as dynamic voltage and frequency scaling, or DVFS for short. What this essentially does is limit or adjust the frequency of the microprocessor to conserve power and prevent excessive heat from being generated.

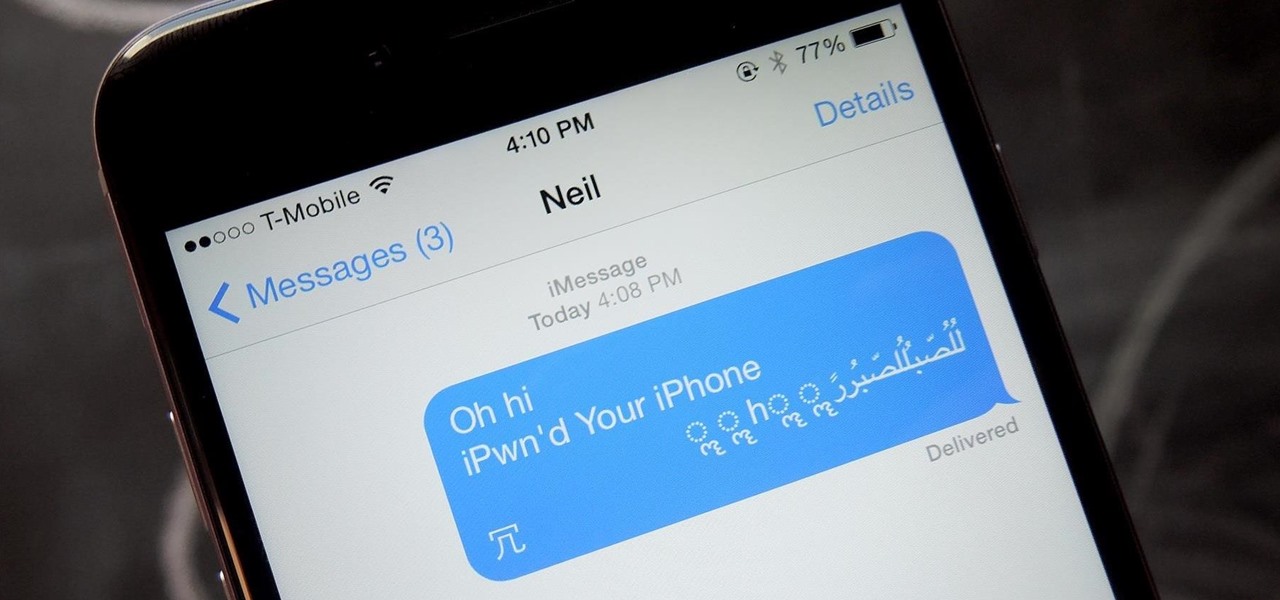
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

Amazingly enough, some of us still have to worry about exceeding our monthly mobile data limits. You'd figure carriers would have given the customers what they want by now by offering truly unlimited plans, but with two conglomerates sitting atop the U.S. cellular market with fat pocketbooks that make for limitless lobbying, they can basically do whatever they want.

Believe it or not, not every Apple lover is willing to make the commitment and fork over $350+ for the Apple Watch. Like many others, I'm not willing to put that much faith into Apple's first attempt at wearable tech.

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

There are more ways to wear an Apple Watch than just the default one. Out of the box, an Apple Watch is set up to be worn on your left wrist with the Digital Crown on the right side. But what if want the Digital Crown facing the opposite way? Or what if you're left-handed and want the Watch on your right wrist instead?

With the high rate of obesity in the United States, it's fantastic to see the massive wave of fitness tools available, even if it's just a trend. And with the companionship of your Apple Watch, keeping track of your progress or fitness goals has never been easier. As my LA Fitness intercom repeatedly announces, "What gets measured gets improved." (Corny, but very true.)

With audible alerts and subtle vibrations, the Apple Watch makes it difficult to miss incoming notifications. But soon enough you'll realize that not every notification is worth receiving on your Watch and can ultimately render the experience annoying under particular circumstances—like when your popular Instagram post floods in notification after notification.

While some of the additions to the emoji keyboard in iOS 8.3 have been criticized for actually doing the opposite of their intended purpose, they've been well received overall. But the biggest winner of the new emojis was one that actually wasn't even released—the "Vulcan salute" emoji.

Your Apple Watch only looks as good as the band that it's bound to, but if you're looking to purchase one directly from Apple, expect to spend anywhere from $149 (for the Milanese Loop) to $449 (for the Link Bracelet).

There are a number of ways to give your productivity a kicktstart, from taking a break from your distracting smartphone to just taking a break, plain and simple. Yet finding the motivation to start working doesn't require any effort at all—just a little bit of green.

Customization helps your device stand out from the rest, and that sentiment is no different when it comes to the Apple Watch. Unlike every other Apple device before it, the Watch allows you to customize the information that appears on the UI—without the need for any jailbreaking.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

As someone who loves to run around my neighborhood, the Apple Watch feature that excited me the most was the ability to go out and exercise while listening to music, all without having to lug my iPhone around.

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.