Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight Videoleap for iOS makes this all easy.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

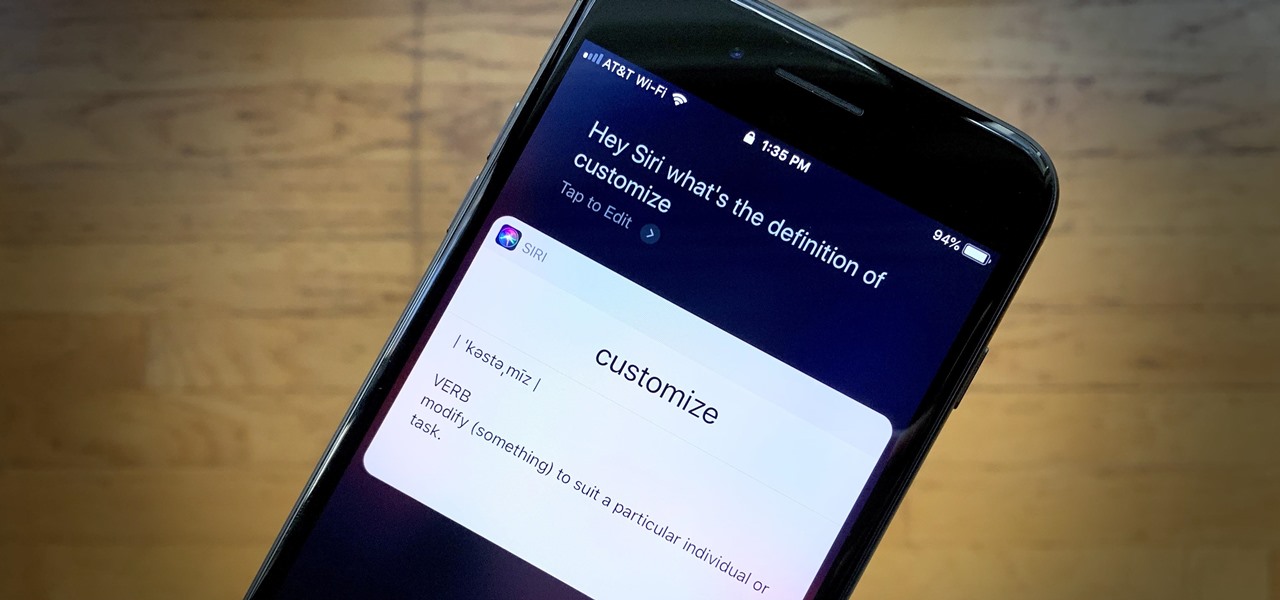
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

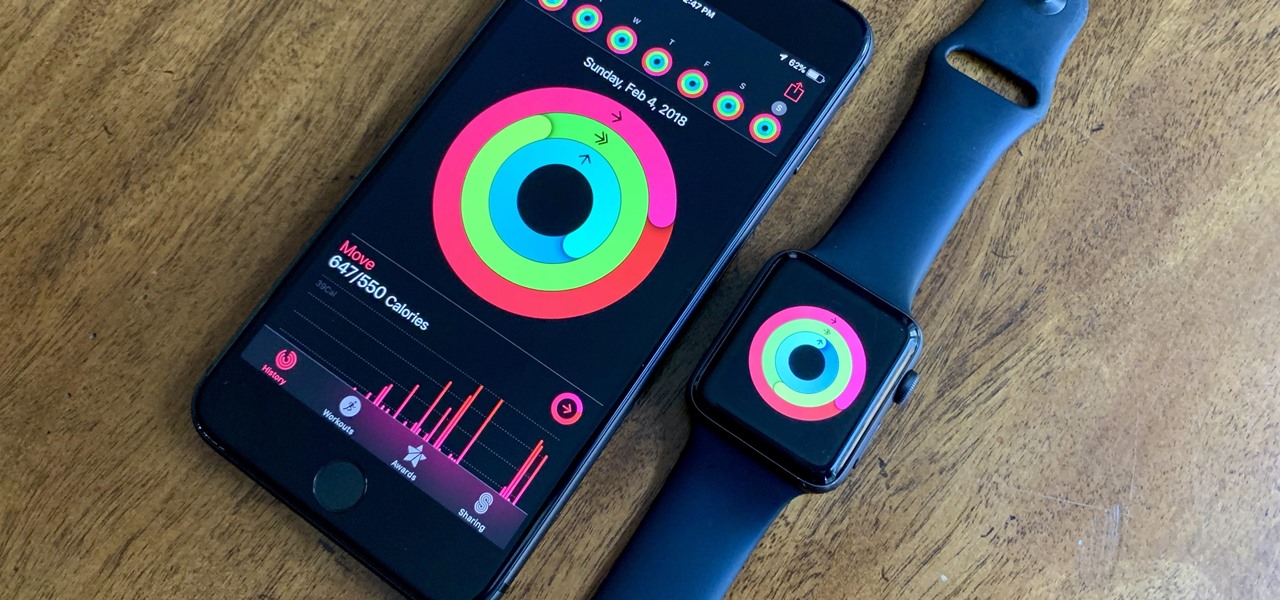
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

MoviePass was once the best subscription service on the market for getting cheap movie tickets. For the price and the number of films you could see and save money on, it was unbeatable, but recent changes to the service have made it less enticing. While it still works well for some users, others may have to rely on other options. Personally, I'm leaning toward the latter.

After poor sales of the Pixel 3 and Pixel 3 XL, Google needs to reinvigorate its Pixel lineup, devices it's been pushing heavily over the last couple years. On May 7, Google had the eyes and ears of the technology industry at its Google I/O keynote, making it the perfect time to announce new devices that would attract a different crowd of users. Meet the Pixel 3a and 3a XL.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

The Pixel 3 runs stock Android, so you might think that since you've used an Android device before, you should know your way around the new phone by default. But Google has actually added several great Pixel-exclusive software features to its flagships, and not all of them are easily discoverable.

In the battle for best stock Android flagships, there are really only two choices: Google Pixel phones and OnePlus phones. Although the latter isn't true stock Android, it is impressively close and usually paired with more impressive hardware than the Pixel lineup. The latest is the OnePlus 6T, which will be a bit controversial for fans this year.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

With all the controversy around the Pixel 3 XL, the regular-sized Pixel 3 might be the phone of choice for most users. Thanks to the huge boost in screen size, the little brother is now an easier pickup for those who like a bigger screen. And once more, the internals are the same, giving you the same experience as the 3 XL without the display notch.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

The iPhone XR offers a discounted experience compared to the expensive iPhone XS and XS Max. However, that lower price tag comes with some caveats, such as "Haptic Touch" in lieu of 3D Touch. If you think these two "touch" features are the same, think again. Before you get an iPhone XR, you'll want to know all the excellent features 3D Touch you might miss. Can you go without them?

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Three new iPhones means you have to make a choice: Do you go with the smaller iPhone XS, the larger iPhone XS Max, or the cheaper iPhone XR? There's lots to like about each model, but if you want to make an informed decision, it's time to learn what each has to offer. Here's what the iPhone XS Max brings to the table.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.