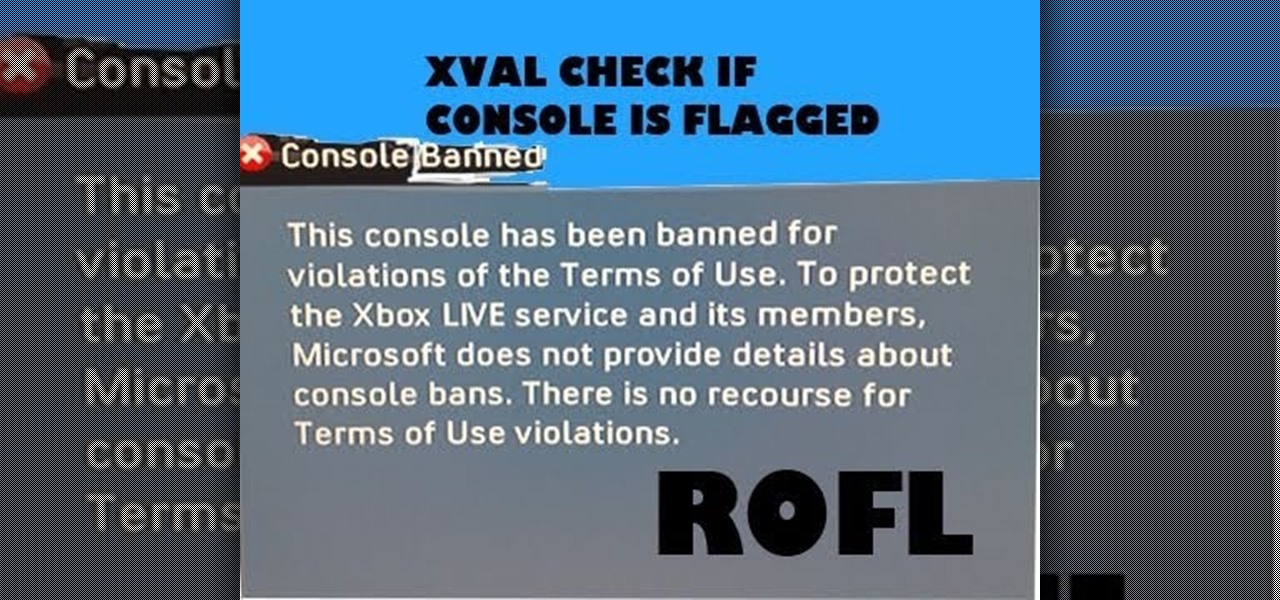
So you were caught doing something nefarious and now you've been banned from playing on Xbox Live. But how long do you have left on your ban? This video shows you a method to check your ban clock and see how long you have left.

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.
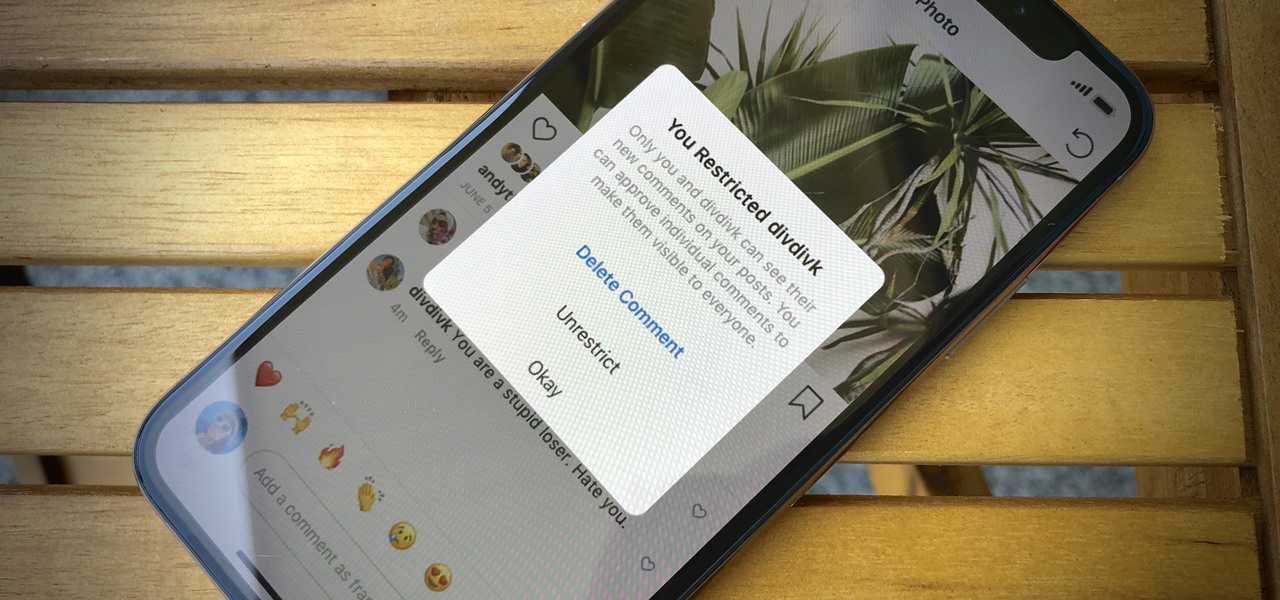
In general, the internet can be a cruel place, and Instagram is no exception. Most of the time, the platform is a fantastic way to share and view unique and creative content, to reach an audience of both fans and friends. People can step out of line and harass or bully others on posts to the detriment of the entire community. However, this type of commenting won't be sustainable for much longer.

Fashion brand Christian Dior is using augmented reality as a carrot to drive up their follower counts on Instagram.

Gotta catch 'em all, right? That's easier said than done, considering that Pokémon GO has region-specific characters that you may never get a chance to see. Sure, you can spoof your GPS location to make the augmented reality game think you're at a different spot on the map, but Niantic Labs seems to be catching on to this method, and some users have been soft-banned for a few hours after trying it.

There was a huge ban wave recently on Xbox Live. In the unfortunate event that you decided to do something against Microsoft policy, and have consequently gotten yourself banned from Xbox Live, you may have come to the realization that doing whatever got you banned from Xbox Live in the first place was not worth the risk.
In what has become a rare scene in Washington, a group of bipartisan lawmakers joined President Barack Obama today at the White House for his signing of the Stop on Congressional Knowledge Act.

If you engage in any nefarious activity on Xbox Live or simply like to swear a lot when you're playing online, your account may be flagged for a ban. Getting banned sucks, so watch this video to see how to use a program called XVAL to check your account and see if it's been flagged for banning in the next ban wave.

Learn how to pronounce the 'ng' sound in American English. This video provides a basic guide for pronunciations for ESL students.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

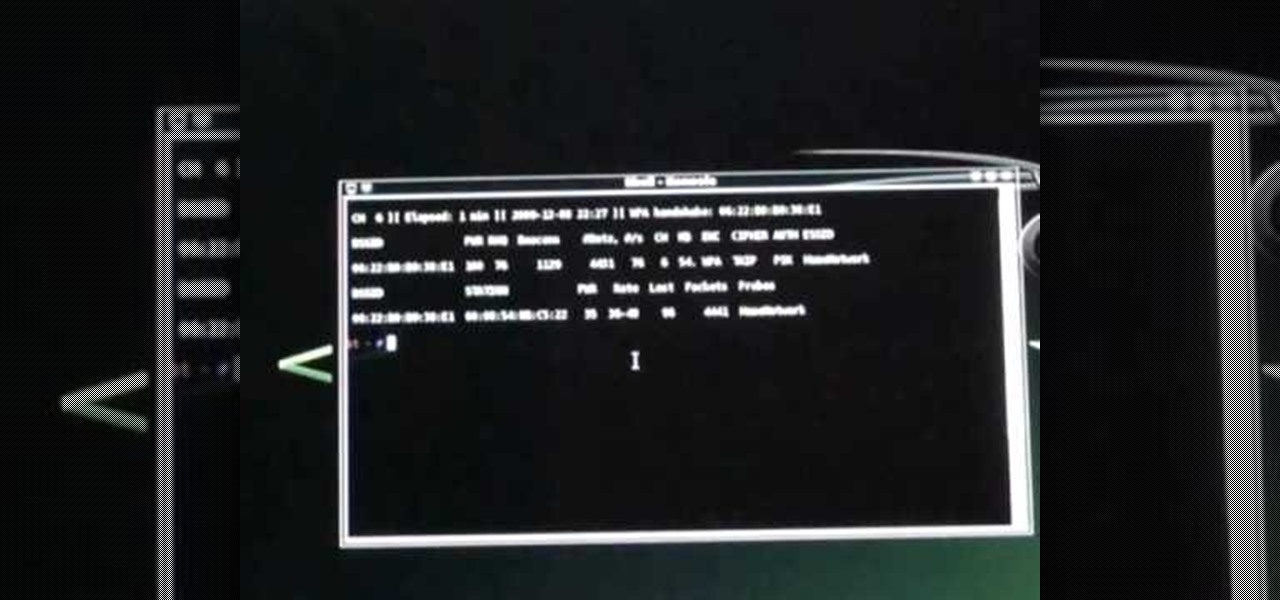
WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

Got banned from a website you love to torment? Well, there's a way to keep it going. You can get back onto a site by changing your IP to get past the servers. This will only work if your IP is banned. If your username is blocked directly, you will have to find another way.

This free video science lesson from YouTube's bionerd23 demonstrates a simple technique for modding a Bresser Biolux NG or Bresser Biolux AL microscope to view larger objects like minerals. You'll also learn how to mod your microscope to allow you to take pictures and shoot video through it. For all of the relevant details and detailed, step-by-step instructions, watch this home-science how-to.

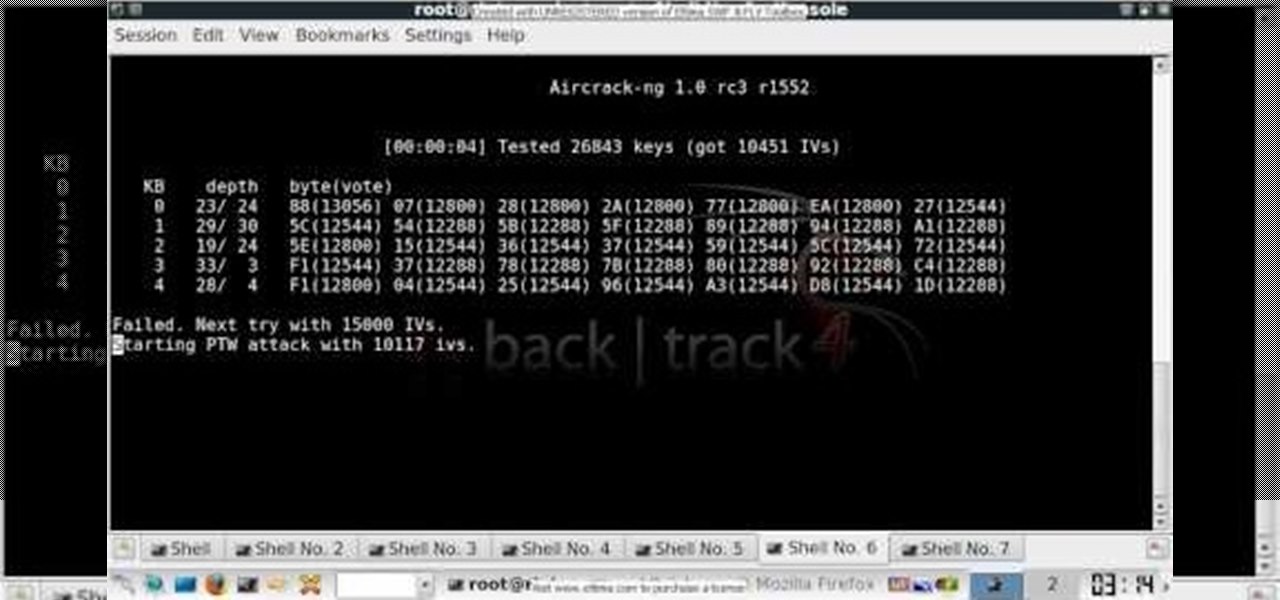
Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

This how-to video is about how to cook Filipino sinigang na ulo ng salmon, normally this dish is salmon boiled with spinach, the best thing about a Filipino dish is that they used to add spinach to most of their dishes which makes the dish more nutritive.

This video demonstrates how to insert an NG tube. An NG tube is a plastic tube inserted to the nose, through the pharynx and into the stomach.

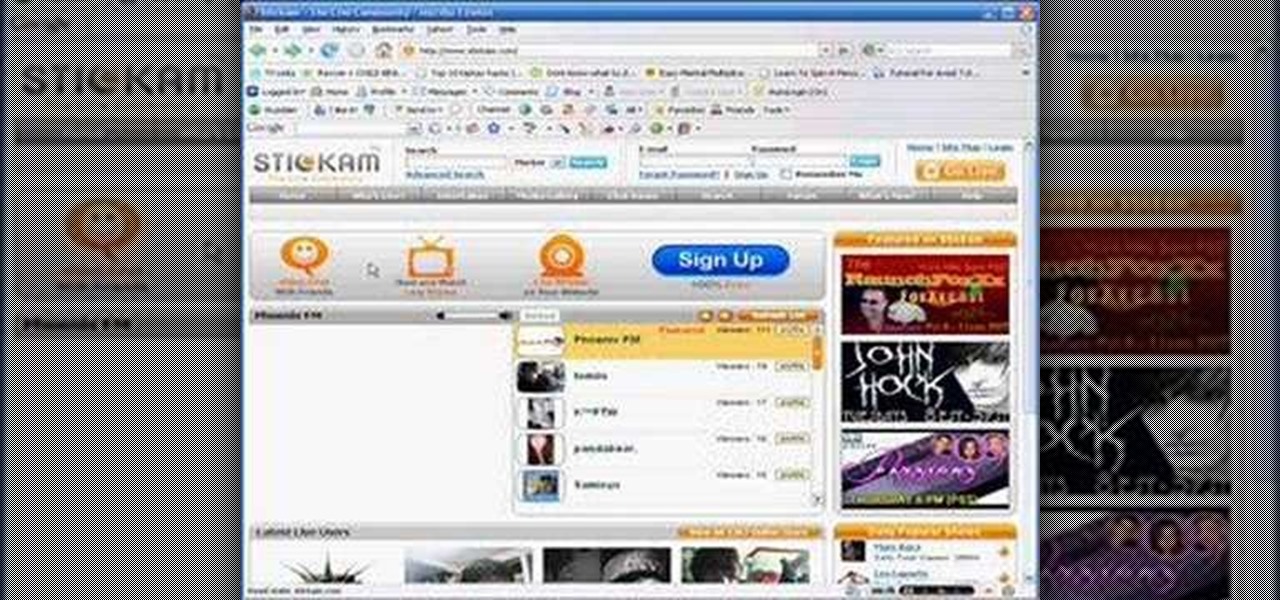
This video shows you how to get unbanned from Stickam - not the IP/Account ban, but the computer ban.

We've seen plenty of good, bad, and weird things that have come out of the worldwide augmented reality game Pokémon GO, including murder and location-based bans, but nothing on a large scale. That was, of course, until Iran decided to ban the game country-wide.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

I see that there are a lot of people that want to install and try the Aircrack-ng program for wireless auditing. But have problems because their Linux knowledge isn't that great. This How-To video tutorial explains step by step exactly what you have to do. No loud background music.

Plastic shopping bags are on the verge of extinction with states threatening plastic bag bans. California has already approved a ban, taking effect in 2012, and other states are proposing the same ban, including Oregon.

Going to be a nurse? Then here are a few things you should know how to do. Follow along with this nursing how-to video to learn how to insert a nasogastric tube in a live person. Watch the demonstration of NG insertion on a live patient. Once you pass around the septum ask the patient to bend their head forward to advance the NG tube into the stomach. Practice inserting a nasogastric tube on a manikin during lab to perfect this technique. And remember to always have your equipment ready befor...

Going to be a nurse? Then here are a few things you should know how to do. Follow along with this nursing how-to video to learn how to insert a nasogastric tube. Watch the demonstration of NG insertion on a manikin. Once you pass around the septum ask the patient to bend their head forward to advance the NG tube into the stomach. Practice inserting a nasogastric tube during lab.

This medical how-to video demonstrates the simple steps for inserting a nasogastric tube. A nasogastric tube is more commonly known as a NG. Follow along and learn the basic protocol for doing this procedure. To do a NG tube insertion you will need 14-16 French gauge nasogastric tubing, water soluble lubricating jelly, catheter tip syringe, suction drainage system, and hypoalergenic tape. For your patient, you should have ready a cup of water with a straw, emesis basin, and a towel.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.