Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the first to be banned by the messaging app.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.
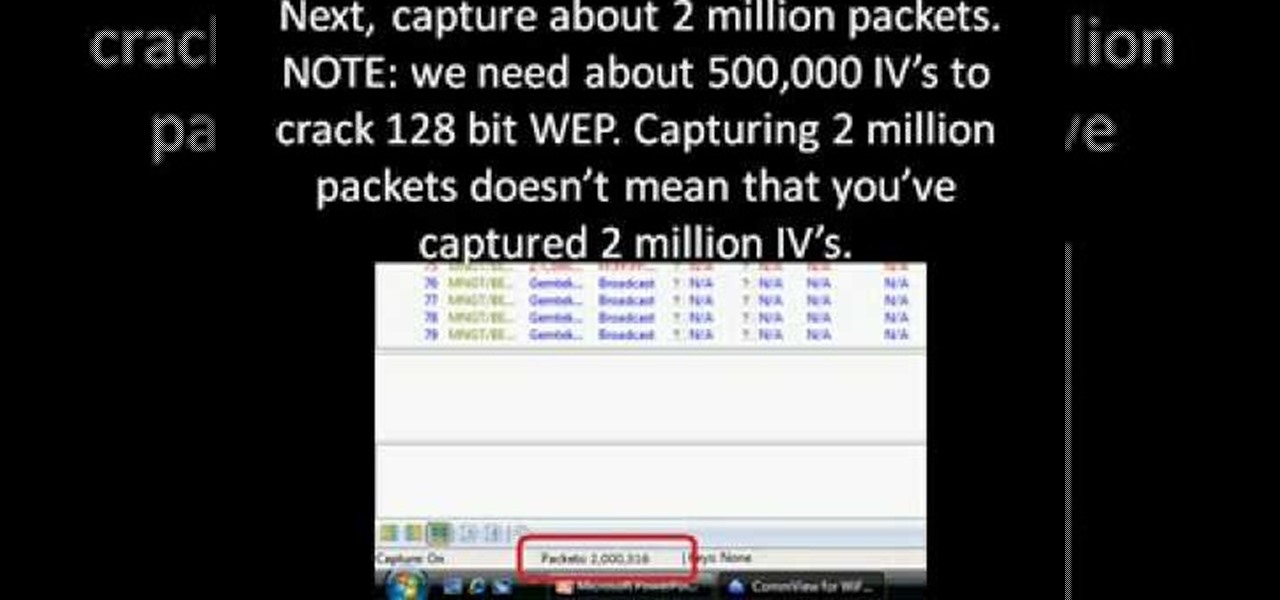
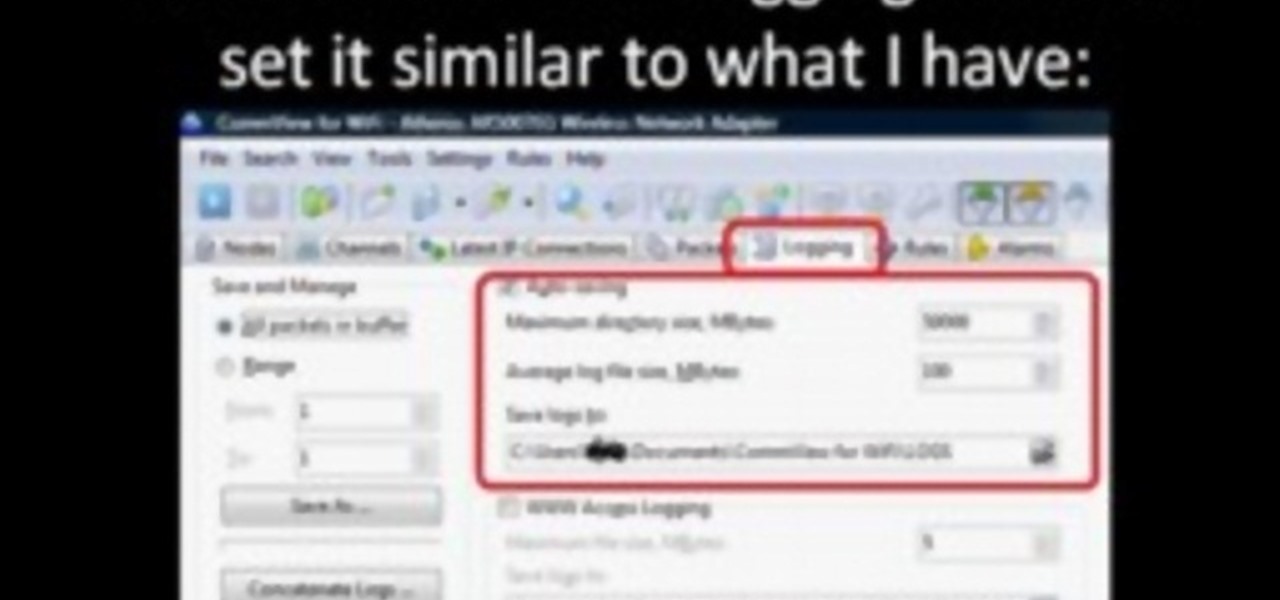
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

This episode of Full Disclosure demonstrates how to hack/crack MD5 password hashes. MD5 (Message-Digest algorithm 5) is a hash function commonly used by websites to encrypt passwords. MD5 is a one-way hash; therefore, to crack the password you most try every possible dictionary word and if that does not work, every possible letter/number/symbol combination. The programs used to crack the passwords are Cain and MDCrack-NG.

In this tutorial, learn all about the controversial and artificial food dye, Red 40. Red 40 is linked to hyperactivity in kids as well as ADHD, migraines, stomach aches and jitters. The UK is actually banning Red dye 40 this year.

A lag switch allows you to cheat in online games or on XBOX LIVE by disabling the flow of data to your console or PC. We will show you how to build one.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

When you apply cologne you want to get the ban for your buck, and you want that bang to smell perfectly. There are a couple key points that you should keep in mind when applying scents. This video will show you exactly how to apply cologne, fragrance, or perfume and love it.

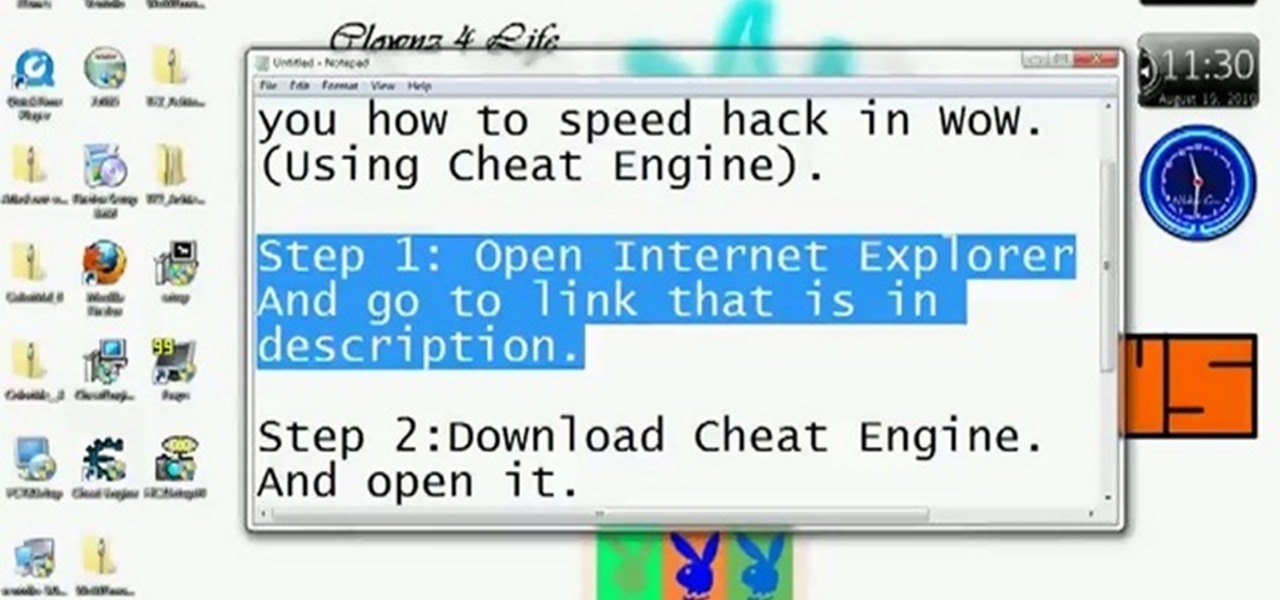
Be careful! If you use this on a public World of Warcraft server, you might get caught and banned by the GMs. However, if you are on a private server, or don't mind the risk, here's how you can use Cheat Engine to hack the game.

In honor of the recent proposed ban in Italy on miniskirts, this tutorial shows you instead how to make a fun, basic jumpsuit! All you'll need is a basic torso pattern and a pant pattern without any pockets. And voila, your own sexy jumpsuit!

With many states accepting laws about banning the use of cell phones while driving, bluetooth is becoming an important feature to have. Not only does it make things easier when talking on the phone, but it's something that is being featured in many new cars. So in this tutorial, you'll find out how to setup your bluetooth on a 2011 Sorento. So good luck and enjoy!

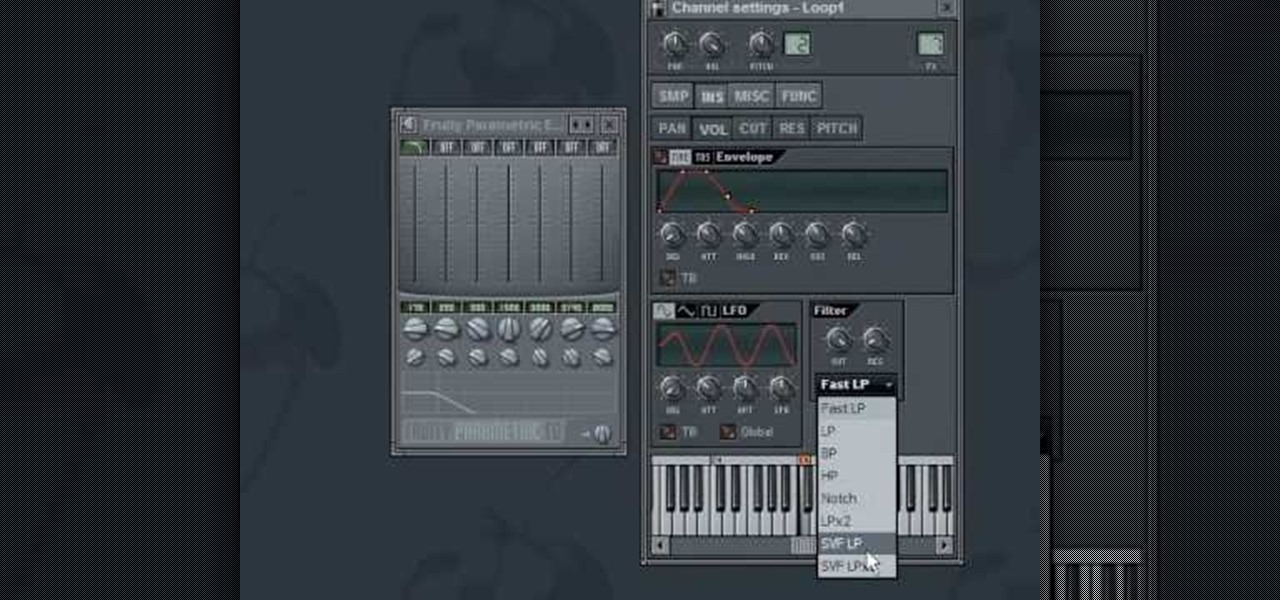
Ever wondered what a High Pass or ban Pass filter does? Why a Low Pass filter might be useful? Well wonder no more as NFX explains these useful EQ effects in FL Studio (Fruity Loops).

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Learn how to install Aircrack on your iPhone to hack into almost any WiFi network. First download Aircrack from iHackMyi, then follow these steps:

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Flashing the disc drive on the XBox 360 is the first step of truly hacking your XBox 360, enabling it to run whatever discs you like but also putting you at risk for being banned from XBox Live. Microsoft has used several different kinds of drives in the console over the course of its lifespan, so you have to check what type of drive you have before you attempt to flash it. This two-part video will show you how to flash the Hitachi 78FK drive used in many XBox 360's.

Many types of knives are banned in many states. Not this one, it is made out of Knex! This video features a walkthrough to making a flick knife out of Knex pieces. You may have a hard time defending yourself with it, but it looks very cool and should impress all of your friends on the playground.

There's probably a reason that laser pointers are banned from most schools: They're just to fun to put down! Whether you're using them as a pointer, to distract your classmates, or to very wickedly point them in people's eyes, they are toys that are quite addicting.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Immersive advertising company Vertebrae has extended its native ad platform to augmented reality via mobile Chrome browsers for Android and Safari for iPhone.

With the US Department of Homeland Security (DHS) banning laptops and tablets on flights originating from 10 international airports, and the United Kingdom taking similar precautions, international travelers are faced with hours of non-productive — or far less entertaining — flight time.

Check out this video tutorial on how to hack into WEP encrypted wireless networks. The aim of this video is to show people how easy it is to crack a wireless network with WEP encryption. Seriously, if you know how to do it, even a little kid could if you showed them how. Now that you know this, you should upgrade to WPA! It is much harder and takes much longer to crack.

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

Learn how to play "Hiling" by Paramita, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here: