Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Fancy feet are a must for sandals and peep-toe shoes. Pamper yourself with a pedicure that’s easy and gets you back on your feet in no time.

Learn how to play "Akala" by Parokya Ni Edgar, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing.

By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

Some studies have shown that vitamin D supplements help fight respiratory infections, but some haven't. A new study published in The BMJ clarified the confusion, and identified a group of people that might be better able to fight off colds and flu with vitamin D supplements.

Long-exposure photography gives us the ability the capture some pretty amazing shots by delicately capturing moving elements in an image while keeping the shutter open at a slow speed. While that's great for things like traffic, scenery, and carnival rides, it can come in especially handy for 4th of July fireworks.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

When iOS releases in the next few weeks, consumers on both iOS and Android operating systems can expect to see more AR ads in the mobile web browsers thanks to Vertebrae, an advertising platform for immersive media.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Approximately 380 billion plastic bags are used in the United States every year. That’s more than 1,200 bags per U.S. resident and more than 54 times the number of people who live on the planet. That's why here in Santa Monica, thanks to a city-wide plastic bag ban, you won't find a plastic bag at any of the major retail stores.

You've had your Xbox 360 for a few years now and your game collection is pretty extensive. Maybe it's not that extensive, but it's still substantial. Now imagine that you live in Europe and you're moving to the United States. I don't know why—maybe your dad got a job offer. Don't ask me, ask your parents. They're the ones that are making you move. Anyways, as most Xbox users know, games are coded by region. Games that work in Europe might not work in the United States. Does this mean you shou...

On Monday, the social media giant Facebook suffered a massive outage that, as of this writing, is still in effect.

Apple is no stranger to lawsuits. They were in a decade-long battle with Samsung that finally came to an end last month, and they've been duking it out in the courtroom with Qualcomm since last year. The more recent case has seen both companies file suits and counter-suits, but now, Qualcomm is claiming that Apple's new iPhone X infringes on patents from a long-deceased mobile operating system.

Online glasses retailer Warby Parker built its reputation by selling fashionable yet affordable eyeglasses, so it perhaps a surprise that it's one of the first developers to take advantage of the technology in the least affordable iPhone yet.

Baidu signed a cooperation agreement on June 7, the first day of the CES Asia conference, with multiple companies in the autonomous vehicles industry. The companies listed in the press release include Desay SV, United Automotive Electronics, and Hangsheng Electronics, as well as possibly additional auto manufacturers. Baidu plans to "jointly develop" upcoming intelligent driving production plans.

For some strange reason, Google Now is unavailable in several countries across the globe. Users from Albania, China, Cyprus, Malta, Nepal, Puerto Rico, Tunisia, and many more big countries have reported for years that the service doesn't work in their area, mostly likely because Location Reporting is not available in their region. This is really a shame, because Google Now has some great features.

So, you've finally managed to get addicted to one of those free farming games, like Farm Story or Tiny Village. You play the game nonstop now, and the only thing stopping you is that dreaded on-screen notice to come back in 23 hours to finish farming or building. Come back in 23 hours… WHAT?!? Most of these free games will start charging you at this point. Time becomes a luxury. Well, not anymore, thanks to XDA Developer StupidIdea, who made a time-tricking app called GMD Speed Time (that's t...

Sea otters are the largest members of the weasel family. When people started hunting sea otters for their fur, their population fell from roughly 225,000 to about 1,500, until the International Fur Seal Treaty took effect in 1911. Since the international ban on otter hunting, the population has rebounded back to roughly 107,000.

Have you ever wanted to be famous? Of course you have! Now you can make your Twitter profile look like it's verified, just like professional skater Lil' Wayne. With Twitter's new header, you can now upload a cover photo onto your profile to be seen online and on mobile devices. Just click here and change your header with the images below to get "verified" in seconds! Note that this will not work on the newer Twitter profile designs, since the verified symbol is located outside of all images.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Be careful, because you could get banned if you get caught using Cheat Engine on this game! Make sure that you have the most current version of the program, and are playing your game in a browser like Mozilla Firefox.

It's about that time again: Facebook has announced the dates for its annual Facebook Connect (formerly known as Oculus Connect until last year).

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

Learn how to practice proper etiquette on a BlackBerry, smartphone or PDA. Make sure your love for your BlackBerry or other PDA device isn't making you obnoxious.

We've reached the point in the trajectory of augmented reality's growth where AR advertising experiences are becoming commonplace tactics rather than rare experiments.

You can block artists no matter where you are in Spotify's mobile app for Android or iOS, but it's not as easy when you want to hide songs from playing. Disliking tracks is possible here and there, but not everywhere, and that's a serious problem if you keep hearing songs you hate.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

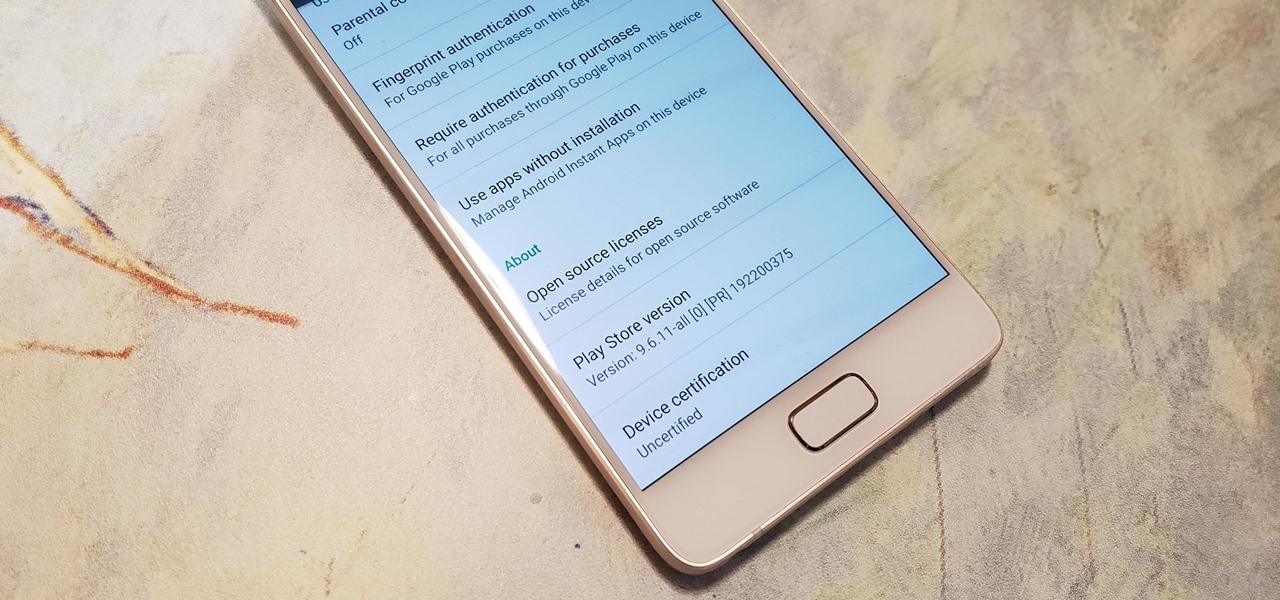
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.