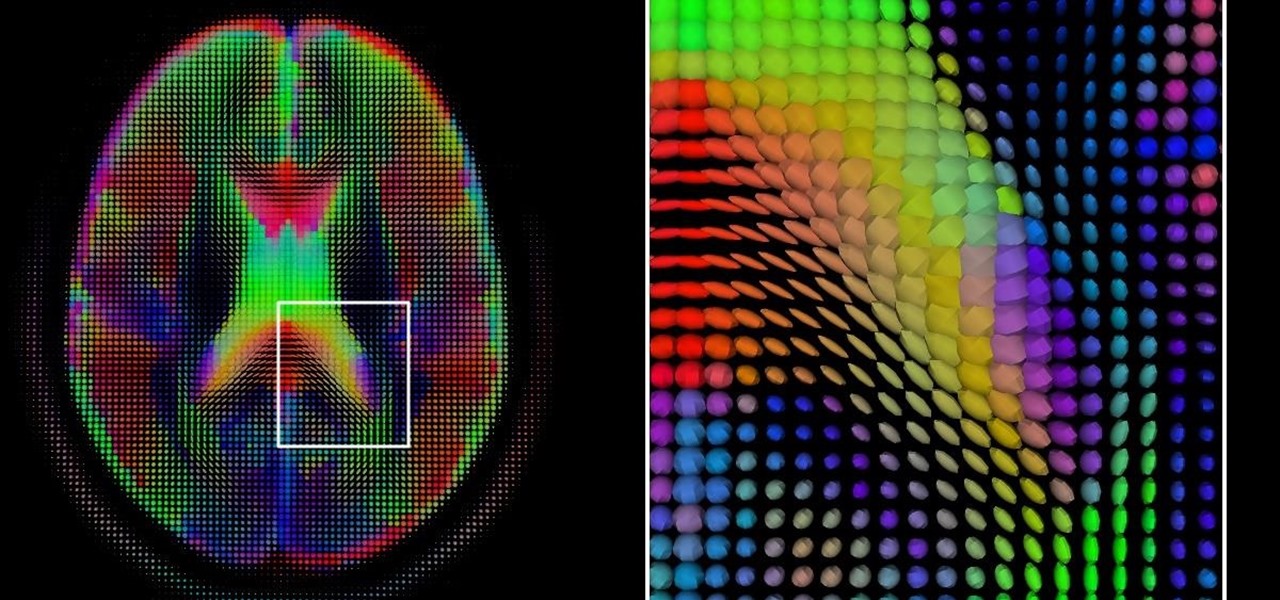
We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

Starbucks is spicing things up ahead of this holiday season with a little augmented reality joy. This week the company launched its first Instagram filter, called Holijoy, delivered like an early Christmas gift and packing four seasonal lenses.
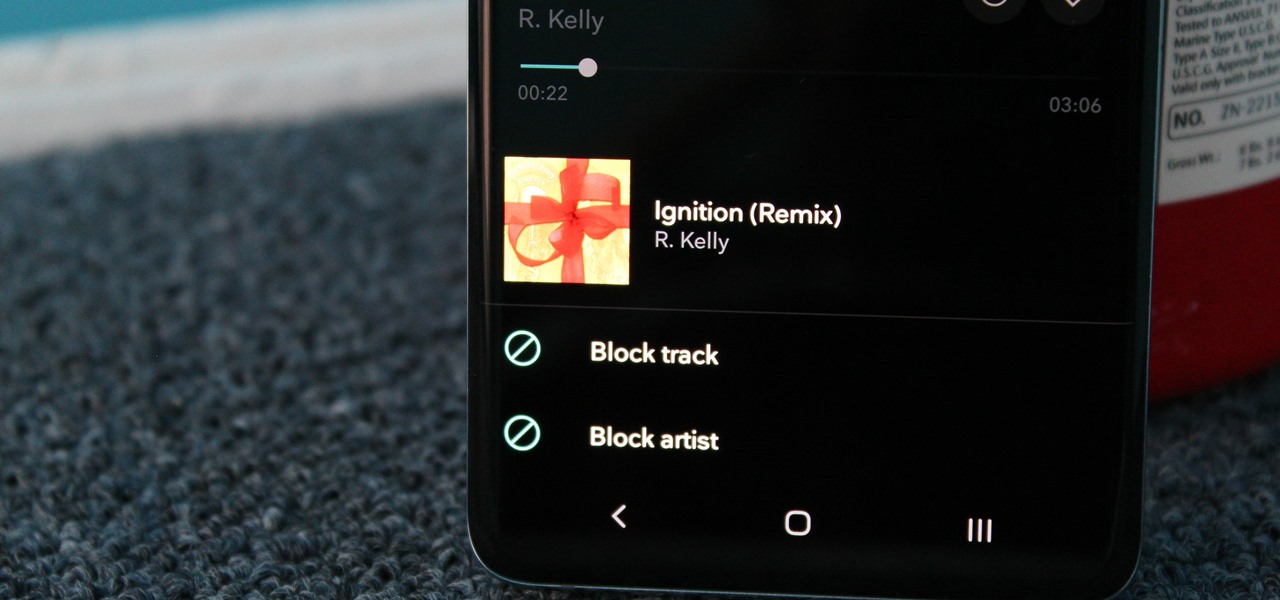
From XXXTentacion to R. Kelly, many artists have been accused of inappropriate actions, so some of us just don't want to hear their music anymore. However, each time streaming services attempt to ban such artists, they face heavy backlash. Recognizing this, Tidal decided to offer a different solution.

Augmented reality experiences created in Lens Studio now have a permanent home in the Snapchat app. On Tuesday, Lens Explorer will begin giving users access to a scrollable screen full of a variety of new Lens Studio creations.

The annual Coachella Valley Music and Arts Festival is one of those events that everyone talks about, so an augmented reality experience in the festival's mobile app and from one of its headlining acts, Eminem, basically means the technology is officially cool.

It looks like Google's feud with Amazon won't end anytime soon. A war has been brewing ever since Amazon pulled Chromecast, Apple TV, and other competing devices from their store in 2015, but the latest exchange is a huge blow to people using Amazon Fire tablets and streaming TV sticks.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Just as the Transformers animated TV series of the '80s were basically half-hour commercials for toys, a new Transformers AR app for iOS similarly functions as a promotion for the latest installment in the film franchise.

The world is a massive place, especially when you consider the field of view of your smartglasses or mobile device. To fulfill the potential promise of augmented reality, we must find a way to fill that view with useful and contextual information. Of course, the job of creating contextual, valuable information, to fill the massive space that is the planet earth, is a daunting task to take on. Machine learning seems to be one solution many are moving toward.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

Uber's legal team may have finally sold their engineering golden boy down the river as their war with Waymo continues. Anthony Levandowski isn't your average sacrificial lamb either — given the alleged stealing and all that — but Uber seems set on distancing themselves from this whole fiasco as fast as they can.

Everyone loves sharing pictures and quick video clips with Snapchat, but while the service itself is tons of fun, the Android app is one of the worst on the market. For one, Snapchat takes terrible photos even on high-end Android phones. And to make matters worse, the app is a notorious data-sucking battery drainer.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Surprise desserts (aka peekaboo desserts) are a gorgeous way to celebrate anything, whether it's a birthday, new baby, or just a brand new day. You can pretty much hide anything you want inside: candy, a cool design, and even other desserts. To help inspire you, try one of these fun-filled desserts out for a special, photo-worthy occasion. Then get creative and try out your own ideas (and make sure to share them with us when you're done).

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

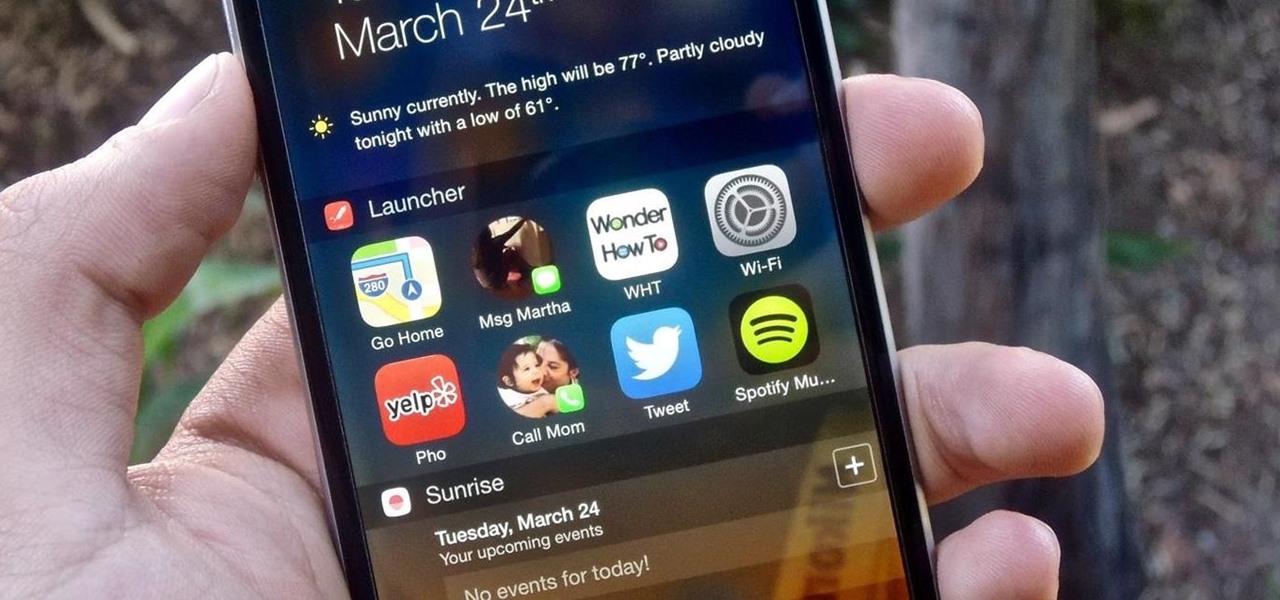
An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

I've known eaters who will fearlessly bite into the hottest peppers, but even they have quailed before durian, the fruit that hails from Southeast Asia and whose smell has been compared to garbage, rotting flesh, and the bathroom post-use. However, this hefty globe with its spiny, prickly outer covering isn't called "the king of fruits" for nothing. According to its many fans, its stench does not correlate to its taste, which has been described in extremely flattering terms. Monica Tan of The...

Revised Version, Gallery pictures of the Ambassabank have been removed since XCL 2.0 has been released.

Chances are that you're living in a city and/or state that's banned using your phone while driving, and because of that, many manufactures have added a "car mode" to their devices. In most instances, this mode is simply an app that simplifies your phone to its basic parts so you can navigate, make calls, and play music, limiting the amount of smartphone distractions.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

While Siri came up on the scene with hardly any competition back in 2011, Google Now has not only caught up to Apple's intelligent personal assistant, but also excelled in certain areas—with its ability to quickly answer questions, give recommendation, and even deliver information that it predicts a user will want.

As we all know, our attention spans are much shorter now that we're accustomed to getting information and news in tiny snippets via text messages, tweets, instagrams, and other constant updates.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

When it comes to the ever-shifting sands of the augmented reality space, you never know which week will end up being truly historic. Well, this one was one for the history books.

Facebook's earnings calls are generally focused on numbers—revenue and user growth. But this week the company's founder and CEO, Mark Zuckerberg, carved out a significant portion of the call to elaborate on Facebook's plans for immersive computing.

Ever since Facebook announced its partnership with Luxxotica brand Ray-Ban to produce smartglasses, the augmented reality space has been on high alert awaiting more details.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

This past year was a big one for WonderHowTo. Our biggest yet. In 2014 our writers, curators, and community members helped over 100 million people learn over 270 million new things. That's 40% more people than the total number of students enrolled in every single school from elementary through college across the entire United States. That's pretty awesome. I couldn't be more proud of our entire team, and of course you, the community members who've helped us grow to this point.

As if answering Apple's major iPhone event on Tuesday, Chinese mobile giant Xiaomi held its own product launch event the following day.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.