With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.
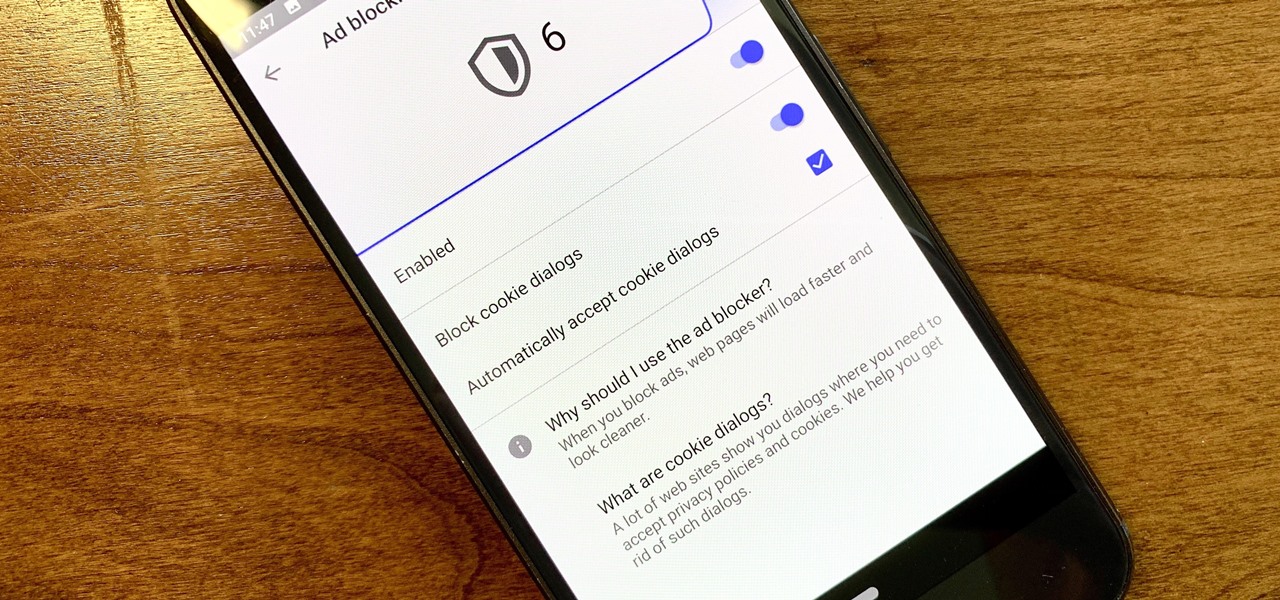
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While I love Spotify, I don't like it devouring my data plan when streaming music away from a Wi-Fi network. If you have the foresight or time to download Spotify tracks for offline playback later, great. For those of you who like to listen to your music more randomly like I do, based on your current mood, streaming is the only way to go, and there are settings you can tweak to use up less data.

Apparently, Amazon's new year's resolution is to bulk up its fitness fashion sales by pumping up its augmented reality muscles.

Although John Chen of BlackBerry still sees Qualcomm as a partner, the chip maker and telecommunications company has just been given a preliminary order to pay BlackBerry $814,868,350 in royalty overpayments.

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

Google dropped its opposition to T-Mobile's Binge On service due to some favorable policy changes at the magenta carrier. From now on, YouTube and Google Play Movies will happily work with the feature. Binge On rolled out late last year, allowing many customers to receive unlimited video streaming at 480p. That's not a great offer if you care about video quality, but it's nice if you want to save money.

Hello there Nullbyters, Last tutorial we discussed navigating and setting some options.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

This past year was a big one for WonderHowTo. Our biggest yet. In 2014 our writers, curators, and community members helped over 100 million people learn over 270 million new things. That's 40% more people than the total number of students enrolled in every single school from elementary through college across the entire United States. That's pretty awesome. I couldn't be more proud of our entire team, and of course you, the community members who've helped us grow to this point.

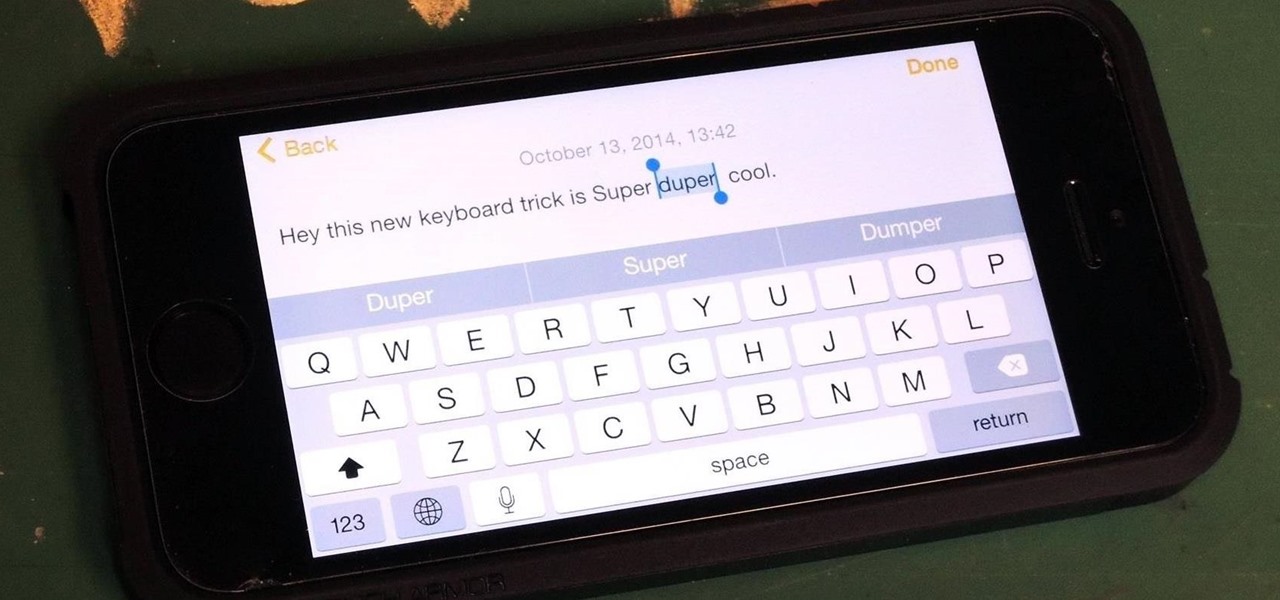
An uncapitalized proper noun in a message or email is a serious no-go for those skilled in the art of grammar. But trying to make a lowercase letter uppercase (and vice versa) is not a fun task if you're using an iPhone. You've got to point the cursor is just the right spot to change a letter, and that's a skilled art in and of itself.

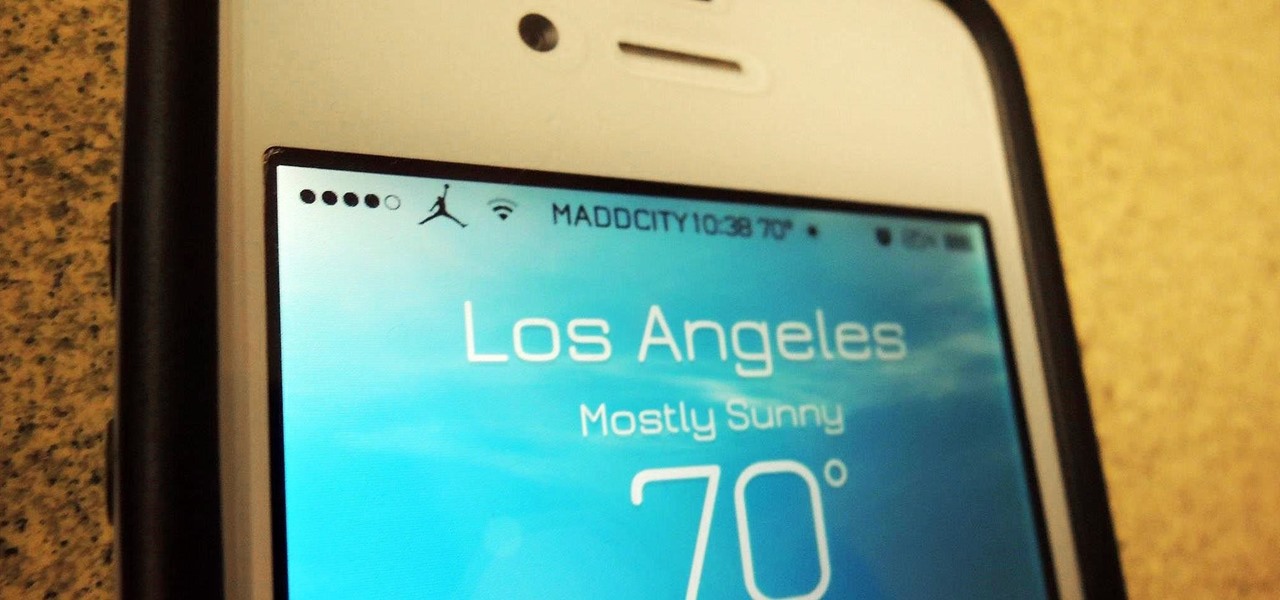
While it may not serve much of a purpose here in sunny Los Angeles, it's still a good idea to keep constant tabs on the weather forecast, because you don't want anything to rain on your parade.

The in-fighting between the major US carriers just got a little more interesting. In July of last year, T-Mobile introduced their JUMP! plan, letting customers upgrade their devices after just six months, up to twice a year. Buy a device, split up the price into monthly payments, and pay an additional $10/month to enroll in the service.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

This homemade hairspray-powered PVC rocket takes less than an hour to construct and only costs about 20 dollars to make. Check out my video below for the step-by-step instructions on building your own backyard rocket, and follow the written guide below for reference.

Got a Samsung Galaxy Note 2 phablet? Sure, it has its problems like any other mobile device, but it's still one of the hottest phablets on the market right now, because, well... it's awesome, right?

Ever drive a friend's car? Maybe a rental? Then you've probably found yourself in a very frustrating situation when you realize you need some gas. Heck, it probably even happens to you in your own car sometimes.

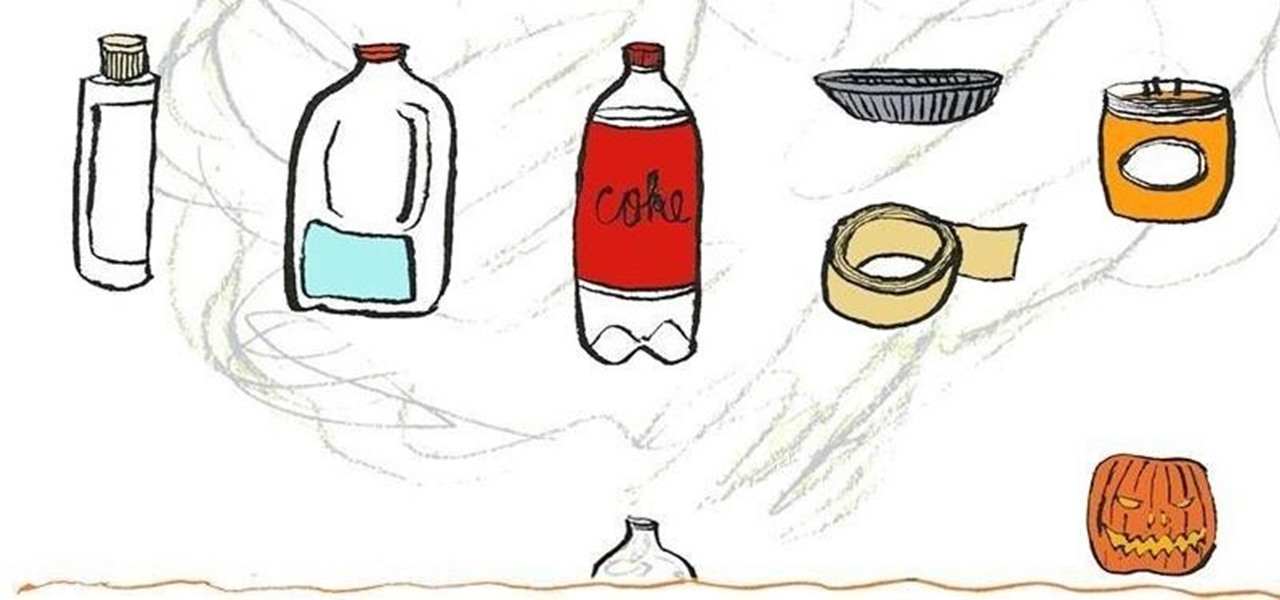
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Free stuff is pretty cool. Free internet is even cooler—and free internet that is actually free is the coolest. If you would rather avoid sitting in a Starbucks and having to listen to hipsters discuss the proper length of cropped jeans, then this should be of interest.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

Take everyday sprinkler parts and form them into a high pressure rocket launcher that will shoot paper rockets nearly 300 feet!!! It's cheap to make and a lot of fun!

Flavored oils are amazing. They add a new flavor and depth to dishes not possible with plain oil. Most unfortunately, however, flavored oils almost always come with a hefty price tag to reflect their deliciousness and to capitalize on the general cluelessness of the public.

Fresh peppercorns add a delicious and noteworthy touch to many dishes. Some of my favorite dishes that include peppercorns are pepper-crusted steak and peppered spread for crostini.

Water is an important resource and it needs preservation. Older toilets suck up way more water than necessary, causing both high water bills and pain for the environment. Follow this tutorial, and learn how turn your old toilet into a newer low-flow model.

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

This is a clever video that teaches you how to make a craft that is both fun to make, and also a useful item to have around the house- soap! This is from Living a Simple Life Blog and details how to make soap, just like the pioneers. To do this, you will need some equipment, a scale, scent, colorant, lard, lye, coconut oil, plastic containers to hold ingredients while you weigh them, a stainless steel pot, safety glasses, rubber gloves, a miter box, scraper, curing racks, a funnel and a plast...

Do you know the oldest gag in the book? Or at least the oldest gag since Diet Coke and Mentos were born. This quick video tutorial will have you testing this out every time you have Mentos and Diet Coke in your hands. Just let thirteen Mentos slide quickly into the Diet Coke and watch the eruption, just like Old Faithful. Now, try and screw a cap on it for the perfect prank. Use this as inspiration for one of your April Fools Day pranks!

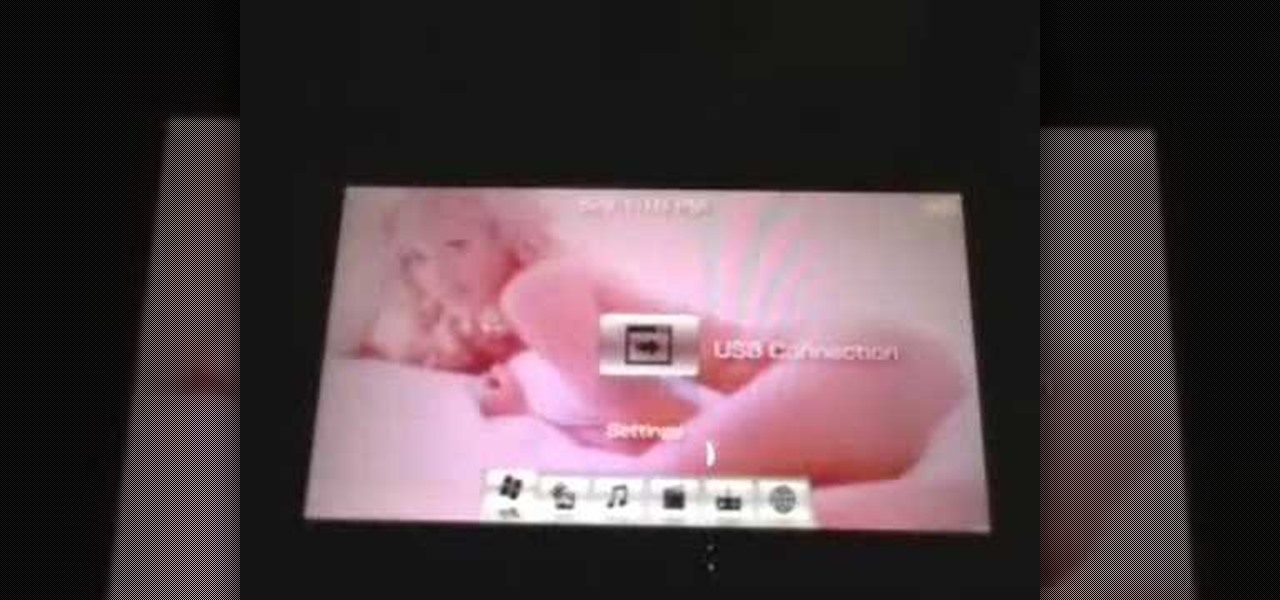
If you’re having trouble getting games on your memory stick, this video will walk you through the steps of just what you will need to do to compress files onto a thumb drive. There are a variety of steps you will have to follow and you’ll have to have a little bit of time to wait for your game to compress but the effort is well worth it.

This entertaining video demonstrates how to make a bottle rocket using tape, paper napkins, Mentos, and Diet Coke or Coke Zero. Try at your own risk! Make a pouch with the paper napkin. Put the Mentos in the pouch and roll the napkin with the Mentos into a tube shape. Open the plastic bottle of Diet Coke or Coke Zero. Place the tube in the top of the bottle, but don't let the Mentos make contact with the soda. Keep the napkin/Mentos tube stuck tightly in the top of the bottle. Re-attach the b...

Watch to learn how to replace a knob on a Neff gas hob. You'll remove and replace a gas hob knob on a Neff gas hob. Replacement knobs as well as burner caps and flame spreaders are easy hob spares to replace. As part of hob maintenance we also use a specialist hob cleaner to get a nice clean hob. This hob maintenance video clip illustrates the many different hob parts

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.