While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

Who doesn't hate Auto Correct? There's nothing worse than hitting 'Send' only to realize that your phone betrayed you by changing a word so that your message doesn't even mean the same thing anymore—especially when it's going to someone like your boss or parents.
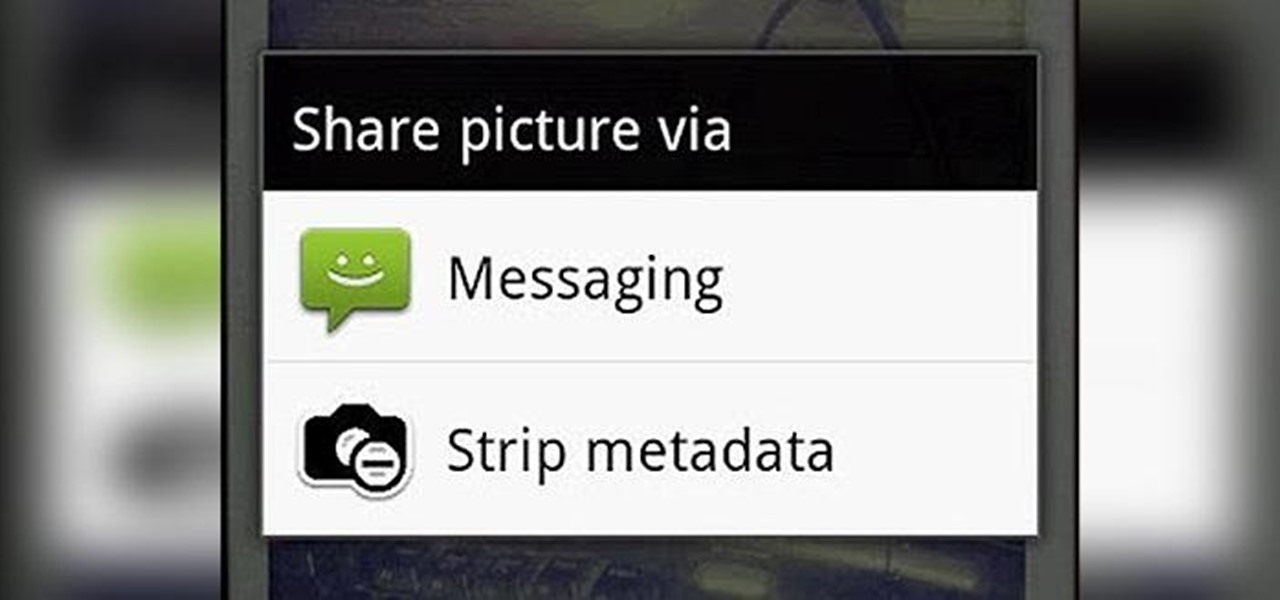
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.

I can certainly say that I don't like be ignored, and you're probably right there with me on that. Also, if you're like me, you don't like being blocked on an instant messenger, either. There's something about being shafted like that that can really cramp your style.

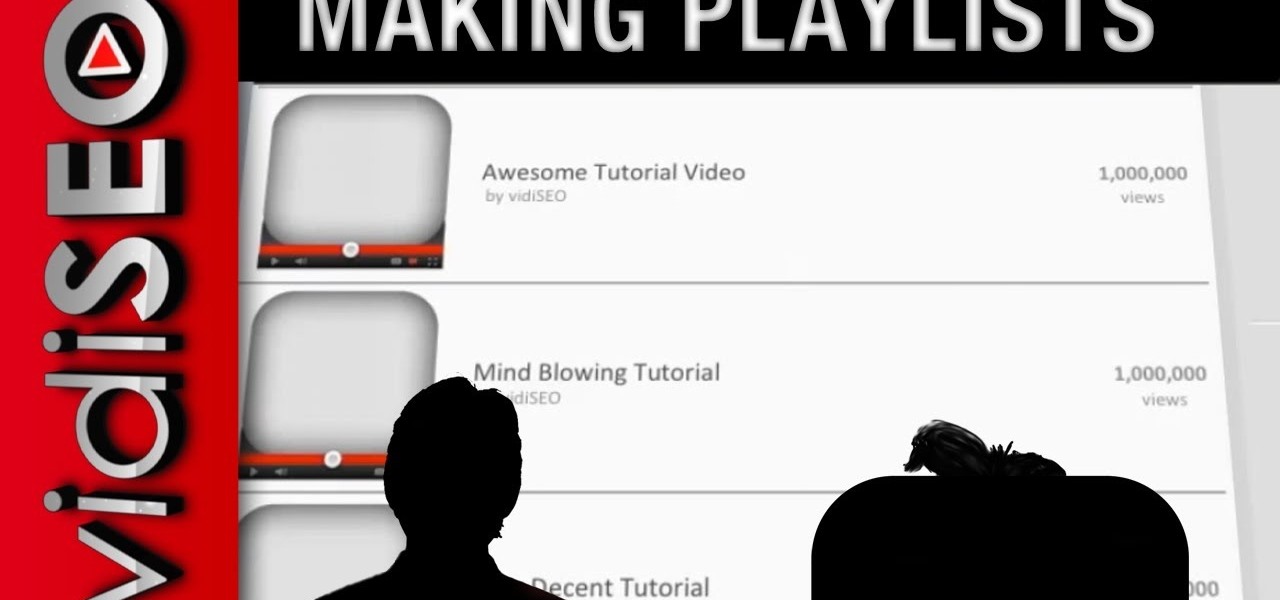
Playlists are a great way to organize and share groups of videos on YouTube. Playlists can consist of your videos, someone else's videos, or a combination of the two.

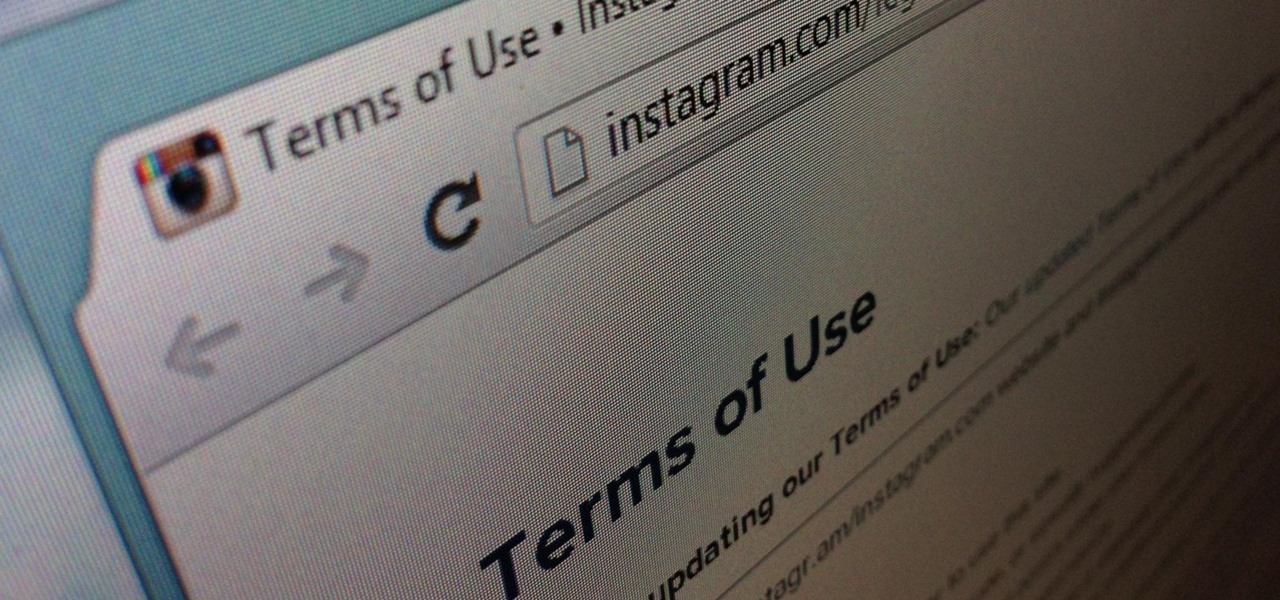
Instagram's controversial terms of service update this past month has spurred an onslaught of dismay and anger from users of the popular photo-sharing social network. The specific set of the new terms that set off this firestorm basically said that businesses could use your uploaded photos for advertisement, without you receiving any of the profit.

Before lead was removed from gasoline, lead from car exhaust got into the air, was breathed in by kids, lowered their IQs, and increased crime rates (there is a very strong correlation between IQ and criminal behavior).

It's been a rough week for Instagram. First they came out with a new terms of service that suggested the right to let companies use people's photos for advertisements without the user's permission. Then everyone started freaking out and debating whether or not to leave the online photo-sharing and social networking service. Now, they've changed the controversial wording saying that the selling of user photos "is not true and it is our mistake that this language is confusing".

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

Last week, Instagram stopped supporting media Cards on Twitter, meaning that in order to view a full photo shared in a tweet, you have to click through to Instagram rather than seeing it on your Twitter feed. Otherwise, the photo will appear to be cropped.

So you've learned all of the dance moves to Gangnam Style and made your very own papercraft version of PSY that dances whenever you want him to. Now it's time to take your obsession a step further—by making yourself the star of the Gangnam Style music video. JibJab, the custom e-card site, has created a free tool that lets you use any photo to replace PSY's face with yours (or whoever you choose), then share the video with your friends.

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Recognizing the signs of schizophrenia is the fist step toward getting help and proper treat for a loved one with this serious mental health affliction. With proper medication and therapy schizophrenia can be controlled so check for and understand what to look for.

This video tutorial from agseo presents how to unlock applications in Facebook social internet network. For more detailed information go to www.agseo.blogspot.comTo unblock Farmwille and other applications on Facebook social network login to your Facebook account.From top menu Account drop-down list select Privacy Settings.Then select Applications and Website from the newly opened window.Select Blocked Applications (click on Edit Blocked Applications button).A list of all blocked applications...

An American Ballroom Companion presents this social dance demonstration from the Library of Congress. Watch this demonstration traditional dance video on the Ragtime Dance: Castle Walk. Not for beginners - this is not an instructional, step by step video. It is an authentic, professional demonstration of the Ragtime Dance: Castle Walk.

This is a demonstration of 17th Century French minuet steps. A minuet is a social dance of French origin for two people.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.
Welcome back Hackers\Newbies!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Sherlock Holmes is one of the most famous characters in modern history, and has appeared in film more often than any other character. No less than 78 different actors have taken their turn at portraying the enigmatic deduction machine in various mediums, and each has brought their own foibles to the role. Some of the names may even surprise you: Tom Baker, John Cleese, Peter Cushing, Charlton Heston, Christopher Lee, Roger Moore, and even Leonard Nimoy.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

In this video, a man performs a French, Baroque-era (17th Century) style dance, the minuet. A minuet is a social dance of French origin for two people. This video gives a demonstration of minuet combinations.

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.