
How To: Add media to your Facebook profile
Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.


Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

Thanks to modern "smart phones" and the internet, media by the people, for the people is finally a reality. Here's how to use your phone to be a mobile journalist.

Everybody knows it really shouldn’t matter, but sometimes entering a school cafeteria without a lunch mate can seem like walking the plank. Here’s how to survive the stroll.

Why waste your vacation dollars on pricey hotel rooms when there are cheaper – and sometimes free – alternatives? Watch this video to learn how to find cheap (or free) places to crash on vacation.

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?
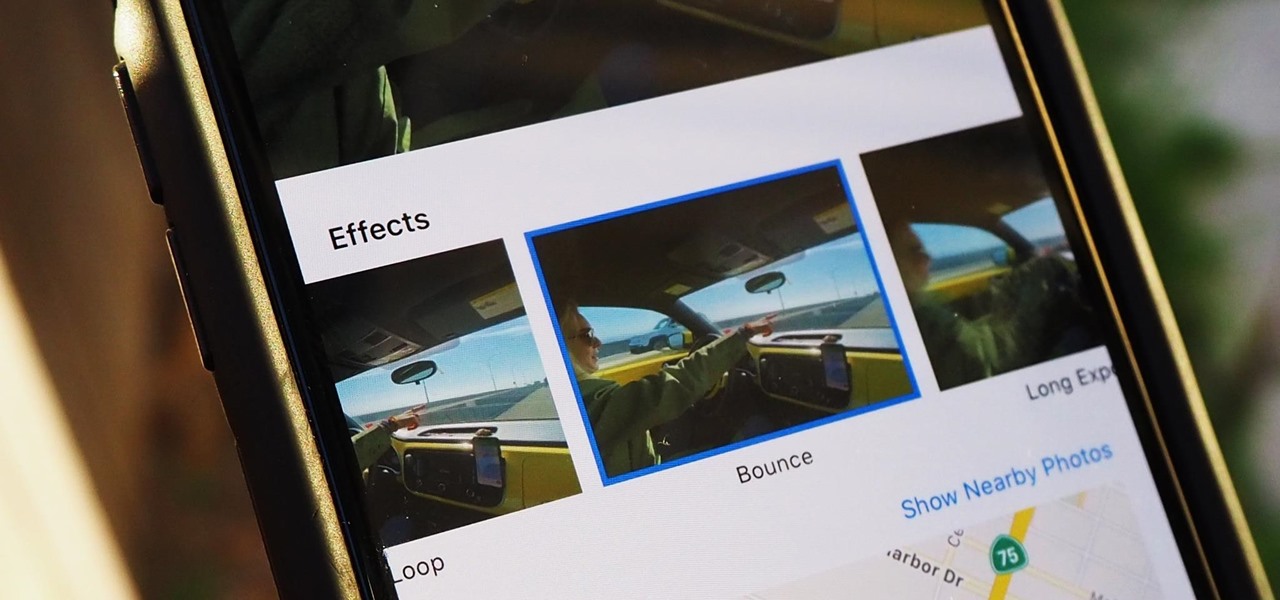
Live Photos haven't caught on as much as Apple probably would like, but they're far from the gimmick that critics initially claimed they were — and things are only getting better as time moves on. Some aspects of the feature are somewhat hidden, however, and you need to find them to unlock Live Photos' full potential.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?
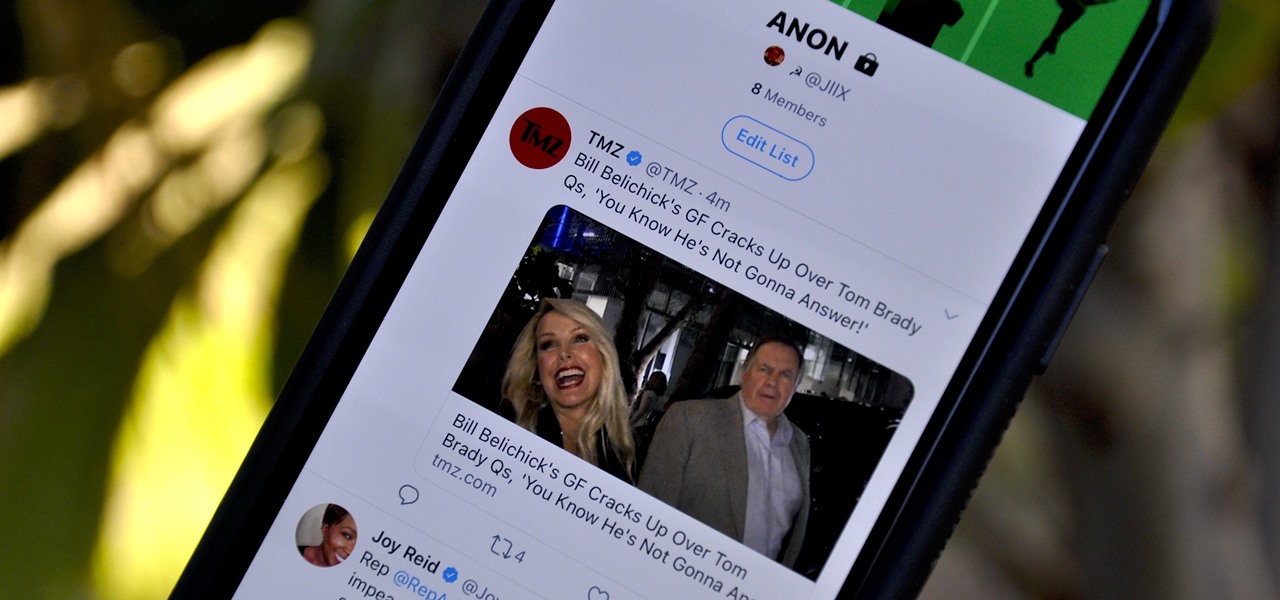
Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.
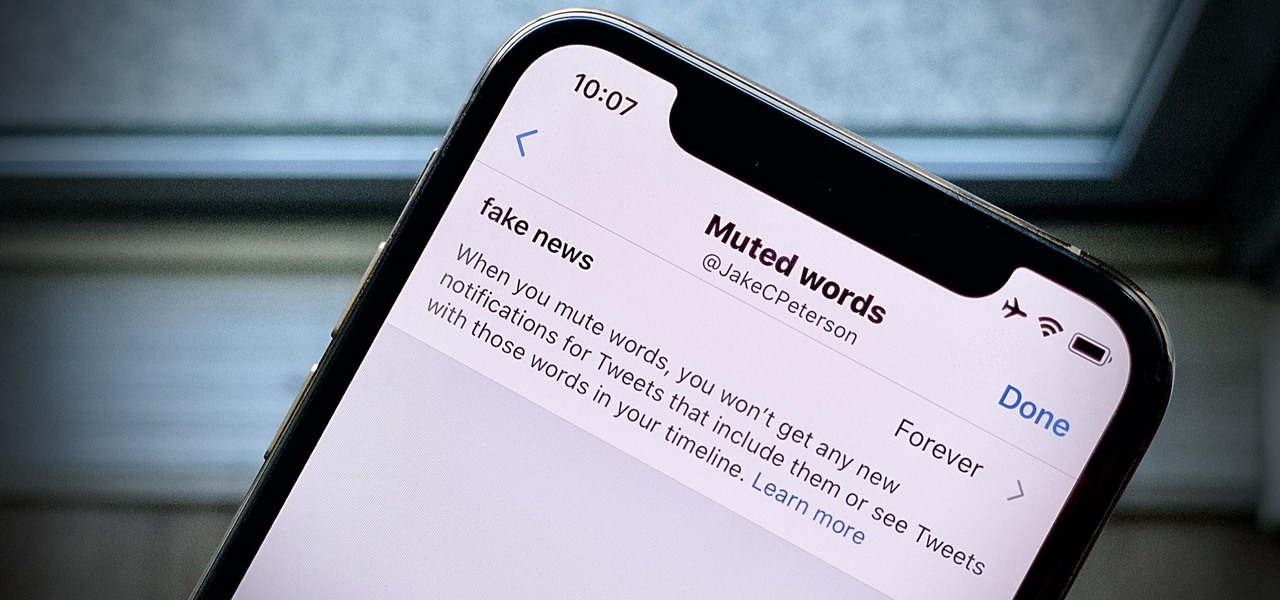
Twitter can be a wonderful place for people to express their emotions and chat with each other in brief. However, it can also be a breeding ground for hateful comments, foul language, and a whole lot of political talk.
If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.
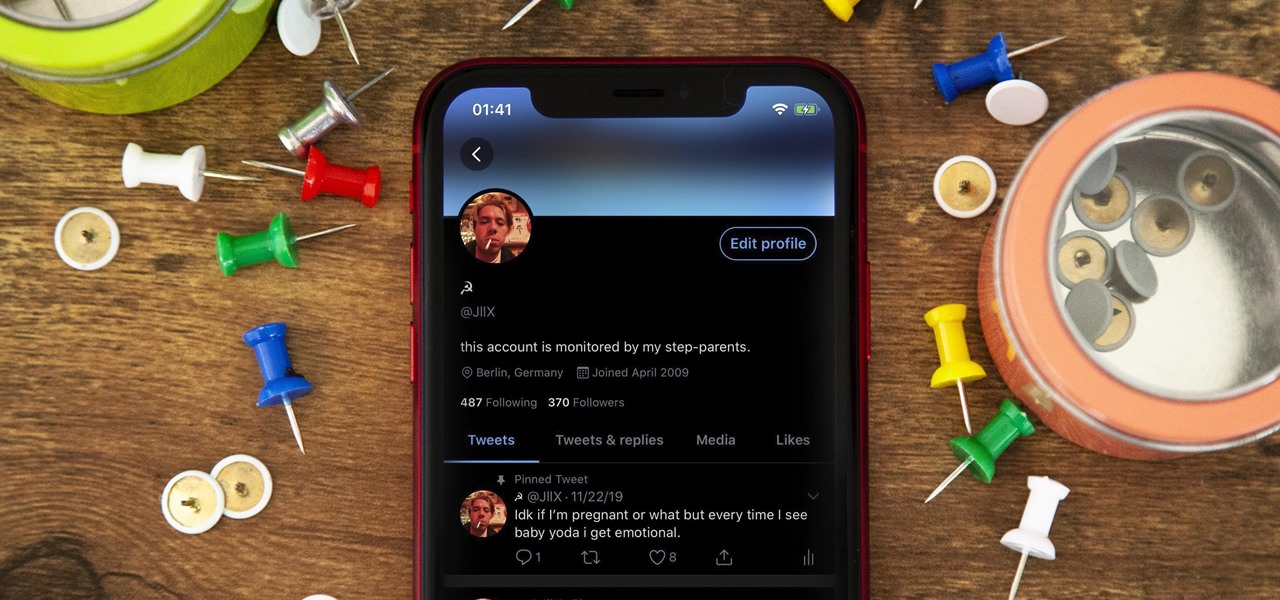
Pinning a tweet is a great way to get the point across because it's the first post people see when they visit your Twitter profile. When you pin a tweet, reply, or retweet, it sticks to the top of your profile, whether you create new tweets or not. It's the perfect spot to place one of your more popular tweets, a fantastic blog you wrote, or even just a joke that shows your personality.
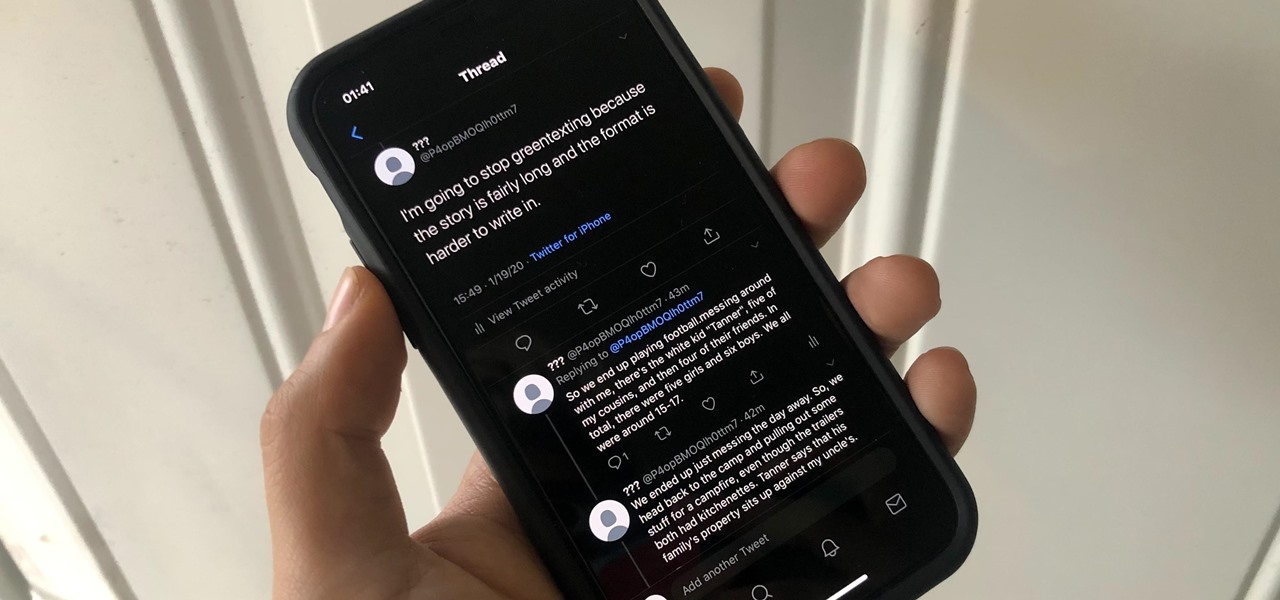
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

While the long-awaited HoloLens 2 officially arrived this week, details leaked about another, arguably longer-awaited AR headset, the fabled wearable from Apple, and a previously undisclosed partner assisting the Cupertino-based company with the hardware.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Augmented reality gaming startup Tilt Five is ready to reinvent old school Dungeons & Dragons-style games for the modern age with its augmented reality headset and tabletop game system.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

TikTok is great for creating short videos of people lip-syncing to songs or comedy sketches, but it's also very entertaining to just browse and share cool videos with friends. When you stumble across a video you like, you can download it onto your phone to watch over and over again. Even better, you can turn the video in a live wallpaper if you just can't get enough of it.

In late-2017, Instagram rolled out a feature that automatically saves your ephemeral Stories to a private archive. Before that, Stories disappeared into the ether after 24 hours, but not everyone was comfortable losing these precious photos and videos. If you post to Instagram Stories quite often, you can now easily access your history from your account — and you might not even know it.

This week, we're beginning to see the wide ranging impacts of some of the early iterations of augmented reality hardware and software.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

Snapchat is mostly credited as the first AR social network, and, like most social media companies, its revenue model is nested largely within advertising. As such, the company now has a new avenue for branded content.
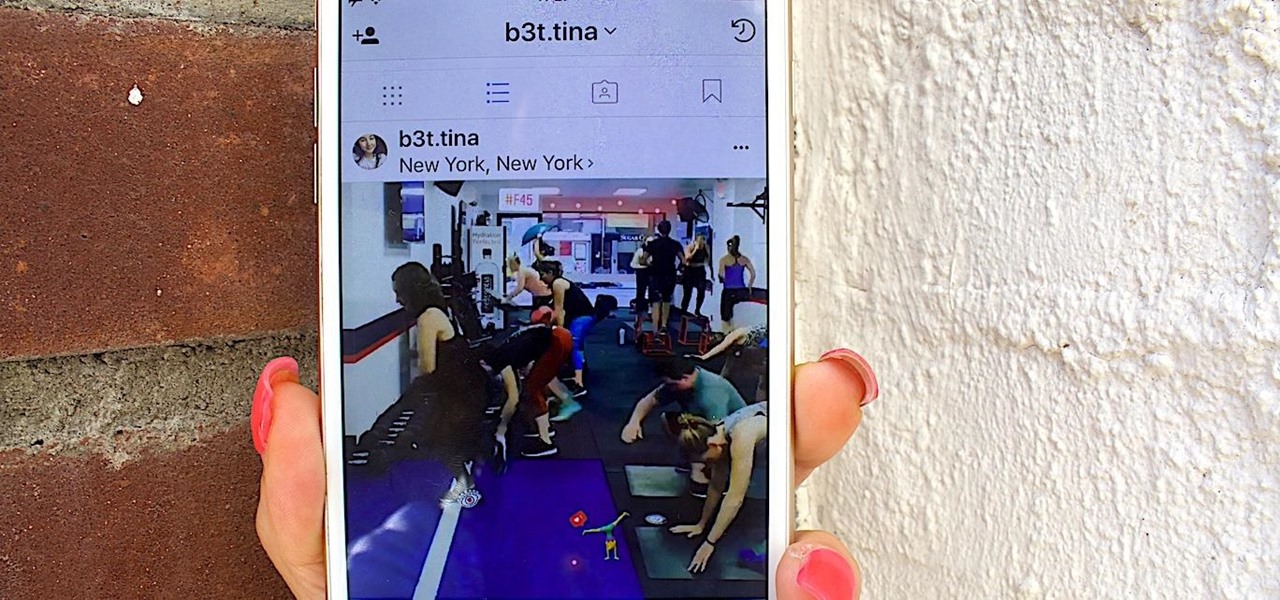
I have nightmares about trying to reply to hundreds of strangers on social media. To prevent the overwhelming feeling of having to small talk with people I don't know, I'm now aiming for more control over the ways that people can contact me. One way is to stop users from hitting me up on Instagram Stories.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.
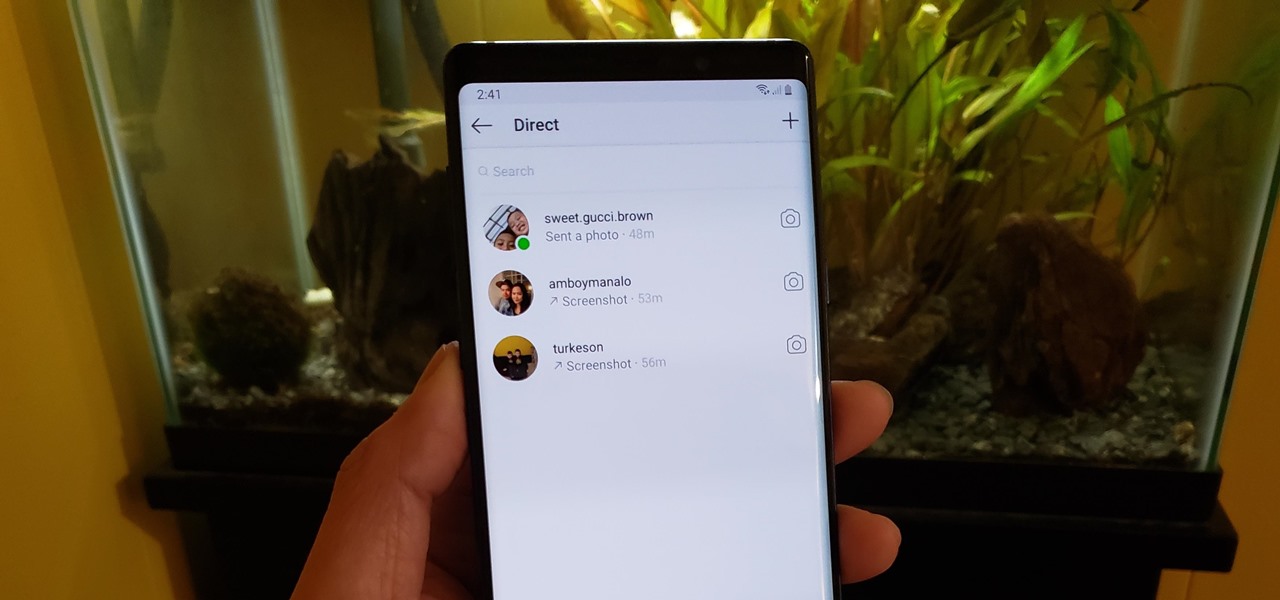
If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

To keep fungal pathogens at bay in their crowded homes, wood ants mix potions to create powerful protection for their nest and their young.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

Practically every smartphone comes with a built-in camera app, but these apps are generally created by the device's manufacturer. And let's face it, manufacturers are hardware companies first and foremost, so they don't always produce the best software.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

Better sleep, smartphone news, and changes to your favorite forms of entertainment. There's been a lot going on over the last couple of weeks in the world of tech, and we thought we'd show you all of the need-to-know products, updates, and ideas that we think are most important.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.