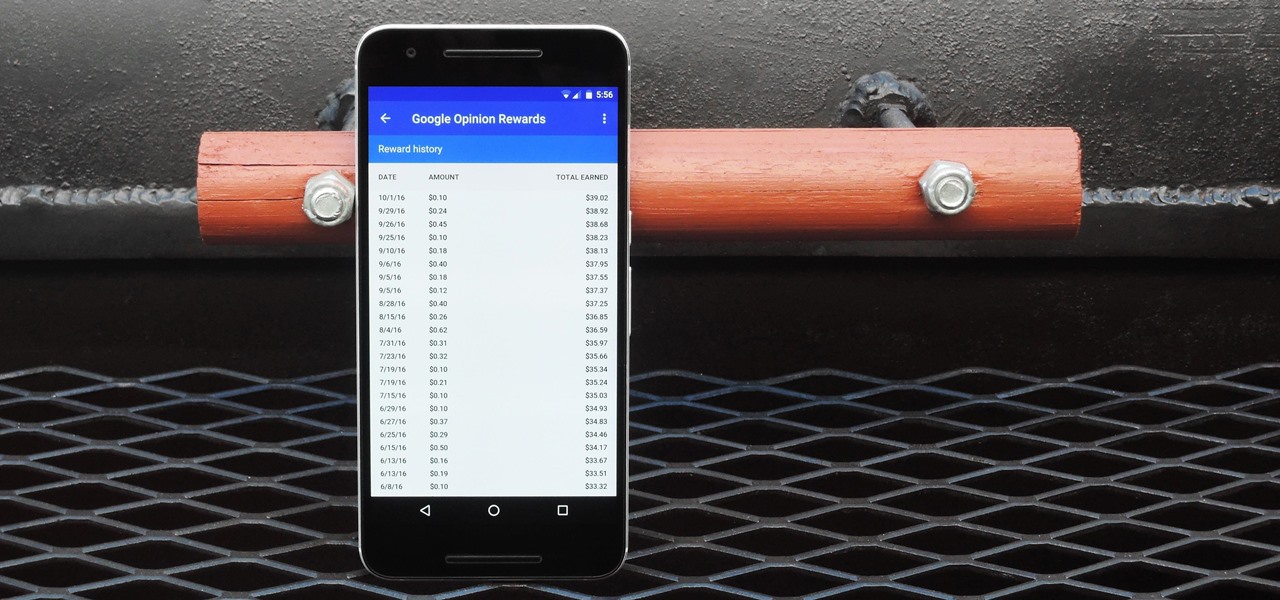
In case you didn't know, Google has an awesome app that gives you free money to spend on apps, games, movies, books, and virtually anything you can buy on the Google Play Store. The app is called Google Opinion Rewards, and all it asks in exchange for the Play Store credit is that you answer a few questions every now and then.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Week 01 : 9/31 - 09/06 Read Chapters 1-2 of Creating Motion Graphics with After Effects

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.
Hello, Hackers/Viewers, Today's topic is going to be based on how to disable autorun for Removable Disks and Drives. Doing that is very easy, i you read the below!

The new Jelly Bean 4.2 is a great improvement over previous Android versions for the most part, except one thing—the lockscreen. Users have voiced their complaints in regards to Android 4.2's new lockscreen features, and it's not pretty.

Scrabble Bingo of the Day: GRUYERE [n] One of the most famous types of cheeses made in Switzerland, made from the milk of a cow. It's a hard yellow cheese named from its town of origin, Gruyère. The cheese can be spelled with or without the grave accent (`) on the è, though in the United States it's usually without.

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.

Beware: After a new caucus — the Congressional Caucus on Virtual, Augmented, and Mixed Reality Technologies for the 115th Congress — formed in the US House of Representatives, the government has decided to go after all mixed reality head-mounted displays. The HoloLens, Magic Leap — nothing is safe anymore.

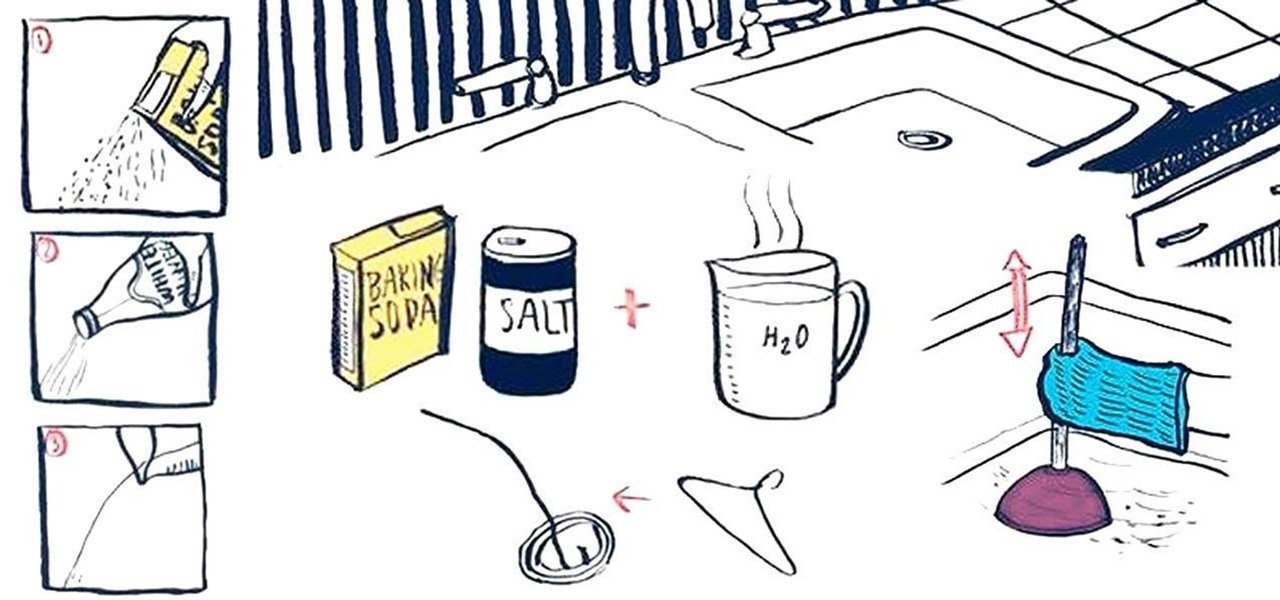
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

The last presidential debate of 2012 is over between President Barack Obama and Republican nominee Governor Mitt Romney. Now it's up to you to choose your candidate by election day on November 6th, 2012, and more importantly—VOTE!
On May Day in 1971, the US Army rounded up approximately 7,000 protesters into a stadium in Washington, DC that they treated like a make-shift prison camp. Have things changed in the past 40 years? Now a Department of Defense document has been leaked to the Web that details "Internment and Resettlement Operations." The manual outlines policies for processing detainees in internment camps domestically and abroad and how to "re-educate" unruly activists. Alex Jones, host of the Alex Jones Show,...
Russia’s top military officer warned Thursday that Moscow would strike NATO missile-defense sites in Eastern Europe before they are ready for action, if the U.S. pushes ahead with deployment.
Infowars has a great new article on the myths of 'limited war'. It's a great read. Here are some excerpts:
Qualifications and Powers I. Executive (President)

The Science Cheerleaders are a group of current and former NBA and NFL cheerleaders, all of whom also happen to be accomplished scientists, engineers and doctors.

From the Huffington Post: Billionaire Republican Meg Whitman reported Monday that she has spent more than $99 million in her quest to become California's governor, while Democrat Jerry Brown is saving money for what could become the most expensive gubernatorial contest in American history.

GOOD, a Los Angeles-based magazine focused on doing good in the world, along with LAUSD, The USDA People’s Garden Initiative, The Environmental Media Association, The National Gardening Association, The Urban & Environmental Policy Institute, The California School Garden Network, and Mia Lehrer & Associates, is sponsoring a contest for people to help design a garden for a LAUSD school. GOOD will help build the winning garden design, and they'd like your participation, too.

In order to win at playing slot machines, you need to keep a few things in mind. Slot machines are not random. They are programmed to pay out at certain times, in certain amounts, and at certain intervals.

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

If you want to stop telemarketers from calling, use this guide and try a multi-pronged approach. You Will Need

Thanks to HTC's new policy on updating their apps through Google Play, we can now get new features without having to wait for a full Sense OS update.

How Get Paid for Donating Plasma. Donating blood doesn't pay, but donating plasma—the part of blood used to treat hemophiliacs and burn victims—does. See if you qualify.

When it comes to your cell phone, do you feel like you’re paying more and more for less and less? Get the upper hand with these tips. You will need:

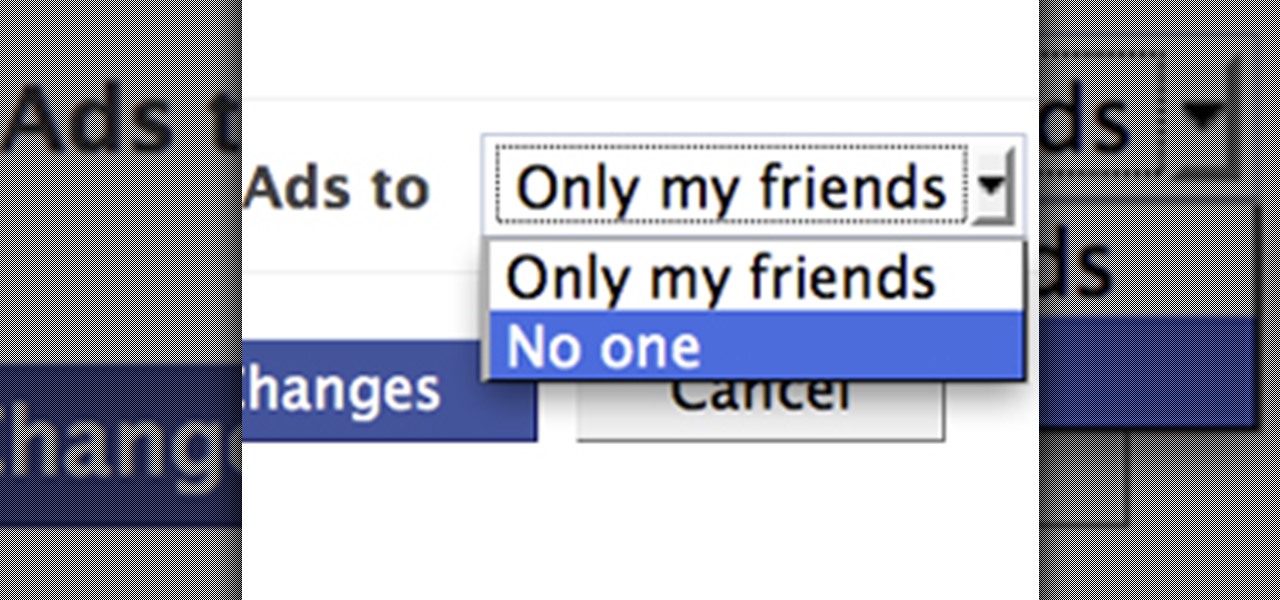
Facebook is constantly evolving, and lately it seems like a bad thing, at least for its users. First, you had to opt out of Instant Personalization, which shared your personal information with Facebook's partner sites. Then, you had to take drastic measures to secure your home address and mobile number from third-party apps and websites. And now?—Now you need to opt out of Facebook Ads.

FRIDAY SEPTEMBER 24 Tonight one of the worlds most intense directors has a premiere of his new film.
Student group hopes to keep bikes on campus By Conrad wilton · Daily Trojan

U.K. department store Debenhams has pulled back the curtain on the reality behind swimsuit modeling. As expected, the standard model goes through quite a bit of "Photoshop magic".

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

Now that Apple Pay Cash has arrived, you (hopefully) might end up getting sent some money right from inside an iMessage. If so, that money gets added to your Apple Pay Cash card in iOS 11.2, which you can use just like any other card in your digital wallet. If you're not so lucky, you can still add money to the card yourself without having to wait for a contact to send you money first.

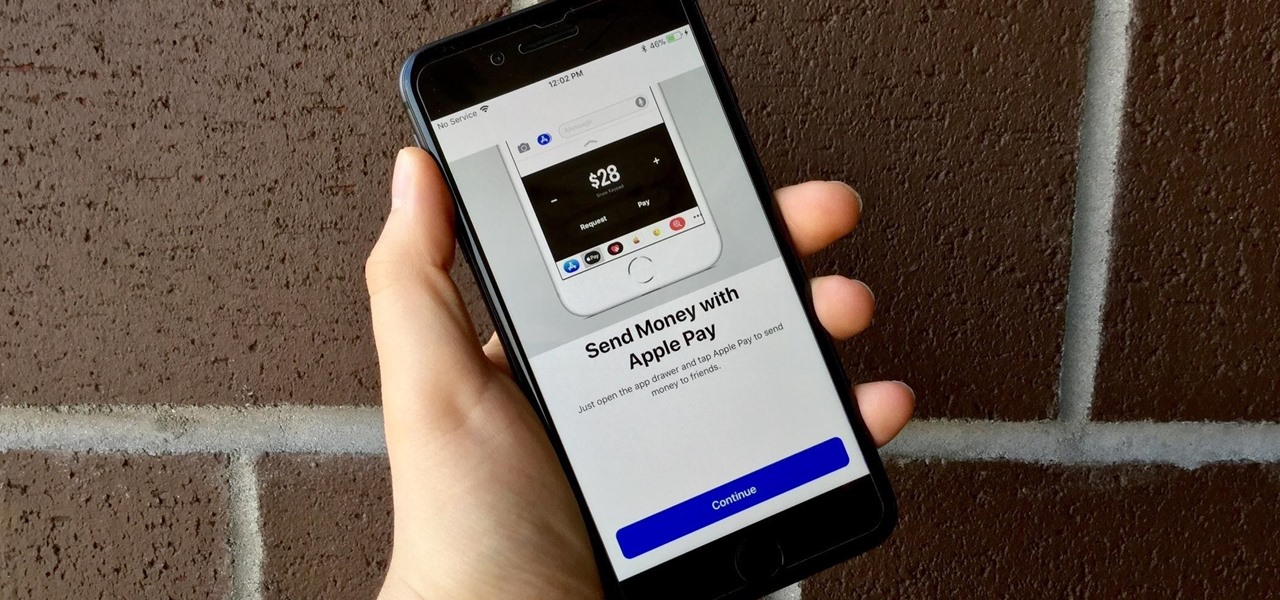
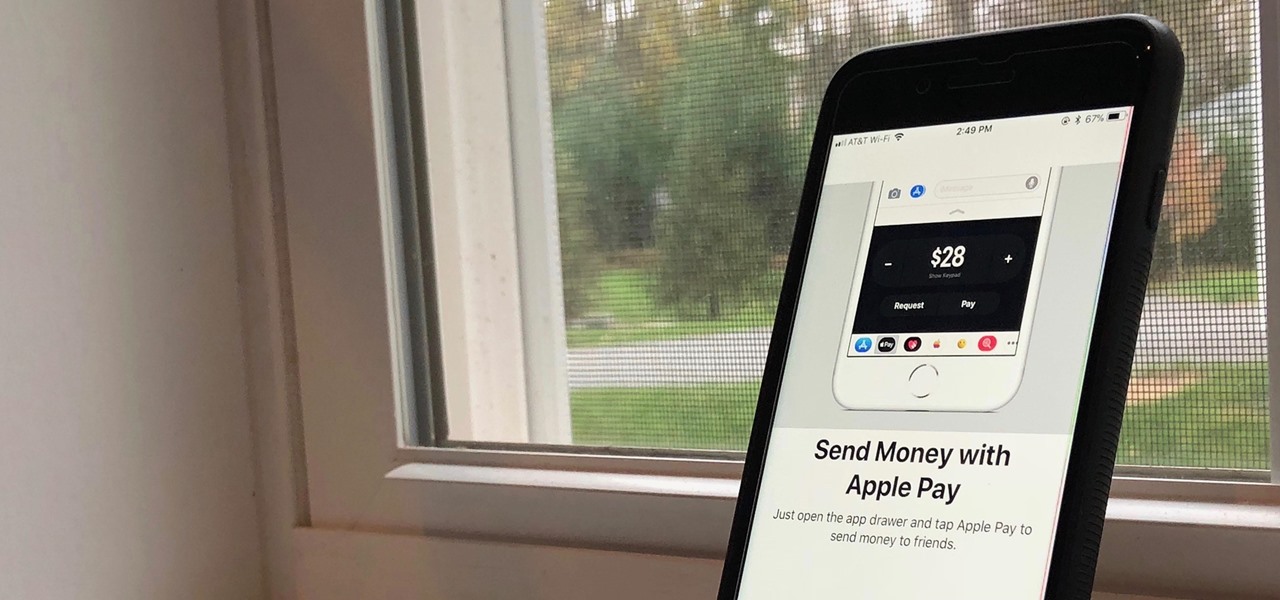
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

First showcased back in June at WWDC, Apple Pay Cash is Apple's answer to Venmo. Although iOS 11 has been out in the wild since September, this new iMessage feature has been mysteriously absent. That's finally changed with the second beta of iOS 11.2 — Apple Pay Cash is here.

Baseball fans can now leave their wallets behind at specific stadiums throughout the country. A new upgrade by Appetize to the foodservice and retail technology used at ballparks means you can now use Apple Pay to make purchases at 5 Major League Baseball stadiums.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.