During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

Recently, buyout talks between Google and Groupon ended with Groupon turning down Google's $6 million offer. But with Amazon backing LivingSocial, should they have? Your guess is as good as mine, but one thing's for sure— Groupon has a great voice, and they're sharing it with the world via their Public Groupon Editorial Manual.

Plantation Shutters Plantation Shutters give your home a clean and contemporary look that is both stylish and functional! This particular brand EuroVue by Bali are easy to install, even for the most novice do-it-yourselfers.
KEH has a great website and awesome resources for photographers who don't need the newest thing, but know lots of other photographers do, which means KEH is there to scoop up all the gently-used and barely-used gear for the more budget minded or just plain more sensible. Also, KEH is the go-to place for vintage equipment. Who needs to get in a bidding war on eBay and pay more than the true value of a vintage camera? Keep your eye on KEH instead.
What should young athletes ages 7-14 eat to get bigger and stronger? Children's Healthcare of Atlanta's Sports Nutritionist, Diane King, discusses the value of energy bars and protein shakes for this age group

The free version of tools is great and offers tons of useful features. The paid "suite" version is a great value too - it lets users collaborate, share updates, manage edits.......the list goes on.

An Australian Liberal senator has slammed the use of Lego to promote creativity among ABC staff as a "bizarre" waste of money, suggesting finger painting would have been cheaper and just as effective.

Ecouterre posts seven upcycled circuit board fashion accessories, many of which were part of a group show to help raise awareness about e-waste and overconsumption.

A few tips to make life on the mountain easier, such as the value of placing a Nalgene bottle full of hot water in a sleeping bag. This is shot from Mt Kilimanjaro the highest mountain in Africa. Throwing a Nalgene water bottle in your sleeping bag can add a great element of warmth to your camp. Keep sleeping bags warm with hot Nalgene water bottles.

How to install Java JDK (Java Development Kit) Go to the Oracle Java SE Download Page and click "Download".

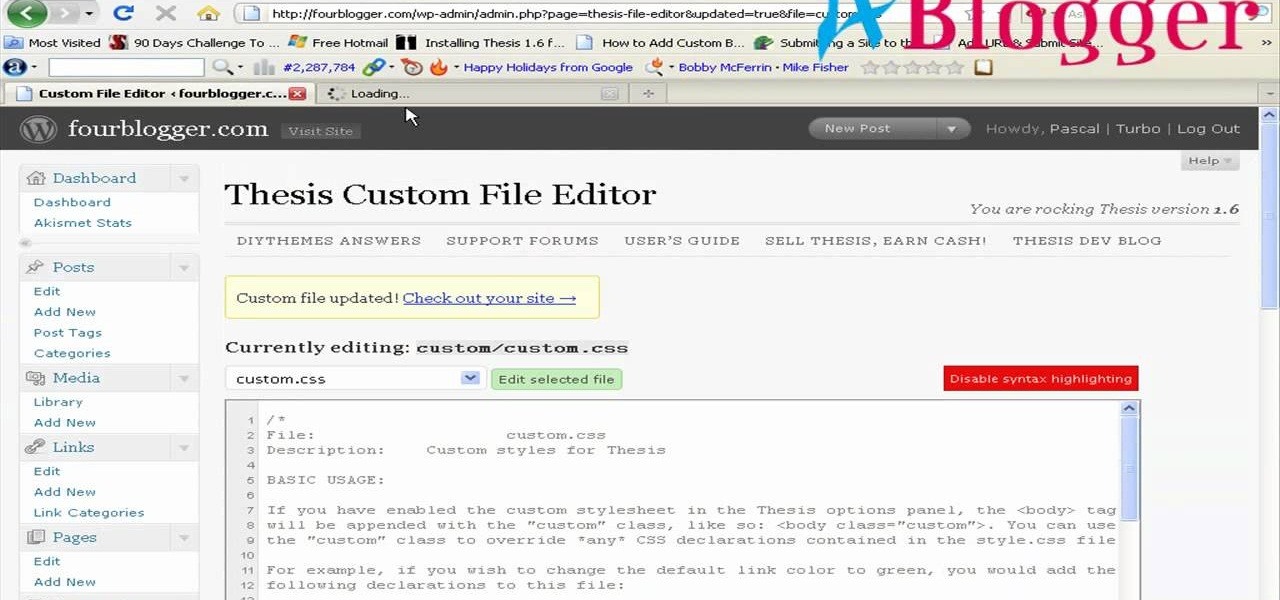
First you need to go to your site and click any post you want and see the simple heading and now you want to change the background. To do this, first you need to go to your word press admin and then click custom file editor in thesis options it will open your code window and here you will have to paste the code which is showing in the video. you will have to paste it in custom.css. After pasting the code you have to click the green save button.

Camera shake is often an unwanted effect in photography, when a telephoto lens or long shutter speed has been used for a camera that hasn't been stabilized. The images subject to camera shake appear blurry and smeared, which is often considered an error - though some photographers find artistic value in camera shake and purposefully try to cause the effect in their art.

In this video tutorial, viewers learn how to speed up the Windows XP Start menu. Begin by clicking on the Start menu and select the Run program. Then type in "regedit" and click on OK. Now select H KEY_CURRENT_USER, go to Control Panel and click on Desktop. On the right side of the window, scroll down the list to find Menu Show Delay. Double-click on it, change the value to 0 and click OK. This video will benefit those viewers who use a Windows computer, and would like to learn how to speed u...

In order to make a smoothie that will give you healthy and glowing skin, you should begin by considering the nutritional value and restorative nature of certain fruits. To make a smoothie that will support your collagen, elasticity, and your complexion, combine the following fruit in a smoothie: blueberries, oranges, strawberries, mango, bananas, and water. These will also provide beta keratin and antioxidants.

In this how-to video, you will learn how to change your start menu text. You will need resource hacker and regedit in order to perform this. First, open resource hacker. Click file and open. Go to 37, and click on 1033. Change 578 to whatever you want the text on the start menu to be. Press compile script. Next, save this file. Now, open regedit and go to software. Go to shell and click modify. Change the value data to the name of your .exe file, which should be saved in the windows folder. N...

Ubuntu and Windows may have trouble syncing time because when they are dual booted, they both assume that your hardware clock is set to a different time setting. Ubuntu assumes that your clock is set to UTC and Windows assumes that your clock is set to local time. Answers Launchpad has solutions to fix the syncing issues. To correct the issue, configure Ubuntu to be set to local time. Launch your terminal window and click on the description box. In the code string change the UTC default value...

In this video the instructor shows you the diameter, radius and also how to find the circumference of a circle using a cookie as an example. When you draw a line against the cookie passing through its center and touching its boundaries, it is a diameter of the circle. Radius of a circle is half the diameter of the circle. The length of the circle along the border of the circle is called circumference of the circle. The formula to compute the circumference of a circle is 2 * Pi * r, where r is...

ITStaff teaches you how to design casino chips in Adobe Photoshop. You start off with a white or grey circle which will be the chip itself. You need to start decorating this so you create five trapezoids and space them equally from one another. Give them a dark red color. Next you create a red circle in the middle, touching the bases of those trapezoids. Add a crown or a symbol created or from the Custom Shapes menu. You also need to create a value so type in a number and add the dollar sign ...

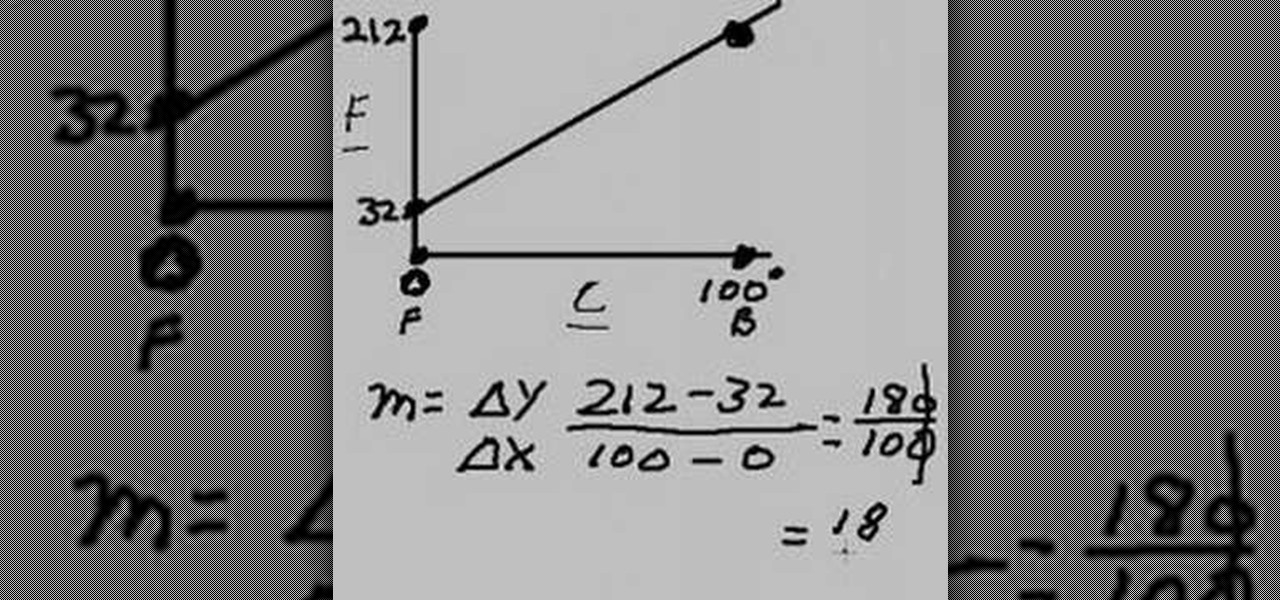
The video teaches how to convert degrees Celsius to degrees Fahrenheit. First the boiling points of 32 degrees Fahrenheit and 100 degrees Celsius are plotted on the Y and X axis. Then a line is drawn to join them both. The value m is delta Y (boiling point minus freezing point, i.e., 212-32)/ delta X (boiling point minus freezing point, i.e., 100-0). So m works out to 180/100 or 1.8. Then the formula y=mx+b (intercept of y = 32) is used, substituting X with Celsius and y with Fahrenheit, to c...

In these PHP basics video the tutor shows how to do form processing. Handling forms in PHP is basically the main functionality of PHP. The forms in HTML take the values of a from and send them to the PHP in real time to do the form processing. In this video the tutor shows how to make a HTML form from the scratch inserting a form into it with some fields and buttons. Now he makes the form post a method to a PHP page when you submit it. Now he shows how to make a PHP file from the scratch by w...

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

When adding and subtracting integers, follow these math rules: Adding Integers

Your ability to control exposure in the Camera app is much better in iOS 14. Instead of setting the exposure for a single shot, you can also lock an exposure compensation value for an entire session while you take photos and videos. A session ends as soon as you exit the app, but you can also remind your iPhone to use your last used ECV the next time you open Camera.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster and some paint.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.