Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The day has finally come. About eight months after unveiling Magic Leap One: Creator Edition, on Wednesday, Magic Leap made the device available for order through a reservation page on its website.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.

Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

A newly-filed patent application from Disney Enterprises, Inc. teases more augmented reality lightsaber duels, either for at-home gaming or for the media behemoth's forthcoming Star Wars theme park.

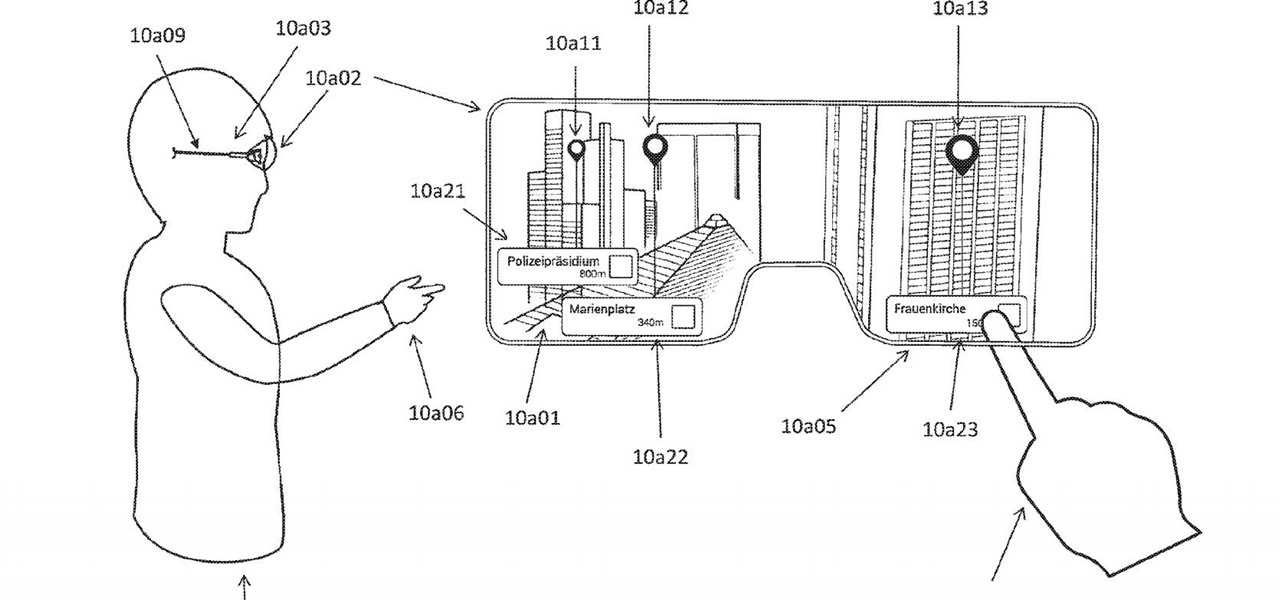
Just days after Bose did its best to frame a pair of glasses frames with spatial audio as "augmented reality," a patent application from Magic Leap, surfaced on Thursday, March 15, offers a similar idea, but with real AR included.

A new smartglasses powerhouse is rising in Europe, led by two of the region's leading brands, optical systems company Zeiss (also known as Carl Zeiss) and telecommunications giant Deutsche Telekom.

With Google's release of Poly API on Thursday, the search giant has found a way to simplify the workflow for AR creators by enabling the ability to integrate its 3D object search engine Poly directly into an application.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

With smartglasses designed for navigating drones and an AR drone racing game to its credit, Epson has just added another credit to its pioneering efforts in the AR-meets-drones space with the launch of a drone simulator app.

Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

5G is showing up more and more in the news, as an increasing number of companies jump on the bandwagon. AT&T made a splash earlier this year with their embarrassing "5G Evolution" debacle, and the other three major wireless carriers soon followed suit, detailing their own vague plans for 5G. Today we find another company has joined the fray, just not a cellular one — Apple has officially been approved to test 5G networks.

Apple has sprung a massive AR following since the announcement of their ARKit, with users waiting to see what exactly the tech giant will do next.

According The Venture Reality Fund, the introductions of Facebook's camera platform and Apple's ARKit catalyzed increased activity among companies developing consumer applications.

At the Microsoft Build 2017 conference in Seattle this past week, 3D application and game platform Unity, partnering with Microsoft, launched a contest that drives HoloLens developers to realize their ideas into a full-fledged application and possibly win money for it.

The keynote at this week's Vision Summit 2017, a two-day event put together by the Unity team in beautiful Hollywood, California, revealed a few new features coming to the Unity platform. They also previewed some of the beta features that are currently available for those less scared of the occasional hiccup.

Microsoft Build 2017, the first of Microsoft's big developer conferences for the year, is just a few weeks away. This very popular conference, which has been going on since 2011, is known to sell out fast. In 2015, it sold out in under an hour, and in 2016, in less than 5 minutes. This year was no different, according to VentureBeat; While not quite as fast as last year with so many rumors of HoloLens on the horizon at the time, this year's Build was sold out in 8 hours. And for this year's B...

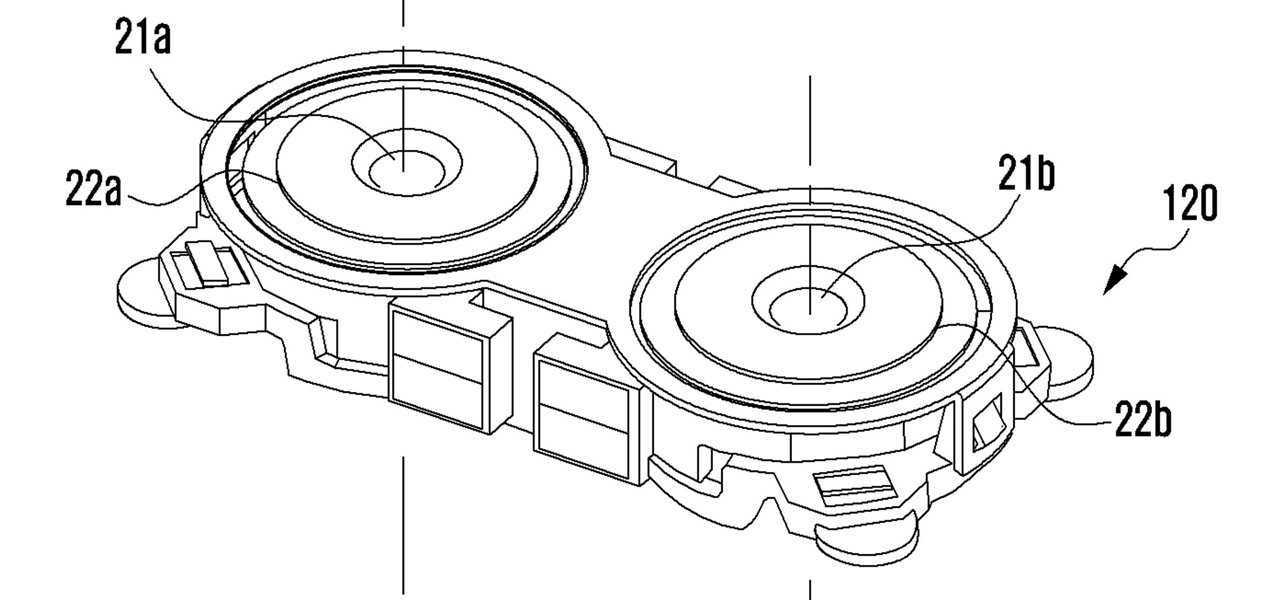
Dual cameras are increasingly popular right now for smartphones, but so far, Samsung has steered clear of all the hype. However, a new patent application shows that Samsung has been working on a dual camera system of their own, featuring tech potentially more advanced than what is currently on the market.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

We live in a marvelous age, a time where technology is driving us forward as a species at a rapid pace, and tech-driven miracles are becoming more and more commonplace. While the human race may not be focused on building the largest wonders of the world, as it once was in history, the current order of wonders are much smaller in scale—even internal.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

In recent weeks, Unity has made a few great leaps forward for HoloLens development. These new features will increase iteration speed inside Unity and quickly increase the output of applications in the mixed reality space. Of these new features, let's take some time to talk about Holographic Emulation and why this will do so much for the development community.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

The Fire TV Stick, as well as the Fire TV, may be limited by Amazon's fight on piracy, but after a quick sideloading of Kodi, the floodgates are back open with the freedom to stream just about any video or song you want.

As Android owners, we ultimately have to look at our device and ask the difficult question: "Where the hell did all these applications come from?"

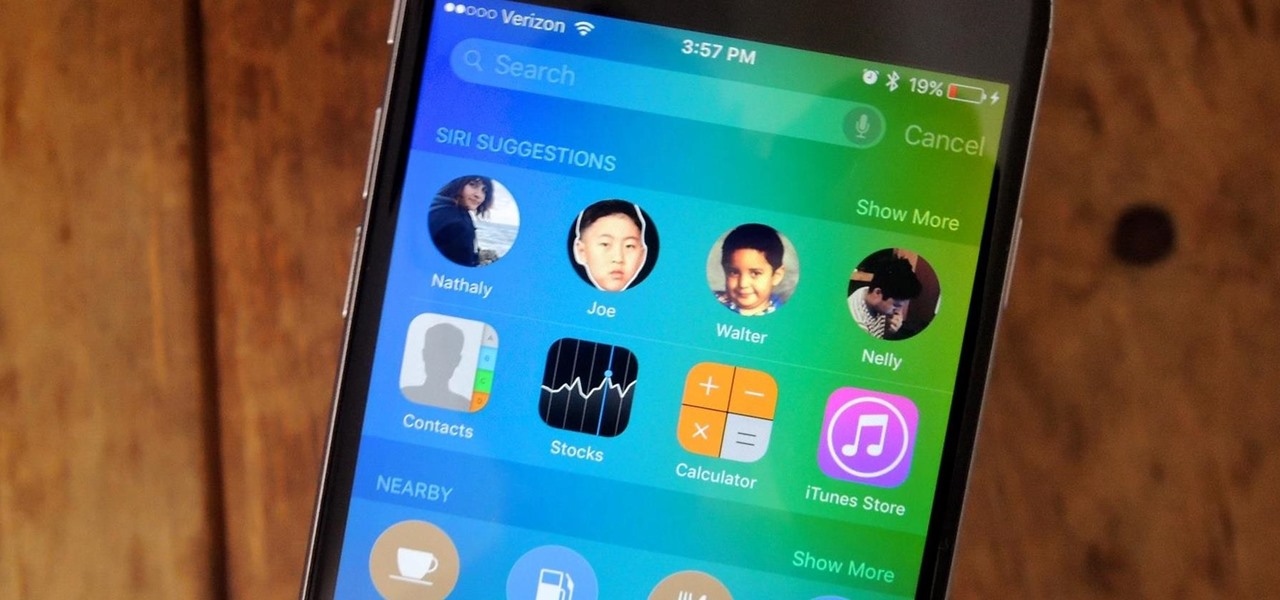
Apple certainly took a page from Google Now with its new "Proactive" search page in iOS 9. Located to the left of the home screen, the page provides quick access to contacts you've recently corresponded with, suggested applications, nearby places, and news articles based off of your Safari activity.

After the Galaxy Note 3 firmware updated to NF4, Samsung decided to remove the option to hide apps in the app drawer, replacing it with an uninstall/disable feature instead. Before, with the hide feature, you could simply hide third-party apps that were barely used or that you didn't want others to see. Now, you can only completely get rid of them.

Being fixated on all of the great additions to Android 5.0 Lollipop, it can be a little difficult to take notice in the features that went missing. For instance, lock screen widgets. It's speculated that the lack of practical use for lock screen widgets and the implementation of the revamped Lollipop lock screen may have lead to their departure, but some of us want them back!

Whether if it's to play games or watch Netflix or YouTube, children love using our smartphones and tablets. As an uncle of many, I don't mind my nieces and nephews using my gear, but I do mind them opening apps they have no business being in, like my photo gallery or messaging app.

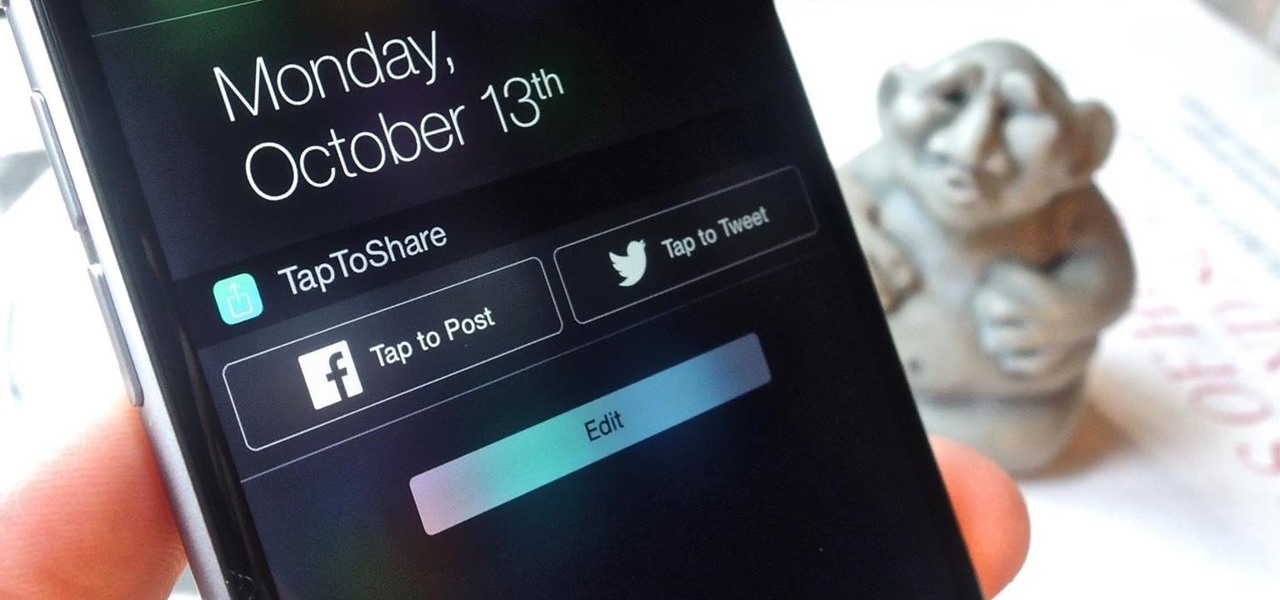
Back in the days of iOS 6, iPhone users were able to send a quick tweet from their notification center, but that has long since been removed. This convenient feature was missed enough on iOS 7 for devs to create a jailbreak tweak in its absence. Thankfully, due to the new widget capabilities of iOS 8, we can have Twitter back in the Notification Center along with Facebook.

Unless you're sporting an LG G3 or a mod that allows tap-to-sleep and/or tap-to-wake functionality, you're probably hitting the power button to sleep and wake your device. But that button may be awkward to hit, may be worn down, or may just stop working due to a manufacturer's error or a device drop. In any case, it is possible to end reliance on the power button, opting instead for a simple swipe gesture that will instantly lock your device.

Apple is bringing one of the biggest updates ever to its Messages app, including a feature that will allow users to send audio messages back and forth with the press of a button. Goodbye, voicemail.

CyanogenMod is one of, if not the most popular, third-party operating system for Android devices. It's so popular in fact, that it is the standard, out-of-the-box operating system on the recently released OnePlus One. CM is a lightweight ROM built on top of AOSP (Android Open Source Project), which is the base for all Android builds.

Changing an app's name on your home screen is not something you can do on stock Android or TouchWiz, but it should be. If you think of it merely from a customization angle, sure, it's not a big deal, but having the ability to alter an app shortcut's name can do wonders for cleanliness and being able to distinguish from similar icons.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.