This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Everyone's favorite Android modding tool is finally available for the Galaxy S6 and S6 Edge. Thanks to some hard work by Wanam and a few other developers, we can now install the Xposed Framework on Samsung's latest mid-sized flagship phones.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

With iOS 8.4 and iTunes 12.2, we got our first look at Apple Music, Apple's new streaming subscription service. While it's a little late to the party, there is definitely an incentive for iOS and Mac OS X users to switch over from competitors due to its heavy integration with the Apple ecosystem.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it.

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

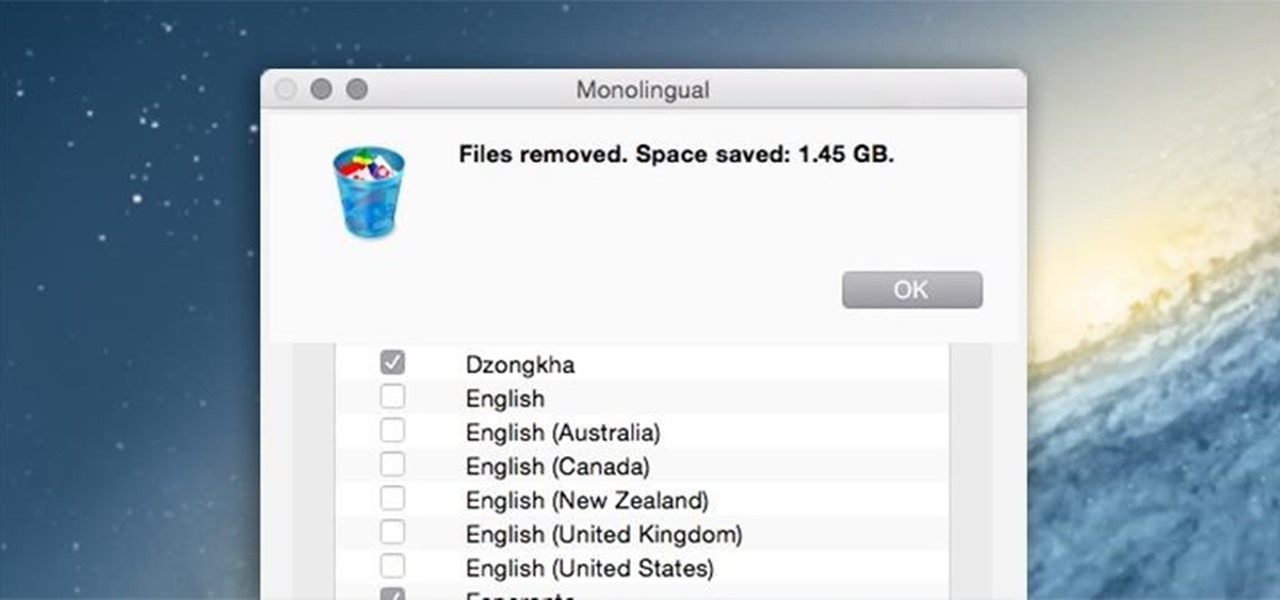
It's nice that most apps ship with multi-language support, but if you only need to utilize one, those extra language packs are doing nothing more than taking up space on your computer. And when you're getting close to filling up your hard drive, every little bit counts.

I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

UPDATE NOVEMBER 2015: The root process has changed for the Nexus Player now that the device is running Android 6.0 Marhsmallow. I've updated this article with detailed instructions on the new root process, but the video below still depicts the old process for Android Lollipop.

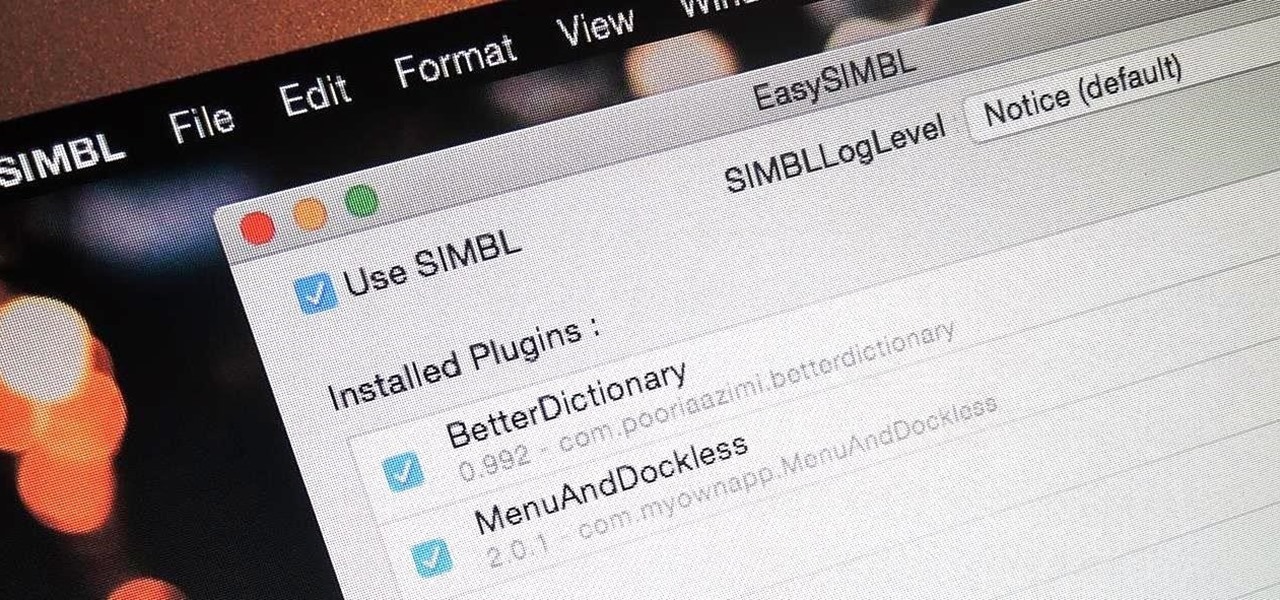
When you buy a Mac, you accept that you're giving up the customization found on Windows or Linux systems for a more fluid and secure machine. This is great for most consumers, but for those of us who'd rather opt for a tailor-made experience, there are always developers that can combine functionality with stability.

Being in a band, I exposed myself to years of extremely high volumes, so I can't hear as well as I once did. I'm not concerned about going deaf or anything, but I tend to have the volume raised to the max, beyond the "high volume" warning, whenever listening to music on my OnePlus One with headphones.

Android Lollipop's new Material Design interface does its best to strike a delicate balance between intuitiveness, usability, and aesthetics. For some folks, though, the use of a lighter color palette throughout the interface disrupts this balance.

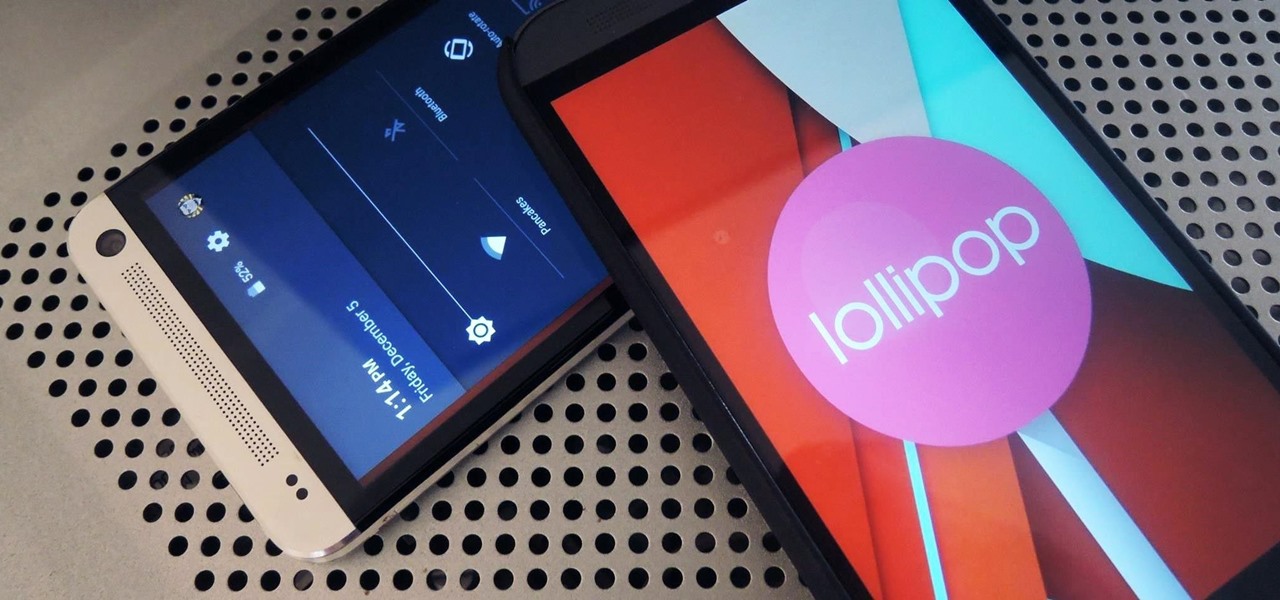
After a few unforeseen delays, the Android Lollipop update is finally here for Google Play Edition HTC Ones. This means that if you have an official GPE M7 or M8, or if you have simply converted your HTC One from a carrier-specific, Sense-based model to a Google Play Edition, you should be receiving an OTA notification shortly indicating an update.

The vague 90-day release window for CyanogenMod 12 has done nothing to stop my craving for Lollipop on my OnePlus One. Luckily, there are other "unofficial" means of getting my hands on it. Since CyanogenMod still gives users a way of building their own variants of their ROM, we can install user-compiled versions of CM 12 pretty easily.

Practically every kid in the '80s would rush home after school to put in some time on the first-gen Nintendo before their parents got home. Games like Super Mario Bros. and Super Smash Bros. were synonymous with fun times, and to this day, call up a wave of nostalgia amongst Generation-Xers.

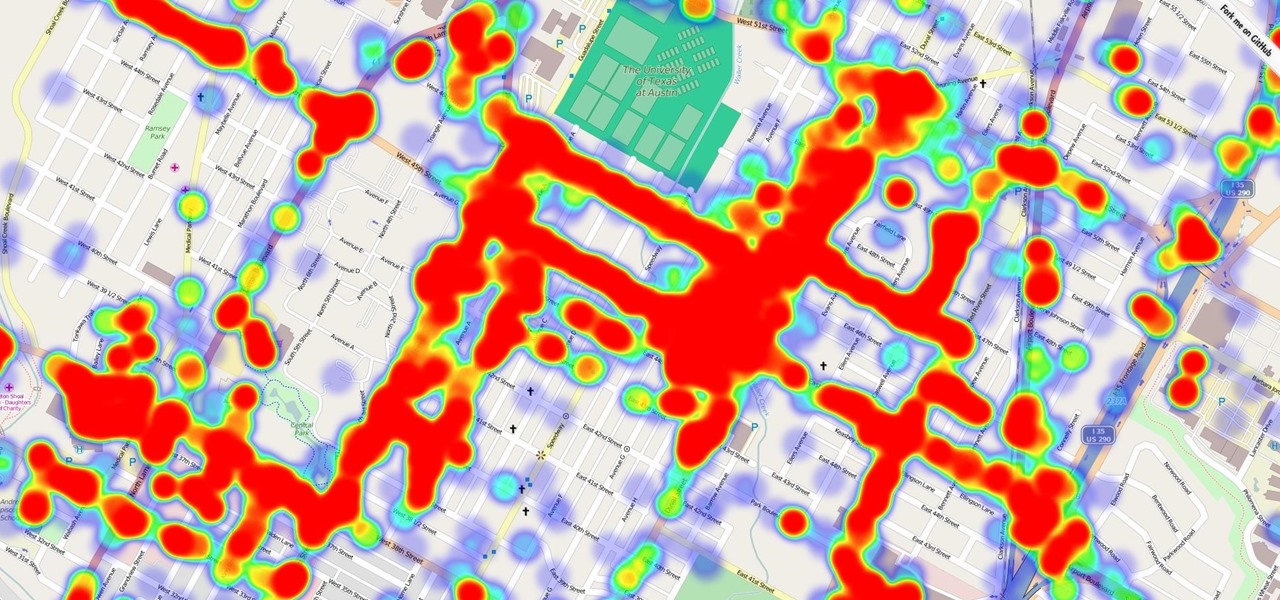
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

Google makes backing up your contacts, messages, and Wi-Fi passwords extremely easy, but leaves you out in the cold when it comes the data on your internal storage. With most Android devices now lacking SD card support, when you unlock your bootloader or do a factory reset, you're stuck having to back up everything to your computer beforehand.

You're in the middle of cooking and a car alarm, cute kitten, or neighborhood brawl made you step away from the stove for a few minutes longer that you should have. It happens to almost every home cook. Most of the time, nothing dramatic happens, but every now and then, you end up with something like this:

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

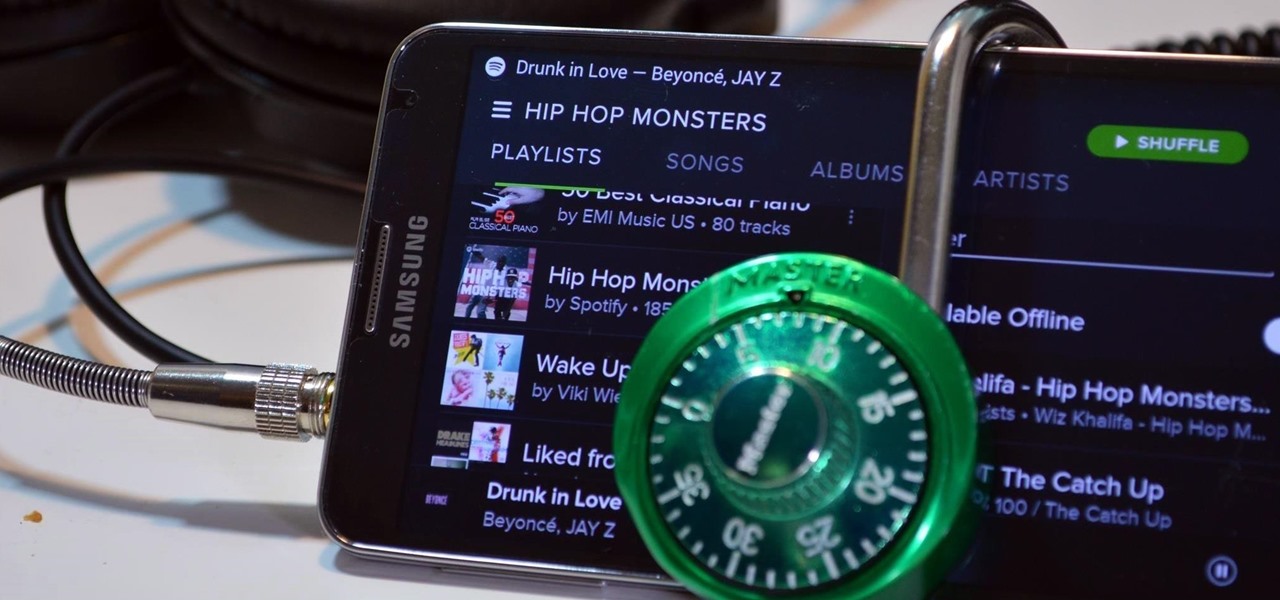
With over 20 million songs, Spotify has become my go-to source for music. I can stream tunes to my desktop or phone, without ever having to worry about storage space being eaten up.

Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

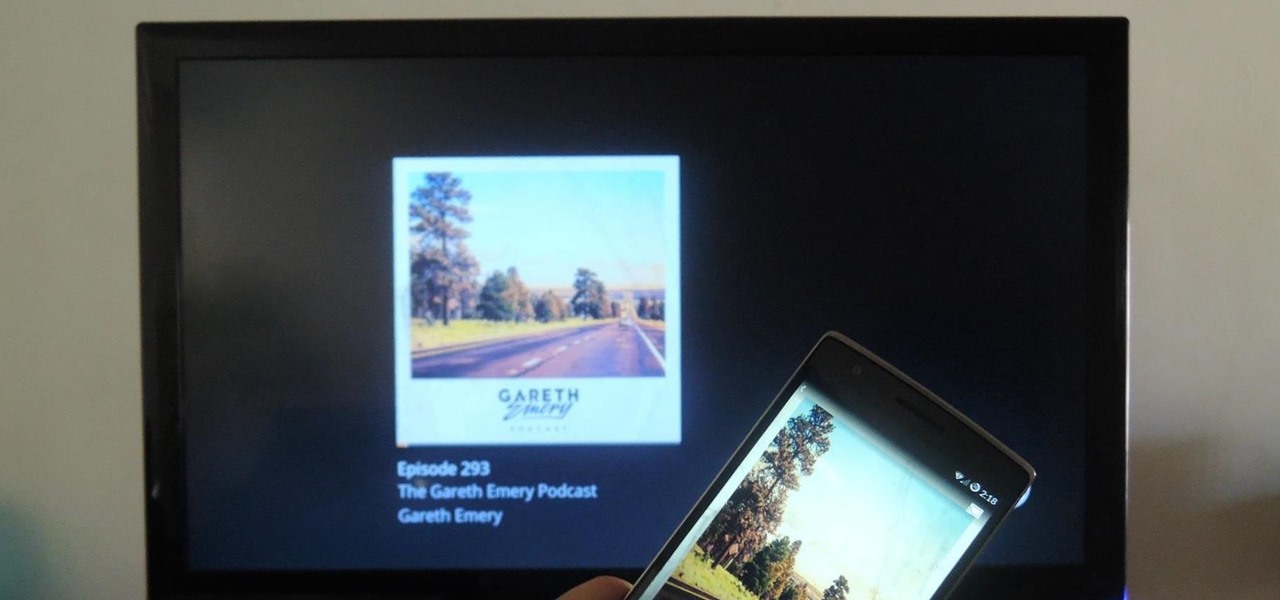
Podcasts have been around and popular for close to a decade now. For the uninitiated, podcasts are like radio shows that can be downloaded directly from the web and listened to on any device. Up until now, only paid apps allowed podcasts to be casted via Chromecast, but with the latest update to Xavier Guillemane's Podcast Addict, you can now do the same thing for free!

One of the most common complaints that people have about the Nexus 4 would have to be its intermittently poor Wi-Fi performance, a problem that for many, persists through the installation of updates and even custom ROMs.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

Included in Spotify's new darker, slimmed down redesign is a much needed My Music section, which consolidates all of your starred music, local files, and playlists into a personal collection of songs, albums, and artists, similar to how iTunes organizes your music. This makes me wonder...

Samsung's TouchWiz skin gets a lot of flak for its appearance, namely the garish colors on the quick settings toggles. The bright green on dark blue scheme is definitely an eyesore compared to the ones in stock Android, and even other manufacturer skins like HTC's Sense.

If you're looking into rooting your device yourself, you're going to need ADB and Fastboot on your computer.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

There are a lot of things your Samsung Galaxy Note 2 can do straight out of the box, but there's also a ton of things it can't, or simply could be better at. That's why most of us end up rooting—to enhance the mobile experience.

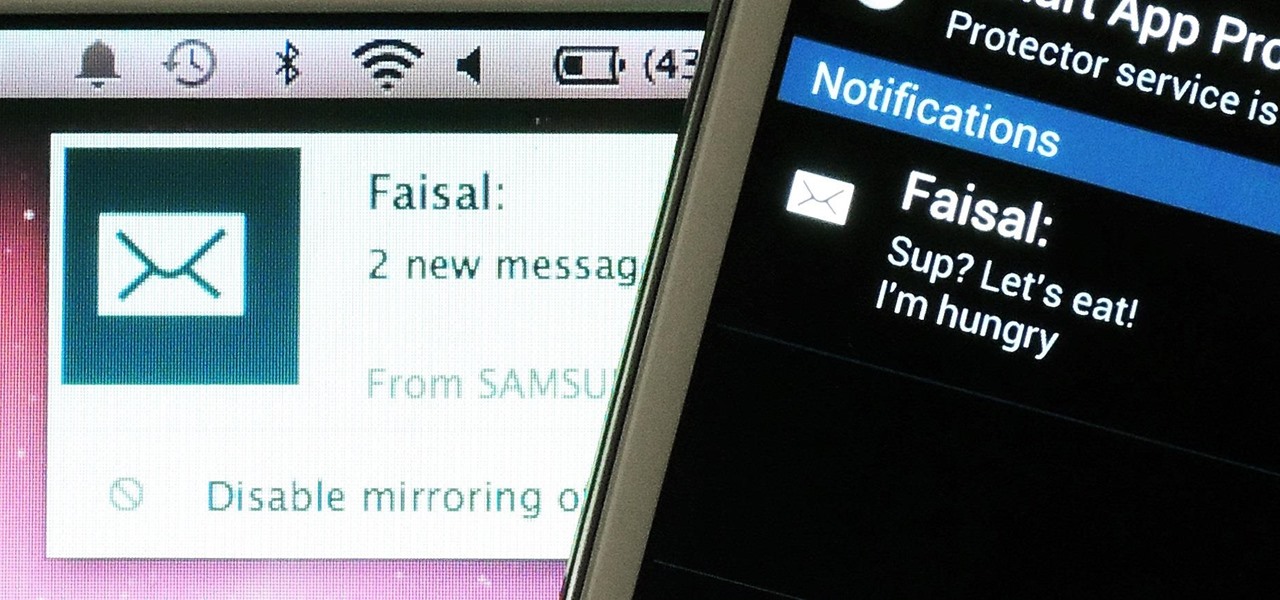
Having quick and immediate access to your notifications is one of the most important features for any modern day phone, but these alerts can be easily missed when your device isn't in the palm of your hand.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).