For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To keep that from happening, try downloading tracks from Apple Music for offline playback.

Like Marvel's Avengers, Facebook's Camera AR platform now has a number of new AR superpowers at its disposal, so it is fitting that Earth's Mightiest Heroes have the distinction of displaying them.

Although Magic Leap's founder Rony Abovitz has a lot to say about his product, what people really want are visuals, and it looks like we're about to get a lot more of those in the coming weeks. In a post on Magic Leap's official announcements forum page, the company revealed that it plans to begin a monthly livestream series on Twitch.
To help keep potential drama at bay, WhatsApp lets you delete questionable messages before the other person even sees them. If you're on the receiving end and you're curious about the deleted text, however, there's an Android app that lets you view erased messages.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

When Google first announced Android Oreo (Go edition), many believed these devices would be focused more on developing countries. However, thanks to ZTE, we'll be getting Android Go stateside, so US customers on even the tightest of budgets can still enjoy the convenience of a smartphone.

While the company is adamant that the Magic Leap One: Creator Edition will ship this year, currently, it seems its CEO is more interested in striking deals with content partners than releasing details about the headset.

Ever since Microsoft sold Nokia to HMD, they've hit the ground running with a new lease on life. Quick updates have become their hallmark, with even their lower-end phones getting Android Oreo in a timely fashion. The same holds true for their current flagship, the Nokia 8, which by our count is now the first phone outside of Pixel or Nexus devices to get Android 8.1.

While augmented reality headset makers are faced with tackling numerous challenges before the category is truly ready for prime time, a start-up comprised of former Microsoft engineers may have nailed fast and precise tracking of hand gestures and full-body locomotion.

On Sunday, the annual Grammy Awards delivered its usual mix of fashion, live performances, and music industry magic, but this time with one important difference: Animojis.

Snapchat is an app built on sending quick-to-disappear pictures to your friends and family. Sure, this is the primary function of the app, but sometimes users want longer-lasting Memories while interacting with Snapchat. While My Story allows snaps to stick around for 24 hours, they still disappear in time. This is where Memories come in handy.

We knew it was coming, it was just a matter of when. Apple has just announced iOS 11.3, a new update for iPad, iPhone, and iPod touch, and it will include a brand-new set of Animoji for the iPhone X.

Android users have had access to live wallpapers since the Eclair days, but some newer apps have made this feature even more useful. Now, you have the ability to use GIFs as your wallpaper, and through the marvels of modern technology, you can even set a video as your home screen and lock screen background.

Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just found.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

With just a few more days to go before its release in theaters, the Star Wars: The Last Jedi push has gone into overdrive. On Monday, Google released "The Last Jedi AR Stickers," a set of augmented reality stickers that lets users put a number of different Star Wars characters and objects into the real world.

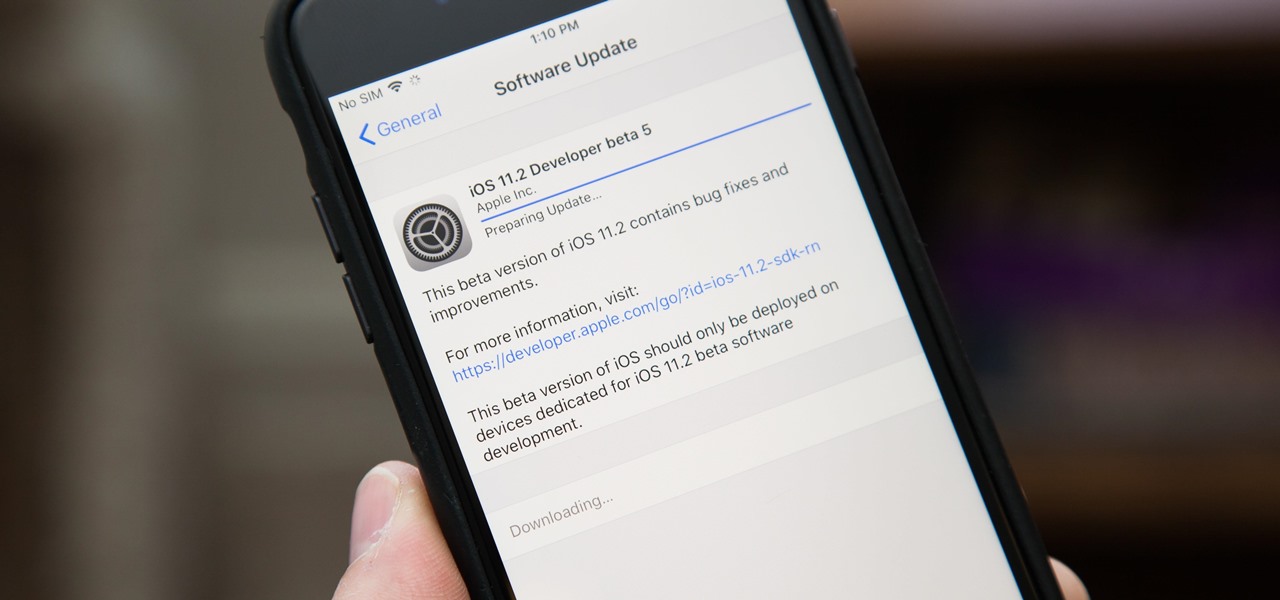
We're getting closer and closer to a final iOS 11.2 release for everyone. Apple just pushed out beta 5 for iOS 11.2 to developers and public testers on Tuesday, Nov. 28, and much like its predecessor from a few weeks ago, there's not much included but bug fixes and security patches.

The Essential Phone didn't have a hot start when it was released back in August. A delayed release, poor camera performance, and high price tag led many to avoid the otherwise well-received device. But after a few software updates and price drops, it's now a steal of a deal.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

Augmented reality is making many of our childhood dreams from Star Wars come true. A week after Lenovo gave us the ability to actually play Holochess, Apple has now made it possible to take live video of ourselves and layer on a (non-3D) hologram-like effect, closely resembling the famous Star Wars hologram scene featuring Princess Leia decades ago.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

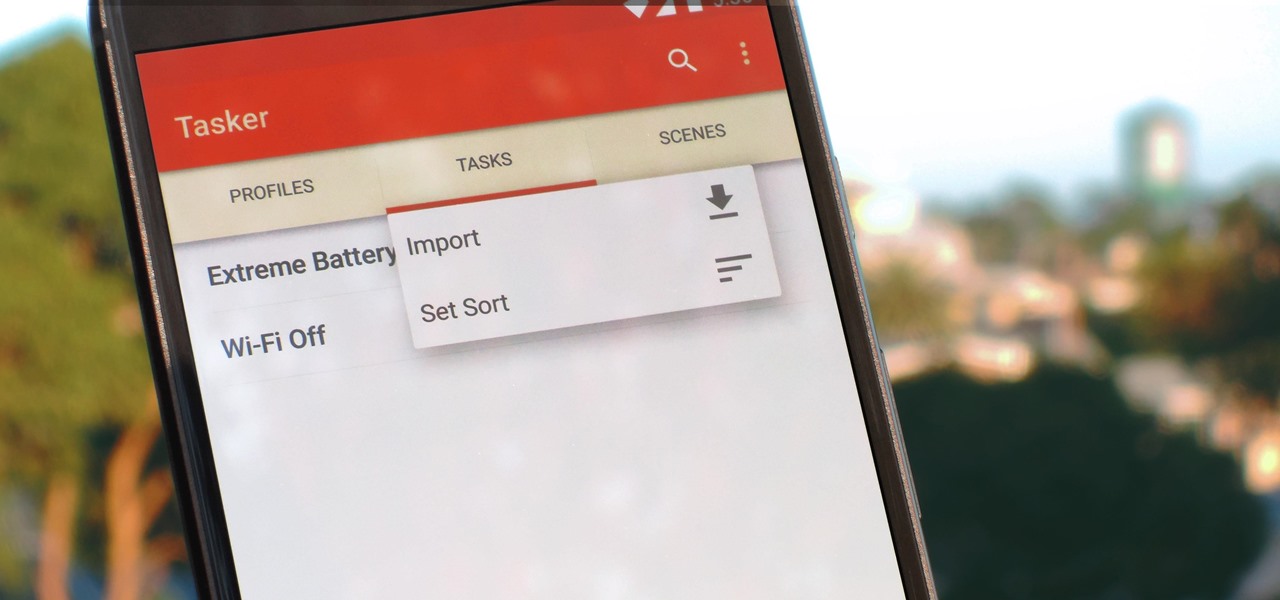
Regardless of what you're trying to accomplish with Tasker, there's a good chance that someone else has already walked through the same steps. If you're unfamiliar with creating tasks and working with profiles, simply importing someone else's work would be a great shortcut. After all, there are 2 billion Android devices out there, so someone must've created a setup that suits your needs, right?

Apple's iOS 11 release promises many improvements and fresh ideas. One of those new ideas is an image codec called HEIF (similar to HEVC for videos), designed to reduce the space photos take up on your iPhone. But it's so new that it's already causing issues with compatibility.

The new iPhone X will be released on Friday, Nov. 3, in Apple Stores located in over 55 countries and territories. For those of you who would rather skip the in-stores lines that will start building well before the 8 a.m. local time openings, you can preorder the iPhone X on Friday, Oct. 27, starting at 12:01 a.m. PDT.

Your display name in ProtonMail is what email recipients will see when they first receive your message in ProtonMail, Gmail, or another email provider. You can choose this name when you first set up your ProtonMail account, but it can also be set up after the fact if you skipped that step.

In most cases, when you create a movie project in iMovie for iPhone, you're starting with just a few media clips. There's no reason to select every photo or video at once, and that's likely a hard task anyway. Adding additional media footage to your movie project couldn't be any easier, especially when it comes to photos.

The developers at Immersion VR are clearly fans of both Apple's ARKit and Rick & Morty, as the company has shared its second demo in as many weeks of the augmented reality platform that is influenced by the animated sci-fi series.

The Xposed Framework is an incredibly powerful tool. But because of this power, there's a chance that something could go wrong when installing a broken or incompatible module, which can cause bootloops or even soft-brick your phone.

When it comes to watching movies and TV shows in Amazon's Prime Video service on an iPhone, it's as simple as installing the Amazon Prime Video app, signing into it, then playing content. However, on an Android phone, it's a lot more complicated.

5G is showing up more and more in the news, as an increasing number of companies jump on the bandwagon. AT&T made a splash earlier this year with their embarrassing "5G Evolution" debacle, and the other three major wireless carriers soon followed suit, detailing their own vague plans for 5G. Today we find another company has joined the fray, just not a cellular one — Apple has officially been approved to test 5G networks.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

The beta firmware for OnePlus devices lets you record calls from the stock Oxygen OS dialer, but this feature is never included in official updates. This is likely due to legal issues with recording calls in some jurisdictions, but thankfully, there's a way to get this feature without having to run beta software.

Researchers are putting driverless shuttles on campus next year at the University of Michigan and the rides are free for students and teachers.

Until recently, Firefox had the ability to continue playing YouTube videos in the background after minimizing the browser. It worked great as a YouTube Red alternative, but unfortunately, Mozilla removed this feature after some pushback from Google. Thankfully, there's a way to get it back.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

Jeep has now jumped on the AR-retail trend with their introduction of the Jeep Compass Visualizer. Customers can now view and customize a Jeep Compass to their liking, all without a real Jeep even present.