Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.
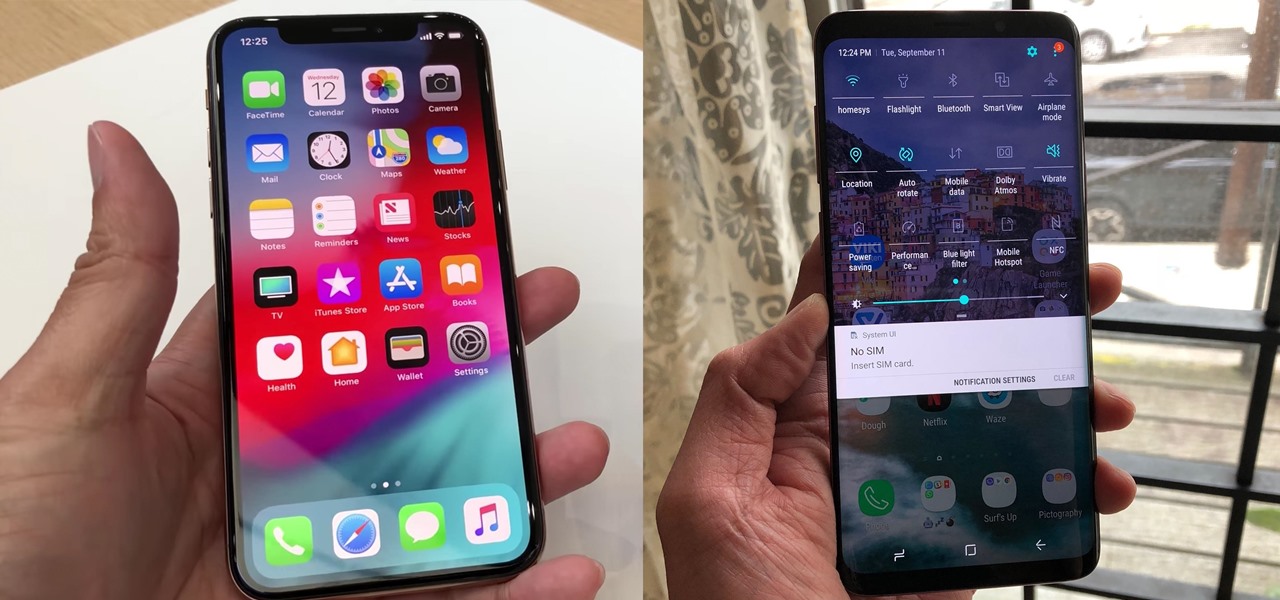
Until next March, the iPhone XS and Samsung Galaxy S9 will be the only phones considered by many. Whether you're an Apple fan wanting to see how your new phone stacks up against the competition or a buyer on the fence, here's how the latest flagships from the two biggest brands compare.
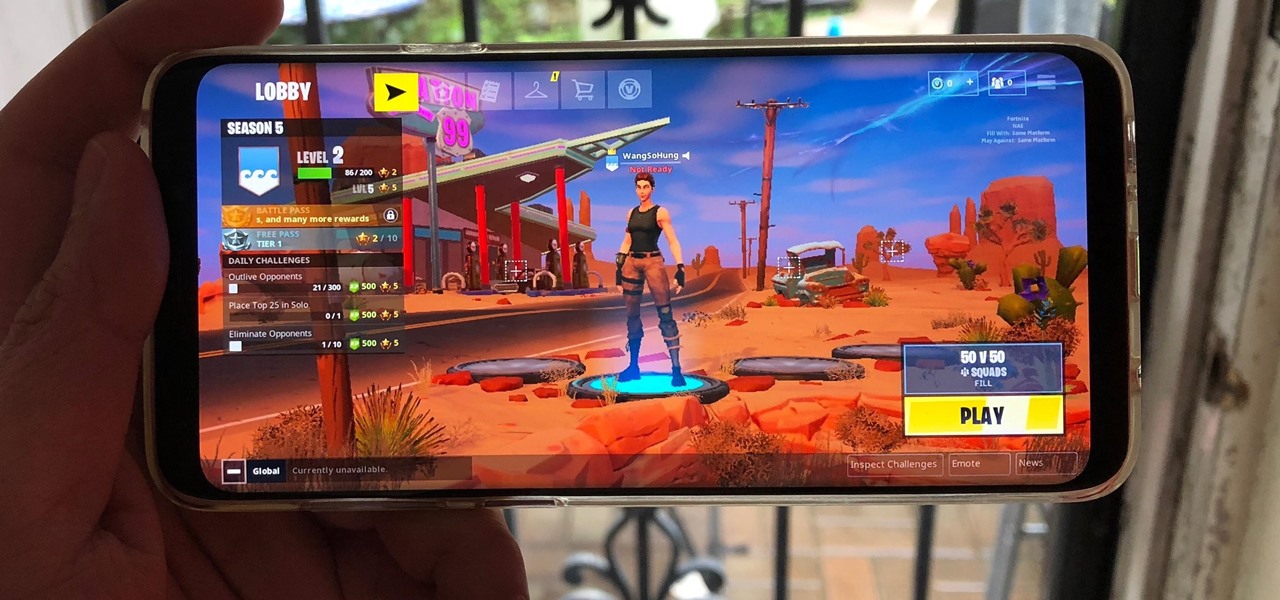
Fortnite's long awaited arrival on Android has ramped up excitement among gamers who are installing the beta version in astounding numbers. With so many midrange and budget devices running Android, however, it's important to stay on top of your device's performance to ensure smooth and uninterrupted gameplay.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.
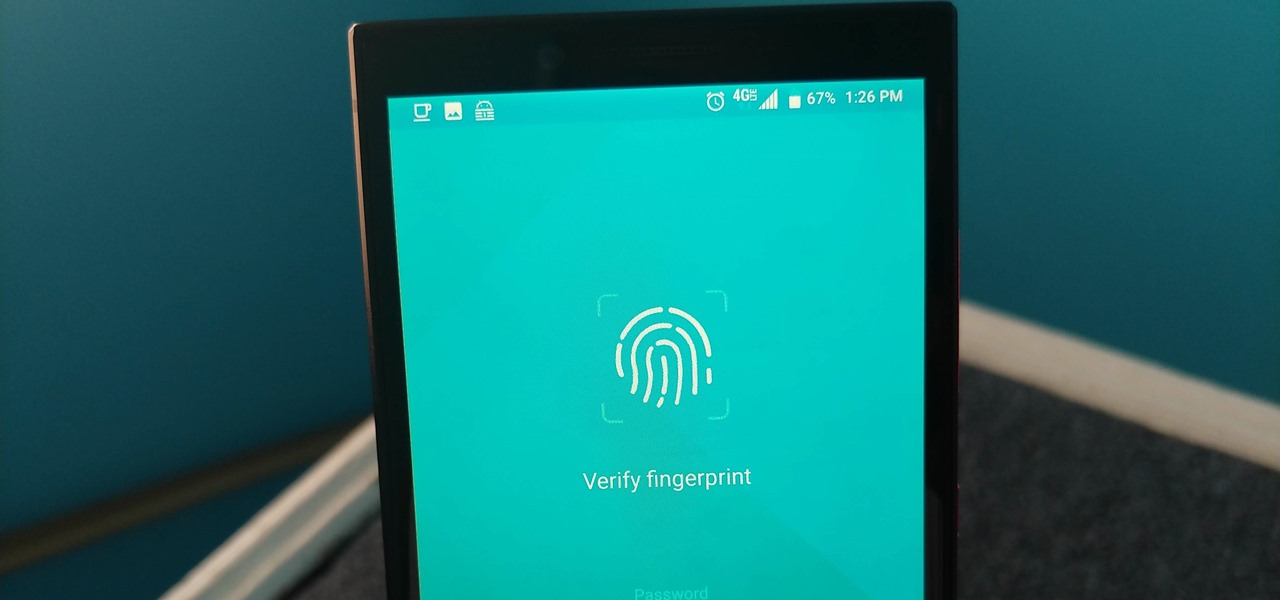
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

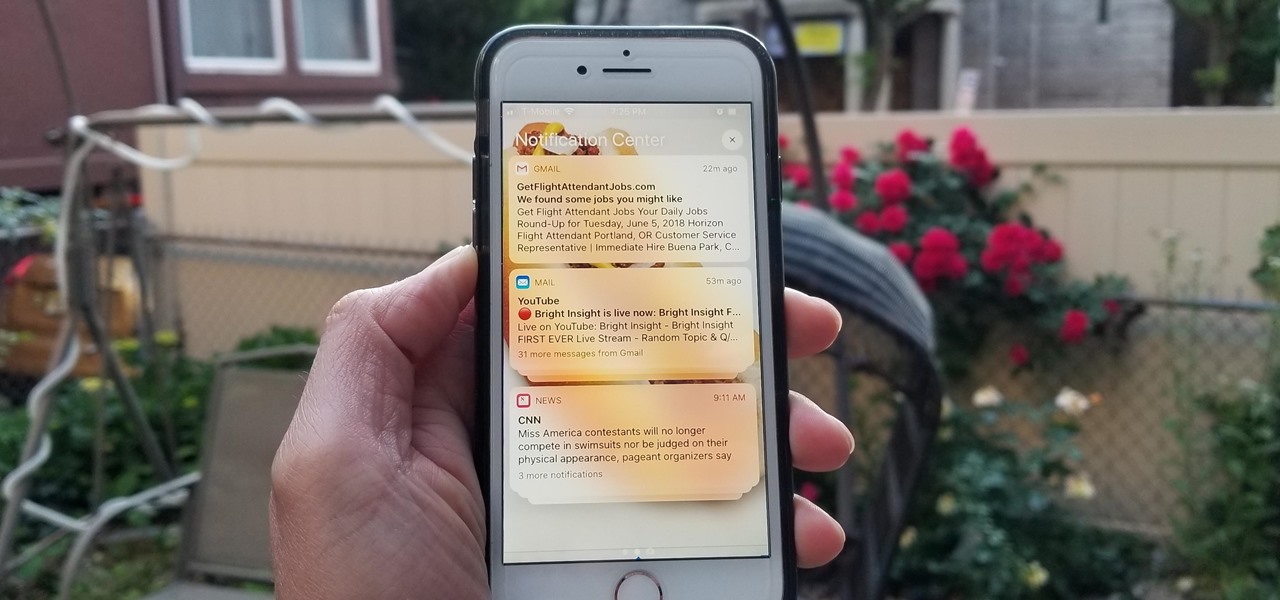
Apple's linear Notification Center has been scattershot at best since iOS 9 when we could group notifications by app. Without any type of grouping ability, the notification history becomes more of a nuisance of random alerts based on time alone, making it a treasure hunt to find the notification wanted. Now, iOS 12 has addressed this issue, bringing back groupings — with improvements.

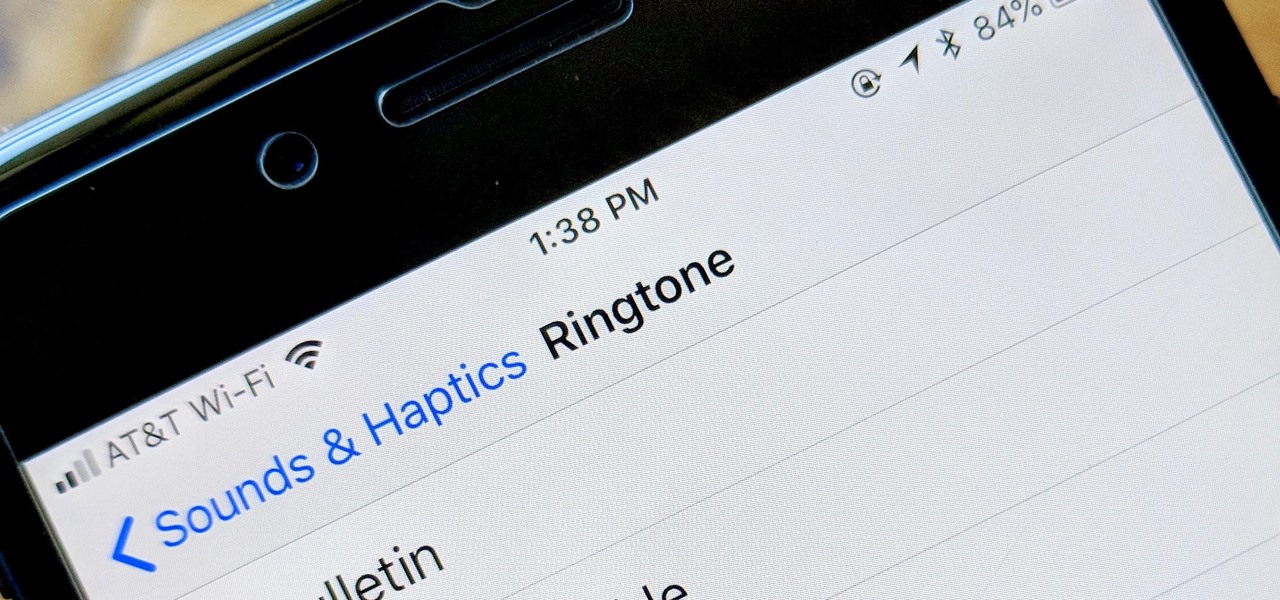
With the exception of "Reflection" on the iPhone X, Apple hasn't updated their catalog of ringtones and alarms since iOS 7 dropped back in 2013. Since then, the company has come a long way with the quality of the iPhone's speakers, but their tones haven't adapted to meet those changes. That's left an opening for others to create their own ringtones mastered for the iPhone.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

There are some nasty iOS bugs out there, many determined to crash the Messages app. For example, in February 2018, we saw a Telugu character render the iPhone messaging app totally useless. While that bug has been fixed, the nightmare continues in a new bug, aptly dubbed the "Black Dot."

Over the years, mobile gaming has become a phenomenon, rivaling in magnitude with its console and PC-based counterparts. We even have mobile versions of Fortnite and PUBG now, games that require lots of processing power to run. But when you just want a quick game to play in the grocery line or even on the toilet, try these simple, quick games that you can play right on your lock screen.

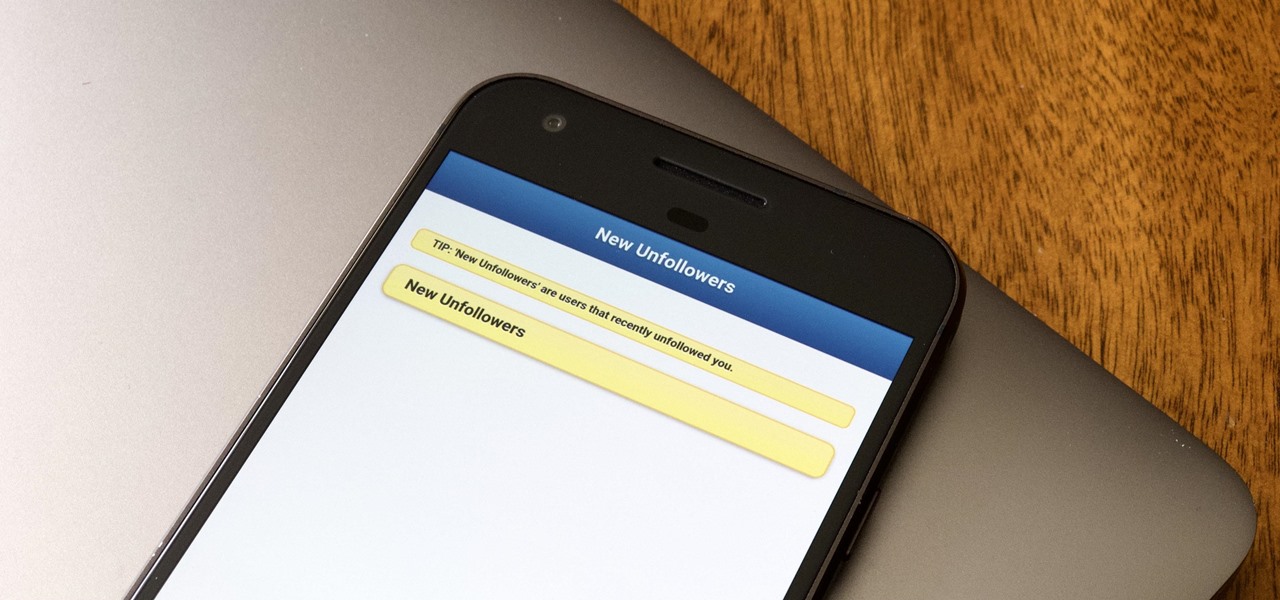
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

On Friday, audio giant Bose emerged as the latest, and perhaps the most surprising company to announce that it's planning to release augmented reality smartglasses.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

During Mobile World Congress 2018, OEMs started to introduce the world to Android Oreo (Go edition). Android Go offers smooth performance on entry-level specs, allowing for genuinely good cheap phones. At first, the US only had one Android Go device, but it looks like a second will join in the near future, the Nokia 1.

Last year, OnePlus released not one but two excellent flagship devices with the OnePlus 5 and 5T. While the 5T released sooner than expected, it brought some worthwhile upgrades, such as a near bezel-less display and a much-needed camera enhancement. Now, that the OnePlus 6 has arrived, it's time to see what OnePlus has in store for 2018.

HMD (the company currently making Nokia-branded phones) only released one flagship device last year, with the rest of the phones falling in the mid-range and entry-level tiers. However, at Mobile World Congress 2018, HMD announced their ambition to become a top five smartphone maker in 3–5 years. Meeting this goal will require penetration in all markets — especially the United States — and it looks like Nokia will get the ball rolling early this year.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

Coming into this year's Consumer Electronics Show (CES), the common sentiment among observers was that this was expected to be the big year for augmented reality.

It's been nearly two months since Samsung kicked off the official Galaxy S8 beta program for Android Oreo. The Korean manufacturer recently announced that the beta is ending on January 15, so it's time to move on to the official build. Today, an official (non-beta) build of Oreo for the S8 has leaked.

So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

Snapchat is mostly credited as the first AR social network, and, like most social media companies, its revenue model is nested largely within advertising. As such, the company now has a new avenue for branded content.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

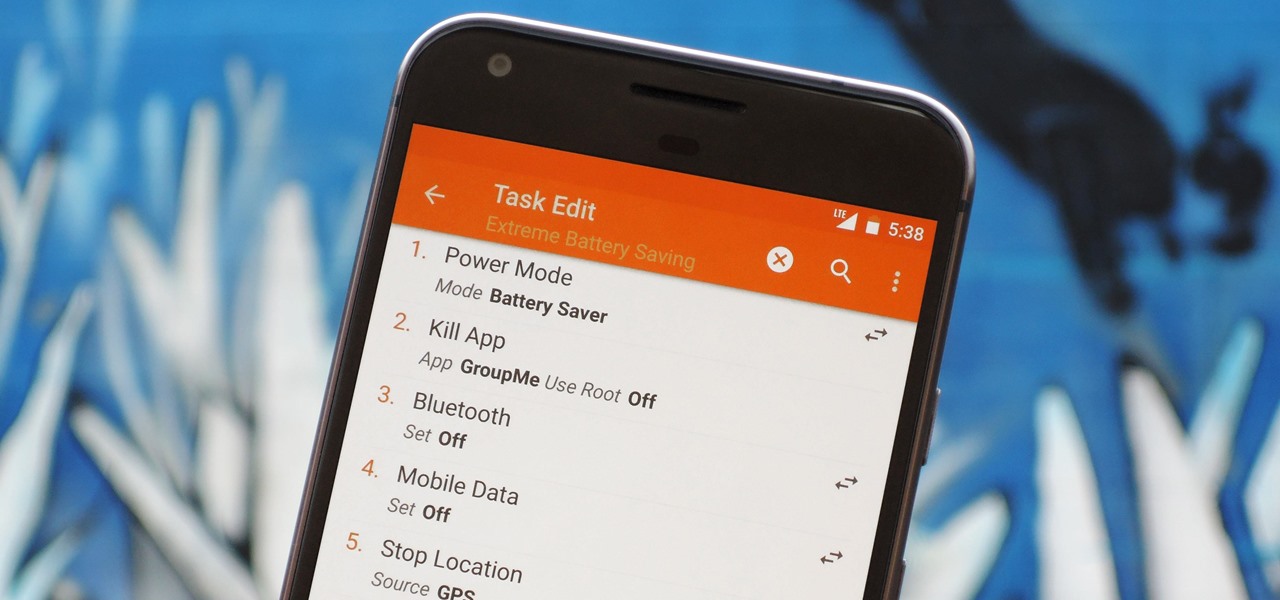
There are two core components to any Tasker automation: A profile and a task. Profiles are basically a set of conditions that must be met before Tasker will do anything. Tasks, on the other hand, are the actions Tasker will perform when your profile's conditions have been met. Think of them like triggers and actions, respectively. Or a cause and an effect.

One of the least important but most noticeable changes in any iOS update is the look of home screen icons. In the new iOS 11, there aren't any drastic icon differences compared to iOS 10, but there's definitely a few design modifications for some of the main stock apps, such as Maps and the App Store.

There are a few different ways to install Magisk. If you're already rooted and you just want access to Magisk modules, you can use Magisk Manager to install the Magisk framework. Or, if you want to pass SafetyNet on a rooted device, you can switch from SuperSU to Magisk SU. But the best way to do it is to start fresh by installing Magisk on a non-rooted phone using TWRP.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

When you think about preparing for an internship, I'm sure your first thought is to go shopping for professional outfits or to brush up on technical skills. While that's all important, there's so much more for you to think about.

Full disclosure — I have almost zero Street Fighter experience. The first time I played the game was at Barcade, way back in ... 2017. Yes, to the shame of gamers everywhere, this reviewer is a Street Fighter noob.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

I don't know how I feel about this. On the one hand, Futurama: Worlds of Tomorrow has charm. The original writers are attached to this project, and that shows in the humorous dialogue between characters.

Deadly rat lungworm parasites have found their way into Florida. The parasitic worm relies on snails and rats to complete its life cycle, but don't let this nematode's name fool you. This worm can cause meningitis and death in humans who inadvertently consume snails, frogs, or crustaceans harboring the infective parasite.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

While you may not notice them at first, iOS 11 included some pretty significant improvements to the Photos app on your iPhone. These upgrades will help you make your Live Photos livelier, surprise you with photos you totally forgot about, keep your photos and videos organized, and more.