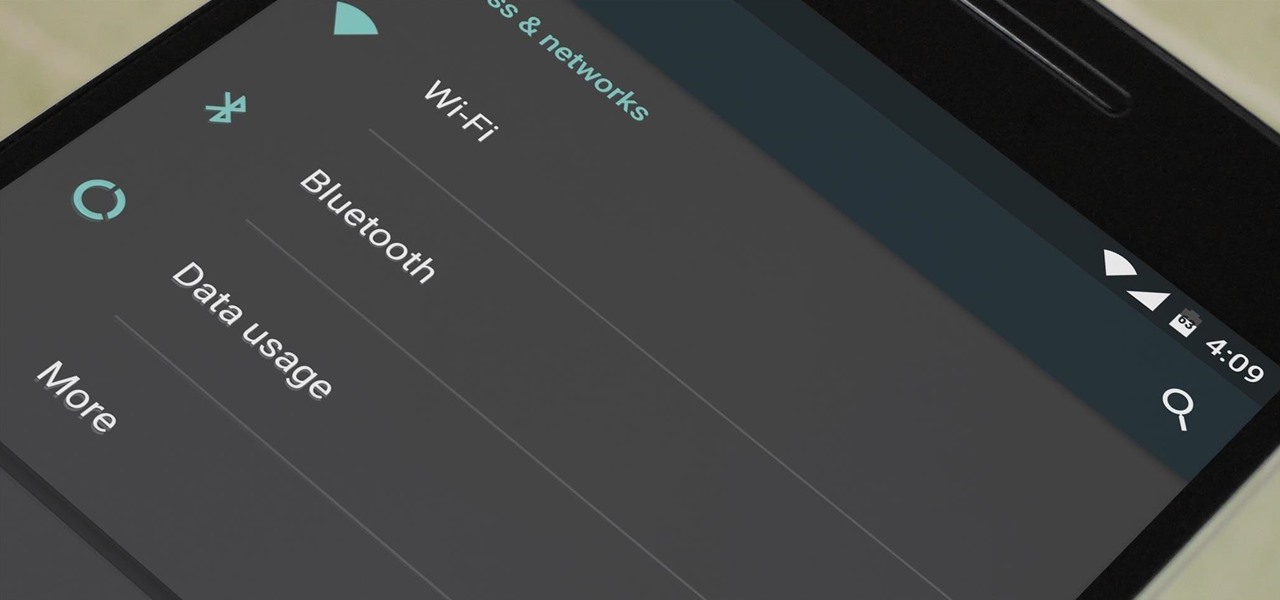
Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

The spice selection at Trader Joe's is both inexpensive and truly top-notch. According to their site, they deal with some of the highest-quality spice manufacturers in the world and, in working with them directly, they eliminate hidden costs spent on promotions, brand-building, and advertising. This allows the customer to experiment with new flavors and build up their spice rack—without the usual limiting factor of high cost. If you don't have access to a Trader's in your culinary neck of the...

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

Google's YouTube Red is an awesome service, particularly in the United States where it comes bundled with a subscription to Google Play Music. You don't have to worry about ever seeing ads again on any videos, you can continue playback after you exit the YouTube app or even when you turn your screen off, you can download videos for offline playback, and you'll have access to YouTube Music.

New technologies in current-generations smartphones allow for much faster charging—Qualcomm Quick Charge 3.0, VOOC Flash Charge, and USB Type-C, for instance, can charge a phone up to 4 times faster than traditional methods. However, the majority of phones on the market still don't support these standards. So for the rest of us, I'll go over an easy tip that can charge any smartphone as much as 25% faster.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

For years, users have been clamoring for a "dark mode" theme in Android, but it has always seemed like Google is so committed to the white motif from their web services that such an option would never become a reality. But in a stunning turn of events, Google is finally embracing the idea with a night theme that will work in any app, and I'll cover all of the specifics below.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

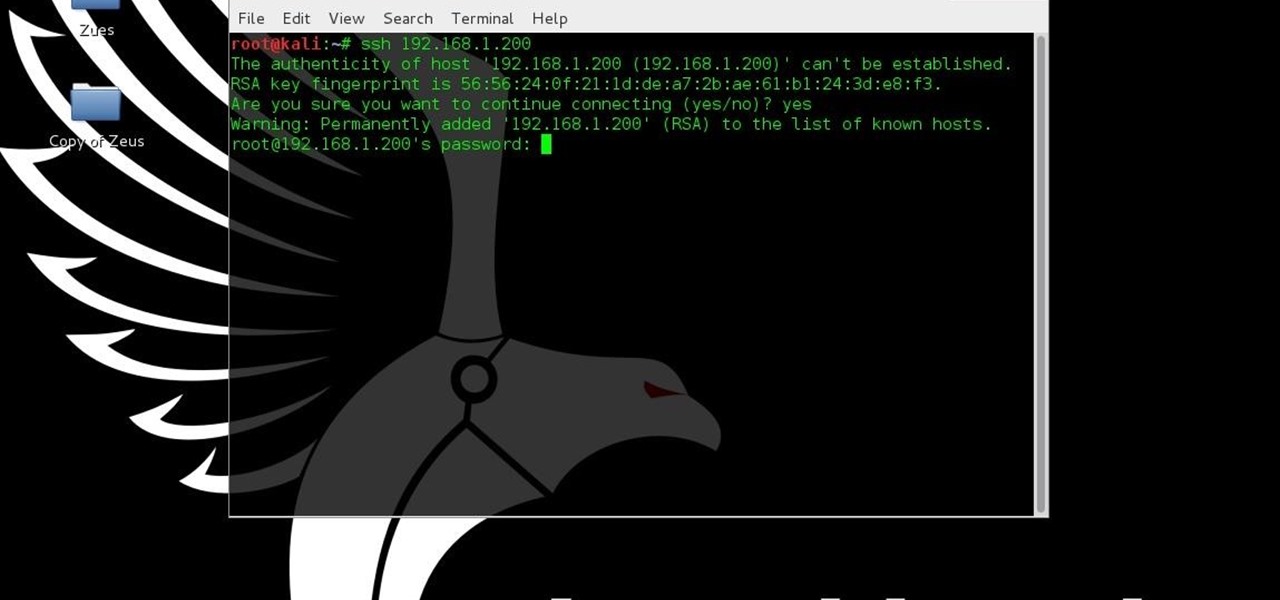
Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Ever since developer bponury created his TouchControl app for the Galaxy Nexus back in 2011, manufacturers and modders alike have been racing to re-implement the "Double-tap-to-wake" functionality it brought to the table. We've seen LG do it with their "Knock On" feature, we've seen Motorola put a twist on it with "Active Display," and we've even seen Google implement the feature in their Nexus 9 tablet.

Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" there are a few likely causes—and we've got you covered with troubleshooting tips and simple fixes below.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Android's copy/paste menu and text selection options have traditionally been downright terrible, but things are starting to get better with some recent improvements made in Marshmallow. That being said, there's still a lot left to be desired, and there's always plenty of room for more useful functionality.

Unless you like boxed wine, your wine bottles are going to either be sealed with a cork or a screw cap, the latter of which should not be frowned upon, especially if it's white wine. However, most wineries still prefer corks over screw caps, and that means you'll need a corkscrew.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

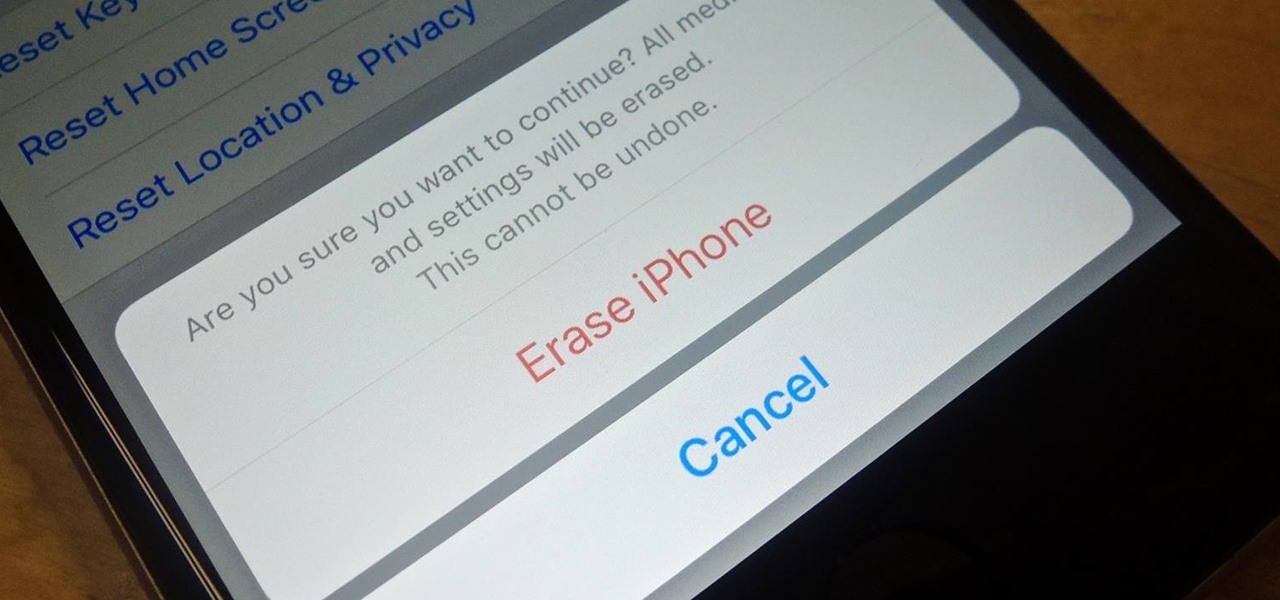
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

The 2015 LA Auto Show showcases the best of the auto industry—well, at least according to car companies. Increases in horsepower, better fuel economy, and most importantly—the latest tech—is all on display during the 10-day event in Southern California. Once of my first missions at the show was to figure out who is putting the most care and thought into in-cabin electronics, mainly the ones that guide us around and play our music, affectionately known as "infotainment."

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Fall is a time of change. The leaves change color, the weather changes from warm to cool, and we change our clocks to fall back an hour. This last change means that many of us will get home from work in pitch-black darkness; for me, the early onset of night makes me less interested in cooking dinner and more interested in getting in my sweats, throwing leftovers in the microwave, and binge-watching The Affair.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

While it seemed like jailbreaking methods were always one update behind the current build, the team over at Pangu have already released a jailbreak tool for iOS 9, and it works up to iOS 9.0.2. It is not available for iOS 9.1 through 9.2 yet, but we will update this guide when they are ready.

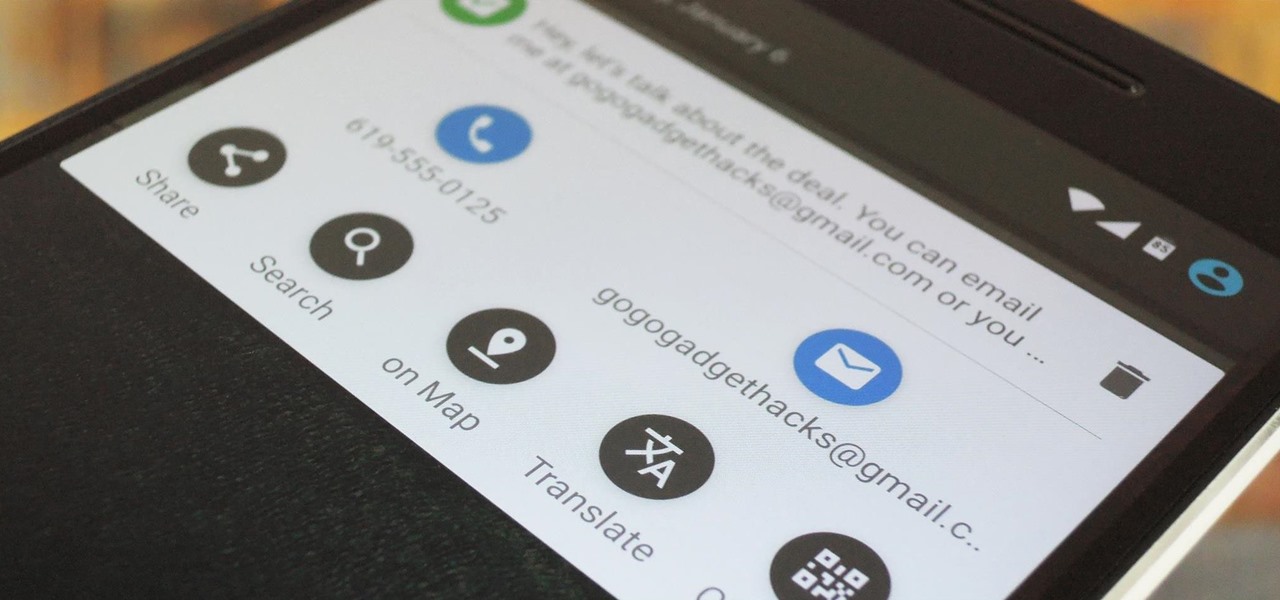
If you're entirely new to smartphones, Android's share menu can seem like a foreign concept at first glance. In reality, it's one of Android's most central and unique features, and with a little experience, it can make your smartphone a lot easier to use.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you could use to capture the issue you're having, then share the screenshot with your tech support.

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

There are many reasons to keep adult websites off your iOS device. They can pop up accidentally at the least opportune moments, can give your device malware, and are not welcome in a kid-friendly home.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

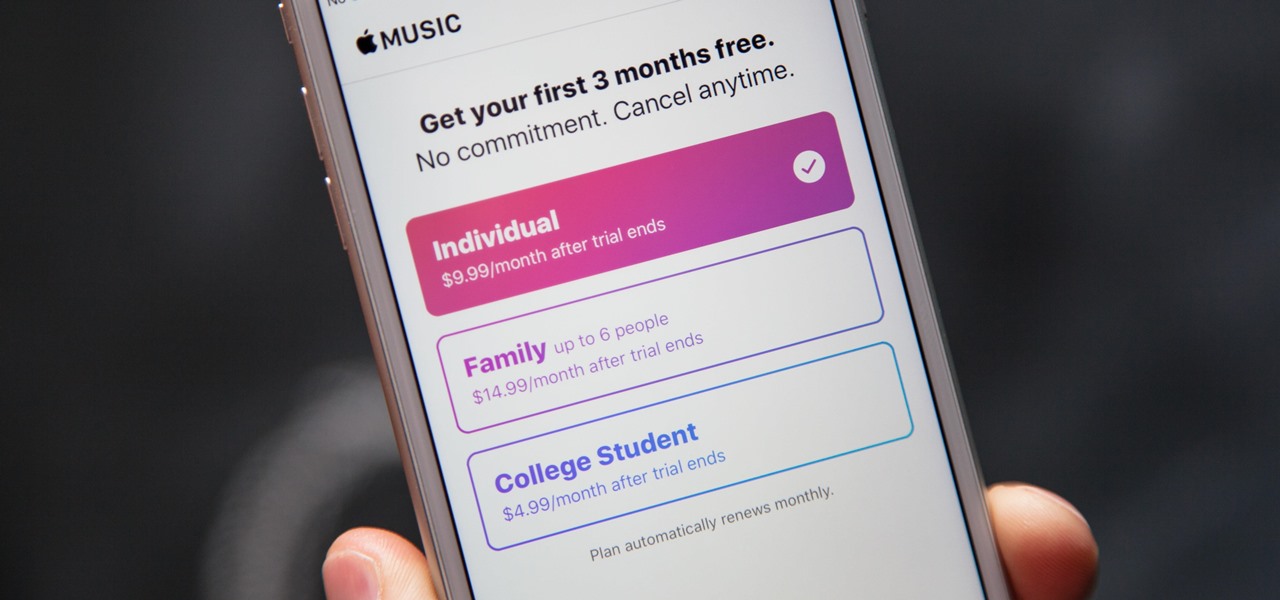
Apple's streaming music service, Apple Music, offers a three-month free trial that hopes to get you addicted enough to pay for a monthly subscription. You may even see a one-month trial if you're a former subscriber. While it's not very obvious, there is a way to cancel either free trial from auto-renewing. That way, you don't have to deal with Apple support to try and get your money back because you forgot.