Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.
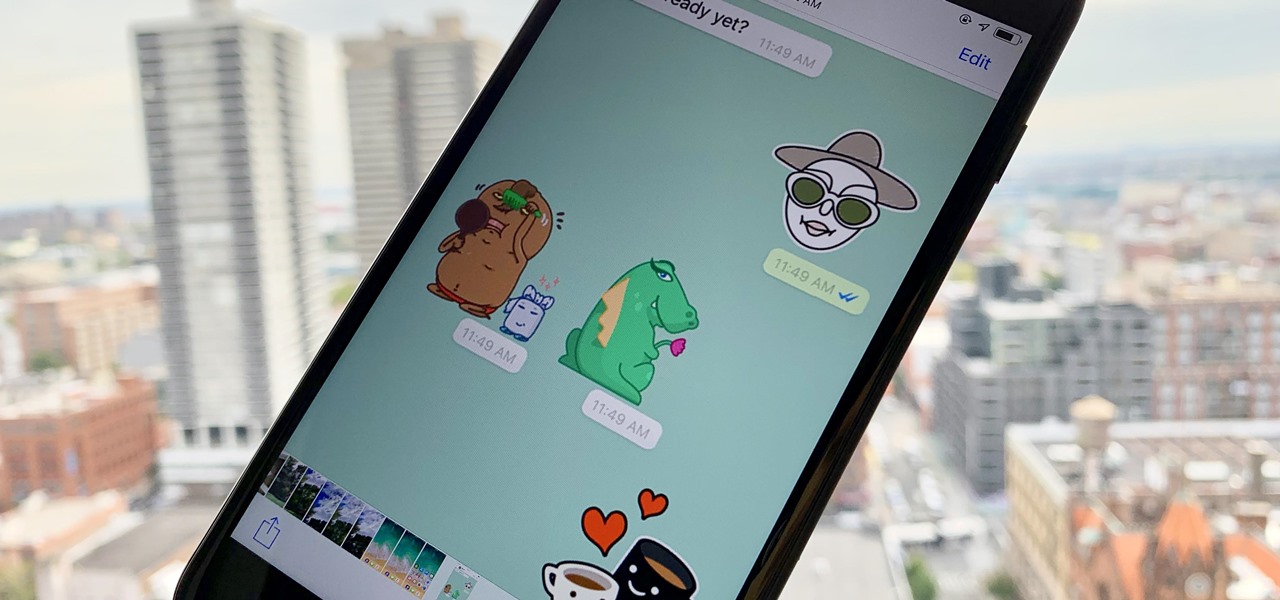
Stickers are a staple in most messaging apps. Facebook Messenger and Apple Messages, among others, are all compatible with still or animated stickers to personalize your chats. Now, WhatsApp is stepping into the sticker arena with a new update, bringing the popular feature to one of the most used chat apps in the world.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

Snapchat is joining the ranks of Netflix, Hulu, Amazon, YouTube, and Apple in the trend toward streaming original programming, but with a twist that rings true to its roots.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

The Daily Prophet, the enchanted newspaper from Harry Potter lore, is no longer the sole source for magical moving printed photos.

Augmented reality experiences for consumers, for the most part, are relegated to mobile devices at present, but creation and development of those experiences is still a province of desktop computers.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Earlier this year, Samsung released the Galaxy J3 and J7 to select markets. These two devices are the latest in the J series, Samsung's super-budget series that tries to rewrite what it means to be a budget phone. Now, starting September 14th, you will be able to get them GSM unlocked.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

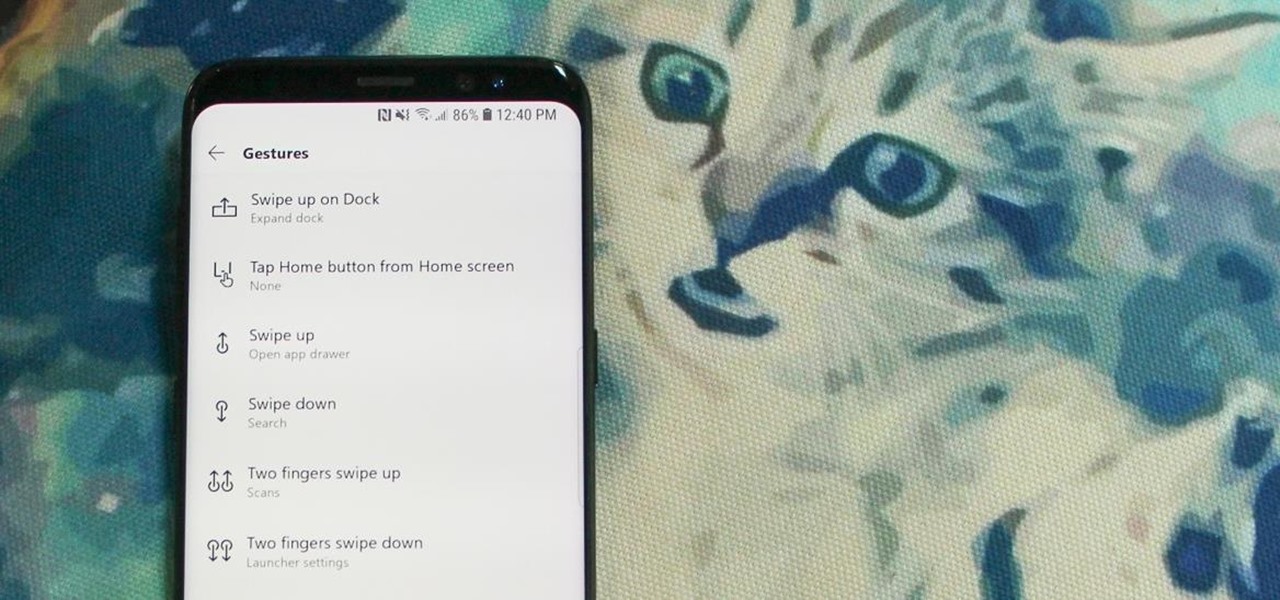
Ever-shrinking bezels and disappearing hardware buttons make for good looking phones, but they also increase the need for gesture controls. Android Pie comes with seven new swipe gestures, but if you don't have the update yet (or find its default gesture options to be lacking), you should take a look at the Microsoft Launcher.

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

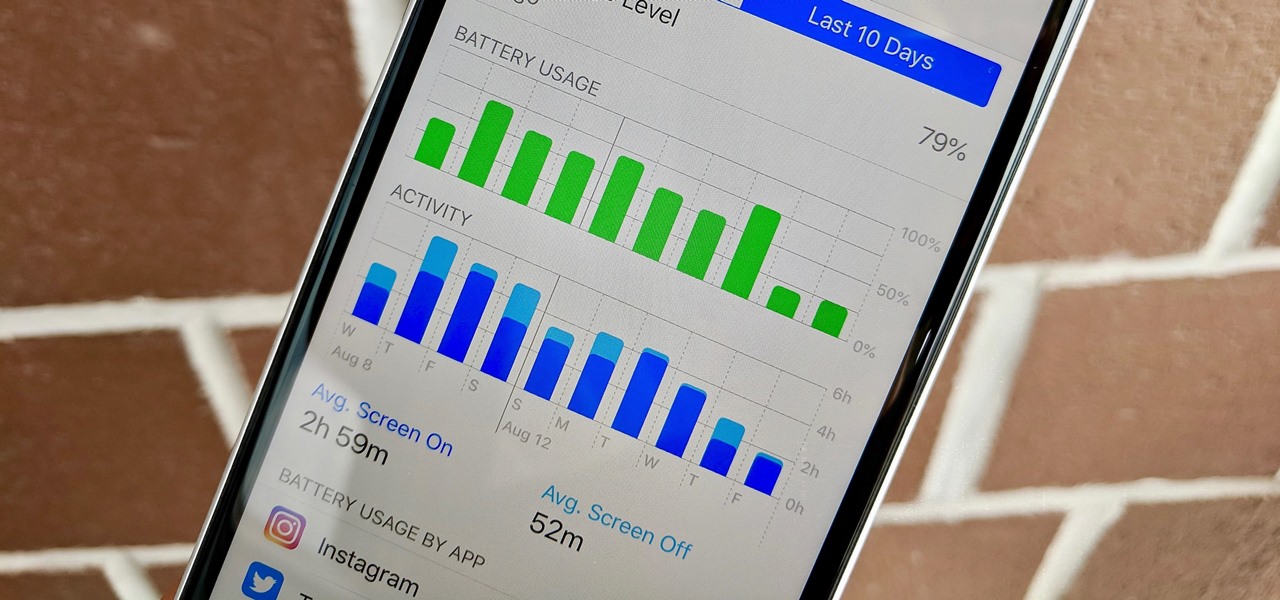
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

For those of us who love to multitask, picture-in-picture mode is a godsend. The feature, introduced in Android 8.0 Oreo, lets you enjoy videos in a floating window overlaid on top of another app. However, while the OS does have native support, only a select number of apps support the feature.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

The availability of space for filming immersive content has just gotten bigger with the launch of Innovation Studios by Sony Pictures Entertainment.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

Using the ARKit 2.0 announcement as its springboard, software maker Adobe is looking leap up to the level of Unity Technologies and Epic Games, the companies making the go-to tools for creating augmented reality experiences.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.

Soon, you'll be able to buy your OnePlus 6, but you can experience some of its apps today thanks to XDA user erayrafet, who ripped a few OxygenOS apps like Weather and this Gallery app. While Google Photos is a great service, this Gallery app should be your go-to app for locally-stored photos.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

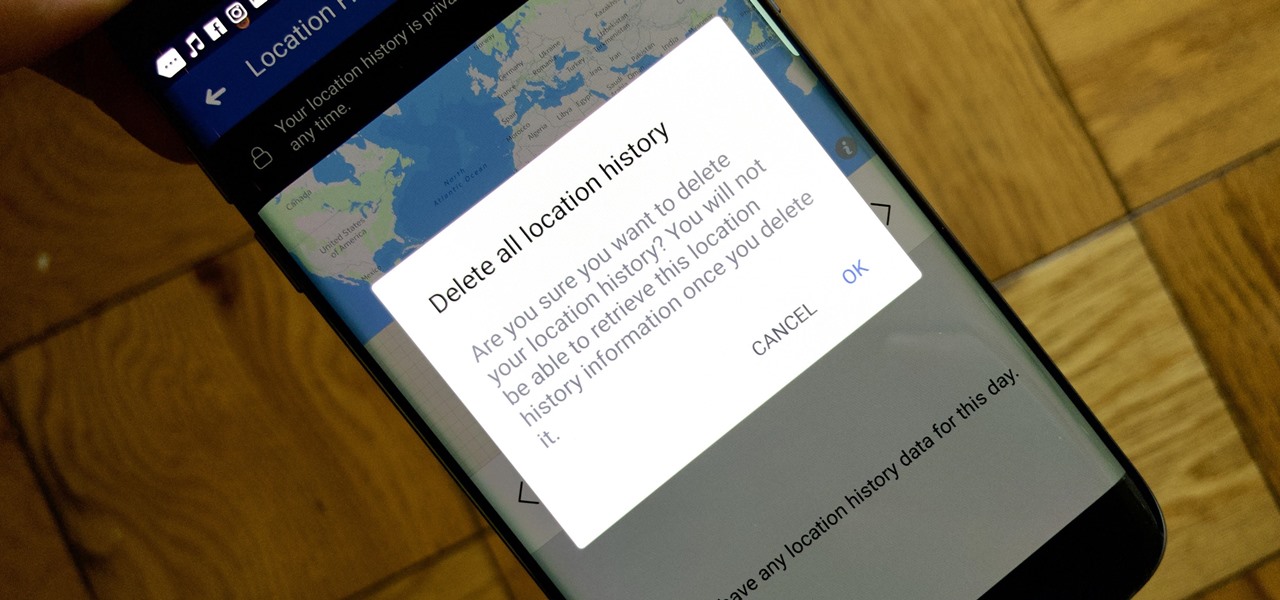
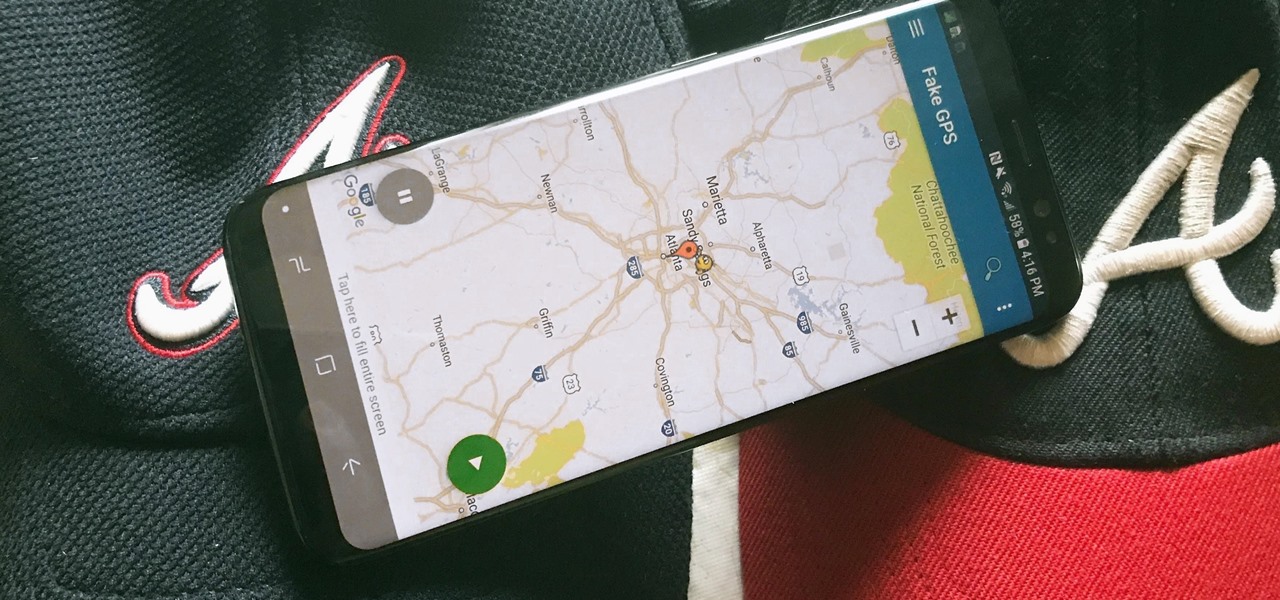
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

The price tag for the Microsoft HoloLens might be out of range for the average consumer's budget, but for enterprises, like BAE Systems, adopting the AR headset is yielding a return on the investment. And for those with even slimmer wallets, Best Buy just made the Lenovo Mirage, part of the Star Wars: Jedi Challenges package, more affordable.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

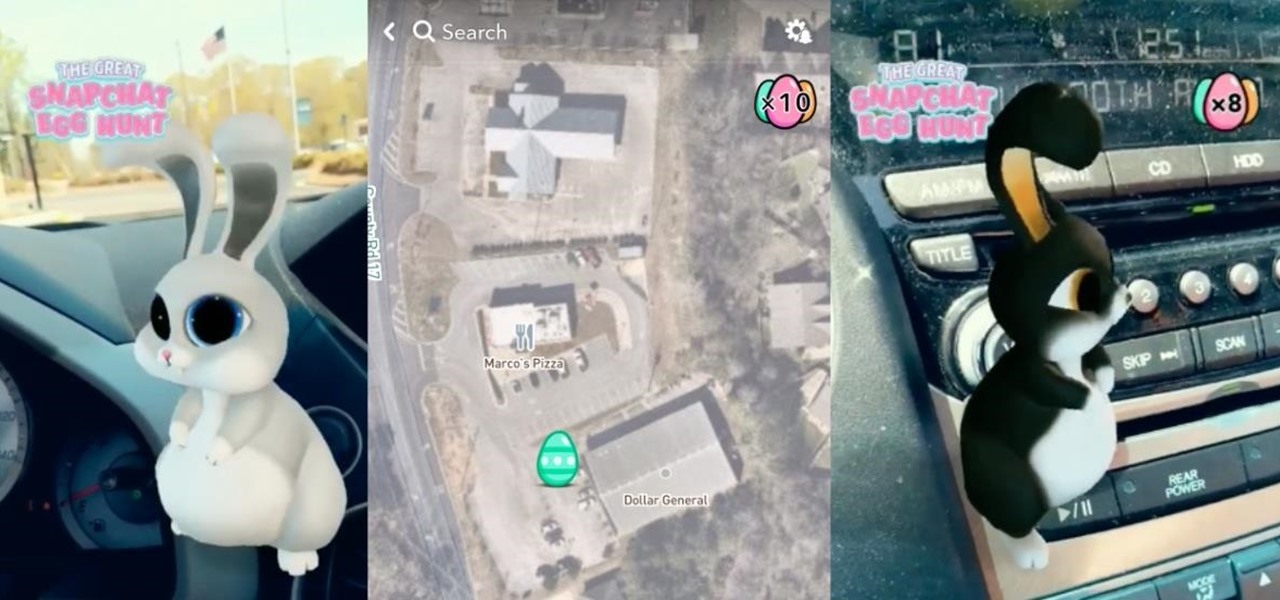
Alongside the usual collection of holiday-themed Lenses, Snapchatters received an extra-special treat from Snapchat over the weekend—a world-spanning Easter egg hunt.

With the recent launch of the developer preview for Android 9.0 Pie, many are clamoring to get their hands on some of the new features. Unfortunately for most Android users, Android Pie will not arrive on their device until 2019. The good news is you can add one of Android Pie's biggest UI changes to your phone today with a simple app.

MLB.TV is a great service that lets you watch most Major League Baseball games in North America, as long as you're a subscriber, of course. While I personally love it, blackouts can ruin the ability to watch my favorite teams. Fortunately, MLB At Bat Android users have an easy way to bypass blackout restrictions — and with no root required.

While Instagram users can attach links to images, they can only do so in stories, and only if they meet the special requirements that most users cannot obtain. Snapchat, on the other hand, lets anyone add a link, and it can be done in regular snaps and in your story. This feature has only been around since July 2017, so you may have missed it and not even realized it was a possibility.

There are few apps or services better than Slack for keeping a team both communicative and productive. But it also makes it difficult to escape your job — after work hours and weekends should be yours, not Slack's. If you want to stop the barrage of notifications and messages on your time off, you should make use of Slack's "Do Not Disturb" and "Away" settings.

If you're on a limited data plan, you no doubt set Google Photos to only back up over Wi-Fi on your Android device. In recent months, however, there have been many complaints that Photos won't actually back up your pictures when you get back home and connect to your network. Thankfully, the fix is fairly simple.

Before the Sept. 2017 event held by Apple, we thought the new iPhone X would come in three different colors. While only a Space Gray and Silver option made it to the Nov. 2017 release, the missing third hue may finally be on its way, if the latest rumors are to be believed. If you can't wait for the new Blush Gold color, here's when and how you can expect to get your hands on one.

If you want to play a game in the Play Store before committing to actually downloading and installing it, you can do that with Google's Android Instant Apps technology. However, if you don't see a "Try Now" button on the app's Play Store page, you'll need to check your Android device's settings to make sure you can play games instantly.

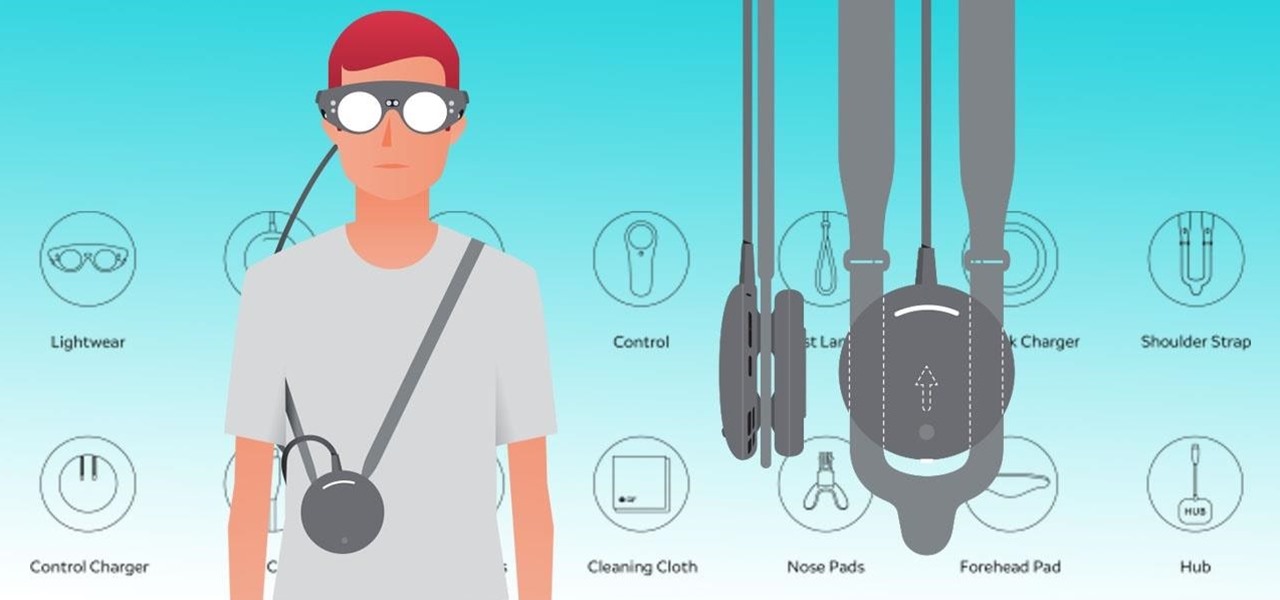
Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.