As the Insider Preview builds of Windows 10 progressed, certain features were removed as new ones joined the fray. Some came back, while others disappeared, seemingly for good. One feature that seems to have been removed are the colored title bars on app windows.

These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time installation fee, and even games that start at 99 cents, but quickly skyrocket in price with in-app purchases.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

Whether you are protecting your children or hiding personal information, there are ways to block unwanted websites from your computer. Follow this tutorial and learn how to accomplish this on a Windows PC easily.

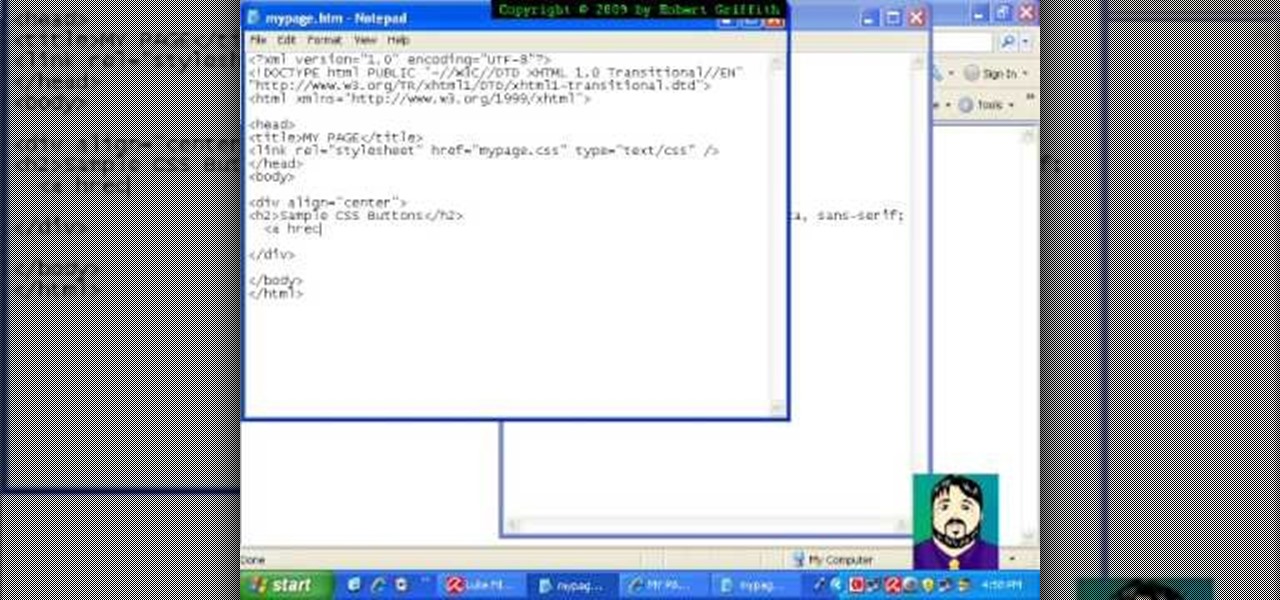
In this tutorial freetutorials teaches you how to create navigation style buttons using cascading style sheets, or CSS, in this the first in his series of "HTML Tips & Tricks". As you follow along, you will be shown how to setup and link your cascading style sheet to your HTML document, and where to place it in the document. Once you have done that, he will show you how to create a CSS, add a body and code the buttons in the CSS using notepad.

Are you tired of having a bunch of files on your computer that you cannot get rid of? Find out how to use Windows notepad to remove unwanted files from your pc.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

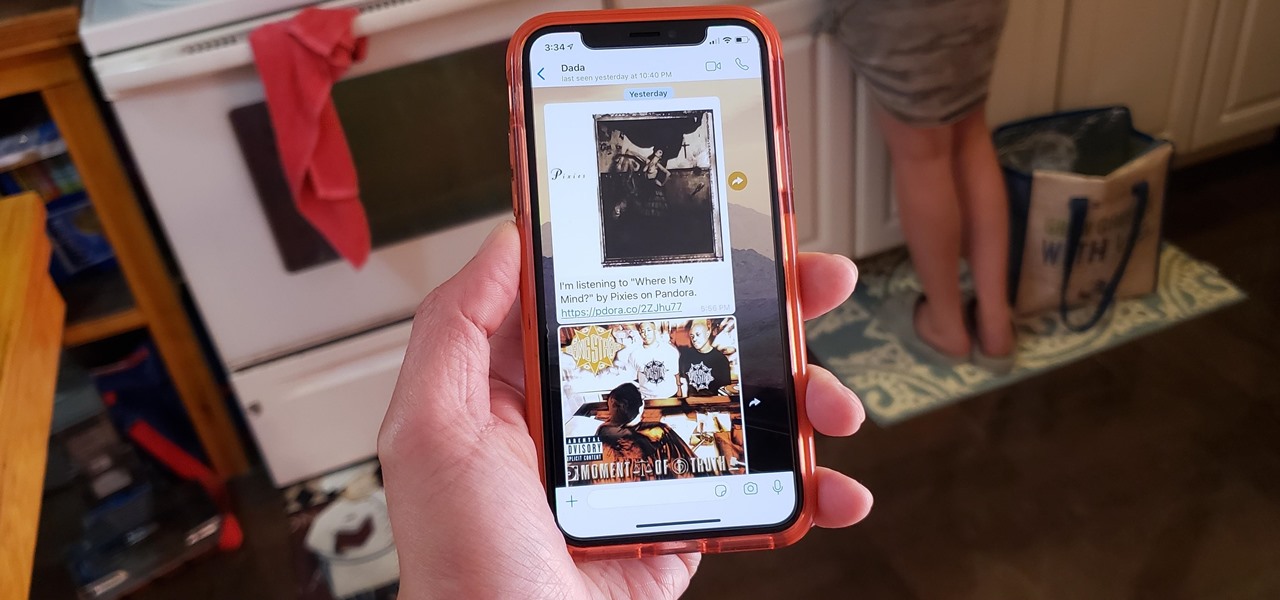
One of the best parts of Pandora is its personalized stations that auto-generate songs within the specific style or genre you've chosen. Not only does this play your favorite tracks with regularity, but it also opens your ears to previously unknown songs or artists — ones you may fall in love with and want to share with others.

Step 1: Introduction: Hello! Hackers

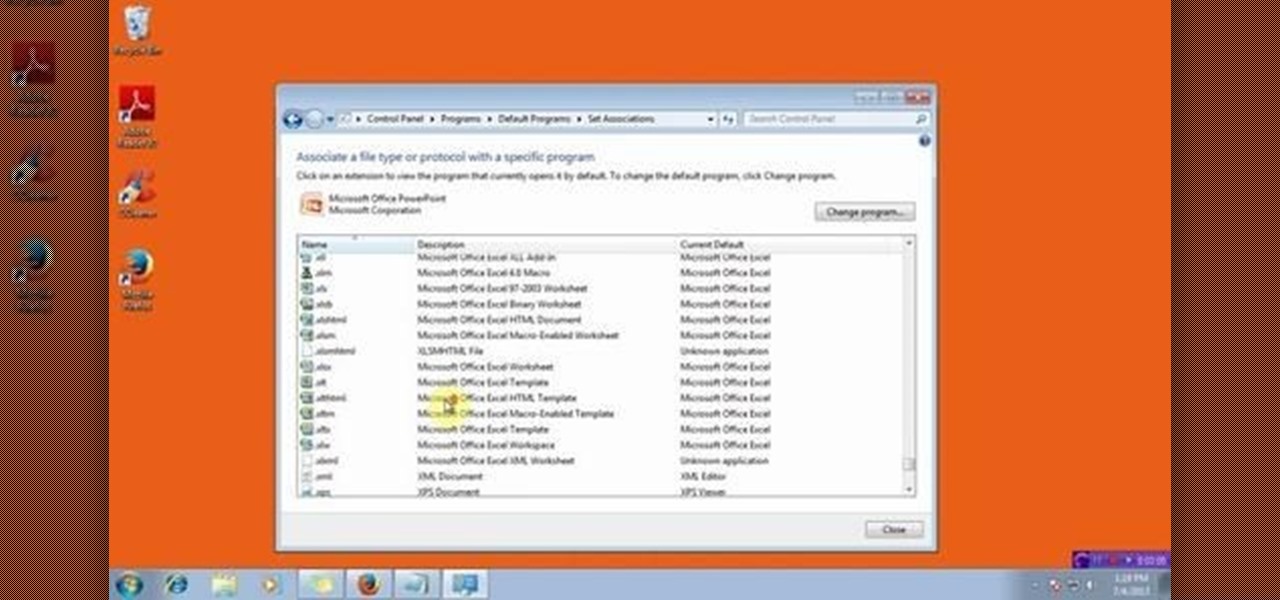
This video will show you how to change the default program for a Specific File Extension in Windows 7.

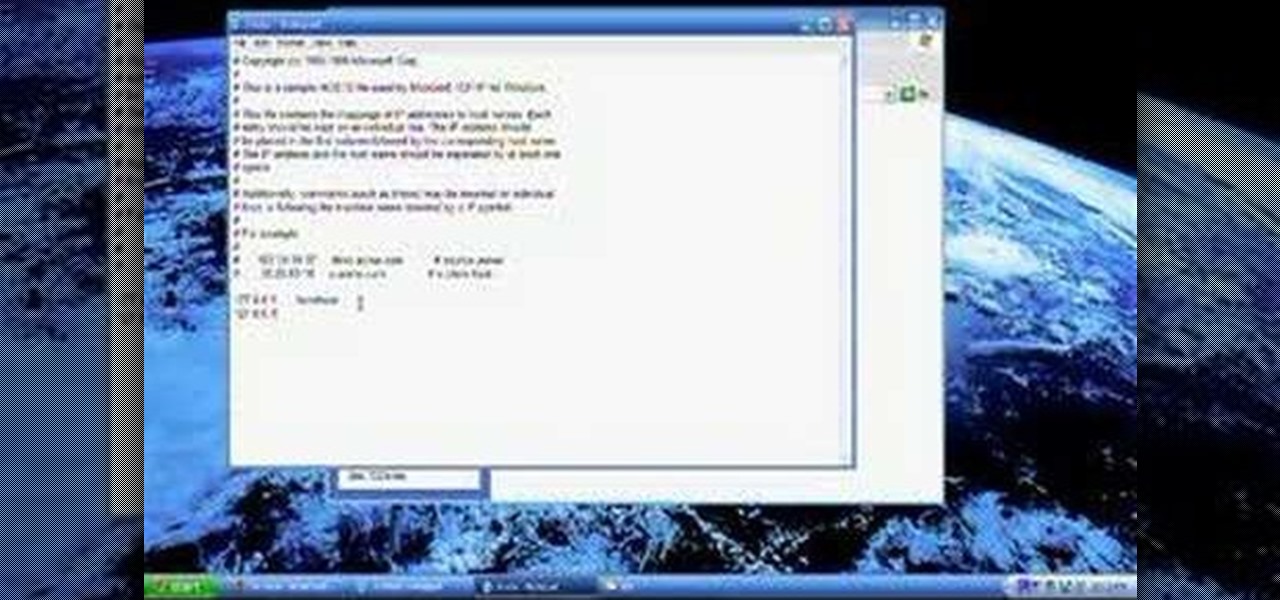
In this video, we learn how to block a website without software. First, open up 'my computer' and then double click on the local disk. After this, open up the 'windows' folder and then locate the 'system 32' folder, open this. Next, open the 'drivers' folder and then open the 'etc' folder. From here, double click 'host' file and then open it with a notepad. Now, after the last text type in "127.0.0.1 (website to block)". After this, save the file and then clean all the temporary internet file...

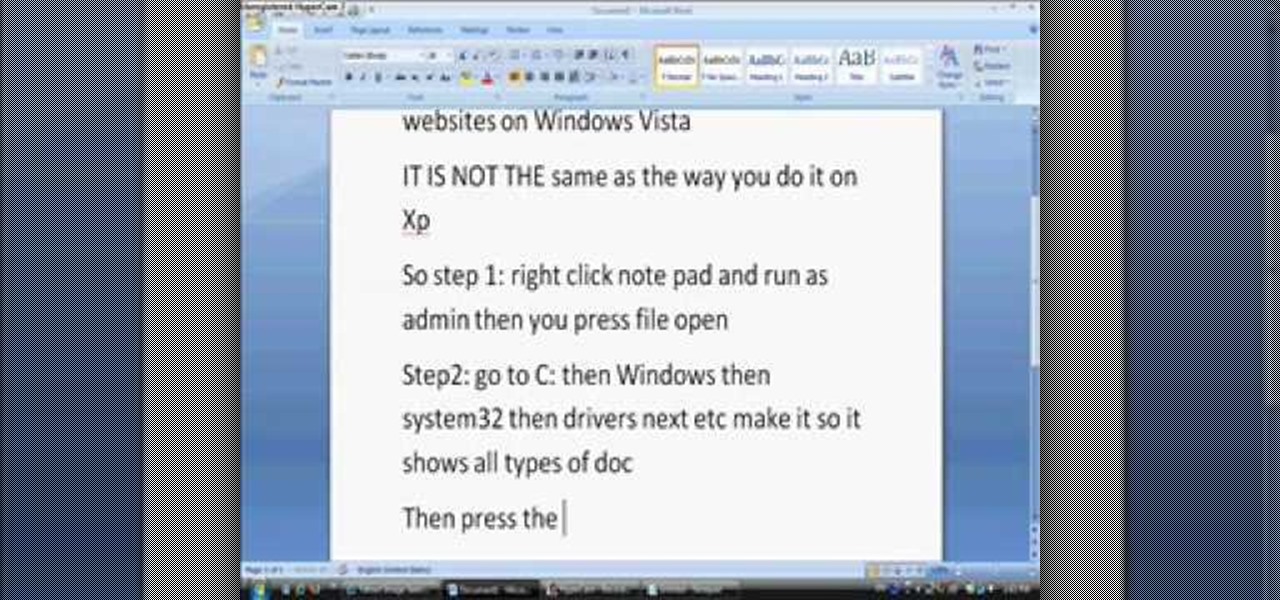
In this tutorial, we learn how to block websites on Windows Vista. First, you will right click on the notepad and then run as admin. From here, you will click "file open". Then, go to the C drive and open up windows. Then, you will go to the system and find the drivers, then click on the host file. From here, go to the second local host and press enter twice. Then, type in "127.0.0.1" and press tab. Then insert all the directories that you want to block. From here, you will be finished blocki...

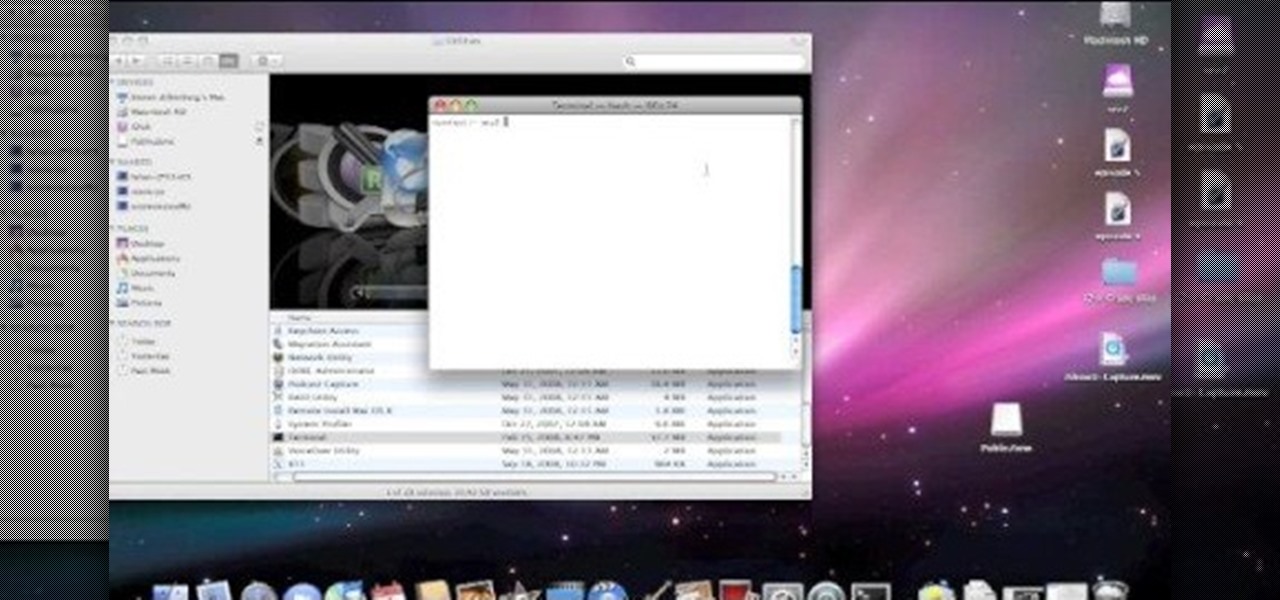
In this tutorial, we learn how to eject devices from the use of the terminal for Mac. First, go to the terminal of your computer where you will see a notepad sort of page. Next, type in "df" and then press return. You will now see a list displaying processes on your computer. On the bottom will be your public zoning device, which is your USB device. Next, type in "hdiutil eject -force (the code under "mounted on)- volumes-publiczone". This is not case sensitive, but don't forget or add in any...

1. Visit 3schools for free and fantastic web building tutorials. 2. Find the subject you are interested in researching and simply click on it and it takes you to a video.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

In this tutorial the author shows how to find out a Cool XP Easter Egg hidden in the XP which comes by downloading the latest update of widows update. The author now opens Internet Explorer and visits the windows site. Now he quits the explorer and holds down both the Control key and alt key and right clicks on the desktop seven times. Now keeping the control key pressed, he releases the alt key and right clicks the desktop and chooses the option 'Create ShortCut'. Now he releases all the key...

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

If you have not used your eRecovery system in a long time and have forgotten the password, have no fear. This video is here to help you retrieve your details and use your program again. In this clip, learn how to recover any lost passwords with Acer's eRecovery Manager for Linux.

And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

While making the transition from Apple to Android may not be hard for some, there are others that miss the small features that Apple offers on the iPad and iPhone. If you just got a Samsung Galaxy Note 2 or other Android device and want a familiar piece of Apple on your device, check out Hi Dev Studio's new Hi Notes application, which gives you iOS-styled notes.

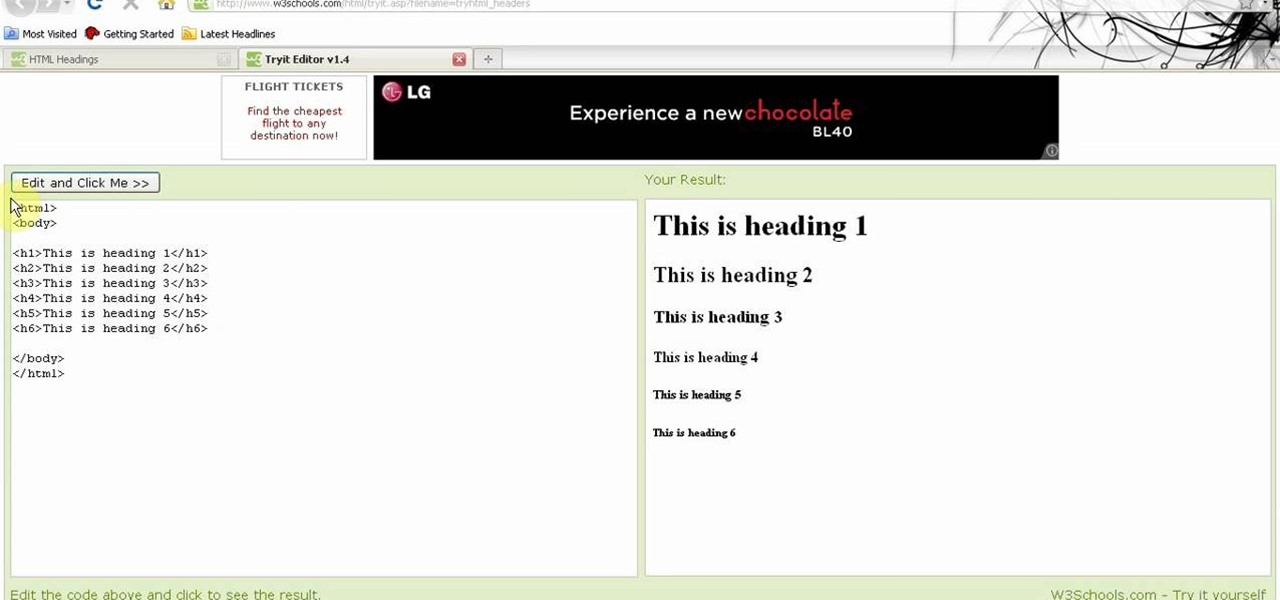
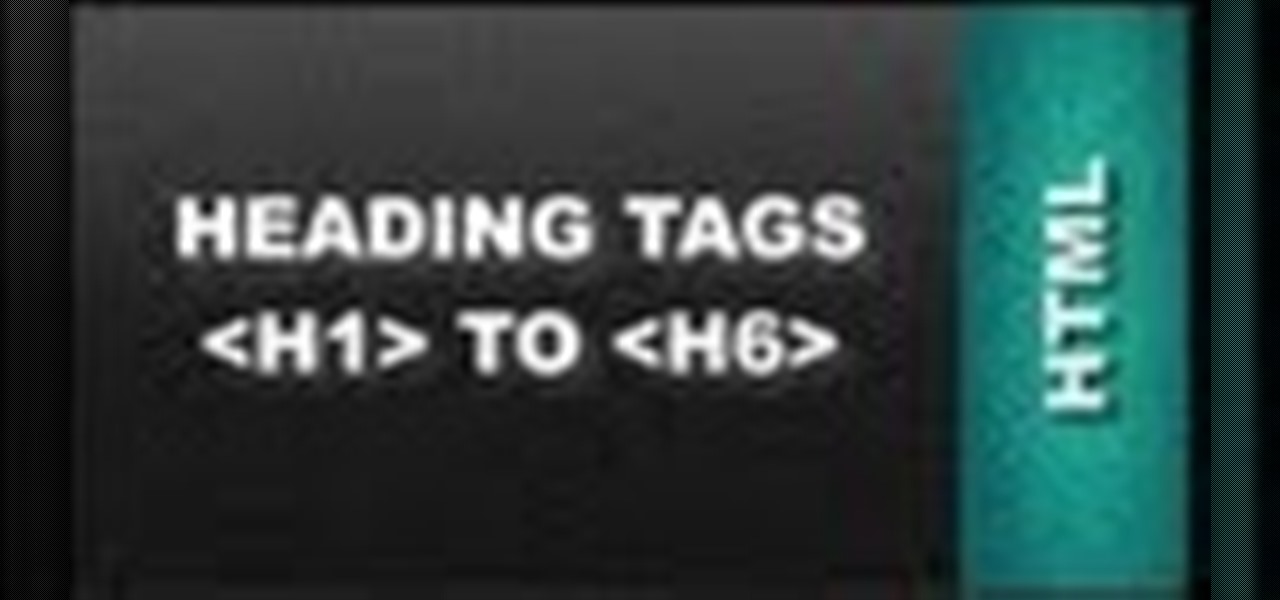
This HTML Web Design tutorial will explain how to add a Heading tag for your website. The heading tag is very important because it helps search engines to determine what the main topic is on a particular web page within your website. The HTML codes for heading tags range from h1 to h6 with h1 being the most important or in other words the main heading HTML web design tag. Make sure to give the h1 tag the most importance in terms of titles on your web page for headings. Another rule I recommen...

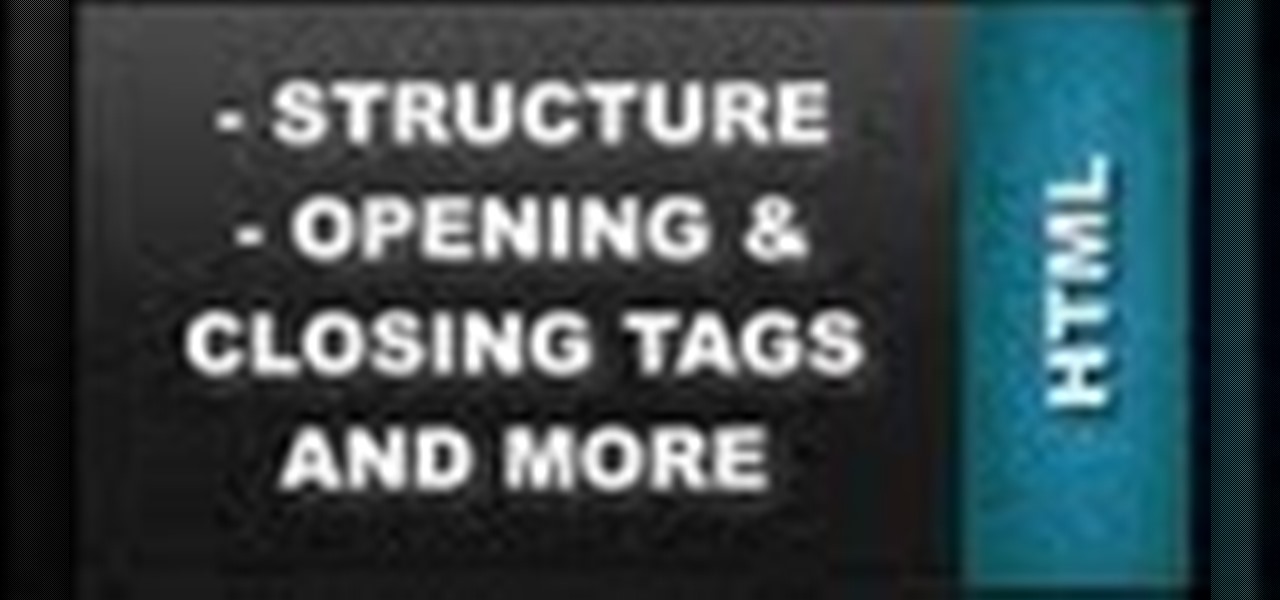
Learn how to setup up a basic structure for a HTML web design document, define the HTML version, open and close HTML tags and learn how to apply the proper file extensions when saving document in notepad. This web design tutorial is by no means a complete structure for HTML coding and is only a brief introduction to HTML web design. This video will only go over a brief introduction to the structure of an HTML document and in a future tutorial we will go over additional components that are nee...

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

With every flagship device they release, Samsung makes sure to add in at least a few little software goodies. Last year's Galaxy Note5 was no exception, because among other things, Samsung included a revamped version of their useful utility called Air Command that gave users quick access to tools and common functions with a small floating bubble.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?