Android Police reported that the upcoming Nexus phones would be getting an exclusive launcher this year, dubbed the "Nexus Launcher." This rumored home screen app was said to feature Google Now integration, a swipe-up app drawer gesture, and a few other finishing touches.

Move over rainbow food trends, there's a new, darker kid in town: jet black ice cream. And no, it doesn't have squid ink in it.

If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

We've both had a fondness for pancakes since we were kids; The way the smells of syrup and warm batter permeated the kitchen and lingered for hours drove us crazy—and still does.

One of the common complaints about dry pasta is that it lacks depth of flavor. This is why, once cooked, it often pairs best with bold and complexly flavored sauces.

Virtual reality headsets are all the rage these days, and among the menagerie of tech companies gunning for the top spot, there's one mysterious startup that is ahead of the game—Magic Leap—and you can tell just by watching their latest demo video of their product in action.

If you find yourself switching between Android devices frequently—for instance, your Nexus 6P and a Samsung tablet—you've probably noticed how the button placement can be different. Normally, it's back, then home, then the recent apps button, from left to right. But Samsung devices have this backwards, which can lead to frustration when muscle memory kicks in and the back button isn't where you expect it to be.

Samsung has been on a tear with its flagship devices since the release of the Galaxy S6; The S6 edge, the Note 5, and this year's Galaxy S7 models have all been met with universal acclaim, and even the staunchest of critics have almost nothing negative to say. Almost.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Video: . For the first prank you're going to need an empty container, preferably black, a smoke bomb and a lighter. I gotta say though this prank is not for just anybody so prank at your own risk. Let me show you how its done, first apply some hot glue on the bottom of the smoke bomb, then stick it inside the container.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Smartphone displays are getting bigger every year, and Samsung devices are at the forefront of that trend. But, from a software standpoint, the icons, buttons, and other on-screen elements seem to stay at the same scale. So while phones are getting bigger, their interfaces are getting bigger as well.

We've been on a constant hunt for the best way to make almond milk at home, and we think this trick might just be the most genius yet.

Dried fruit makes a great snack or salad topping, but after a while, they tend to become fossilized, rock-hard versions of their former selves. At this point, most folks probably just toss them out, as they're unpleasant to chew on when eaten raw and even more unpleasant to eat in bread or cooked with other ingredients.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

We knew it was coming eventually, but this is a bit out of left field—early builds of the next version of Android have been released almost two months ahead of schedule. Android N, as it's being called for now, is already available for the last two generations of Nexus devices, though it's just an early preview build for now.

Rich, creamy chocolate cups stuffed with smooth, salty-sweet peanut butter in a bite-sized package—yep, Reese's Peanut Butter Cups are an amazing fix for your sweet tooth at best, and a guilty pleasure at worst. It's easy enough to buy them on a whim at the local grocery store, but it's even easier than you might think to make them right at home.

Hey guys I am starting this Series because I thought there was a lack of post about Hacking from Android.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

For me, shredded coconut is something that is eaten several times a week in a variety of ways—and that includes in savory dishes. It can be added to just about anything, and this is a good thing if you enjoy having some variety in your diet. Because I get tired of eating the same foods all the time, over the last few weeks I've tried some pretty interesting and simple ways to use coconut flakes in order to keep my finicky palate satisfied.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

If you've ever used the YouTube mobile app for Android or iOS, you've probably noticed a cool little multitasking feature it has. While watching any video, you can simply swipe down on your screen to shrink the video down to a thumbnail view, which then allows you to browse the rest of YouTube while the original video keeps playing.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

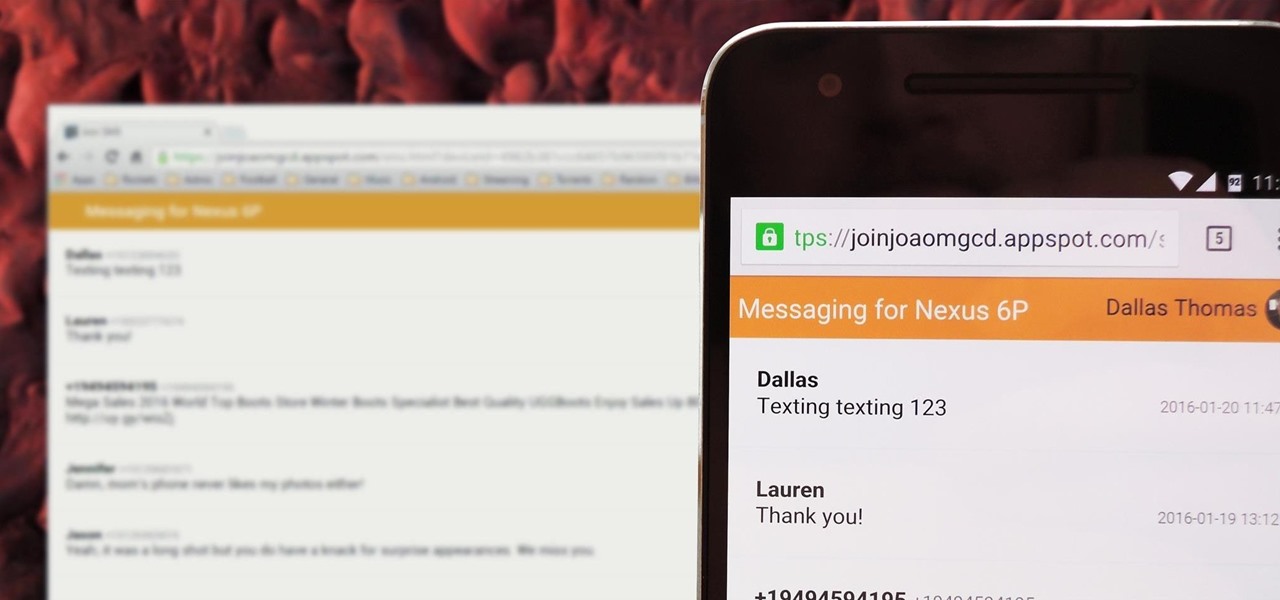
There's no iMessage app on Android, so unlike the folks who own both an iPhone and a Mac, we have to rely on third-party solutions to send and receive SMS messages from our computers. But on the bright side, this means we don't have to buy an exorbitantly expensive desktop or laptop to respond to texts when our phones are out of reach, because Android is all about cross-platform compatibility instead of chaining you to an ecosystem.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Past video recording apps we've covered made it easy to turn your Android device into a hidden spy camera, even allowing you to inconspicuously record videos using your volume buttons. While both are viable options that can secretly capture video, today we're going over an additional method that will let you both schedule recordings or discretely trigger them without anyone around you noticing a thing.

I've never had a problem with veggies—we've always been the best of friends—but I do have a lot of other people in my life that have been less than enamored with this basic food group in the past. Some cite the bitter flavor associated with veggies like Brussels sprouts, while others dislike the various consistencies that come with boiling or steaming vegetables such as broccoli or eggplant.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default browser, Chrome, so none of your synced data like bookmarks, passwords, and history is available when an app is using WebView to display a page.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

Back in August, Google unveiled a new YouTube Gaming service meant to compete with e-sports streaming sites like Twitch. At its launch, the service was capable of broadcasting desktop PC gameplay, but when it came to the mobile segment, users were only capable of viewing streams hosted by others.