It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

It looks like the dust is finally starting to settle on Google's POLED PR nightmare. The Pixel 2 XL — one of the most hotly-anticipated phones of the year — has been plagued by screen issues and worries. While it is certainly not without its faults, Google has created several software fixes and is offering a 2-year warranty for screen burn-in, so we can rest a bit easier about purchasing Google's latest Pixel.

Google just released the second developer preview of the Android 8.1 update for Nexus and Pixel devices, and even though it's just a point-one release, there are lots of cool changes. Before you run off to join the Android beta program and try the new version, it's worth reading up on what's new.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

I don't know about you, but I'm tired of hearing some of the same old jargon from people online who claim that all you need to make it on Instagram is to take good pictures and post consistently. Yes, for sure, but do you really think it's that easy?

Are you interested in video editing, but have no background in it? Are you looking to put together a short from some clips you've shot, but don't know where to start? You could use iMovie, an application that comes free with every iPhone, but then what would you do on Android? There must be a universal solution that works across both iOS and Android to let you work however and wherever you like.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain application after it has been around for many years, it can be downright intimidating to know where to begin.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Update: June 19, 2014 Android 4.4.4 has been released, fixing a small security bug in 4.4.3. The factory images have already been made available to all current-generation Nexus devices, and I've linked them out below. This does not affect the process depicted, you can still use these same steps to bring your device up to date with this latest release.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

Hello, all. In this article, I will be showing you how to make one of the most useful products known to man. I am talking, of course, about charcoal.

If you actually had to look up what "DS" stands for in Nintendo DS, that probably means you weren't a huge fan of the portable game system. To be honest, I never was. It's fairly bulky and has two tiny displays.

The best part about April Fool's Day is that everyone is fair game. Even big tech companies like Google and Twitter get in on the action every year. It encourages even the most uptight, unfunny party-poopers among us to have a little fun driving each other crazy with pranks — even at work.

Hello again, faithful readers. For today's lesson, we will be learning the correct way to restring and tune an electric guitar. I almost wasn't going to post this because it is so basic. But, as with many basic tasks, there are a lot of people who know how to do it, but can't really do it right. If you are a new guitarist, this is an essential piece of maintenance work, because guitar shops usually charge way too much for this task. Of course, I'm kinda cheap, so even 5 bucks is too much for ...

One of the hardest, most intimidating parts of making your own Steampunk guns from scratch is the wooden stock of the gun. To be fair, it's probably the hardest part. It requires the most artistry, and is the easiest to mess up.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

If you don't work in construction or are a woodworking master, you probably aren't entirely sure what all those marks are on a tape measure. Sure, you likely know the basics, like there are 12 inches to a foot, but what are all those little tick marks for? Don't let all those little lines dissuade you from using a tape measure. Follow these guidelines to help you read all those little ruler marks.

Pastry Chef Anne Heap demonstrates how to use a pastry bag, as well as techniques for decorating cupcakes. Frosting a cake or cupcakes with a pastry bag is much easier than using a knife. The bags come with many different styles of tips. Just choose the tip you want to use, fill the bag with frosting, squeeze to apply the frosting, pull up and let go.

To really make your eyes stand out you may want to emphasize the crease in the eyelid with eye shadow. Dramatic eyes are great for going out at night and by using your darker shadow in the crease you will be sure to be noticed.

You don’t need a camera to recreate a picture you see. Choose and object and with only a pen and pencil you can recreate that object as a sketch. Take your time, and choose somewhere quite where you can focus on your creation.

You’re munching away on walnuts and, oh no, you notice you have a scratch on your wood floor. You already have the solution in your hand. The oil in nuts will fill in and make scratches on a wood floor disappear.

If your in college or just want to be prepared for an unfortunate situation, it is important to know how to tell if someone is suffering from alcohol poisoning. Binge drinking can lead to long term health problems but with vigilance, immediate death can be prevented.

It takes more than a kicky costume to become a professional wrestler. Start young to build up your basic wrestling skills and athleticism. To turn pro you’re going to need some acting flare, love for performing and a little luck.

Tired of the same old snacks? This cheeky treat will be sure to shock your guests. Although, we might not consider ants as a regular food source, they are edible. Plus, anything tastes good with butter and garlic.

We've all attempted to fold a paper airplane before, right? One we hoped would sail majestically through the air for a good while but just ended up nose-diving into the grass. Paper planes, an invention likely as old as paper, are models of engineering; and they must account for the same dynamics as real planes, from drag force to stability to weight. So what is the perfect design?

Discover the art of Telescopic Pole Setup in this informative video, where we guide you through the process of preparing your pole for speedfishing. Whether you're targeting Bluegill, Crappie, Trout, or Perch, pole fishing stands out as one of the most effective methods to reel in a catch.

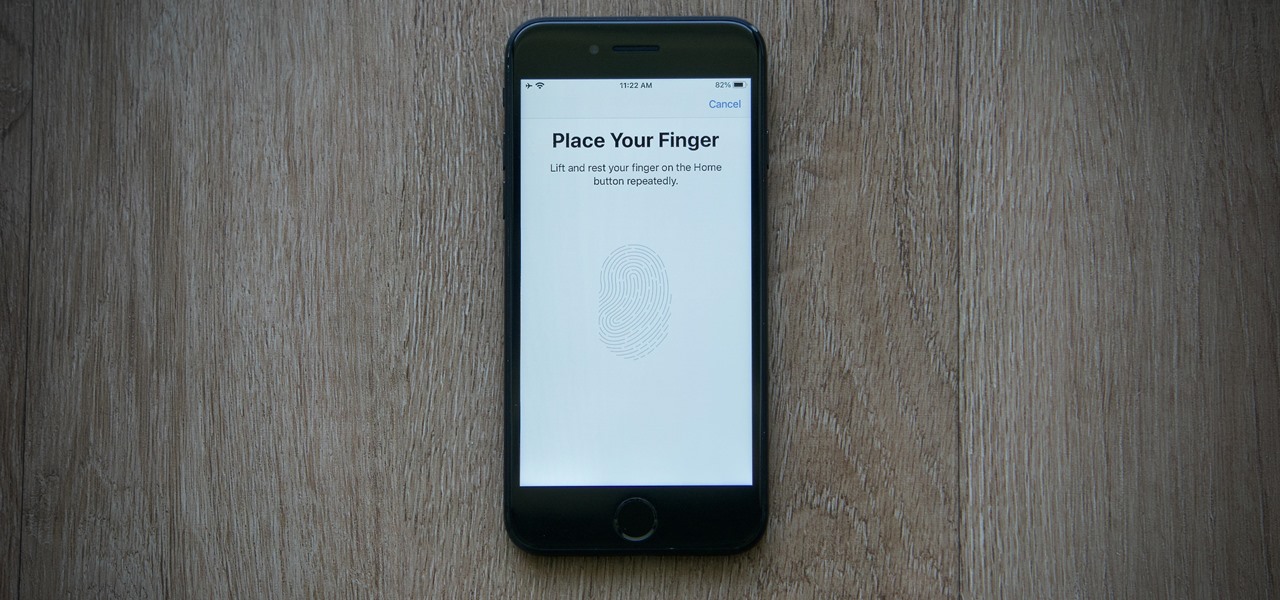
While Face ID might have taken over as Apple's favorite authentication method, Touch ID is still very much alive. The tech is usually speedy and accurate, but you might have noticed that it's been a bit laggy recently. If that's the case, you should know that Apple actually fixed this issue. Here's what you can do.