Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!

One of my favorite things about American Chinese food is how easy it is to eat: the pieces are bite-sized, the flavors are addictive, and the meat is always tender and easy to chew. But if you've ever tried to replicate any of your favorite takeout in the kitchen, you've likely noticed that the high heat required for most recipes thoroughly dries out the meat that you're trying to cook.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Beer isn't just for drinking anymore. There are many useful and surprising things that an ice-cold brewski can help you accomplish, from household chores to better-tasting food. It can even help you look and feel healthier.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Dropping upwards of $60 on a new game can really break the bank, and being a struggling college student leaves me having to decide whether to pick up the latest title or, you know, eat. But often my more primitive urges win out, meaning the only way to enjoy the latest and greatest games are vicariously, using increasingly-popular live streams.

Without a doubt, sushi is one of my favorite foods—dainty and delectable, while also fun to make. So let's get started with maki rolls, aka makizushi, probably the most iconic form of sushi. You know, the one filled with rice and your standard sushi ingredients, rolled up in a sheet of dried seaweed.

Not all batteries are created equal, but one thing's for sure—they all lose capacity over time. Thankfully, the advanced lithium-ion batteries in your MacBook and iPhone are meant to last for several years before they begin to lose their overall charge capacity.

When I get struck by a craving for something SCJ (savory, crunchy, juicy), nothing fits the bill better than a BLT. But why settle for the sandwich form when there are so many other possibilities? Some of my favorite alternative ways to serve up a BLT are 1) as a salad, 2) in tomato cups, 3) in mini bread bowls, 4) as lettuce wraps, 5) as a dip, and 6) in bacon cups.

Whether you call them chickpeas, garbanzo beans, or Egyptian peas, these little morsels are one of my favorite snacks—when properly seasoned, that is. Being mild in flavor on their own, they're incredibly versatile and fun to experiment with. (They're also incredibly healthy.)

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

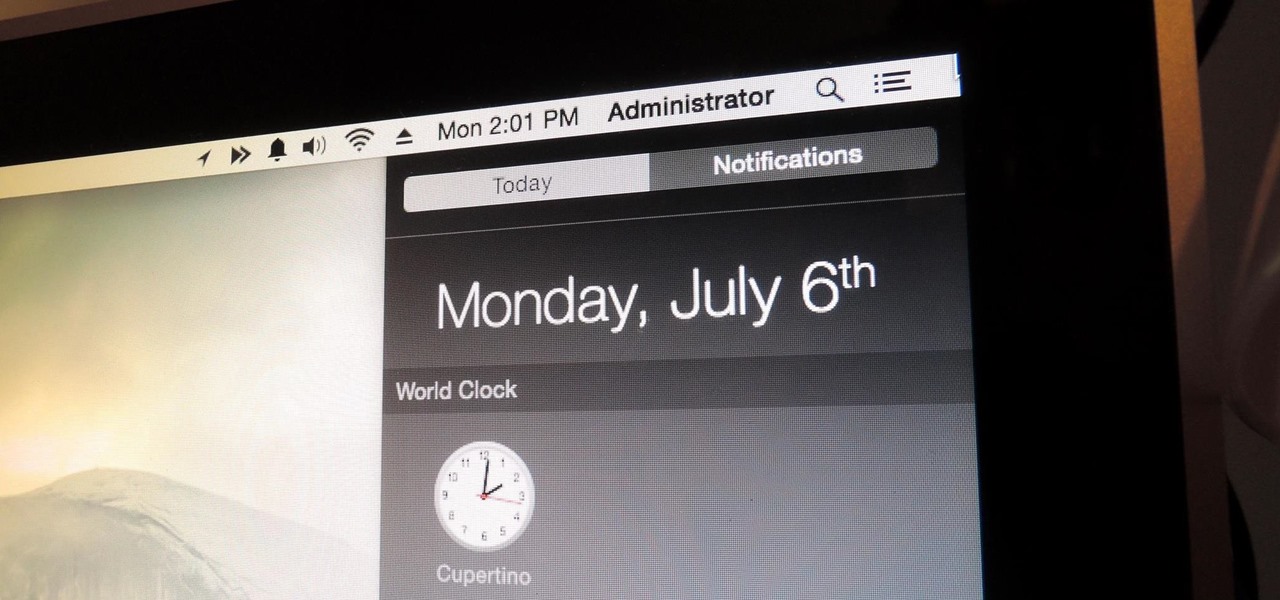
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free.

Protein powder is a fad in the same way that Justin Bieber's music is: you either love it, or you hate it. Everyone I know has a strong opinion about protein powder, ranging from "daily necessity" to "utterly useless."

The other day I was doing the math on roughly how many eggs I eat each year. I estimated about 500. That's a lot of eggs. And, subsequently, that's a lot of eggshells to throw in the trash.

As Android owners, we ultimately have to look at our device and ask the difficult question: "Where the hell did all these applications come from?"

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

Ask ten different people how they feel about boxed cake mixes, and you'll likely get ten different answers. Some baking purists will berate them and throw them in the same category as garlic presses and knife sets sold on infomercials. Many people will say that they prefer not to use mixes, but keep one in the pantry just in case. And I dare you to find a college student that doesn't sing their praises.

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

We are visual animals. So when it comes to food, presentation is everything. In deciding what to eat, certain colors and textures instantly turn us off or on. Think of runny sautéed spinach versus a salad of fresh vibrant spinach. Which one would you reach for first?

With an Android device, you can replace almost any default app with a third-party offering. Don't like your home screen app? Replace it. Tired of the text messaging interface? Upgrade it. The same can be said for Android's lock screen. But while many third-party lock screen apps are available, so far, only one has been designed with the Samsung Galaxy S6 and its fingerprint scanner in mind.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

While Kobe beef cows get massaged, American dairy cows are taking a real beating. Many people are cutting back on dairy while a growing number of people are discovering that they're lactose intolerant. As the public's disdain of cow's milk grows, milk sales themselves are at a forty-year low.

It's 3 a.m. and you're wide awake—your mind is running wild with worries, workplace stress, and panic about the day that lies ahead. How can you possibly slip back into sleep and snag a few more hours of rest when you're so anxious?

When I was younger, my family would go to fancy restaurants and I would invariably order a Shirley Temple. (Ironically, the real Shirley Temple actually didn't like it much.) But it's hard to really find anything offensive in this kiddie cocktail: It's ginger ale with a splash of grenadine. There's also the less famous Roy Rogers, which is Coca-Cola with grenadine. The grenadine, red and sumptuous, always made its drinks look and taste much cooler.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Leaving your computer unattended, whether at home, work, or a coffee shop, even for just a short while, is enough time for someone to steal it or look at your personal files. While there are ways to deter thieves, it's a little harder to keep snoops away.

Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Google's got a hit on its hands with this one. Android 5.0—AKA "Lollipop"—will be making its official debut next month, but a new preview build has given us a glimpse into the future, which looks brighter than ever.

Every year, some overly ambitious neighbor down the street amazes the crowds with his DIY illusion costume. While these costumes certainly require more work than pulling a mask over your head, they do have that wow factor that others lack.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Apple definitely wasn't first to the widget game, but any iPhone running iOS 8 or higher can add widgets to their Today View found via a swipe down from the top of the screen when on the home screen or in any app. There's even access to widgets on the lock screen via the same swipe down on iOS 8 and iOS 9 (on iOS 10, iOS 11, and iOS 12, all you have to do is swipe right on the lock screen).