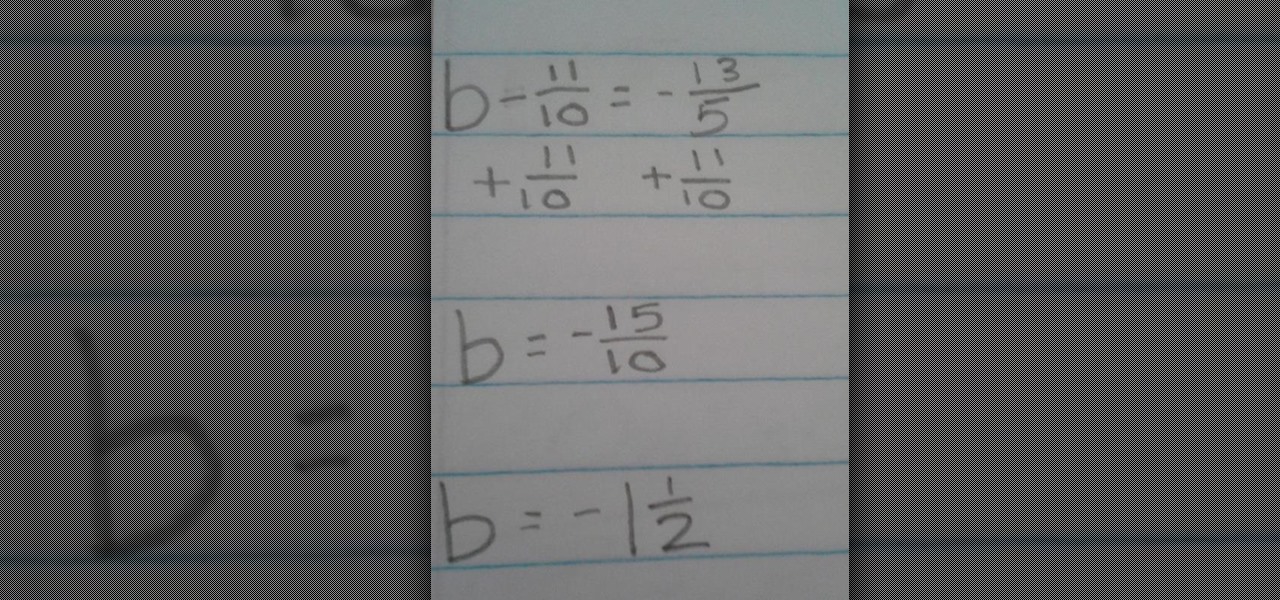
Excitement is building for the official Android Oreo release on the Galaxy Note 8. We detailed a leaked Oreo build for the Galaxy S8 and made a short tutorial on how to install it on your device. Now, there's a newer Oreo build available for the Galaxy Note 8 as well. Both of these builds appear to be closer to the official release candidate than the official beta updates on the Galaxy S8.

Samsung's latest Oreo Beta update for the Galaxy S8 brings an impressive number of new customization features. On the lock screen, we've seen the introduction of new colorization options for the clock and transparent notifications. Not to be forgotten, the Always On Display is getting some new clock styles and colors.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

Update 6/16: This number is now way higher. In just the first two days of this sale, over 350,000 people have pre-registered for the phone.

Update 6/15: Netflix responded to our request for comment: This [download limit] may vary depending on the title and licensing agreement. There may be limits to the number of titles from the same licensing agreement that you can download at the same time. We will only enforce these limits in cases where our licensing agreements require us to do so.

When you think ticks, one of the first things to come to mind is Lyme disease. However, as terrible as Lyme disease is, there's another threat from ticks rising in rank in Connecticut and the Northeast — one that is spreading and that hospitals are not prepared for — the Powassan virus.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Google has added a number of new features in the latest update to Google Keyboard including a one-handed mode and a setting that lets you adjust the height of the keys. The update hasn't gone live on the Play Store yet, but you can download the APK right now for both 32-bit and 64-bit phones.

Google has been working on its voice recognition technology ever since the days when you had to call a phone number with a Silicon Valley area code to dictate your query. As you can imagine, things have come a long way in the decade or so that has passed, to the point where we talk to our phones as if they were a person nowadays.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

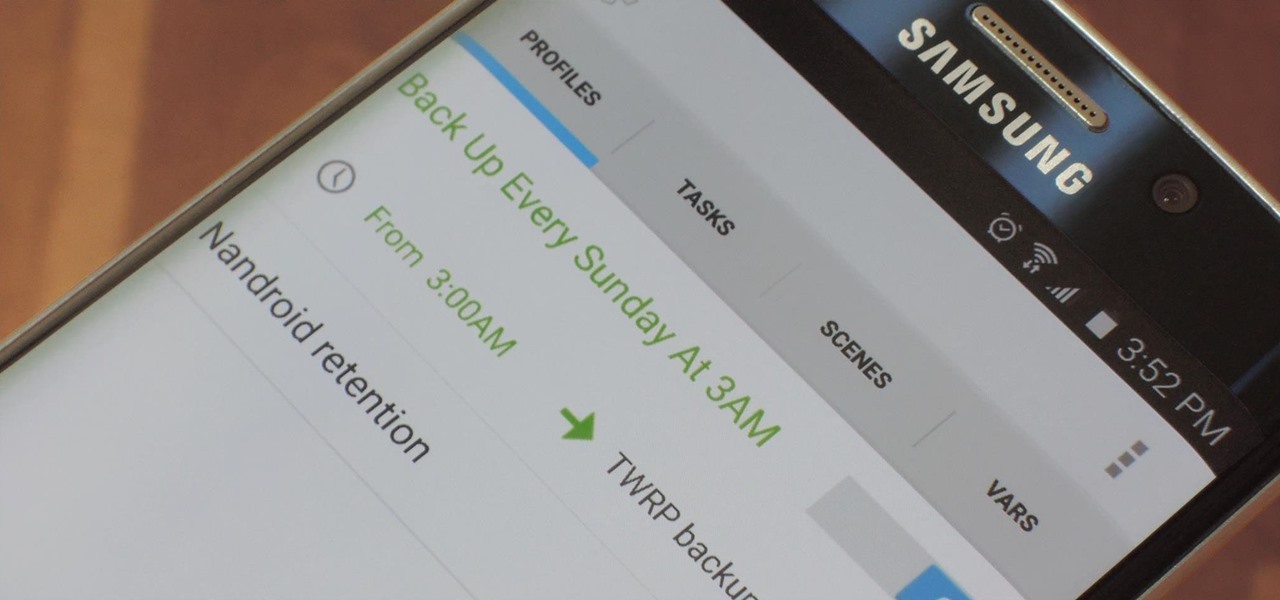
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

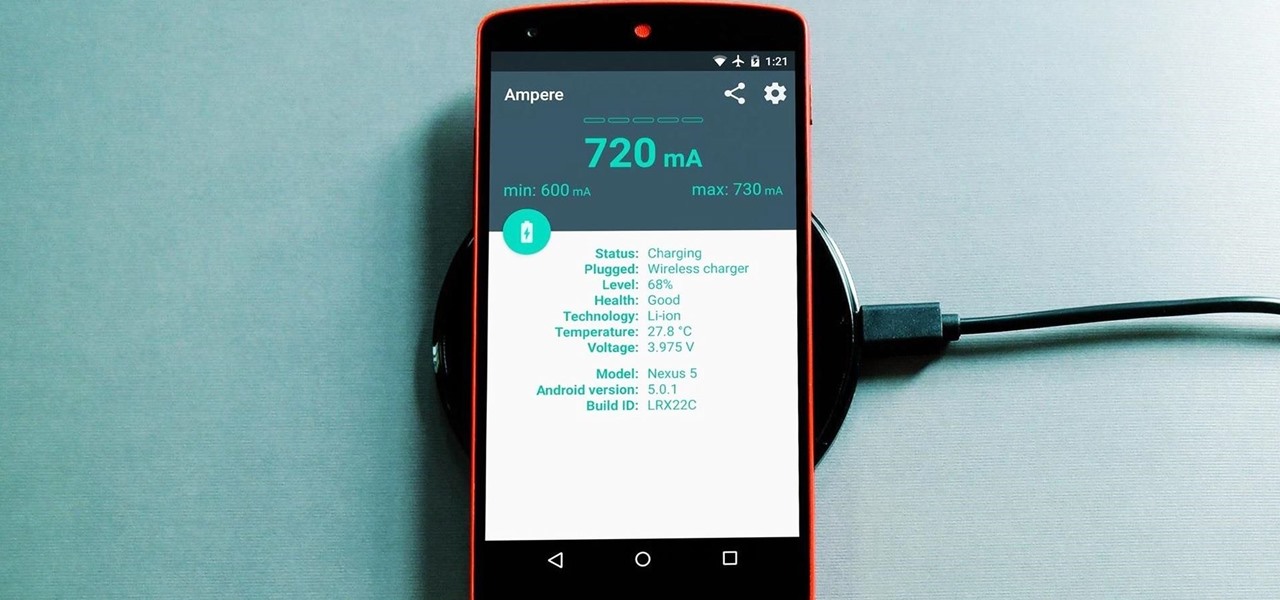
Not all smartphone chargers put out the same amount of current. The adapter in your car probably charges your phone a lot slower than the one plugged in at your bedside, and if you use wireless charging, it may be a bit slower still.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

We're living through the technological revolution, and while devices like the iPhone 6 or Galaxy S5 have made life easier and more entertaining, it's possible that sometimes our smartphone usage can become uncomfortably excessive. In your own experience, think about how anxious and off you feel when you leave your phone at home—Cell Phone Separation Anxiety or Phantom Phone Vibrations shouldn't be a real thing that we deal with.

If you purchased your Nexus 5 from Google Play in the United States, we've got great news for you. In an unprecedented move, Google has started offering customers the chance to exchange their broken or water-damaged Nexus 5 for a new or refurbished unit—free of charge.

With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?"

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.

It is really quite easy to flash a custom recovery to your Nexus, and there are many excellent tutorials on how to do so (see the How-To below): The Easiest Way to Install a Custom Recovery on Your Nexus 7 Tablet « Nexus 7.

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

I never really cared much for the clock widget on my Nexus 7, mainly because it only gave me two styles—analog and digital. There are many different styles of clock widgets available on Google Play, but the majority of them just don't look good enough for me.

Unless you're using something like 360 Vault to store photos and videos, people you lend your iPhone to can easily browse through the gallery without you knowing. It makes me anxious just thinking about it.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

Are you tired of your snoopy coworkers and friends lingering over your shoulder as you type in your security passcode? Unless you have the newer iPhone 5S with Touch ID that scans your fingerprint, you've only got a couple of security options—either a 4-digit numeric passcode or a cumbersome password.

I know it's a very first-world problem, but I really can't stand it. Email was invented to speed up communications between people across the world, even just across the office, yet when I'm on my super awesome iPhone running iOS 7, I have to go back and forth between my gallery and my email to send more than five photos at one time.

Why can't I see who is stalking my Facebook profile?

Solving Equations with Fractions Using Addition In our first example, our equation is b - 11/10 = -13/5

There is a substantial number of helpful tools at your disposal in Microsoft Word when it comes to writing; grammar check, word count, dictionary, thesaurus, and tons more. One tool that doesn't necessarily make itself obvious is testing your document's readability. With this built-in tool, you can not only check your spelling and grammar, but also the reading level of your document.

In a previous how-to, I showed how to send and receive text messages by wirelessly syncing them from your phone to your Nexus 7 tablet. Some eagle-eyed users may have notice that the Nexus 7 with 3G actually has a SIM card slot.

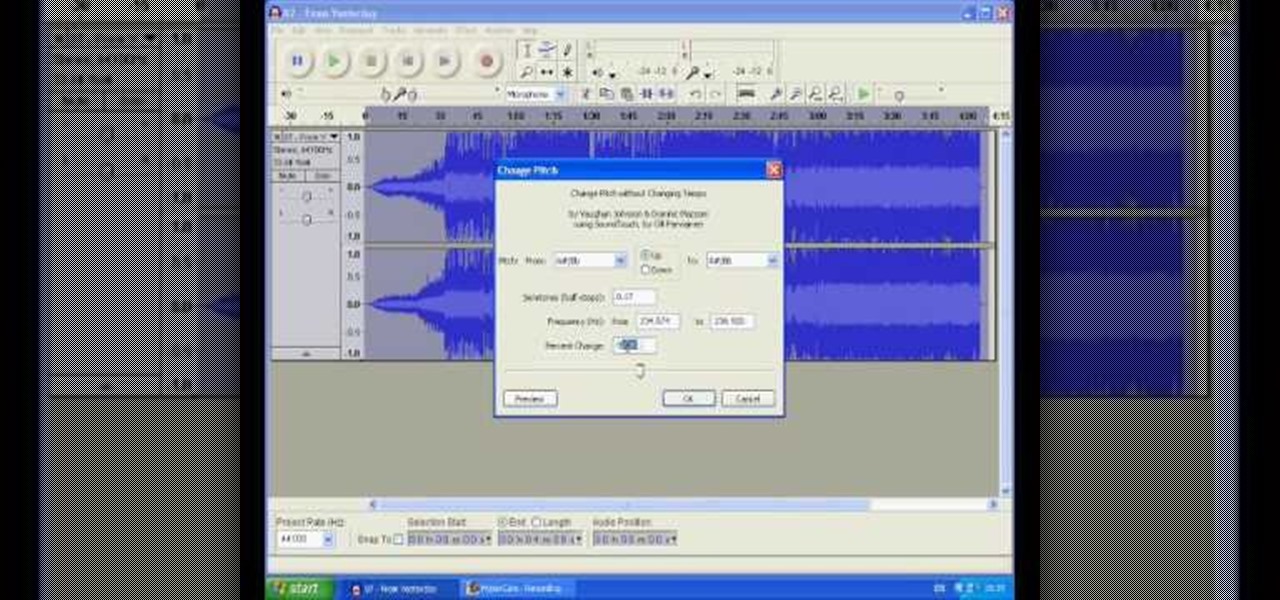
If you're a user of digital editing software Audacity, you already know you can do a ton of cool things. One of the cooler things you can do is changing a guy's voice to sound like a woman's. This is done with pitch control, or autotune, and will like you modify the voice by a number of octaves. I this video, rock band 30 seconds to Mars is made to sound like Avril Lavigne. Check it out! Of course, this can also be done with your own voice too!