News: Many Lookup Engines
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.
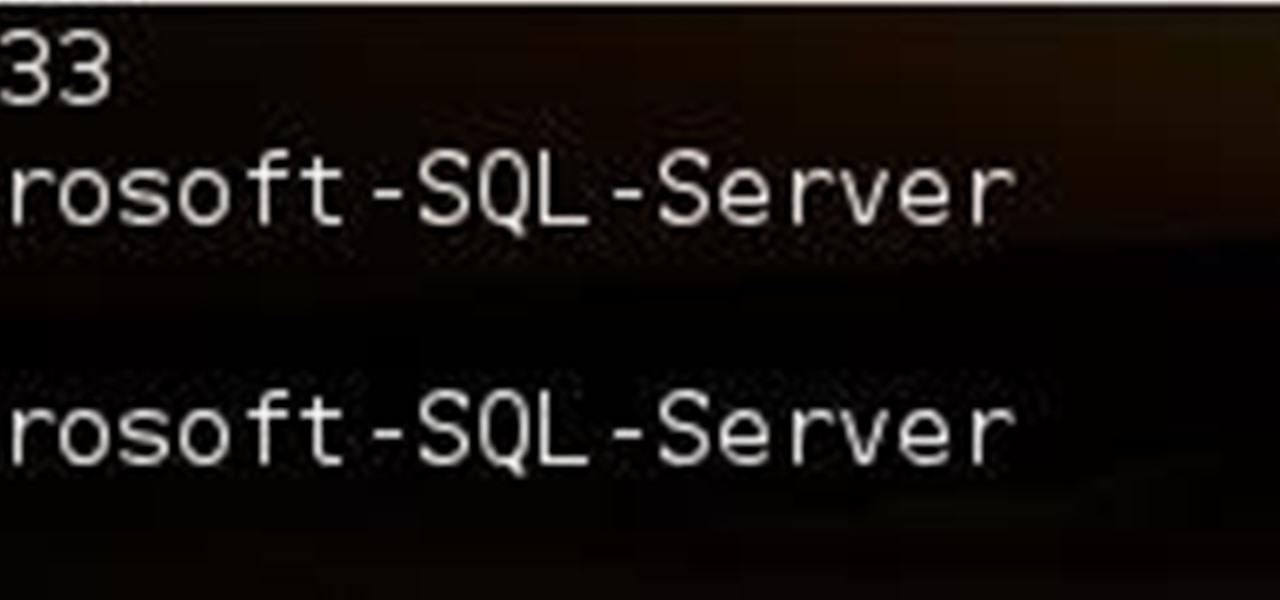
I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do:

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

For a number of years, I have had a vortex cannon on the top of my list of projects to attempt. Creating a sturdy cone for the barrel has always been a hurdle in the design, one I finally found a solution for in this video.

Aside from the fact that it was the only game available on my cell phone at the time, I was really good at Snake. I still occasionally play it on my smartphone, but I've never been able to duplicate the same level of achievement as I once did.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.
Reddit is a force to be reckoned with. What started out as link aggregator has become one of the world's most popular websites, with over 170 million unique visitors and 6 billion monthly pageviews. Whether you're into cute animals, crazy conspiracy theories, sports, or Taylor Swift's armpit, Reddit definitely has something for every taste, interest, and morbid curiosity.
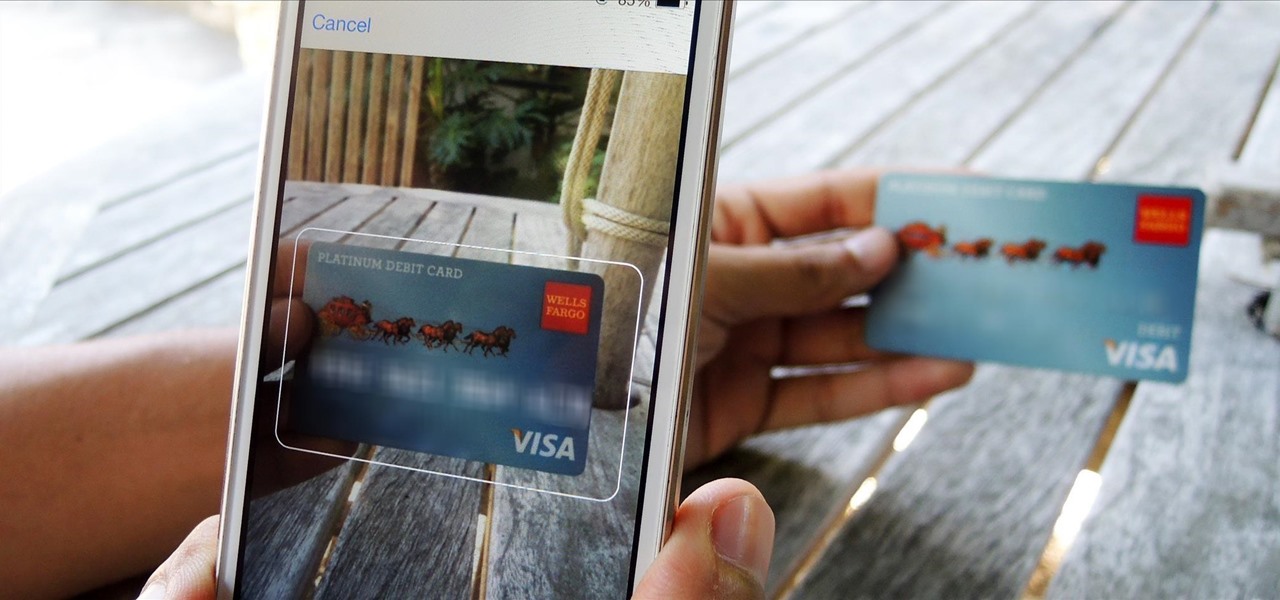
There's a feature that debuted in iOS 7 that lets you to save your credit or debit card information in Safari so that you can auto-fill text boxes when purchasing something online. Unfortunately, you still had to manually fill in your card info the first time, and if you wanted to disable the feature for security concerns, it was entirely useless.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.
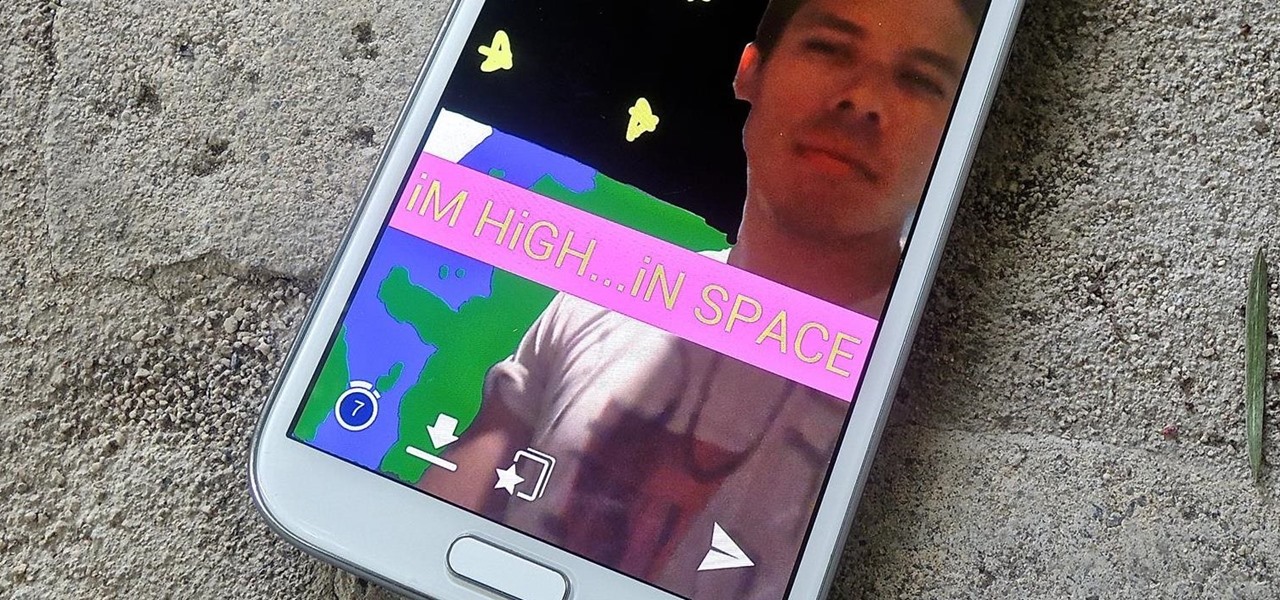
In an attempt to keep things simple, Snapchat has a limited amount of editing features, made up of "smart" photo filters, drawing pens, and special text captions. If you want more editing capabilities, you'll be pleased to know there's a way, no thanks to Snapchat, but you will need to be rooted.

Numbers are everywhere in life, and some are better at doing the math than others. Unless you're Gert Mittring, it's safe to say you use the calculator app on your tablet just as much as I do, and it's often disrupting your other tasks.

I don't drink a lot of milk, so when I do, it's always whole milk. I'll drink two-percent if it's the only kind available, but skim? I'd rather have none at all. Tons of people buy reduced fat milk because they're trying to eat healthier, but to me, the extra calories are totally worth it. And, contrary to popular belief, whole milk is actually better for you anyway. Just like diet soda, the downsides of reducing the number of calories in milk outweigh the benefits. Studies have found that co...

As you level up in online gameplay for Grand Theft Auto 5, certain vehicles become inaccessible—no longer spawning as they regularly would. One such vehicle is the Cargobob helicopter, otherwise known as the largest and heaviest helicopter in the game. If you're no longer able to spawn a Cargobob in GTA 5 and want one for your own, you can purchase one with a little help from YouTube user omgurheadsgone.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

There's something missing on your brand new Samsung Galaxy S4, and if you're a softModder like me, you know exactly what it is already. If you don't know, keep reading, because you should—anyone who wants a better Android experience should.
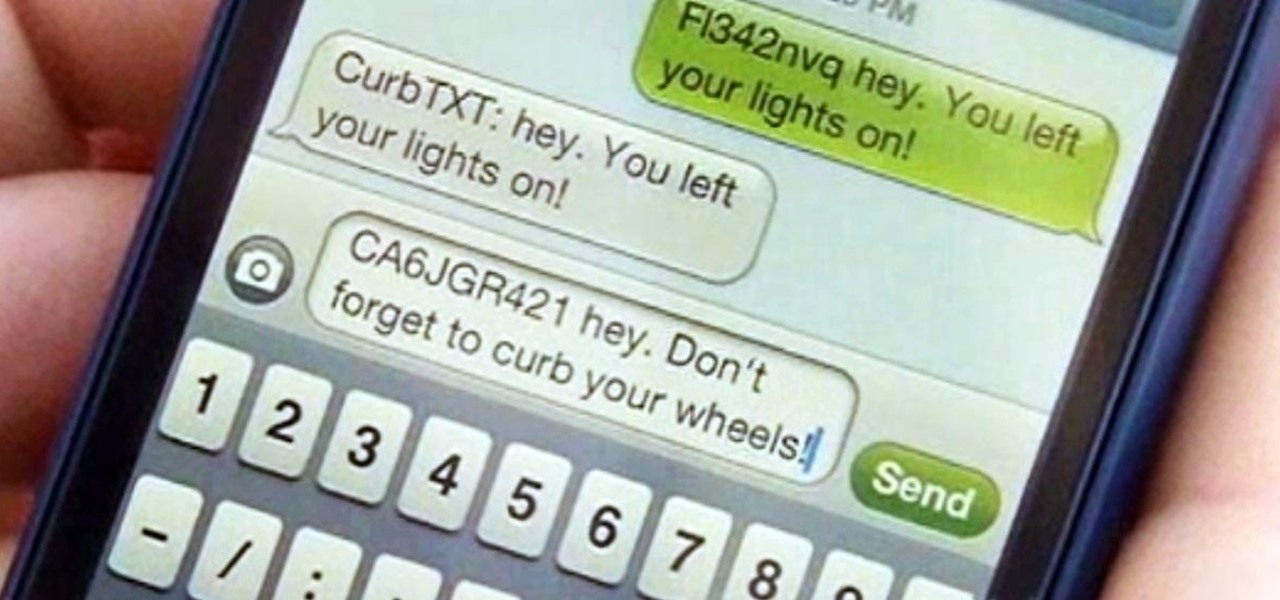
Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers.
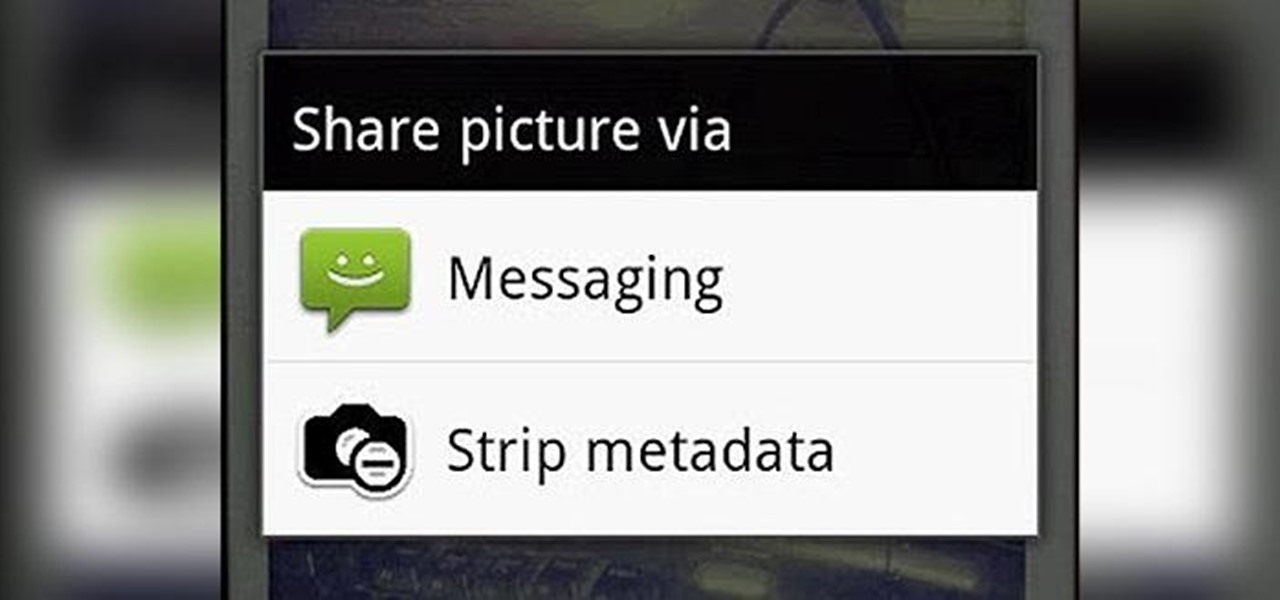
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.
As someone who writes an extreme amount, it's a necessity for me to have an organized and multifunctional text editor. The stock iPhone Notes application is useful to an extent, but it sorely lacks in features and design. Writing and text editing applications are nothing new to the iPhone, but many of them are overloaded on features, making it even harder to keep organized. Here are just a few alternatives that I find helpful in my day-to-day writing.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

Motorola launched a new webpage on Friday that tells Android users how to unlock the bootloaders on a limited number of new Motorola smartphones and tablets. This new 'Unlock My Device' page helps demystify the process and make it easier for users to customize their phones.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Yes! soon I will be able to log in more as I untie the shackles this map has placed on me in the time leading up to its eventual release and log in once in a while!

The Smurfs. The Super Nintendo. Together, they're a nostalgic combination of our youth. Hanna-Barbera and 16-bit video games. There's nothing better than taking a trip down memory lane… and kicking its butt!
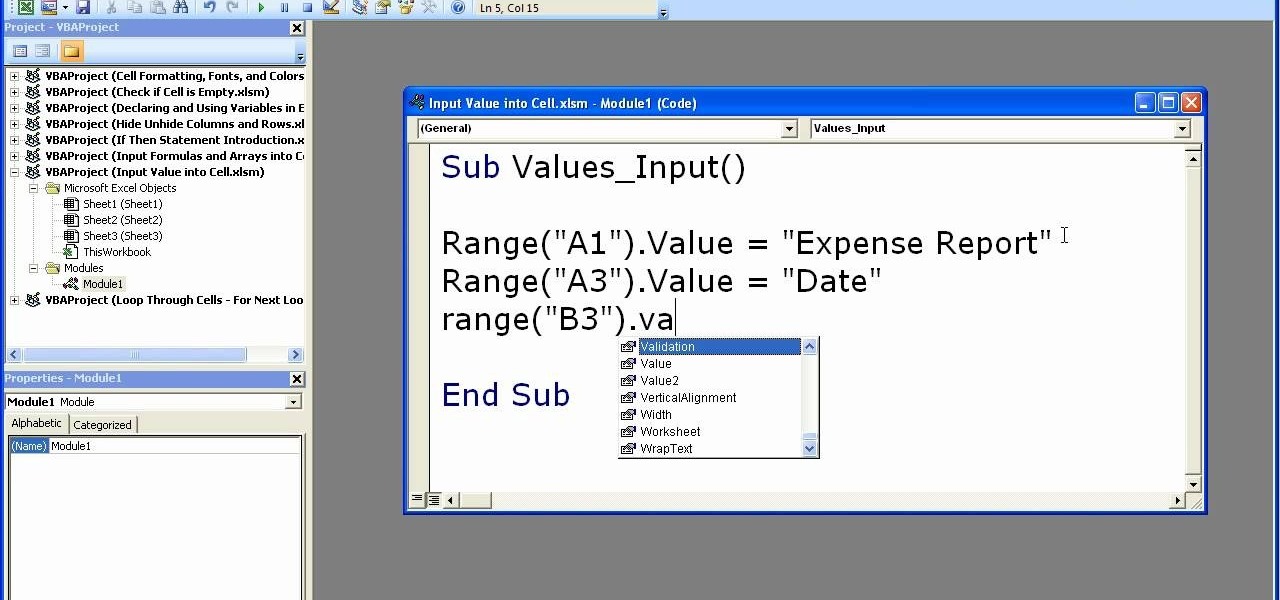
This video shows how to enter values into cells using Excel macros and Visual Basic. This includes a sample Expense Report that is used in this demonstration. In this demonstration, we will create the macro that inputs a title as "Expense Report", Three columns i.e. "Date", "Item" & "Amount", and the summery field as "Total Expenses", as well as the formulas located at the respective cells. Now, we're going to use two keyboard shortcuts i.e. "Alt + F11" to open-up the VBA window and "Alt + F8...


Learn how to do a standing barbell curl drop set while leaning against a wall. Presented by Real Jock Gay Fitness Health & Life.

It doesn’t matter how long ago your last geometry class was, you can still impress your friends by finding a geometric mean. The geometric mean can be used to find the average of numbers with out unusually high or low results effecting the result.
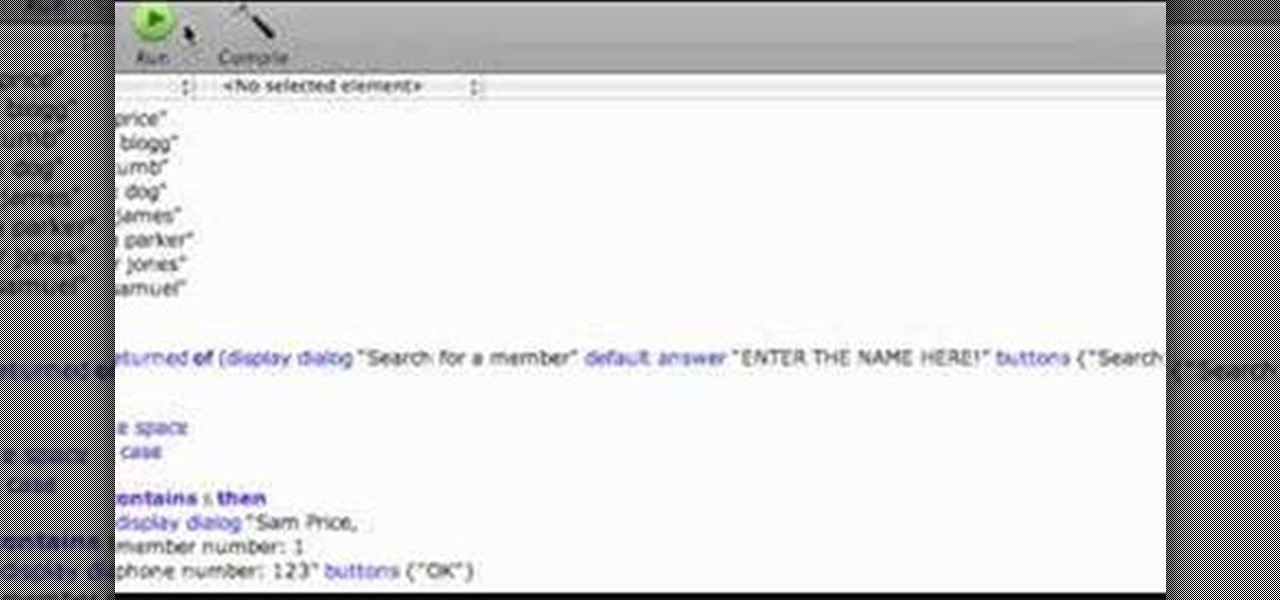
This video tutorial shows you how you can build a database in AppleScript! You don't know what AppleScript is? Well, it's a programming language for Mac computers only. You can build and design your own little applications if you are good enough.

The video shows you how to calculate capital budgeting with a Texas Instruments BA2+ financial calculator. Capital budgeting will help you determine cash flows for given investments for a certain number of years in the future, thus helping you determine if the investment is worthwhile. The buttons you will use are the CF (cashflows) button, the NPV (net present value) button, and the IRR (internal rate of return) button. The video uses the example of a $10,000 investment that will return $5,0...

Here is another cool photo manipulation you can do using Photoshop CS3. You can take a normal photo you’ve taken and really make it look unique by giving it harder edges and some more texture to the shot. Mix up your photos with this effect.

Learn how to play gin rummy: knocking variation. In this version of Gin, you can end a game by "Knocking."

Video: . Download: here

Friendship bracelets are the most personal testaments to a good friend that you can make. Celebrate your friendship while creating a work of art that will last a very long time by weaving together this friendship bracelet with an "S" spiral.
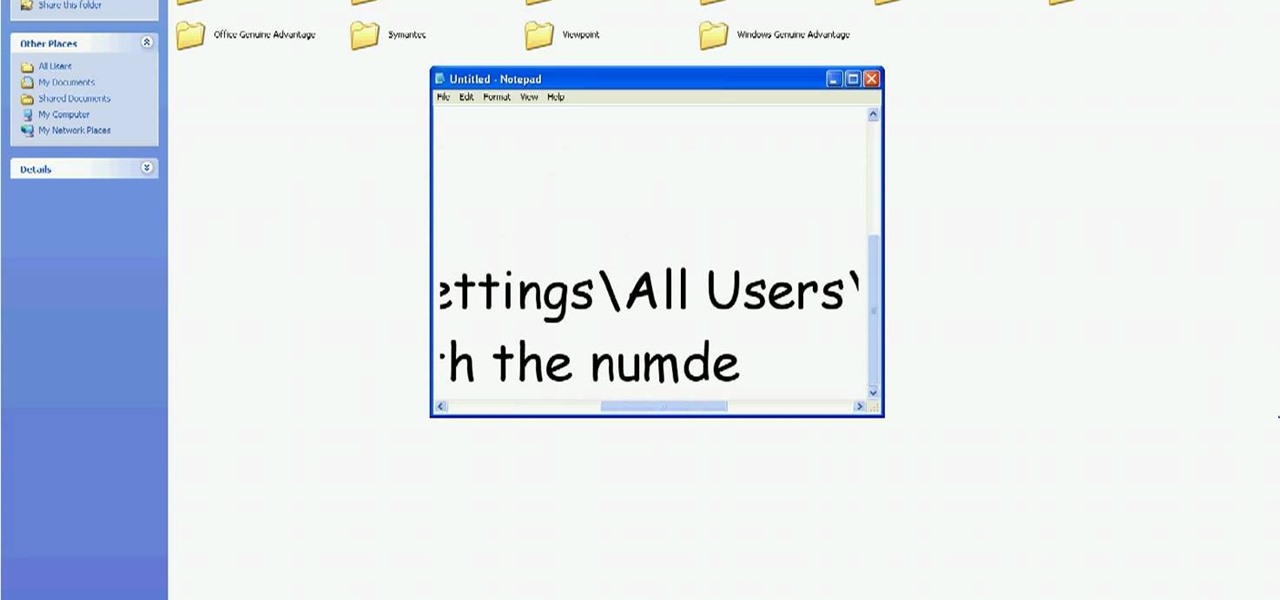
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...

No matter what kind of business you have, small or big, online-based or not, when you're dealing with email marketing, the number one things your targets will see is the subject line, and if your subject line looks spammy or uninteresting, it's not going to help you one bit.