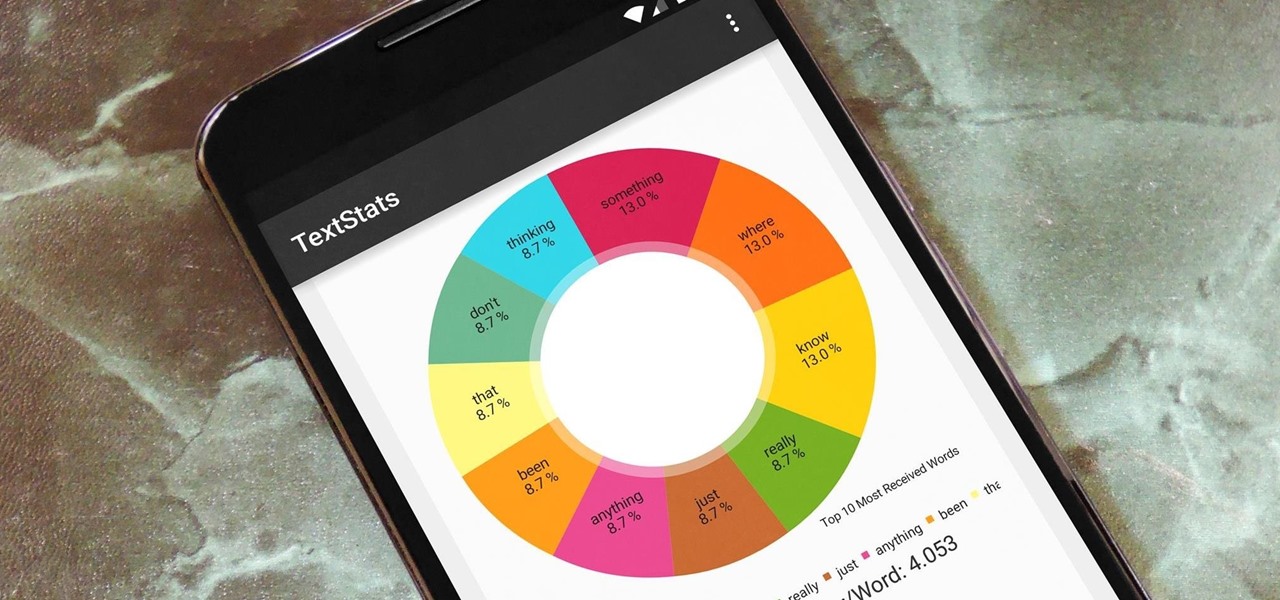
Android's copy/paste menu and text selection options have traditionally been downright terrible, but things are starting to get better with some recent improvements made in Marshmallow. That being said, there's still a lot left to be desired, and there's always plenty of room for more useful functionality.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

What's up guys! It's time to discuss strings in more detail. Review

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

At this point, it'd be surprising if an iPhone release wasn't coupled with some sort of new scandal or controversy; it's gradually becoming Apple's new modus operandi. First, there was antennagate with the iPhone 4. Then it was scuffgate with the iPhone 5. Last year, it was bendgate with the iPhone 6 models. This year, it's chipgate with the iPhone 6S models, which affects something important to all on us—battery life.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

As it stands, Android's notification system is one of its biggest strengths—but that doesn't mean it couldn't use a few tweaks here and there. For one thing, when you receive multiple notifications from the same app, there is no indication as to exactly how many notifications you've received.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

With platforms like Facebook, Instagram, and Snapchat available for anyone to take advantage of, I'm all about differentiating from the mundane and repetitive images we see on social media everyday.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

With the advent of text messaging, our communication habits have changed drastically. Social niceties are still there, but we budget our words a little more since they have to be typed out rather than spoken. After all, SMS stands for "Short Message Service," so this is the nature of the beast.

Before phones became mobile-gaming, music-playing, app-downloading devices, they were used simply to make convenient, cordless phone calls. There's so much on phones these days that a passcode is needed to keep everything secure, and making calls is now more complicated.

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

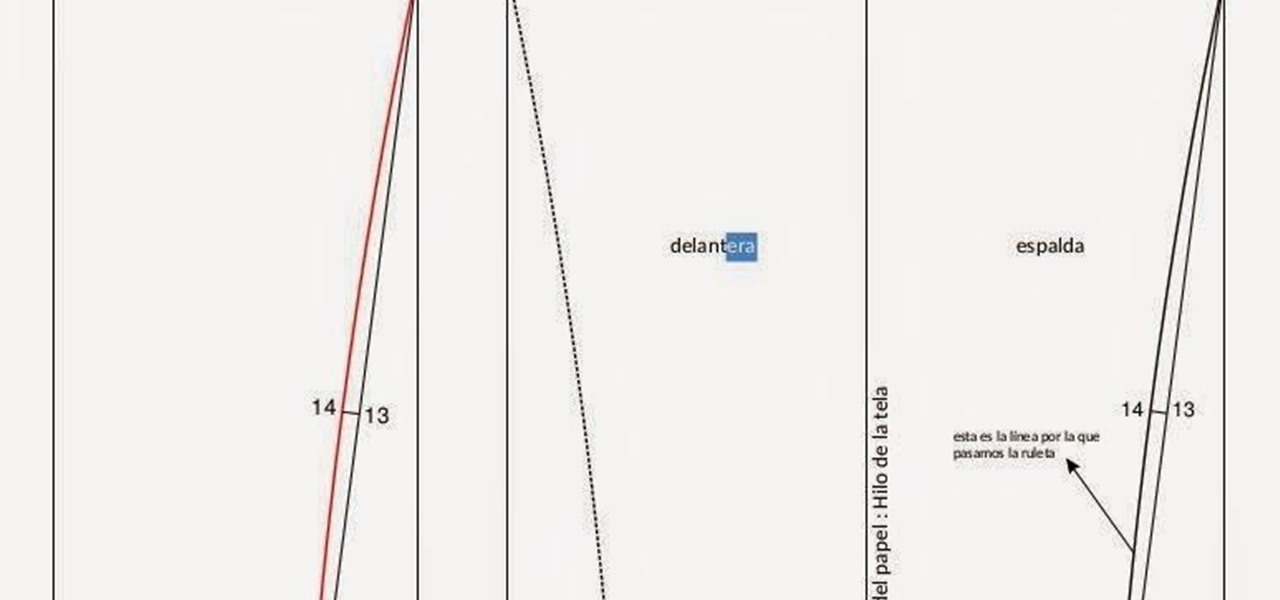
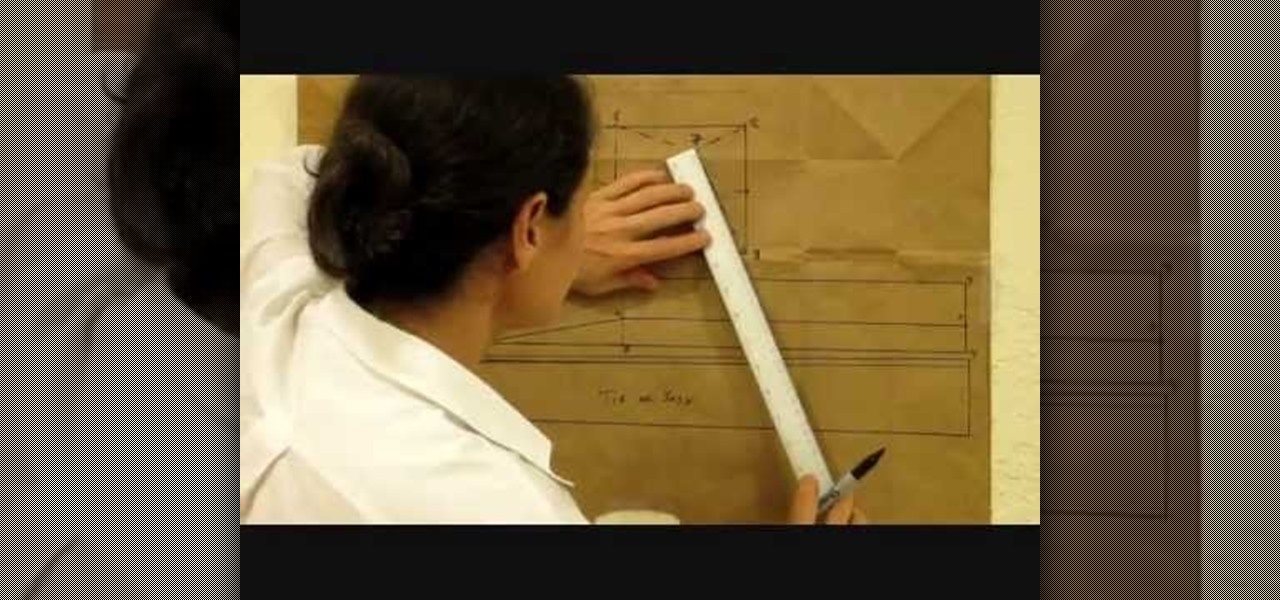
A well designed sleeve is very important to creating a top or jacket that fits comfortably. Get your correct measurements before you begin. Please view the following step-by-step instructions and accompanying video and diagram to create the basic sleeve.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

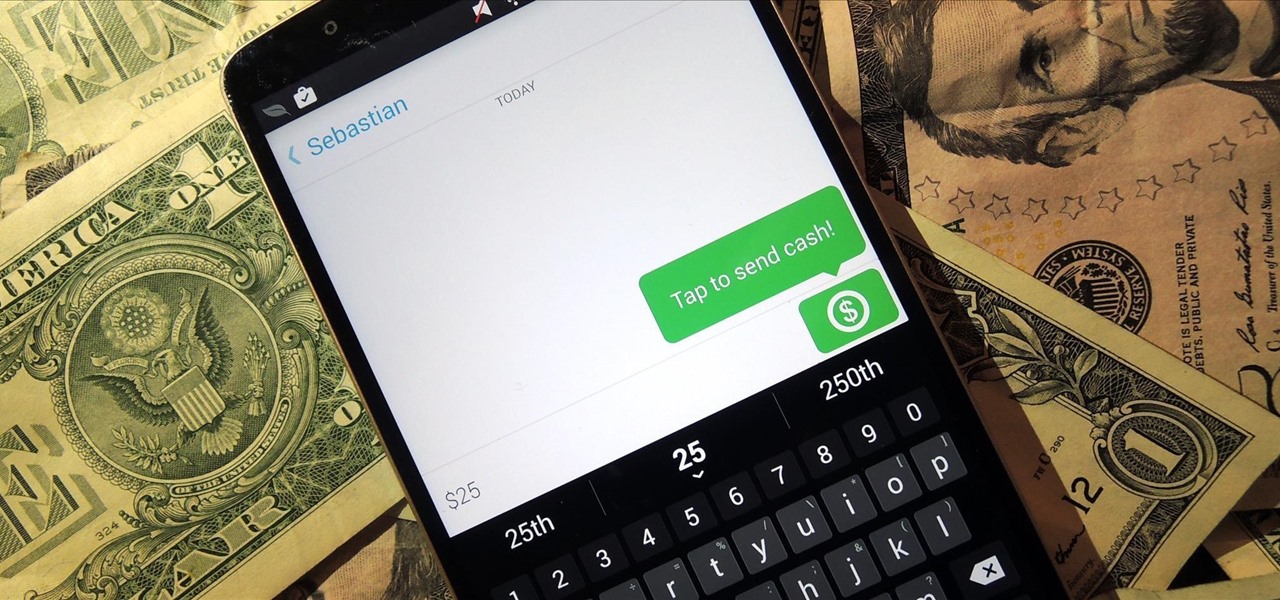
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

At one point, Netflix did have trailers for movies online, but they have long since abandoned the practice for a number of reasons. Firstly, trailers have to be licensed in addition to films themselves. Secondly, previews apparently did not increase the number of titles added to user queues.

Automator takes the work out of common repetitive tasks in Mac OS X. One of my least favorites is resizing images for the web, so I created a drag and drop action to quickly do it for me.

Welcome to the first chapter of Excel is Simple, a place where we will burst all myths around excel and try to make it simpler and fun to use.

While LG G3 users have been patiently waiting, developer the cubed and his Codefire team have been diligently working on a successful unlock method for the heavily locked-down bootloader. Now it's finally here, and the unlocking method is extremely easy to do—and it works for all G3 variants.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

When I stumble upon a new song that I'm really into, I don't just listen to it repeatedly—I share it with family and friends that I think might enjoy it just as much as I do. Now, thanks to a new iOS app called Craaave, sharing those tunes are a cinch, no matter if I'm using Spotify, SoundCloud, or any other music streaming app on my iPhone.

Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

HTC has made it their mission to get updates out to its devices as quickly as possible, with new builds slated for release 90-days after Google finalizes a build—this is dubbed HTC Advantage.

If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible.

Apple is bringing one of the biggest updates ever to its Messages app, including a feature that will allow users to send audio messages back and forth with the press of a button. Goodbye, voicemail.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

Having an open-source platform like Android is great, allowing manufacturers and developers the ability to make their own skins and apps to truly customize the end-user experience. The only downside is that when an update comes to vanilla Android, many of us are left in the cold, unless you have a Google Play Edition HTC One.

I don't read all of my emails, and even though it may sound a little bit odd, I don't listen to all of my voicemails either. For me, the problem isn't reading or listening to them, it's how it affects my iPhone's home screen.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

One of the best things about iOS 7 is the Control Center, which gives you quick access from anywhere on your iPhone to turning on or off Airplane Mode, Wi-Fi, Bluetooth, and more. It also makes it very easy to adjust the brightness of your display, and gives app shortcuts for your Flashlight, Calculator, Timer, and Camera.

Video: . Whether you are gardening, cooking, riding a motorcycle or just want to cover up on a bad hair day, doo rags are easy to make and fun to personalize to suit to your style. If you would rather just download the durag pattern click here.

No matter how much of a gamer you are, typing with your PS4 controller is a bitch. Let's just be real. Having to move left, then right, then down, for every single letter can make writing a message very time consuming; so much so that I usually avoid messaging altogether.