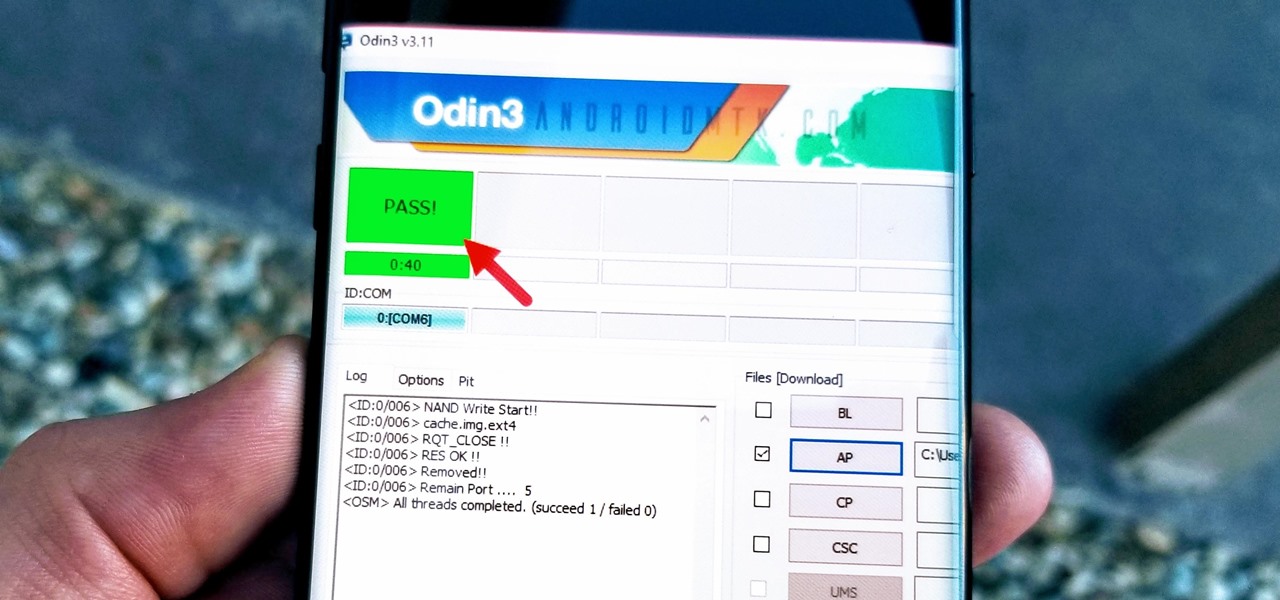
One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.
During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

The LG G7 ThinQ will likely be lambasted for its notch and awkward name, but one thing they seem to have gotten right is the new display. The G7 ThinQ will give many a first look at a new type of panel with lots of promise. While it was previously limited to TVs, from what we know, it should really shine on a smaller screen.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

Over the past week, we've had a number of important launches take place in the Android community. Samsung is in the middle of their rollout of the Galaxy S9, with preorders in the US shipping this week. Google also rolled out the first Android P developer preview last week. While these may seem unrelated, there are actually a number of Android P features inspired by Samsung software.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

OnePlus is on track to deliver Android 8.0 Oreo to its flagship users by Q1 2018. Open Beta 1 was released for the 5T in late December, and we just received Open Beta 2. But this update isn't just tweaks and bug fixes, OnePlus has included a few new features to enhance the Android experience.

With beta testing coming to a close, it's quite likely we will see the stable Android Oreo OTA roll out for the Galaxy S8 in late January. Yesterday, a Reddit user posted a link to an official Oreo OTA build for the Galaxy S8. We've already detailed everything that's new in this stable build. Now, let's take a look at how you can install the update on your device.

One of the biggest gripes we always hear about is the changes OEMs make to Android's notification shade. Icon styling and home screen layouts can be fixed with custom launchers like Nova and Action, but we're stuck with the tacky Quick Settings theme our phones came with. Today, we no longer have to envy Pixel 2 owners, as a new app will give you that clean stock Android look on any phone.

Shortly after we detailed several indicators that the Galaxy S8 Oreo Beta Program would begin rolling out in the month of November, we now have a full changelog for the update.

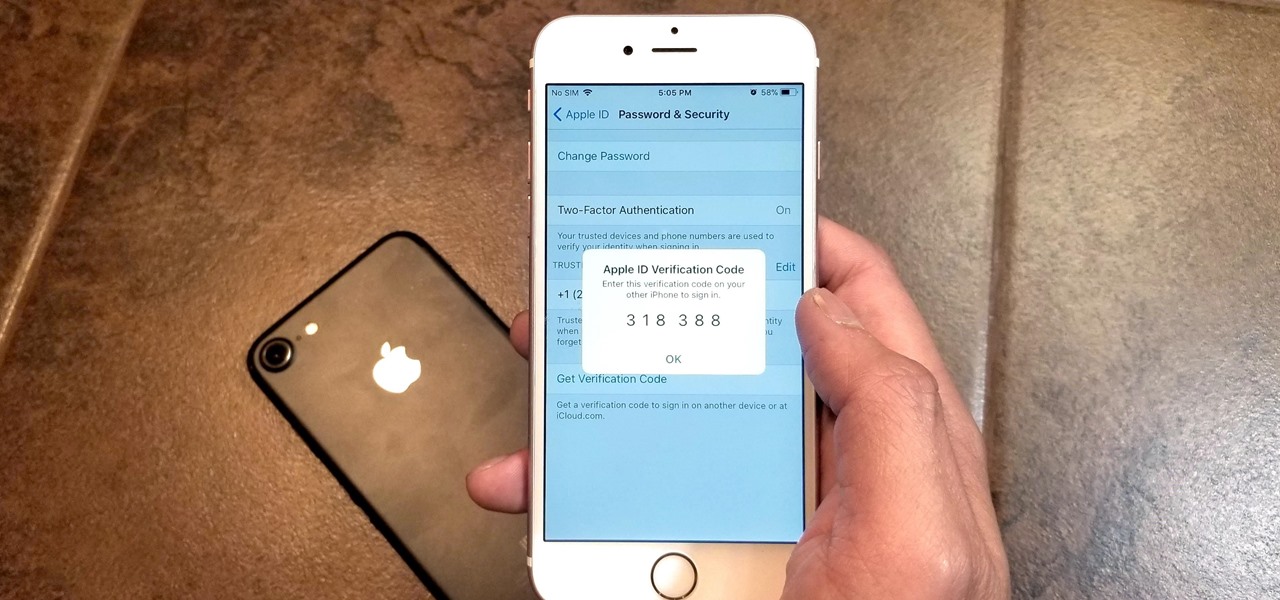
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

One of the least important but most noticeable changes in any iOS update is the look of home screen icons. In the new iOS 11, there aren't any drastic icon differences compared to iOS 10, but there's definitely a few design modifications for some of the main stock apps, such as Maps and the App Store.

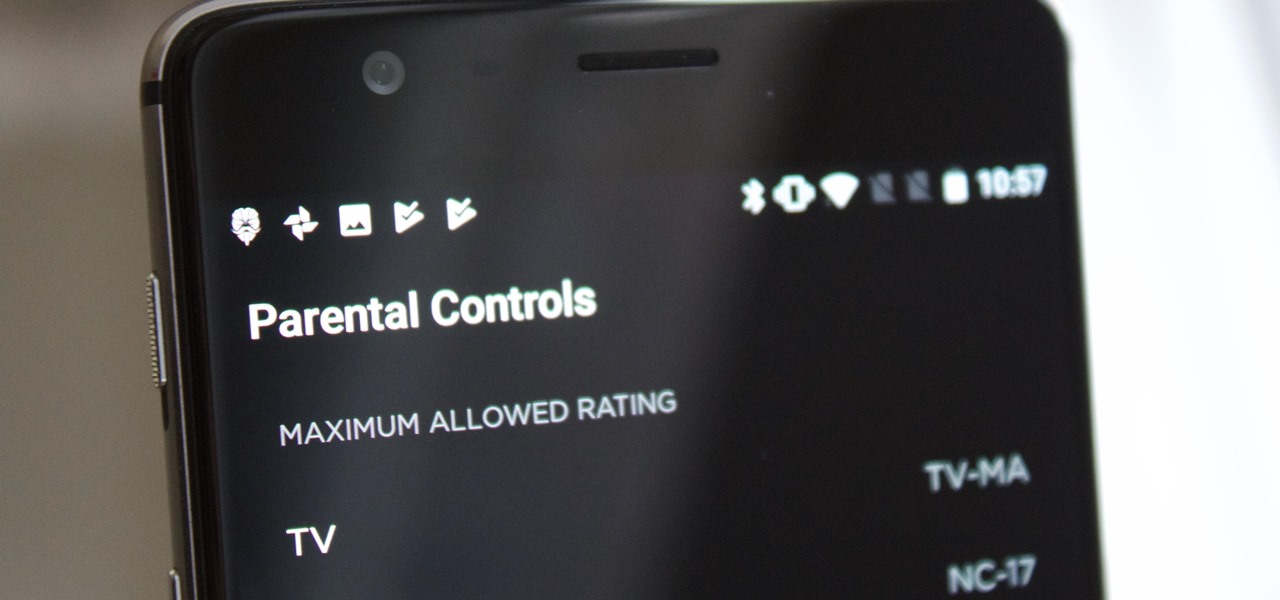
It's no secret that HBO has some ... mature content. Just watch the first five minutes of Game of Thrones. Yeah, I know. What a ride. But here's the thing — HBO has kids content, too, and it's good stuff!

One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend will receive a fire emoji next to your names.

Just like your gastrointestinal tract, and the soil we walk on — a dust storm has a collection of bacteria, fungi, and viruses all its own called a "dust microbiome."

To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

The possibility of severe tickborne illness is increasing as an aggressive tick from the American southeast moves up the Atlantic Coast.

When just floating peacefully in the water with their brood mates, the Culex mosquito larvae in the image above does not look very frightening. But in their adult form, they are the prime vector for spreading West Nile virus — a sometimes mild, sometimes fatal disease.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

Update Feb. 2020: Google has removed the feature flag to move the address bar to the bottom of the screen. We've out to see if they have plans to bring it back, but received no comment. In the meantime, you can use the new Chrome Duet bottom bar instead.

A sometimes serious disease spread by fleas is making inroads in Texas, quietly doubling case numbers since 2008, and beginning to encroach on larger metropolitan areas.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

Although their effectiveness is waning, antibiotics remain a front-line defense against many infections. However, new science reveals using the wrong antibiotic for an infection could makes things much worse.

Lighthouses and signal fires may have been the first social media. Without the ability to share language, a distant light meant "humans here." A new study from the University of California, San Diego, finds that bacteria can also send out a universal sign to attract the attention of their own, and other bacterial species.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

Smartphone manufacturers do their best to keep you tied down to their ecosystem, but the reality is that there's not much keeping you from switching. Transfer some files, install a few apps here and there, and all of a sudden, you're knee-deep in a new operating system.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.