This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

When an album sells a million copies, it gets certified as platinum and cements itself as one of its generation's biggest hits. When an album sells 10 million copies, it reaches diamond status and transcends generational gaps. But when an album sells well over 40 million copies, there's only one thing you can call it—Michael Jackson's Thriller.

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

With every version bump, Android gets a new Easter egg that can be accessed by tapping the "Android version" entry in Settings. For the most part, these have generally been little animations or live wallpapers that depict the Android code name, but starting with version 5.0 Lollipop, things got a bit more interesting.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

Android 6.0 Marshmallow is bringing in lots of changes to our favorite smartphone operating system, ranging from battery-saving tweaks like Doze to a Now on Tap feature that essentially bakes Google right into every app on your phone. But for folks that like to tweak the interface of their device, a new hidden menu might be the most exciting addition of them all.

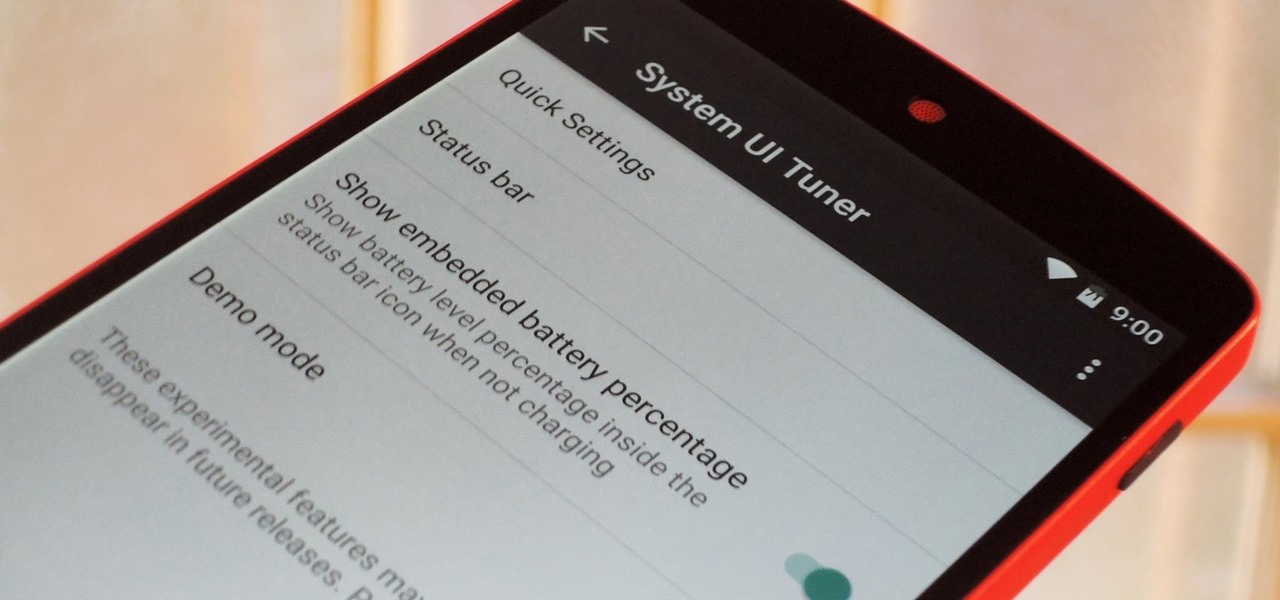
With as much creativity and freedom that we have on Android, it feels a little underwhelming that the only gesture we can perform on the status bar is a downward swipe to expose the notification tray or quick settings. Maybe this is a field for Android to expand on in the future, but until that day, third-party developers are exploring this now.

Step aside, vodka—whiskey will soon be the best-selling hard liquor in the United States. The whiskey renaissance has been largely attributed to the current trend for locally- and artisan-produced goods. Local whiskey distilleries are rapidly increasing in number across the nation while bars in every state are including the old-fashioned cocktail on their menus in an attempt to capitalize on the trend (which we can probably thank Mad Men for).

Cauliflower has become trendy again, and it's mostly thanks to the low-carb crowd who use its mild flavor and soft texture as a replacement for things like rice and pizza dough.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

In response to the success of Apple Pay and an attempt to stave off the appealing Samsung Pay service, Google is completely revamping Android's mobile payments system. Instead of just using Google Wallet as an app to make payments with your phone, a new service called Android Pay, with an extensive underlying framework and API, will soon make its debut—and maybe even sooner than you'd think.

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around this time, you start to wonder if your trusty old remote has finally called it quits or if it's just a dead battery.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Who doesn't experience food cravings? Whether you're trying to adhere to a strict diet, or simply hoping to avoid sugary, fatty foods, curbing cravings can feel like a monumental task.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

The Samsung Galaxy S6 includes a pretty nifty feature known as "Gesture wake up," which lets users wave their hand over their locked display to wake it, making those periodic notification checks from the lock screen a lot more simple than having to press the power or home key every time.

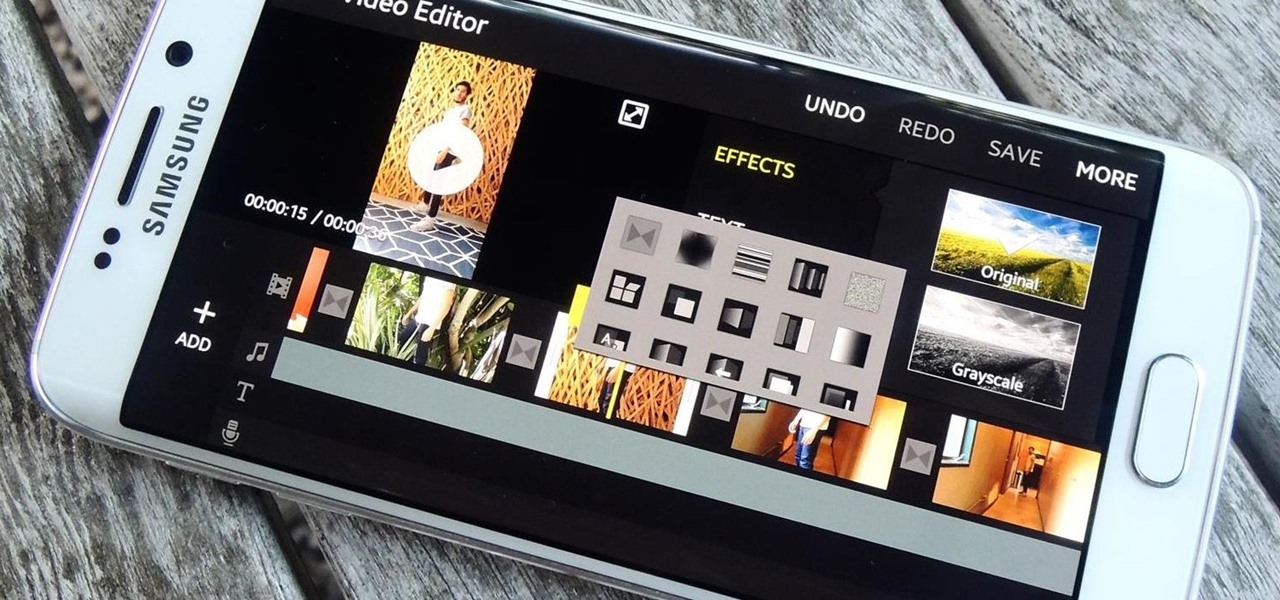
Editing a video by trimming or adding audio is fairly simple on Galaxy devices, but if you want to include other clips or transition animations and really get those creative juices flowing, you might find the standard editing tools limited—unless you know how to unlock Samsung's hidden video editor.

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

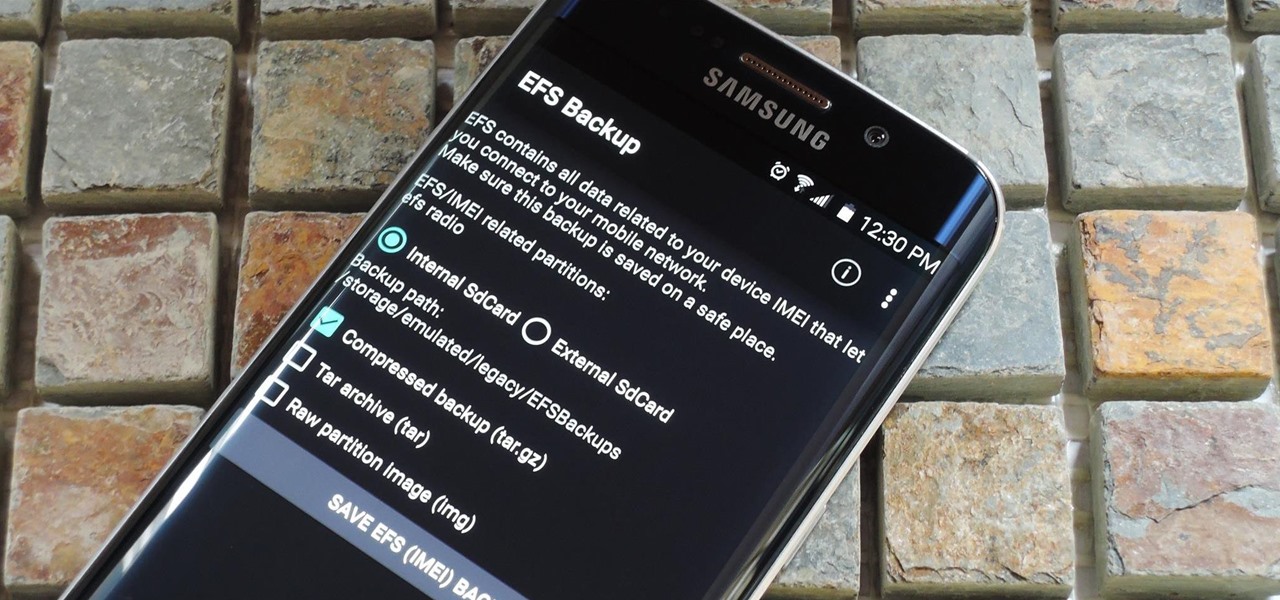
The EFS partition on modern Android phones houses the unique IMEI for your device, which is essentially an identification number that lets you connect to mobile networks. But sometimes, when you're flashing ROMs or restoring backups in custom recovery, the EFS partition can become corrupted, which will prevent your phone from connecting to any type of mobile network.

As crazy as it sounds, there are times when bottles of wine go unfinished. I love a glass or three of vino, but am often guilty of not finishing the bottle. Sometimes I don't have the time to finish it, and other times I like it so much that I open bottle number two and can't finish that.

If your iPhone is rebooting or your Messages app is constantly crashing, you might be the victim of an iOS exploit or just a buggy software update. While one problem sounds worse than the other, they both can get annoying real quick when you can't send any messages or even read new ones.

Fruit flies are nearly as frustrating as ants and equally impossible to eradicate—but there are a few ways to get rid of them. We've already shown you that apple cider vinegar, dishwashing soap, and plastic wrap is a great way to trap and kill fruit flies, but if you just want to keep them away, there's another option—cloves. Fruit flies are attracted to ripened fruits and vegetables, but don't actually eat them. They eat the fungus or rot that grows on them, according to Todd Schlenke, assis...

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.

There are a number of ways to give your productivity a kicktstart, from taking a break from your distracting smartphone to just taking a break, plain and simple. Yet finding the motivation to start working doesn't require any effort at all—just a little bit of green.

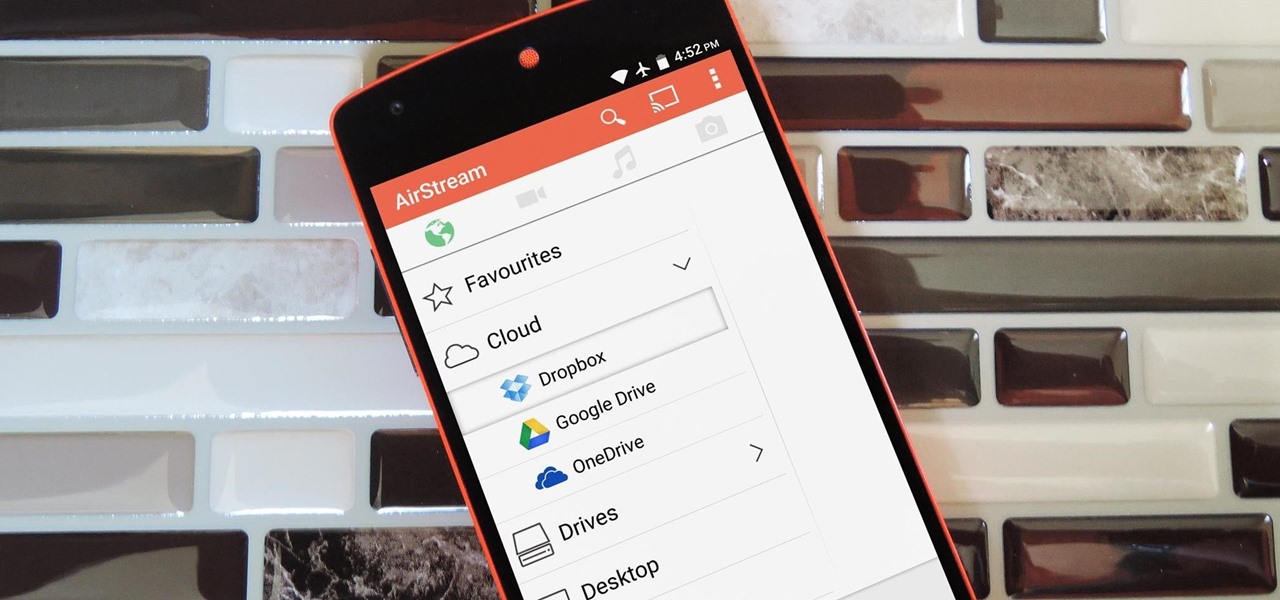
Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

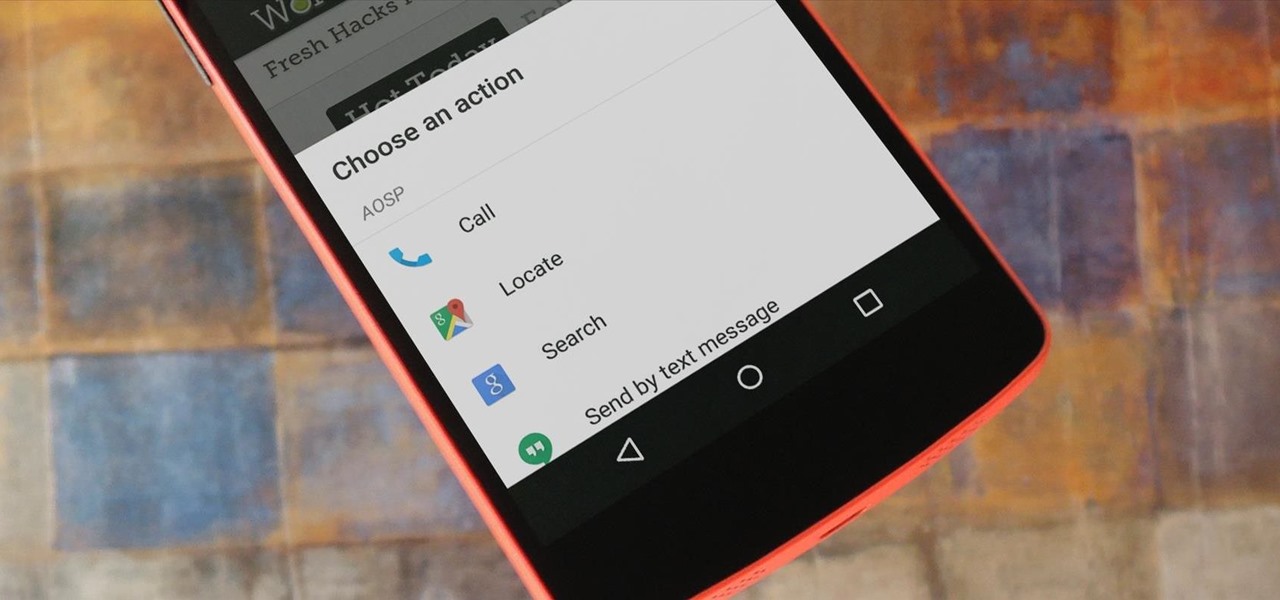
For the most part, when you're copying text on your Android device, it's because you intend on pasting it into a different app than the one you're currently using. For instance, you might be looking at a posting on Craigslist. So you copy the seller's phone number, then head to your home screen, switch over to your phone app, paste it into your dialer, and finally make the call.