There are several ways to get around location restrictions on subscription sites like Netflix and Hulu using apps, extensions and proxies, but they tend to only work on laptops and computers. Users who want to access content from mobile devices and gaming consoles are usually out of luck.

Apple has released the third beta of its iOS 7.1 software to developers, just a few weeks after their second beta introduced us to button shapes, a new calendar list view toggle, a hidden Car Display control and several other tweaks and performance improvements.

One good thing about having friends who are constantly on their phones and tablets is it's easy to figure out what to get them for Christmas. Everyone hates getting gifts that just sit around, so it's always nice to get something that improves an item you use on a daily basis.

For those of you who have (or had) and iPhone, one of the cooler photo apps for iOS was VSCO Cam, an extremely popular camera with pro-quality filters and effects. Now this app is available for Android on Google Play for your Nexus 7 tablet and any other devices running Android 4.0 and up.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Phone interruptions are commonplace, as is evident by my historically epic missed phone call list, ranging from annoying sales people to my mom checking in every five minutes to see if I'm still alive.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

The day I picked up my iPhone 5S was a very exciting day. I had taken all the correct steps in backing up my old device so that after a quick restore-from-backup (which turned into half an hour), I was right at home on the new hardware.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

If you've seen our guide on the 18 coolest features in iOS 7, you know that there's a lot to like about Apple's new mobile OS, but there's also a laundry list of grievances to go with it. One that bugs me is the lack of Home screen customization, something that has always driven me to jailbreak in the past.

Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

For most of us regular folk, the only opportunity to relish in the conveniences of a maid is during hotel stays. Personally, I would love to have a maid around to help fold my clothes and sweep up those crumbs that accumulate in the corners of my kitchen, but sadly, I currently live in reality and can't afford that luxury just yet. In real life, I'm on my own.

Learning to make giant bubbles for this video has been the most fun I've had with a project in a long time. It's addicting to try to get them to grow bigger and bigger than the ones before. Since filming this video, my skill has improved tremendously and the bubbles you're about to see, though spectacularly big, are dwarfed by what I've made since. Everyone loves to watch. This is definitely one project that will draw a crowd!

If you're new to Android phones, one of the first things you've probably noticed is how notification alerts differs from Apple devices, especially in regards to getting a text message.

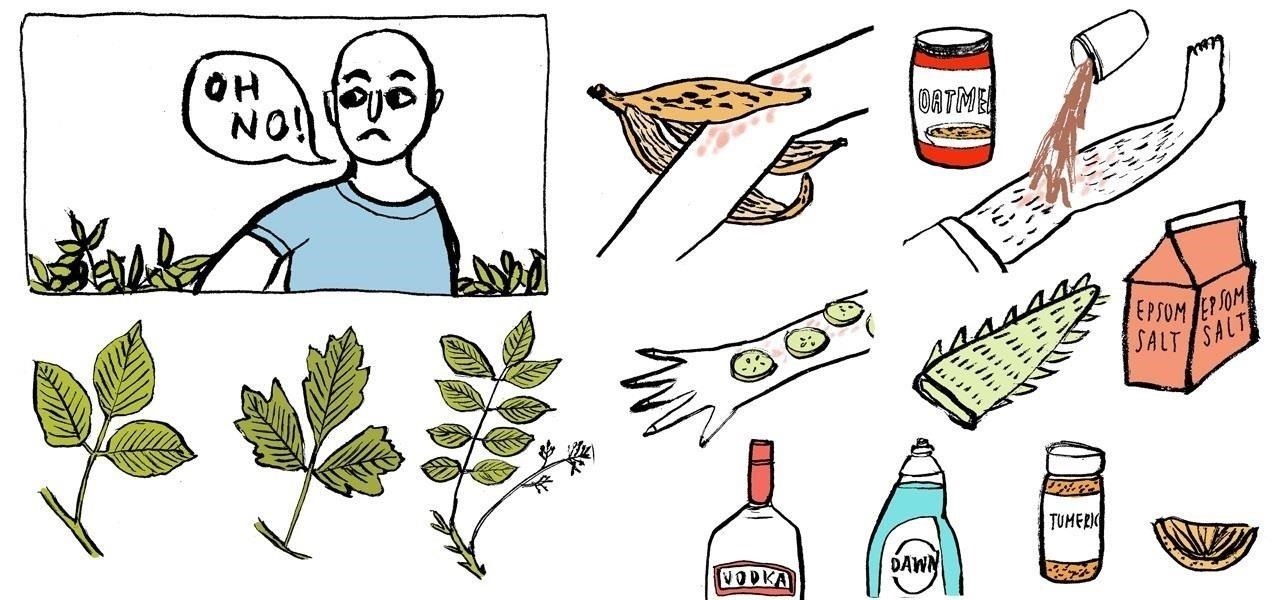
Poison ivy, poison oak, and the lesser known skin irritator, poison sumac, can all cause a conundrum in the search of itch relief: to scratch or not to scratch. Fortunately, there are a number of home remedies one can try to help alleviate the itch(ing), with many like coffee, a banana, baking soda, or mouthwash likely already in-house for most.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.

The new Android 4.3 Jelly Bean has been out for a while already, and most of you already have it installed on your Nexus 7 tablets. Many of you softModders have also probably rooted your tablet so you can take advantage of some of the more popular root-only softMods, like speeding up performance, installing WhatsApp, increasing internet speeds, getting Beats Audio, etc.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

Once when I was a kid, my dad used a glue trap to catch a mouse in our basement. The result was so awful for the mouse that my mom and I made him promise to never use that kind of trap again. Call me a softy, but I'm a firm believer that you don't have to kill pests to get rid of them.

With so many cloud storage services out there, many people are starting to keep their important documents online, especially when they know they'll need to view them when they're away from their computer.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

What's the most installed Android app in the world? Facebook? Gmail? Maps? While those all have well over 100 million installs, the one that takes the cake—and always will—is Google Play.

Here's a quick and easy video tutorial on how to root any Qualcomm-based U.S. or Canadian Galaxy S4 Android smartphone.

Like most Android devices, the Nexus 7 suffers from its fair share of battery gripes. Nobody wants to see that dreaded "connect charger" warning pop up on their screen. NOBODY. Yet it probably happens to you every day nonetheless. What can you do about it besides charge, charge, and charge? Well, there's actually plenty that you can do. You can manage your notifications better, keep your screen brightness low, and kill apps running in the background. Or, you could just optimize your battery t...

Plastic red cups are synonymous with college parties, beer pong, and generally a good time. The reason these cups are so rampant in the party scene is because they're cheap, easily disposable, and, well... who wants to drink out of a blue cup?!? Oh, to be young and in debt.

Gaining remote access to a phone isn't only for super hackers and spies. There are plenty of times when the average smartphone user would want to have remote access to their device.

There are so many things in life I wish I could've canceled without any repercussions, and I'm mostly talking about text messages.

I'm not entirely sure how to describe band Frenchy and the Punk, but if I say things like cabaret, punk, and fun, you'll probably get the idea. Their website calls them "rollicking flapper folk punk cabaret", which is about as many words as you need to describe them. I wouldn't call them punk per se, but you can definitely hear the punk influence in their sound.

PUT THE PHONE DOWN!!! Don't call the locksmith just yet! Watch this video and l will save you at least $100.00

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Hello again, faithful readers. For today's lesson, we will be learning the correct way to restring and tune an electric guitar. I almost wasn't going to post this because it is so basic. But, as with many basic tasks, there are a lot of people who know how to do it, but can't really do it right. If you are a new guitarist, this is an essential piece of maintenance work, because guitar shops usually charge way too much for this task. Of course, I'm kinda cheap, so even 5 bucks is too much for ...

Portal has been one of the most critically acclaimed and universally loved games of the last few years, and there's plenty of fan art to prove it. From building a Portal gun, to a gravity defying Companion Cube, and even installing Portal onto a graphing calculator, fans have found some innovative ways to show their love for the games.

A car is stolen every 33 seconds in the United States, and from that, the percentage of vehicles recovered in the first day is a whopping 52 percent. Over the next week, that number rises to around 79 percent, but after those initial seven days are up, it's unlikely the vehicle will be found.